SPECIAL INSERT:WEB SERVICES EDGE CONFERENCE & Expopg. 59
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introduction Overview Digital Technology Center
Introduction Overview Digital Technology Center Supercomputing Institute Programs Supercomputers Research Laboratories Graduate Programs Partnerships Research Scholarship Program Undergraduate Internship Program Researchers and Administration Fellows of the Institute National Advisory Board Administrative Staff Technical Support Staff Committee and Panel Members External Support Conferences Sponsored Symposia Ongoing and Recently Completed Research Projects from January 1, 2002 to March 15, 2003 University of Minnesota–Duluth Campus College of Science and Engineering Department of Chemistry Department of Computer Science Department of Electrical and Computer Engineering Department of Physics School of Medicine #Department of biochemistry and moleculsar biology|region Department of Pharmacology University of Minnesota–Hormel Institute Hormel Institute University of Minnesota–Twin Cities Campus College of Agricultural, Food, and Environmental Sciences Department of Agronomy and Plant Genetics Department of Animal Science Department of Plant Pathology Department of Soil, Water, and Climate College of Biological Sciences Biotechnology Institute Department of Ecology, Evolution, and Behavior Department of Plant Biology College of Biological Sciences and Medical School Department of Biochemistry, Molecular Biology, and Biophysics Department of Genetics, Cell Biology, and Development College of Liberal Arts Department of Economics College of Natural Resources Department of Wood and Paper Science College of Pharmacy College of Pharmacy Department of Medicinal Chemistry Department of Pharmaceutics College of Veterinary Medicine Department of Veterinary Pathobiology Curtis L. Carlson School of Management Department of Finance Department of Operations and Management Science Institute of Technology Department of Aerospace Engineering and Mechanics Department of Astronomy Department of Biomedical Engineering Department of Chemical Engineering and Materials Science Department of Chemistry and Chemical Physics Program Department of Civil Engineering St. -

Corporate Profile of Nihon Unisys, Ltd
Nihon Unisys Group Marketing, Business development and Consulting Infrastructure Services ●Nihon Unisys, Ltd. https://www.unisys.co.jp/e/ ●UNIADEX, Ltd. https://www.uniadex.co.jp/ We coordinate, propose and execute business and ICT services (including We are a global and vendor-agnostic company offering comprehensive Corporate Profile consulting, planning, development, operation and maintenance). services (including consulting, planning, construction, operation and maintenance, facilities) for ICT infrastructure (data center, servers, networks ●UEL Corporation https://www.excel.co.jp/ and devices). We develop 3D CAD/CAM and housing CAD systems as well as business Nihon Unisys, Ltd. solutions and services. ●S&I Co., Ltd. https://sandi.jp/ We provide ICT infrastructure solutions to our clients including consulting,design, ●Cambridge Technology Partners, Ltd. https://en.ctp.co.jp/ construction, operation and maintenance based on virtualization strategy. We provide a wide range of facilitation-driven consulting services from planning for transformation at customers to IT implementation and Systems Services restructuring. ●USOL Vietnam Co., Ltd. https://www.usol-v.com.vn/ AFAS Inc. https://www.afasinc.co.jp/ ● Offshore development center of the Nihon Unisys Group. Our expert professionals in financial business provide the optimal solutions Providing software development services for the Nihon Unisys Group and its for financial institutions. customers in Japan. ●Canal Ventures, Ltd. https://www.canal-v.com/ ●International Systems Development Co., Ltd. https://www.isd.co.jp/ We are a corporate venture capital arm of Nihon Unisys Group. We provide locally based services utilizing latest technology and knowhow in Our mission is to accelerate the digital transformation through Okinawa region. the creation of business ecosystem comprising such players as startups, investors and large companies. -

