Polynomial Interpolation 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Simpson's Rule
Simpson's rule In numerical analysis, Simpson's rule is a method for numerical integration, the numerical approximation of definite integrals. Specifically, it is the following approximation for equally spaced subdivisions (where is even): (General Form) , where and . Simpson's rule also corresponds to the three-point Newton-Cotes quadrature rule. Simpson's rule can be derived by In English, the method is credited to the mathematician Thomas Simpson (1710–1761) of Leicestershire, England. However, approximating the integrand f (x) (in Johannes Kepler used similar formulas over 100 years prior, and for this reason the method is sometimes called Kepler's blue) by the quadratic interpolant P rule , or Keplersche Fassregel (Kepler's barrel rule) in German. (x) (in red) . Contents Quadratic interpolation Averaging the midpoint and the trapezoidal rules Undetermined coefficients Error Composite Simpson's rule An animation showing how Simpson's 3/8 rule Simpson's rule approximation Composite Simpson's 3/8 rule improves with more strips. Alternative extended Simpson's rule Simpson's rules in the case of narrow peaks Composite Simpson's rule for irregularly spaced data See also Notes References External links Quadratic interpolation One derivation replaces the integrand by the quadratic polynomial (i.e. parabola) which takes the same values as at the end points a and b and the midpoint m = ( a + b) / 2. One can use Lagrange polynomial interpolation to find an expression for this polynomial, Using integration by substitution one can show that [1] Introducing the step size this is also commonly written as Because of the factor Simpson's rule is also referred to as Simpson's 1/3 rule (see below for generalization). -

Elementary Numerical Methods and Computing with Python
Elementary Numerical Methods and computing with Python Steven Pav1 Mark McClure2 April 14, 2016 1Portions Copyright c 2004-2006 Steven E. Pav. Permission is granted to copy, dis- tribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. 2Copyright c 2016 Mark McClure. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Ver- sion 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled ”GNU Free Documentation License”. 2 Contents Preface 7 1 Introduction 9 1.1 Examples ............................... 9 1.2 Iteration ................................ 11 1.3 Topics ................................. 12 2 Some mathematical preliminaries 15 2.1 Series ................................. 15 2.1.1 Geometric series ....................... 15 2.1.2 The integral test ....................... 17 2.1.3 Alternating Series ...................... 20 2.1.4 Taylor’s Theorem ....................... 21 Exercises .................................. 25 3 Computer arithmetic 27 3.1 Strange arithmetic .......................... 27 3.2 Error .................................. 28 3.3 Computer numbers .......................... 29 3.3.1 Types of numbers ...................... 29 3.3.2 Floating point numbers ................... 30 3.3.3 Distribution of computer numbers ............. 31 3.3.4 Exploring numbers with Python .............. 32 3.4 Loss of Significance .......................... 33 Exercises .................................. 36 4 Finding Roots 37 4.1 Bisection ............................... 38 4.1.1 Modifications ........................ -

Approximation of Finite Population Totals Using Lagrange Polynomial
Open Journal of Statistics, 2017, 7, 689-701 http://www.scirp.org/journal/ojs ISSN Online: 2161-7198 ISSN Print: 2161-718X Approximation of Finite Population Totals Using Lagrange Polynomial Lamin Kabareh1*, Thomas Mageto2, Benjamin Muema2 1Pan African University Institute for Basic Sciences, Technology and Innovation (PAUSTI), Nairobi, Kenya 2Jomo Kenyatta University of Agriculture and Technology, Nairobi, Kenya How to cite this paper: Kabareh, L., Mage- Abstract to, T. and Muema, B. (2017) Approximation of Finite Population Totals Using Lagrange Approximation of finite population totals in the presence of auxiliary infor- Polynomial. Open Journal of Statistics, 7, 689- mation is considered. A polynomial based on Lagrange polynomial is pro- 701. posed. Like the local polynomial regression, Horvitz Thompson and ratio es- https://doi.org/10.4236/ojs.2017.74048 timators, this approximation technique is based on annual population total in Received: July 9, 2017 order to fit in the best approximating polynomial within a given period of Accepted: August 15, 2017 time (years) in this study. This