M. Craig Weaver Society for Worldwide Interbank Financial
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Jül Spez 0467.Pdf
EMULATING SIMULA IN TURBO PASCAL by Morton John Canty EMULATING SIMULA IN TURBO PASCAL M. J. Canty 1. lntroduction Although the computer language SIMULA /1,2/ is now over 20 years old it remains an excellent general purpose programming tool as well as a popular and powerfuf simulation language, the purpose for which it was originally developed. SIMULA is an extension of ALGOL 60, which it contains as a true subset, and its advanced concepts have served as a model for modern object-oriented languages such as SMALLTALK. The properties which make SIMULA especially suitable for simulation tasks are 1. a hierarchic cfass concept with inheritance, 2. sophisticated list handfing facilities and 3. concurrent programming capability. Of these three, the most essential property to allow for programming of discrete time simulation tasks is the third one, concurrent programming. By this is meant the ability to sustain parallel autonomous entities (called processes or co-routines) in memory. Allowing an arbitrary number of such processes to interact with each other along a time axis forms the basis of SIMULA's model for discrete time simulation. Although virtually all major programming languages have been implemented in one form or another on personal computers, SIMULA is a notable exception. Perhaps the main reason for this is that, while enjoying great popularity in Europe, SIMULA is not as well known on the North American continent. Pascal belongs to the same Afgol famify as SIMULA, and the dialect Turbo Pascal of the firm Borland Interna tional has become one bf the most wide spread high-levef languages for MS-DOS personal computers. -

Introduction Overview Digital Technology Center
Introduction Overview Digital Technology Center Supercomputing Institute Programs Supercomputers Research Laboratories Graduate Programs Partnerships Research Scholarship Program Undergraduate Internship Program Researchers and Administration Fellows of the Institute National Advisory Board Administrative Staff Technical Support Staff Committee and Panel Members External Support Conferences Sponsored Symposia Ongoing and Recently Completed Research Projects from January 1, 2002 to March 15, 2003 University of Minnesota–Duluth Campus College of Science and Engineering Department of Chemistry Department of Computer Science Department of Electrical and Computer Engineering Department of Physics School of Medicine #Department of biochemistry and moleculsar biology|region Department of Pharmacology University of Minnesota–Hormel Institute Hormel Institute University of Minnesota–Twin Cities Campus College of Agricultural, Food, and Environmental Sciences Department of Agronomy and Plant Genetics Department of Animal Science Department of Plant Pathology Department of Soil, Water, and Climate College of Biological Sciences Biotechnology Institute Department of Ecology, Evolution, and Behavior Department of Plant Biology College of Biological Sciences and Medical School Department of Biochemistry, Molecular Biology, and Biophysics Department of Genetics, Cell Biology, and Development College of Liberal Arts Department of Economics College of Natural Resources Department of Wood and Paper Science College of Pharmacy College of Pharmacy Department of Medicinal Chemistry Department of Pharmaceutics College of Veterinary Medicine Department of Veterinary Pathobiology Curtis L. Carlson School of Management Department of Finance Department of Operations and Management Science Institute of Technology Department of Aerospace Engineering and Mechanics Department of Astronomy Department of Biomedical Engineering Department of Chemical Engineering and Materials Science Department of Chemistry and Chemical Physics Program Department of Civil Engineering St. -

