Automating Configuration N49(PDF)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
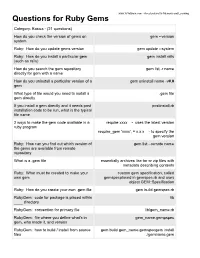
Questions for Ruby Gems
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for Ruby Gems Category: Basics - (21 questions) How do you check the version of gems on gem --version system Ruby: How do you update gems version gem update --system Ruby: How do you install a particular gem gem install rails (such as rails) How do you search the gem repository gem list -r name directly for gem with a name How do you uninstall a particular version of a gem uninstall name -v#.# gem What type of file would you need to install a .gem file gem directly If you install a gem directly and it needs post postinstall.rb installation code to be run, what is the typical file name 2 ways to make the gem code available in a require xxxx - uses the latest version ruby program require_gem 'xxxx', = x.x.x - to specify the gem version Ruby: How can you find out which version of gem list --remote name the gems are available from remote repository What is a .gem file essentially archives like tar or zip files with metadata describing contents Ruby: What must be created to make your custom gem specification, called own gem gemspecplaced in gemspec.rb and uses object GEM::Specification Ruby: How do you create your own .gem file gem build gemspec.rb RubyGem: code for package is placed within lib ____ directory RubyGem: convention for primary file lib/gem_name.rb RubyGem: file where you define what's in gem_name.gempspec gem, who made it, and version RubyGem: how to build / install from source gem build gem_name.gemspecgem install files ./gemname.gem RubyGem: how to push a created gem to gem push gem_name-0.0.0.gem RubyGems.org RubyGems: how to detect a gem on gem list -r gem_name RubyGems.org RubyGems: convention for adding modules / make a directory inside lib with same name classes to gem as gemlib/gem_name/ . -

Third-Party Software for Engage Products APPLICATIONS Red Hat
Third-Party Software for Engage Products APPLICATIONS Red Hat Enterprise Linux General Information Source Code Status Not modified by Vocera URL https://www.redhat.com/en/about/licenses-us Supplemental END USER LICENSE AGREEMENT (November 2010) License Text RED HAT® ENTERPRISE LINUX® AND RED HAT APPLICATIONS PLEASE READ THIS END USER LICENSE AGREEMENT CAREFULLY BEFORE USING SOFTWARE FROM RED HAT. BY USING RED HAT SOFTWARE, YOU SIGNIFY YOUR ASSENT TO AND ACCEPTANCE OF THIS END USER LICENSE AGREEMENT AND ACKNOWLEDGE YOU HAVE READ AND UNDERSTAND THE TERMS. AN INDIVIDUAL ACTING ON BEHALF OF AN ENTITY REPRESENTS THAT HE OR SHE HAS THE AUTHORITY TO ENTER INTO THIS END USER LICENSE AGREEMENT ON BEHALF OF THAT ENTITY. IF YOU DO NOT ACCEPT THE TERMS OF THIS AGREEMENT, THEN YOU MUST NOT USE THE RED HAT SOFTWARE. THIS END USER LICENSE AGREEMENT DOES NOT PROVIDE ANY RIGHTS TO RED HAT SERVICES SUCH AS SOFTWARE MAINTENANCE, UPGRADES OR SUPPORT. PLEASE REVIEW YOUR SERVICE OR SUBSCRIPTION AGREEMENT(S) THAT YOU MAY HAVE WITH RED HAT OR OTHER AUTHORIZED RED HAT SERVICE PROVIDERS REGARDING SERVICES AND ASSOCIATED PAYMENTS. This end user license agreement (“EULA”) governs the use of any of the versions of Red Hat Enterprise Linux, certain other Red Hat software applications that include or refer to this license, and any related updates, source code, appearance, structure and organization (the “Programs”), regardless of the delivery mechanism. 1. License Grant. Subject to the following terms, Red Hat, Inc. (“Red Hat”) grants to you a perpetual, worldwide license to the Programs (most of which include multiple software components) pursuant to the GNU General Public License v.2. -