proposed technique has shown to be unbiased Published: August 18, 2017 under a linear polynomial. The use of real data indicated that the polynomial Copyright © 2017 by authors and is efficient and can approximate properly even when the data is unevenly Scientific Research Publishing Inc. spaced. This work is licensed under the Creative Commons Attribution International Keywords License (CC BY 4.0). http://creativecommons.org/licenses/by/4.0/ Lagrange Polynomial, Approximation, Finite Population Total, Open Access Auxiliary Information, Local Polynomial Regression, Horvitz Thompson and Ratio Estimator 1. Introduction This study is using an approximation technique to approximate the finite popu- lation total called the Lagrange polynomial that doesn’t require any selection of bandwidth as in the case of local polynomial regression estimator. -

Language Program for Lagrange's Interpolation
International Journal of Emerging Trends & Technology in Computer Science (IJETTCS) Web Site: www.ijettcs.org Email: [email protected] Volume 5, Issue 6, November - December 2016 ISSN 2278-6856 ICT Tool: - ‘C’ Language Program for Lagrange’s Interpolation Pradip P. Kolhe1 , Dr Prakash R. Kolhe2 , Sanjay C. Gawande3 1Assistant Professor (Computer Sci.), ARIS Cell, Dr. PDKV, Akola (MS), India 2Associate Professor (Computer Sci.) (CAS), Dr. BSKKV, Dapoli (MS), India 3Assistant Professor (Mathematics), College of Agriculture, Dr. PDKV, Akola Abstract Although named after Joseph Louis Lagrange, who In mathematics to estimate an unknown data by analysing the published it in 1795, it was first discovered in 1779 by given referenced data Lagrange’s Interpolation technique is Edward Waring and it is also an easy consequence of a used. For the given data, (say ‘y’ at various ‘x’ in tabulated formula published in 1783 by Leonhard Euler. Lagrange form), the ‘y’ value corresponding to ‘x’ values can be found interpolation is susceptible to Runge's phenomenon, and by interpolation. the fact that changing the interpolation points requires Interpolation is the process of estimation of an unknown data recalculating the entire interpolant can make Newton by analysing the given reference data. In case of equally polynomials easier to use. Lagrange polynomials are used spaced ‘x’ values, a number of interpolation methods are in the Newton–Cotes method of numerical integration and available such as the Newton’s forward and backward in Shamir's secret sharing scheme in cryptography. interpolation, Gauss’s forward and backward interpolation, Bessel’s formula, Laplace-Everett’s formula etc. -

The Chebyshev Points of the First Kind
Applied Numerical Mathematics 102 (2016) 17–30 Contents lists available at ScienceDirect Applied Numerical Mathematics www.elsevier.com/locate/apnum The Chebyshev points of the first kind Kuan Xu Mathematical Institute, University of Oxford, Oxford OX2 6GG, UK a r t i c l e i n f o a b s t r a c t Article history: In the last thirty years, the Chebyshev points of the first kind have not been given as much Received 12 April 2015 attention for numerical applications as the second-kind ones. This survey summarizes Received in revised form 31 August 2015 theorems and algorithms for first-kind Chebyshev points with references to the existing Accepted 23 December 2015 literature. Benefits from using the first-kind Chebyshev points in various contexts are Available online 11 January 2016 discussed. © Keywords: 2016 IMACS. Published by Elsevier B.V. All rights reserved. Chebyshev points Chebyshev nodes Approximation theory Spectral methods 1. Introduction The Chebyshev polynomials of the first kind, Tn(x) = cos(n arccos x), were introduced by Pafnuty Chebyshev in a paper on hinge mechanisms in 1853 [11]. The zeros and the extrema of these polynomials were investigated in 1859 in a paper by Chebyshev on best approximation [12]. The zeros of Chebyshev polynomials are called Chebyshev points of the first kind, Chebyshev nodes, or, more formally, Chebyshev–Gauss points; they are given by (2k + 1)π xk = cos θk,θk = , k = 0,...,n − 1. (1) 2n The extrema, given by kπ yk = cos φk,φk = , k = 0, 1,...,n − 1, (2) n − 1 are called the Chebyshev points of the second kind, or Chebyshev extreme points, or Chebyshev–Lobatto points. -
Lagrange Interpolation Polynomial Pdf