A Domain-Specific Embedded Language for Probabilistic
AN ABSTRACT OF THE THESIS OF Steven Kollmansberger for the degree of Master of Science in Computer Science presented on December 12, 2005. Title: A Domain-Specific Embedded Language for Probabilistic Programming Abstract approved: Martin Erwig Functional programming is concerned with referential transparency, that is, given a certain function and its parameter, that the result will always be the same. However, it seems that this is violated in applications involving uncertainty, such as rolling a dice. This thesis defines the background of probabilistic programming and domain-specific languages, and builds on these ideas to construct a domain- specific embedded language (DSEL) for probabilistic programming in a purely functional language. This DSEL is then applied in a real-world setting to develop an application in use by the Center for Gene Research at Oregon State University. The process and results of this development are discussed. c Copyright by Steven Kollmansberger December 12, 2005 All Rights Reserved A Domain-Specific Embedded Language for Probabilistic Programming by Steven Kollmansberger A THESIS submitted to Oregon State University in partial fulfillment of the requirements for the degree of Master of Science Presented December 12, 2005 Commencement June 2006 Master of Science thesis of Steven Kollmansberger presented on December 12, 2005 APPROVED: Major Professor, representing Computer Science Director of the School of Electrical Engineering and Computer Science Dean of the Graduate School I understand that my thesis will become part of the permanent collection of Ore- gon State University libraries. My signature below authorizes release of my thesis to any reader upon request. Steven Kollmansberger, Author ACKNOWLEDGMENTS This thesis would not be possible without the ideas, drive and commitment of many people. -

Corporate Profile of Nihon Unisys, Ltd
Nihon Unisys Group Marketing, Business development and Consulting Infrastructure Services ●Nihon Unisys, Ltd. https://www.unisys.co.jp/e/ ●UNIADEX, Ltd. https://www.uniadex.co.jp/ We coordinate, propose and execute business and ICT services (including We are a global and vendor-agnostic company offering comprehensive Corporate Profile consulting, planning, development, operation and maintenance). services (including consulting, planning, construction, operation and maintenance, facilities) for ICT infrastructure (data center, servers, networks ●UEL Corporation https://www.excel.co.jp/ and devices). We develop 3D CAD/CAM and housing CAD systems as well as business Nihon Unisys, Ltd. solutions and services. ●S&I Co., Ltd. https://sandi.jp/ We provide ICT infrastructure solutions to our clients including consulting,design, ●Cambridge Technology Partners, Ltd. https://en.ctp.co.jp/ construction, operation and maintenance based on virtualization strategy. We provide a wide range of facilitation-driven consulting services from planning for transformation at customers to IT implementation and Systems Services restructuring. ●USOL Vietnam Co., Ltd. https://www.usol-v.com.vn/ AFAS Inc. https://www.afasinc.co.jp/ ● Offshore development center of the Nihon Unisys Group. Our expert professionals in financial business provide the optimal solutions Providing software development services for the Nihon Unisys Group and its for financial institutions. customers in Japan. ●Canal Ventures, Ltd. https://www.canal-v.com/ ●International Systems Development Co., Ltd. https://www.isd.co.jp/ We are a corporate venture capital arm of Nihon Unisys Group. We provide locally based services utilizing latest technology and knowhow in Our mission is to accelerate the digital transformation through Okinawa region. the creation of business ecosystem comprising such players as startups, investors and large companies. -

The Protection of Information in Computer Systems
The Protection of Information in Computer Systems JEROME H. SALTZER, SENIOR MEMBER, IEEE, AND MICHAEL D. SCHROEDER, MEMBER, IEEE Invited Paper Abstract - This tutorial paper explores the mechanics of Confinement protecting computer-stored information from unauthorized Allowing a borrowed program to have access to data, use or modification. It concentrates on those architectural while ensuring that the program cannot release the structures--whether hardware or software--that are information. necessary to support information protection. The paper Descriptor develops in three main sections. Section I describes A protected value which is (or leads to) the physical desired functions, design principles, and examples of address of some protected object. elementary protection and authentication mechanisms. Any Discretionary reader familiar with computers should find the first section (In contrast with nondiscretionary.) Controls on access to be reasonably accessible. Section II requires some to an object that may be changed by the creator of the familiarity with descriptor-based computer architecture. It object. examines in depth the principles of modern protection Domain architectures and the relation between capability systems The set of objects that currently may be directly and access control list systems, and ends with a brief accessed by a principal. analysis of protected subsystems and protected objects. Encipherment The reader who is dismayed by either the prerequisites or The (usually) reversible scrambling of data according the level of detail in the second section may wish to skip to to a secret transformation key, so as to make it safe for Section III, which reviews the state of the art and current transmission or storage in a physically unprotected research projects and provides suggestions for further environment. -