Puppet Offers a Free, Reliable and Cross Flavor Option for Remote Enterprise Computer Management
This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author (s) and do not necessarily reflect the views of the National Science Foundation C4L8S1 System administrators are constantly challenged when managing large enterprise systems using Linux-based operating systems. Administrators need to know a variety of command line differentiations, dependency variations, and support options to support the various computers systems in use. Puppet offers a free, reliable and cross flavor option for remote enterprise computer management. This lesson will introduce you to the Puppet AdministrativeU the tool and provide you with a basic overview on how to use Puppet. Lab activities will provide you with hands-on experience with the Puppet application and assignments and discussion activities will increase your learning on this subject. Understanding Puppet is important because of its ability to manage enterprise systems. Students hoping to become Linux Administrators must gain mastery of enterprise management tools like Puppet to improve efficiency and productivity. C4L8S2 You should know what will be expected of you when you complete this lesson. These expectations are presented as objectives. Objectives are short statements of expectations that tell you what you must be able to do, perform, learn, or adjust after reviewing the lesson. Lesson Objective: U the Given five computers that need to be configured, -

Symbols & Numbers A
ruby_02.book Page 267 Thursday, May 10, 2007 4:12 PM INDEX Symbols & Numbers \ (backslash), in regular expression, for literal characters, 144 %Q for instantiating Strings, 23, \W, in regular expression, for 108–109, 215–216, 219, 239, whitespace, 66 245, 248–250 { } (braces) %w for instantiating Arrays, 47, for blocks, 28 113, 115 for declaring Hash, 42 & (ampersand), for expressing blocks {x}, in regular expression, 79 and Procs, 105–106 - method (Hash), 93 ! (exclamation point), for destructive ||= operator, 77–78, 127 methods, 20, 22–23 | (pipe) character, in regular || (or) operator, 17 expression, 56 # character + method of Integers and Strings, 3–4 for comments, 14 + (plus sign), in regular for instance method, 234 expression, 62 #{} for wrapping expression to be = (equal sign), for assigning value to interpolated, 23 variable, 9 #! (shebang), 47 == operator, for equality testing, 14 $ (dollar sign), for bash prompt, 19 =begin rdoc, 22 * (asterisk), in irb prompt, 8 =end, 22 ** (asterisk doubled), for “to the <=> method (Comparable), 145, power of,” 72 150–151 /\d+/ in regular expression, for digits <% and %> tags, 211 only, 79 <%= tag, for printing expression, 214 :needs_data Symbol key, 116 99bottles.rb script, 20–25 :nitems Symbol key, 116 :unless0th Symbol key, 116 ? (question mark) A in predicate method names, 22 actionpack, warnings related to, 226 in regular expression, for optional Active Record, Rails dependence expressions, 144 on, 227 @ sign, for instance variable, 21–22 Agile Web Development with Rails @@ sign, for class -

Tsuru Documentation Release 1.6.2
tsuru Documentation Release 1.6.2 tsuru Oct 04, 2018 Contents 1 Understanding 3 1.1 Overview.................................................3 1.2 Concepts.................................................4 1.3 Architecture...............................................5 2 Installing 7 2.1 tsuru Installer...............................................7 2.2 Installing tsuru components....................................... 12 3 Managing 21 3.1 Installing platforms............................................ 21 3.2 Creating a platform............................................ 22 3.3 Using Pools................................................ 23 3.4 Provisioners............................................... 25 3.5 Clusters.................................................. 26 3.6 Segregate Scheduler........................................... 27 3.7 Upgrading Docker............................................ 27 3.8 Managing Git repositories and SSH keys................................ 28 3.9 Managing users and permissions..................................... 28 3.10 Managing Application Logs....................................... 32 3.11 Debugging and Troubleshooting..................................... 33 3.12 Volumes................................................. 34 3.13 Event webhooks............................................. 35 4 Using 39 4.1 Installing tsuru client........................................... 39 4.2 Deploying................................................ 40 4.3 App-Deploy.............................................. -
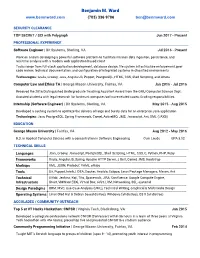
Benjamin M. Ward (703) 336 9706 [email protected]
Benjamin M. Ward www.benmward.com (703) 336 9706 [email protected] SECURITY CLEARANCE TOP SECRET / SCI with Polygraph Jun 2017 - Present PROFESSIONAL EXPERIENCE Software Engineer | Bit Systems, Sterling, VA Jul 2016 - Present Work on a team developing a powerful software platform to facilitate mission data ingestion, persistence, and real-time analysis with a modern web application based client Tasks range from full-stack application development, database design, file system infrastructure enforcement, peer code review, technical documentation, and configuration of integrated systems in classified environments Technologies: Grails, Groovy, Java, AngularJS, Puppet, PostgreSQL, HTML, CSS, Shell Scripting, and others Computer Law and Ethics TA | George Mason University, Fairfax, VA Jan 2016 - Jul 2016 Received the 2016 Distinguished Undergraduate Teaching Assistant Award from the GMU Computer Science Dept. Assisted students with legal research for landmark computer/software related cases; Grading responsibilities Internship (Software Engineer) | Bit Systems, Sterling, VA May 2015 - Aug 2015 Developed a caching system to optimize the delivery of large and bursty data for an enterprise Java application Technologies: Java, PostgreSQL, Spring Framework, Camel, ActiveMQ, JMS, Javascript, Ant, XML (JAXB) EDUCATION George Mason University | Fairfax, VA Aug 2012 - May 2016 B.S. in Applied Computer Science with a concentration in Software Engineering Cum Laude GPA 3.52 TECHNICAL SKILLS Languages Java, Groovy, Javascript, PostgreSQL, Shell -