Creativity – Success – Obscurity
Author Gerry Pickering CREATIVITY – SUCCESS – OBSCURITY UNIVAC, WHAT HAPPENED? A fellow retiree posed the question of what happened. How did the company that invented the computer snatch defeat from the jaws of victory? The question piqued my interest, thus I tried to draw on my 32 years of experiences in the company and the myriad of information available on the Internet to answer the question for myself and hopefully others that may still be interested 60+ years after the invention and delivery of the first computers. Computers plural, as there were more than one computer and more than one organization from which UNIVAC descended. J. Presper Eckert and John Mauchly, located in Philadelphia PA are credited with inventing the first general purpose computer under a contract with the U.S. Army. But our heritage also traces back to a second group of people in St. Paul MN who developed several computers about the same time under contract with the U.S. Navy. This is the story of how these two companies started separately, merged to become one company, how that merged company named UNIVAC (Universal Automatic Computers) grew to become a main rival of IBM (International Business Machines), then how UNIVAC was swallowed by another company to end up in near obscurity compared to IBM and a changing industry. Admittedly it is a biased story, as I observed the industry from my perspective as an employee of UNIVAC. It is also biased in that I personally observed only a fraction of the events as they unfolded within UNIVAC. This story concludes with a detailed account of my work assignments within UNIVAC. -
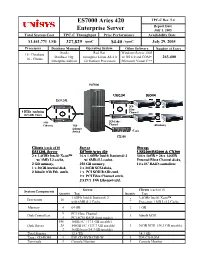
ES7000 Aries 420 Enterprise Server
ES7000 Aries 420 TPC-C Rev. 5.4 Report Date Enterprise Server July 1, 2005 Total System Cost TPC-C Throughput Price Performance Availability Date $1,441,771 USD 327,829 tpmC $4.40 / tpmC July 29, 2005 Processors Database ManagerOperating System Other Software Number of Users Oracle Red Hat Windows Server 2003 16 - Database Database 10g Enterprise Linux AS 4.0 w/ IIS 6.0 and COM+ 263,400 16 - Clients Enterprise Edition for Itanium Processors Microsoft Visual C++ ES7000 USS2200 RS2000 ES3120L 5 2Gb 8 Fibre 8 RTEs emulating Channel 263,400 Users 8 5 1Gb 2Gb Fibre Ethernet 1Gb Channel (Database) Ethernet Switch (Log) CX300 Clients (each of 8) Server Storage ES3120L Server ES7000 Aries 420 USS2200/RS2000 & CX300 2 x 3.4GHz Intel® Xeon™ 16 x 1.6GHz Intel® Itanium® 2 546 x 18GB + 28 x 146GB w/ 1MB L2 cache, w/ 6MB iL3 cache, External Fibre Channel disks, 2 GB memory, 256 GB memory, 10 x FC RAID controllers 1 x 36GB internal disk, 2 x 36GB SCSI disks, 2 Inbuilt 1Gb Eth. cntrls. 1 x PCI SCSI RAID cntrl, 9 x PCI Fibre Channel cntrls, 2 x PCI 1Gb Ethernet cntrl. Clients (each of 8) System Components Server Quantity Type Quantity Type 1.6GHz Intel® Itanium® 2 3.4GHz Intel® Xeon™ Processors 16 2 with 6MB iL3 Cache Processor, 1MB Lvl 2 Cache Memory 4 64 GB 2 1 GB 9 PCI Fibre Channel Disk Controllers 1 Inbuilt SCSI 1 PCI SCSI RAID (boot media) 546 18GB FC (17.1 GB useable) Disk Drives28 146GB FC (133.7 GB useable) 1 36GB SCSI (34.3 GB useable) 2 36GB boot (34.3 GB useable) Total Storage 12.8 TB 34.3 GB Tape / CD-ROM1 IDE CD/DVD/CDR-W1 IDE CD-ROM Terminals1 Console Monitor1 Console Monitor ES7000 Aries 420 TPC-C Rev. -

Building the Foundation Forthe Real-Time Infrastructure
Building the Foundation for the Real-Time Infrastructure 1 Your entire business rides on the technology infrastructure you choose. So, if you’re looking to align your business’ IT operations more closely with your strategic business goals, here’s an aggressive investment opportunity that can help you start producing real, measurable results. This Executive Brief provides an overview of specific business benefits that you can expect from a Unisys standards-based, enterprise- computing environment. We help you secure your business operations so you can focus on opportunities and gain the visibility to see your business more clearly – ahead of decision points, investments, and risk. Secure Business Operations. It’s More Than You Think. Having a secure organization, meaning the ability to manage risk, is of paramount importance for most executives. And, most IT vendors offer some sort of security promise to their customers. Secure organizations are: • Confident in managing their enterprise • Trusted by their stakeholders • Positioned to enable their clients to succeed • Accustomed to exceptional performance • Able to control costs • Excellent at managing risk • Positioned for long-term competitive advantage Unisys services and technology are the foundation for the solutions you need to plan, build, run, and monitor business operations where confidence, trust, reliability, and managing risk are critical components. Gain Visibility into Your Enterprise Unisys 3D Visible Enterprise (3D-VE) is our vision for what an enterprise can become – a new way of seeing the inner workings of an organization through a virtual model of the enterprise. The result is an understanding of the cause-and-effect relationships between business vision, business operations, and the IT systems that support them – allowing you to see the results of your business decisions before you make them. -