TCD-SCSS-T.20121208.032.Pdf
AccessionIndex: TCD-SCSS-T.20121208.032 Accession Date: 8-Dec-2012 Accession By: Prof.J.G.Byrne Object name: Burroughs 1714 Vintage: c.1972 Synopsis: Commercial zero-instruction-set computer used by the Dept.Computer Science from 1973-1979. Just two prototyping boards survive. Description: The Burroughs 1714 was one of their B1700 family, introduced in 1972 to compete with IBM's System/3. The original research for the B1700 series, initially codenamed the Proper Language Processor or Program Language Processor (PLP) was done at the Burroughs Pasadena plant. The family were known as the Burroughs Small Systems, as distinct from the Burroughs Medium Systems (B2000, etc) and the Burroughs Large Systems (B5000, etc). All the Burroughs machines had high-level language architectures. The large were ALGOL machines, the medium COBOL machines, but the small were universal machines. The principal designer of the B1700 family was Wayne T. Wilner. He designed the architecture as a zero-instruction-set computer, an attempt to bridge the inefficient semantic gap between the ideal solution to a particular programming problem and the real physical hardware. The B1700 architecture executed idealized virtual machines for any language from virtual memory. It achieved this feat by microprogramming, see the microinstruction set further below. The Burroughs MCP (Master Control Program) would schedule a particular job to run, then preload the interpreter for whatever language was required into a writeable control store, allowing the machine to emulate the desired virtual machine. The hardware was optimised for this. It had bit-addressable memory, a variable-width ALU, could OR in data from a register into the instruction register (for very efficient instruction parsing), and the output of the ALU was directly addressable as X+Y or X-Y read-only registers. -

Creativity – Success – Obscurity
Author Gerry Pickering CREATIVITY – SUCCESS – OBSCURITY UNIVAC, WHAT HAPPENED? A fellow retiree posed the question of what happened. How did the company that invented the computer snatch defeat from the jaws of victory? The question piqued my interest, thus I tried to draw on my 32 years of experiences in the company and the myriad of information available on the Internet to answer the question for myself and hopefully others that may still be interested 60+ years after the invention and delivery of the first computers. Computers plural, as there were more than one computer and more than one organization from which UNIVAC descended. J. Presper Eckert and John Mauchly, located in Philadelphia PA are credited with inventing the first general purpose computer under a contract with the U.S. Army. But our heritage also traces back to a second group of people in St. Paul MN who developed several computers about the same time under contract with the U.S. Navy. This is the story of how these two companies started separately, merged to become one company, how that merged company named UNIVAC (Universal Automatic Computers) grew to become a main rival of IBM (International Business Machines), then how UNIVAC was swallowed by another company to end up in near obscurity compared to IBM and a changing industry. Admittedly it is a biased story, as I observed the industry from my perspective as an employee of UNIVAC. It is also biased in that I personally observed only a fraction of the events as they unfolded within UNIVAC. This story concludes with a detailed account of my work assignments within UNIVAC. -