Lagrange interpolation polynomial pdf Continue Lagrange Interpolation Polynomials If we want to describe all the ups and downs in the data set, and hit every point, we use what is called polynomial interpolation. This method is associated with Lagrange. Suppose the dataset consists of N data points: (x1, y1), (x2, y2), (x3, y3), ..., (xN, yN) Polynomial Interpolation will have a degree N - 1 . It is given: P (x) j1 (x) y1 y2 (x) y2 y3 (x) y3 ... It's easier than it looks. The main thing to note is that the ji numerator (x) contains the entire sequence of factors (x - x1), (x - x2), (x - x3), ... (x - xN), except for one factor (x - xi). Similarly, the denominator contains the entire sequence of factors (xi - x1), (xi - x2), (xi - x3), ... (xi - xN), except for one factor (xi - xi). Now note: ji (xi) No 1 (number and denominator), but ji (xj) 0 (number 0, as it contains the factor (xj - xj) ) for any j is not i. This means P (xi) and yi, which is exactly what we want! If this seems like smoke and mirrors, consider a simple example. Here's the data for g again: x g(x) 0 -250 10 0 20 50 30 -100 In this case there is a N 4 data point, so we will create a polynomial degree N - 1 and 3 . We have x1 y 0, x2 x 10, x3 x 20, x4 y 30, and y1 - 250, y2 y 0, y3 y 50, y4 and 100. So: Multiplying each of them appropriate yi (i q 1, 2, 3, 4) and adding together conditions of similar power, then gives: cubic conditions are canceled, and we come to a simple square description of the data. -
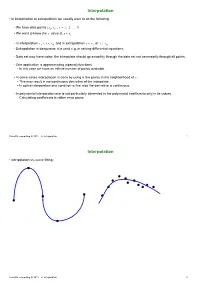
Interpolation Interpolation
Interpolation • In interpolation or extrapolation we usually want to do the following - We have data points xi yi , i = 12} N - We want to know the y value at xxz i - In interpolation x1 xxN and in extrapolation xx 1 or xx! N - Extrapolation is dangerous; it is used e.g. in solving differential equations. - Data set may have noise: the interpolate should go smoothly through the data set not necessarily through all points. - One application is approximating (special) functions - In this case we have an infinite number of points available. - In some cases interpolation is done by using a few points in the neighborhood of x. - This may result in noncontinuous derivative of the interpolate. - In spline interpolation one condition is that also the derivative is continuous. - In polynomial interpolation one is not particularly interested in the polynomial coefficients only in its values. - Calculating coefficients is rather error prone. Scientific computing III 2011: 6. Interpolation 1 Interpolation • Interpolation vs. curve fitting: Scientific computing III 2011: 6. Interpolation 2 Interpolation • Degree of interpolation is (number of points used)-1. - Below an example of interpolation of a smooth function original function low degree interpolation high degree interpolation - When the original function has sharp corners an interpolation polynomial with a lower degree may work better Scientific computing III 2011: 6. Interpolation 3 Interpolation: polynomials • We have a data set xi yi , yi = fx()i , i = 1} N - We have to find a polynomial P N – 1 x that fulfills the condition PN – 1()xi = yi , i = 1} N - It is easy to show that the polynomial is at most of degree N – 1 and it is unique if all x i are different. -
A Key Distribution Scheme in Broadcast Encryption Using Polynomial Interpolation
International Journal of Applied Engineering Research ISSN 0973-4562 Volume 12, Number 24 (2017) pp. 15475-15483 © Research India Publications. http://www.ripublication.com A Key Distribution Scheme in Broadcast Encryption Using Polynomial Interpolation Deepika M P Research Scholar, Department of Computer Applications, Cochin University of Science and Technology, Ernakulum,Kerala, India. Orcid Id: 0000-0003-0282-5674 Dr. A Sreekumar Associate Professor, Department of Computer Applications, Cochin University of Science and Technology, Ernakulum,Kerala, India. Abstract hop networks, which each node in these networks has Broadcast encryption is a type of encryption scheme first limitation in computing and storage resources. proposed by Amos Fiat and Moni Naor in 1993. Their original In general, to broadcast (verb) is to cast or throw forth goal was to prove that two devices, previously unknown to something in all directions at the same time. It is something each other, can agree on a common key for secure like as shown in Figure.1 communications over a one-way communication path. Broadcast encryption allows for devices that may not have even existed when a group of devices was first grouped together to join into this group and communicate securely. This paper describes broadcast encryption in general, a brief survey on the same, and a new scheme for the key distribution in broadcast encryption using polynomial interpolation. The proposed scheme is a revocation scheme. Keywords:Broadcast encryption, Data sharing, Revocation scheme, Key Distribution, Polynomial Interpolation. INTRODUCTION Traditionally, secure transmission of information has been achieved through the use of public-key cryptography. For this system to work, communicating devices must know about each other and agree on encryption keys before transmission. -