Sperry Rand Third-Generation Computers
UNISYS: HISTORY: • 1873 E. Remington & Sons introduces first commercially viable typewriter. • 1886 American Arithmometer Co. founded to manufacture and sell first commercially viable adding and listing machine, invented by William Seward Burroughs. • 1905 American Arithmometer renamed Burroughs Adding Machine Co. • 1909 Remington Typewriter Co. introduces first "noiseless" typewriter. • 1910 Sperry Gyroscope Co. founded to manufacture and sell navigational equipment. • 1911 Burroughs introduces first adding-subtracting machine. • 1923 Burroughs introduces direct multiplication billing machine. • 1925 Burroughs introduces first portable adding machine, weighing 20 pounds. Remington Typewriter introduces America's first electric typewriter. • 1927 Remington Typewriter and Rand Kardex merge to form Remington Rand. • 1928 Burroughs ships its one millionth adding machine. • 1930 Working closely with Lt. James Doolittle, Sperry Gyroscope engineers developed the artificial horizon and the aircraft directional gyro – which quickly found their way aboard airmail planes and the aircraft of the fledgling commercial airlines. TWA was the first commercial buyer of these two products. • 1933 Sperry Corp. formed. • 1946 ENIAC, the world's first large-scale, general-purpose digital computer, developed at the University of Pennsylvania by J. Presper Eckert and John Mauchly. • 1949 Remington Rand produces 409, the worlds first business computer. The 409 was later sold as the Univac 60 and 120 and was the first computer used by the Internal Revenue Service and the first computer installed in Japan. • 1950 Remington Rand acquires Eckert-Mauchly Computer Corp. 1951 Remington Rand delivers UNIVAC computer to the U.S. Census Bureau. • 1952 UNIVAC makes history by predicting the election of Dwight D. Eisenhower as U.S. president before polls close. -

Breakthrough: Coopervision Establishes Clear Vision for Future
case study Breakthrough: CooperVision Establishes Clear Vision for Future. Imagine It Business Challenge: IT Infrastructure When CooperVision acquired Ocular Sciences, Inc. in Experiences Growing Pains 2004, the company became the world’s third largest CooperVision has been helping contact lens wearers “see contact lens company. The acquisition dramatically beyond the ordinary” since 1958. The company has long increased the demands on CooperVision’s IT been recognized as a market leader for toric lenses — infrastructure and staff. manufacturing premium-quality soft lenses that help people with astigmatism and spherical vision conditions see more Done clearly. With the acquisition of Ocular Sciences, Inc. in Thanks to the new 64-bit solution from Unisys, 2004, CooperVision became the third largest contact lens Microsoft® and Intel®, CooperVision has realized company in the world. Based in upstate New York, profound performance improvements — enabling the CooperVision now maintains a network of facilities in 14 company to maintain its global data center model countries — and plans to grow even more. without incurring additional subsidiary site costs. Of course, with rapid growth come major challenges for any company’s IT team. CooperVision is no different. In 2004, Results: Managing Growth and the IT team was supporting 550 concurrent users in three Enabling Future Agility countries and about 14,000 orders per day. But by 2006, the firm expects to have about 1,550 concurrent users in CooperVision deployed a scale-up solution using Unisys 14 countries — and to process about 50,000 orders per day. ES7000 servers with Intel Itanium® 2-based processors, Microsoft Windows® Server 2003, Datacenter Edition, and Clearly, enhancing the company’s IT infrastructure was Microsoft SQL Server 2000. -