Harmless Advice∗
Harmless Advice ∗ Daniel S. Dantas David Walker Princeton University Princeton University [email protected] [email protected] Abstract number of calls to each method: The what in this case is the com- when This paper defines an object-oriented language with harmless putation that does the recording and the is the instant of time aspect-oriented advice. A piece of harmless advice is a compu- just prior to execution of each method body. In aspect-oriented ter- what advice tation that, like ordinary aspect-oriented advice, executes when minology, the specification of to do is called and the when pointcut control reaches a designated control-flow point. However, unlike specification of to do it is called a . A collection of ordinary advice, harmless advice is designed to obey a weak non- pointcuts and advice organized to perform a coherent task is called aspect interference property. Harmless advice may change the termination an . behavior of computations and use I/O, but it does not otherwise in- Many within the AOP community adhere to the tenet that as- oblivious fluence the final result of the mainline code. The benefit of harmless pects are most effective when the code they advise is to advice is that it facilitates local reasoning about program behavior. their presence [11]. In other words, aspects are effective when a More specifically, programmers may ignore harmless advice when programmer is not required to annotate the advised code (hence- mainline code reasoning about the partial correctness properties of their programs. forth, the ) in any particular way. When aspect- In addition, programmers may add new pieces of harmless advice oriented languages are oblivious, all control over when advice to pre-existing programs in typical “after-the-fact” aspect-oriented is applied rests with the aspect programmer as opposed to the style without fear they will break important data invariants used by mainline programmer. -
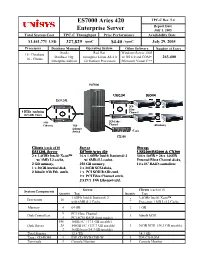
ES7000 Aries 420 Enterprise Server
ES7000 Aries 420 TPC-C Rev. 5.4 Report Date Enterprise Server July 1, 2005 Total System Cost TPC-C Throughput Price Performance Availability Date $1,441,771 USD 327,829 tpmC $4.40 / tpmC July 29, 2005 Processors Database ManagerOperating System Other Software Number of Users Oracle Red Hat Windows Server 2003 16 - Database Database 10g Enterprise Linux AS 4.0 w/ IIS 6.0 and COM+ 263,400 16 - Clients Enterprise Edition for Itanium Processors Microsoft Visual C++ ES7000 USS2200 RS2000 ES3120L 5 2Gb 8 Fibre 8 RTEs emulating Channel 263,400 Users 8 5 1Gb 2Gb Fibre Ethernet 1Gb Channel (Database) Ethernet Switch (Log) CX300 Clients (each of 8) Server Storage ES3120L Server ES7000 Aries 420 USS2200/RS2000 & CX300 2 x 3.4GHz Intel® Xeon™ 16 x 1.6GHz Intel® Itanium® 2 546 x 18GB + 28 x 146GB w/ 1MB L2 cache, w/ 6MB iL3 cache, External Fibre Channel disks, 2 GB memory, 256 GB memory, 10 x FC RAID controllers 1 x 36GB internal disk, 2 x 36GB SCSI disks, 2 Inbuilt 1Gb Eth. cntrls. 1 x PCI SCSI RAID cntrl, 9 x PCI Fibre Channel cntrls, 2 x PCI 1Gb Ethernet cntrl. Clients (each of 8) System Components Server Quantity Type Quantity Type 1.6GHz Intel® Itanium® 2 3.4GHz Intel® Xeon™ Processors 16 2 with 6MB iL3 Cache Processor, 1MB Lvl 2 Cache Memory 4 64 GB 2 1 GB 9 PCI Fibre Channel Disk Controllers 1 Inbuilt SCSI 1 PCI SCSI RAID (boot media) 546 18GB FC (17.1 GB useable) Disk Drives28 146GB FC (133.7 GB useable) 1 36GB SCSI (34.3 GB useable) 2 36GB boot (34.3 GB useable) Total Storage 12.8 TB 34.3 GB Tape / CD-ROM1 IDE CD/DVD/CDR-W1 IDE CD-ROM Terminals1 Console Monitor1 Console Monitor ES7000 Aries 420 TPC-C Rev. -

Building the Foundation Forthe Real-Time Infrastructure
Building the Foundation for the Real-Time Infrastructure 1 Your entire business rides on the technology infrastructure you choose. So, if you’re looking to align your business’ IT operations more closely with your strategic business goals, here’s an aggressive investment opportunity that can help you start producing real, measurable results. This Executive Brief provides an overview of specific business benefits that you can expect from a Unisys standards-based, enterprise- computing environment. We help you secure your business operations so you can focus on opportunities and gain the visibility to see your business more clearly – ahead of decision points, investments, and risk. Secure Business Operations. It’s More Than You Think. Having a secure organization, meaning the ability to manage risk, is of paramount importance for most executives. And, most IT vendors offer some sort of security promise to their customers. Secure organizations are: • Confident in managing their enterprise • Trusted by their stakeholders • Positioned to enable their clients to succeed • Accustomed to exceptional performance • Able to control costs • Excellent at managing risk • Positioned for long-term competitive advantage Unisys services and technology are the foundation for the solutions you need to plan, build, run, and monitor business operations where confidence, trust, reliability, and managing risk are critical components. Gain Visibility into Your Enterprise Unisys 3D Visible Enterprise (3D-VE) is our vision for what an enterprise can become – a new way of seeing the inner workings of an organization through a virtual model of the enterprise. The result is an understanding of the cause-and-effect relationships between business vision, business operations, and the IT systems that support them – allowing you to see the results of your business decisions before you make them. -