Enterprise Integration with Ruby a Pragmatic Guide
Enterprise Integration with Ruby A Pragmatic Guide Maik Schmidt The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas P r a g m a t i c B o o k s h e l f Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. Every precaution was taken in the preparation of this book. However, the publisher assumes no responsibility for errors or omissions, or for damages that may result from the use of information (including program listings) contained herein. Our Pragmatic courses, workshops, and other products can help you and your team create better software and have more fun. For more information, as well as the latest Pragmatic titles, please visit us at http://www.pragmaticprogrammer.com Copyright © 2006 The Pragmatic Programmers LLC. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmit- ted, in any form, or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior consent of the publisher. Printed in the United States of America. ISBN 0-9766940-6-9 Printed on acid-free paper with 85% recycled, 30% post-consumer content. First printing, March 2006 Version: 2006-5-4 Für meine Eltern. -

Zentrale Verwaltung Mit Facter, Puppet Und Augeas
System-Management-Trio Zentrale Verwaltung mit facter, puppet und augeas Verwaltung mit facter, puppet und augeas © SpeedPartner GmbH Seite: 1 / 34 GUUG Frühjahrsfachgespräch, 01.03.2012 Über den Vortrag Aufbau / Ziele: ● Einführung / Überblick ● Begriffsklärung ● Aufbau / Arbeitsweise von Manifests ● Templates, Klassen, Typen, Module ● Facter: Umgebungsparameter ermitteln ● Augeas: Konfigurationen bearbeiten ● Client-Server-Betrieb ● Arbeit mit mehreren Umgebungen ● Links / Hilfen Verwaltung mit facter, puppet und augeas © SpeedPartner GmbH Seite: 2 / 34 GUUG Frühjahrsfachgespräch, 01.03.2012 Über mich ● Stefan Neufeind ● Mit-Geschäftsführer der SpeedPartner GmbH aus Neuss ein Internet-Service-Provider (ISP) ● Individuelle TYPO3-Entwicklungen ● Hosting, Housing, Managed Services ● Domains / Domain-Services ● IPv6, DNSSEC, ... ● Aktive Mitarbeit im Community-Umfeld (PHP/PEAR, TYPO3, Linux) ● Freier Autor für z.B. t3n, iX, Internet World, ... Verwaltung mit facter, puppet und augeas © SpeedPartner GmbH Seite: 3 / 34 GUUG Frühjahrsfachgespräch, 01.03.2012 Aufgabenstellung Alltägliche Administrationsaufgaben für ein (Server-)System Basisinstallation Fehler bei Ausführung von Zugänge „Standard-Aufgaben“? Backup Monitoring Fehlersuche / Einrichtung / Fehlerkorrektur Konzeptfehler? Konfiguration Netzwerk Fehler durch die Systemstatistiken „Sonderlösungen“? Architektur Virtuell? Individuelle Anpassungen Aufgaben RAID? Verwaltung mit facter, puppet und augeas © SpeedPartner GmbH Seite: 4 / 34 GUUG Frühjahrsfachgespräch, 01.03.2012 Aufgabenstellung -