CISER: Cornell Researchers Team Itanium® 2-Based Unisys ES7000* Server with SAS* 9 and Windows* Server 2003 to Boost Performance and Streamline Data Center
Intel® Business Center Case Study Business Intelligence CISER CISER: Cornell Researchers Team Itanium® 2-Based Unisys ES7000* Server with SAS* 9 and Windows* Server 2003 to Boost Performance and Streamline Data Center SOLUTION SUMMARY Challenge The Cornell Institute for Social and Economic Research (CISER) urgently needed to boost performance for processing- and memory-intensive SAS* applications. CISER needed to acquire the resources to run 64-bit SAS 9 when it became available for the Windows* Server 2003 operating system. Yet, more than 600 researchers still needed broad-ranging 32-bit support. CISER needed to find an economical way to manage both 64-bit and 32-bit user communities demanding more power. Solution Rather than continue to add 2- and 4-way servers, CISER decided to purchase a Unisys ES7000* Enterprise Server containing eight Intel® Itanium® 2 processors and 16 Intel Xeon™ processors MP. This mainframe-class machine provides tremendous processor and memory scalability in the familiar Windows environment. CISER will be able to host 32-bit and 64-bit applications in the same system while consolidating its server holdings from 12 to 1. Business value By moving to the Unisys ES7000, CISER will boost the performance of some particularly demanding SAS applications by as much as 70 percent. The additional processing power allows researchers to crunch through demanding data analyses much faster than before and to work with much larger data sets to answer questions they couldn’t even ask before. Faster answers lead to more work accomplished in a given grant period and an improved chance of renewing grant funding. -

Unisys Takes Lead in Integrating Dual-Core Intel® Itanium® 2 Processor Into Enterprise Server Offerings
News Release Contacts: John Schneidawind, 215-986-2472 [email protected] Brian Daly, 215-986-2214 [email protected] Janet Martin, 650-228-5175 [email protected] Unisys Takes Lead in Integrating Dual-Core Intel® Itanium® 2 Processor into Enterprise Server Offerings New Unisys ES7000/one servers based on Intel’s new dual-core processor accelerate performance for heavy-duty business intelligence and transaction processing applications San Francisco, Calif., July 18, 2006 – Unisys Corporation (NYSE: UIS) today announced another building block in the development of its recently unveiled next-generation server architecture, making the new Dual-Core Intel® Itanium® 2 processor 9000 Series – better known as “Montecito” – the engine for new models of its ES7000/one Enterprise Server. Unisys was among the first system providers to announce support for the new Itanium 2 processor 9000 series and played a major role in Intel’s announcement here today. Unisys intends to make ES7000/one servers based on the Montecito platform available in late August. Entry-level configurations of new Itanium 2 models of the ES7000/one are priced from US$45,000. The ES7000/one server powered by the new Dual-Core Intel Itanium 2 processors has demonstrated the highest performance of any 16-processor and the lowest price/performance of any non-clustered server in the 3000 GB TPC-H benchmark, widely recognized as a standard measure of system performance for decision support and business Page 1 of 3 intelligence in commercial enterprise computing. In performance -

Capacity and Scaling of Microsoft Terminal Server on the Unisys
white paper Capacity and Scaling of Microsoft Terminal Server on the Unisys ES7000/600 Unisys Systems & Technology Modeling and Measurement This technical white paper has been written for IT professionals who are responsible for preparing and deploying a Unisys ES7000/600 server configured as a Microsoft Terminal Server. The paper reviews the scalability benchmark results of a 4- and 8-processor ES7000/600 server configured as a Terminal Server, and discusses specific results about server resource usage and user response times. 2 Table of Contents Executive Overview 5 Introduction 6 Test Environment 6 Test Components and Tools 6 Hardware 7 Software 8 Remote Desktop Client 8 Simulated User Scripts 8 Microsoft Office 9 Mail and Web Service 9 Print Service 9 Analysis Support Tools 9 Operating System 9 Methodology 9 Test Procedure 10 Terminal Server Capacity 10 X64 versus x86 10 Scaling Terminal Server 11 CPU Usage and Hyperthreading 11 Response Time 12 System Characteristics 13 Resource Requirements 13 Memory Usage 13 Disk Usage 15 Network Usage 16 3 Settings, Tunings, Best Practices 16 Office Configuration Settings 17 Registry Settings 17 ConnManagerPoll 17 NoRecentDocsHistory 18 Best Practices 18 Conclusion 18 Additional Online Resources 19 List of Figures Figure 1. Test Configuration 6 List of Tables Table 1. Benefits of a Terminal Server 5 Table 2. Unisys ES7000/600 7 Table 3. Supporting Systems 8 Table 4. Workload Descriptions 8 Table 5. Theoretical Limits for Knowledge Worker Sessions 10 Table 6. Office Options 17 List of Charts Chart 1. Terminal Server Scaling 11 Chart 2. Response Time 12 Chart 3. User Cycle Time 12 Chart 4. -