Poker, a Process-Interaction Simulator and Controller for Use in Collaborative Simulation
POKer, a Process-Interaction Simulator and Controller for use in Collaborative Simulation Andriy Levytskyy, Eugene J.H. Kerckhoffs Delft University of Technology Faculty of Information Technology and Systems Mediamatica Department Zuidplantsoen 4, 2628 BZ Delft, The Netherlands e-mail: [email protected] and a subset of it, a process interaction world-view Keywords [20], which is of particular interest to us. This world- Discrete-Event simulation, Process-Interaction view gained its popularity due to the easiness of world-view, operational semantics, scripting mapping real-world processes into this formalism, languages, Python. and easiness of comprehending the essence of the process by a human. The above, as well as special application Abstract requirements for the simulation system we seek, In this paper we present the ideas and inspired us to develop our own special-purpose implementation of a small process-interaction kernel simulation software while trying to preserve its and cover its evolution from operational semantics connection to the formal background. In this paper of process-oriented simulation languages to the we present the ideas and implementation of a small current state of the kernel as (simulation) core of a process-interaction kernel and cover its evolution collaborative environment controller. from operational semantics of process oriented simulation languages to the current state of the kernel as (simulation) core of a collaborative 1. Introduction environment controller. Simulation as problem-solving methodology has been widely adopted in many practical domains. 2. View on the environment Users are free to select from a number of available general-purpose simulation software [14, 4] or, in 2.1. -

Sperry Rand Third-Generation Computers
UNISYS: HISTORY: • 1873 E. Remington & Sons introduces first commercially viable typewriter. • 1886 American Arithmometer Co. founded to manufacture and sell first commercially viable adding and listing machine, invented by William Seward Burroughs. • 1905 American Arithmometer renamed Burroughs Adding Machine Co. • 1909 Remington Typewriter Co. introduces first "noiseless" typewriter. • 1910 Sperry Gyroscope Co. founded to manufacture and sell navigational equipment. • 1911 Burroughs introduces first adding-subtracting machine. • 1923 Burroughs introduces direct multiplication billing machine. • 1925 Burroughs introduces first portable adding machine, weighing 20 pounds. Remington Typewriter introduces America's first electric typewriter. • 1927 Remington Typewriter and Rand Kardex merge to form Remington Rand. • 1928 Burroughs ships its one millionth adding machine. • 1930 Working closely with Lt. James Doolittle, Sperry Gyroscope engineers developed the artificial horizon and the aircraft directional gyro – which quickly found their way aboard airmail planes and the aircraft of the fledgling commercial airlines. TWA was the first commercial buyer of these two products. • 1933 Sperry Corp. formed. • 1946 ENIAC, the world's first large-scale, general-purpose digital computer, developed at the University of Pennsylvania by J. Presper Eckert and John Mauchly. • 1949 Remington Rand produces 409, the worlds first business computer. The 409 was later sold as the Univac 60 and 120 and was the first computer used by the Internal Revenue Service and the first computer installed in Japan. • 1950 Remington Rand acquires Eckert-Mauchly Computer Corp. 1951 Remington Rand delivers UNIVAC computer to the U.S. Census Bureau. • 1952 UNIVAC makes history by predicting the election of Dwight D. Eisenhower as U.S. president before polls close.