Ruby on Rails™ Tutorial: Learn Web Developments with Rails
ptg8286261 www.it-ebooks.info Praise for Michael Hartl’s Books and Videos on Ruby on RailsTM ‘‘My former company (CD Baby) was one of the first to loudly switch to Ruby on ptg8286261 Rails, and then even more loudly switch back to PHP (Google me to read about the drama). This book by Michael Hartl came so highly recommended that I had to try it, and the Ruby on RailsTM Tutorial is what I used to switch back to Rails again.’’ —From the Foreword by Derek Sivers (sivers.org) Formerly: Founder, CD Baby Currently: Founder, Thoughts Ltd. ‘‘Michael Hartl’s Rails Tutorial book is the #1 (and only, in my opinion) place to start when it comes to books about learning Rails. It’s an amazing piece of work and, unusually, walks you through building a Rails app from start to finish with testing. If you want to read just one book and feel like a Rails master by the end of it, pick the Ruby on RailsTM Tutorial.’’ —Peter Cooper Editor, Ruby Inside www.it-ebooks.info ‘‘Grounded in the real world.’’ —I Programmer (www.i-programmer.info), by Ian Elliot ‘‘The book gives you the theory and practice, while the videos focus on showing you in person how its done. Highly recommended combo.’’ —Antonio Cangiano, Software Engineer, IBM ‘‘The author is clearly an expert at the Ruby language and the Rails framework, but more than that, he is a working software engineer who introduces best practices throughout the text.’’ —Greg Charles, Senior Software Developer, Fairway Technologies ‘‘Overall, these video tutorials should be a great resource for anyone new to Rails.’’ —Michael Morin, ruby.about.com ‘‘Hands-down, I would recommend this book to anyone wanting to get into Ruby on Rails development.’’ —Michael Crump, Microsoft MVP ptg8286261 www.it-ebooks.info RUBY ON RAILSTM TUTORIAL Second Edition ptg8286261 www.it-ebooks.info Visit informit.com/ruby for a complete list of available products. -

Junos® OS Puppet for Junos OS Administration Guide Copyright © 2021 Juniper Networks, Inc
Junos® OS Puppet for Junos OS Administration Guide Published 2021-06-14 ii Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net Juniper Networks, the Juniper Networks logo, Juniper, and Junos are registered trademarks of Juniper Networks, Inc. in the United States and other countries. All other trademarks, service marks, registered marks, or registered service marks are the property of their respective owners. Juniper Networks assumes no responsibility for any inaccuracies in this document. Juniper Networks reserves the right to change, modify, transfer, or otherwise revise this publication without notice. Junos® OS Puppet for Junos OS Administration Guide Copyright © 2021 Juniper Networks, Inc. All rights reserved. The information in this document is current as of the date on the title page. YEAR 2000 NOTICE Juniper Networks hardware and software products are Year 2000 compliant. Junos OS has no known time-related limitations through the year 2038. However, the NTP application is known to have some difficulty in the year 2036. END USER LICENSE AGREEMENT The Juniper Networks product that is the subject of this technical documentation consists of (or is intended for use with) Juniper Networks software. Use of such software is subject to the terms and conditions of the End User License Agreement ("EULA") posted at https://support.juniper.net/support/eula/. By downloading, installing or using such software, you agree to the terms and conditions of that EULA. iii Table of Contents About This -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Ruby Programming
Ruby Programming Wikibooks.org December 1, 2012 On the 28th of April 2012 the contents of the English as well as German Wikibooks and Wikipedia projects were licensed under Creative Commons Attribution-ShareAlike 3.0 Unported license. An URI to this license is given in the list of figures on page 249. If this document is a derived work from the contents of one of these projects and the content was still licensed by the project under this license at the time of derivation this document has to be licensed under the same, a similar or a compatible license, as stated in section 4b of the license. The list of contributors is included in chapter Contributors on page 243. The licenses GPL, LGPL and GFDL are included in chapter Licenses on page 253, since this book and/or parts of it may or may not be licensed under one or more of these licenses, and thus require inclusion of these licenses. The licenses of the figures are given in the list of figures on page 249. This PDF was generated by the LATEX typesetting software. The LATEX source code is included as an attachment (source.7z.txt) in this PDF file. To extract the source from the PDF file, we recommend the use of http://www.pdflabs.com/tools/pdftk-the-pdf-toolkit/ utility or clicking the paper clip attachment symbol on the lower left of your PDF Viewer, selecting Save Attachment. After extracting it from the PDF file you have to rename it to source.7z. To uncompress the resulting archive we recommend the use of http://www.7-zip.org/.