M. Craig Weaver Society for Worldwide Interbank Financial
M. Craig Weaver 106 Lakewood Drive Coatesville, PA 19320 (484) 712-0479 [email protected] S UMMARY Software Engineering professional with extensive experience in the design and development of system networking software and layered network architectures. A team-oriented communicator with the ability to solve complex problems using strong analytical skills. Effectively analyzed, designed and developed global networking software products on platforms ranging from micro, server, and mid-range to mainframe computers. Core strengths: • Software design, specification, and programming • Team Management • Software Quality Assurance Testing • Network troubleshooting and problem solution • Software problem analysis and solution • Burroughs Network Architecture expert • Complex protocol design and implementation • Networking and layered network architectures T E C H N I C A L S KILLS LANGUAGES JavaScript, C++, C, ALGOL, FORTRAN, HTML, Intel Assembler, Pascal, and others. PLATFORMS UNIX Systems; Microsoft Windows based systems (WINNT/WIN2000/WINXP); Unisys A-Series; Unisys V-Series; Unisys Clearpath; Unisys ES7000; Burroughs Large Systems; Burroughs Medium systems; Intel Processor based communications processor cards; Burroughs CP9500/B900. P ROFESSIONAL E XPERIENCE Society for Worldwide Interbank Financial Telecommunication (SWIFT) 2008 – 2014 International Member Owned Banking Cooperative Manassas, Virginia SENIO R SOFTWARE ENG INEER – CONTRACT FIN Renewal Project – Moving the SWIFT financial application software from Unisys machines (ALGOL) to HP UNIX machines (C++) • Tested ALTOS conversion tool. Created test cases from canonical ALGOL forms, converting them using ALTOS, then comparing the ALGOL and C++ test results. Diagnosed discrepancies and either designed solutions or required changes to the tool. • Converted Unisys ALGOL into UNIX C++ code. Tested, debugged and maintained the converted C++ code. -

Corporate Profile
Corporate Profile Nihon Unisys, Ltd. Corporate Headquarters 1-1-1 Toyosu, Koto-ku, Tokyo, 135-8560 Japan Tel : +81-3-5546-4111 (main switchboard) http://www.unisys.co.jp/ Nihon Unisys, Ltd. Copyright © 2015 Nihon Unisys, Ltd. All rights reserved. 010901004-5 チ1510 Corporate Data Location of Corporate Headquarters, Regional Headquarters and Offices History of Nihon Unisys Group Company Name Nihon Unisys, Ltd. ■Corporate Headquarters ■Regional Offices 1955 Installed Japan's first computer, the "UNIVAC-120," at the Tokyo Stock 2005 Established G&U System Service, Ltd. jointly with Gunze. Exchange and Nomura Securities Co., Ltd. 50 years have passed since UNIVAC 120,the first commercial computer 1-1-1 Toyosu, Established March 29, 1958 Hokkaido Regional Office 1958 Nippon Remington Univac Kaisha, Ltd. founded(. later Nippon Univac) was installed in Japan. Koto-ku, Tokyo 135-8560 8・3 Square-Kita Bldg.7F, 2006 Nihon Unisys launched sales of mission-critical ES7000/one server series. Representative Shigeru Kurokawa, President & CEO 1962 Introduced "B5000", the world's first computer to combine hardware/ Japan 3-32 Kitahachijyo-Nishi, software in its design. Established USOL Vietnam Corporation in Hanoi as our overseas software development subsidiary. Paid-in Capital Approx. 5.5 billion yen Tel : +81-3-5546-4111 Kita-ku, Sapporo-shi 060-0808 1964 First successful attempt at online real-time processing in Japan. 2007 Announced evaluation framework based on the practice standard ■ Tel : +81-11-558-1111 1967 Launched Japan's first online banking process. Annual Sales 269.2billion yen(consolidated net Regional Headquarters supporting Japanese SOX regulations. 1971 Nippon Univac Kaisha, Ltd.