Numerical Methods
Numerical Methods Andrew Kobin Fall 2014 Contents Contents Contents 1 Introduction and Background 1 1.1 Basic Calculus . .1 1.2 Floating Point Numbers . .5 1.3 Absolute and Relative Error . .6 1.4 Finite Digit Arithmetic . .7 2 Solving Equations 9 2.1 The Bisection Method . .9 2.2 Fixed Point Iteration . 10 2.3 Newton's Method . 12 2.4 The Secant Method . 13 2.5 Convergence of Iterative Algorithms . 14 3 Interpolation and Approximation 16 3.1 Lagrange Interpolating Polynomials . 16 3.2 Chebyshev Nodes . 23 3.3 Hermite Interpolation . 24 3.4 Splines . 25 4 Numerical Differentiation and Integration 28 4.1 Numerical Derivatives . 28 4.2 Richardson's Process . 31 4.3 Numerical Integration . 32 4.4 Round-Off Error . 36 4.5 Romberg Integration . 37 5 Numerical Linear Algebra 38 5.1 Linear Systems of Equations . 38 5.2 Iterative Methods for Solving Linear Systems . 39 5.3 Norms of Vectors and Matrices . 41 5.4 Convergence of Iterative Methods . 44 5.5 Least Squares Solutions . 45 5.6 Estimating Functions . 49 5.7 The Chebyshev Polynomials . 54 i 1 Introduction and Background 1 Introduction and Background These notes are taken from a course taught by Dr. Matt Mastin at Wake Forest University in the fall of 2014. The main text used for the course is Numerical Analysis, 9th ed., by Burden and Faires. The main topics covered in this course are: Review calculus Floating point arithmetic and rounding error Convergence of algorithms Solving equations Interpolation and approximation Numerical derivatives and integrals Numerical linear algebra 1.1 Basic Calculus A primary tool in calculus is Theorem 1.1.1 (Taylor). -
Numerical Methods (Wiki) GU Course Work
Numerical Methods (Wiki) GU course work PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sun, 21 Sep 2014 15:07:23 UTC Contents Articles Numerical methods for ordinary differential equations 1 Runge–Kutta methods 7 Euler method 18 Numerical integration 25 Trapezoidal rule 32 Simpson's rule 35 Bisection method 40 Newton's method 44 Root-finding algorithm 57 Monte Carlo method 62 Interpolation 73 Lagrange polynomial 78 References Article Sources and Contributors 84 Image Sources, Licenses and Contributors 86 Article Licenses License 87 Numerical methods for ordinary differential equations 1 Numerical methods for ordinary differential equations Numerical methods for ordinary differential equations are methods used to find numerical approximations to the solutions of ordinary differential equations (ODEs). Their use is also known as "numerical integration", although this term is sometimes taken to mean the computation of integrals. Many differential equations cannot be solved using symbolic computation ("analysis"). For practical purposes, however – such as in engineering – a numeric approximation to the solution is often sufficient. The algorithms studied here can be used to compute such an approximation. An alternative method is to use techniques from calculus to obtain a series expansion of the solution. Ordinary differential equations occur in many scientific disciplines, for instance in physics, chemistry, biology, and economics. In addition, some methods in numerical partial differential equations convert the partial differential equation into an ordinary differential equation, which must then be solved. Illustration of numerical integration for the differential equation The problem Blue: the Euler method, green: the midpoint method, red: the exact solution, The A first-order differential equation is an Initial value problem (IVP) of step size is the form, where f is a function that maps [t ,∞) × Rd to Rd, and the initial 0 condition y ∈ Rd is a given vector. -

Barycentric Lagrange Interpolation∗
SIAM REVIEW c 2004 Society for Industrial and Applied Mathematics Vol. 46, No. 3, pp. 501–517 Barycentric Lagrange Interpolation∗ Jean-Paul Berrut† Lloyd N. Trefethen‡ Dedicated to the memory of Peter Henrici (1923–1987) Abstract. Barycentric interpolation is a variant of Lagrange polynomial interpolation that is fast and stable. It deserves to be known as the standard method of polynomial interpolation. Key words. barycentric formula, interpolation AMS subject classifications. 65D05, 65D25 DOI. 10.1137/S0036144502417715 1. Introduction. “Lagrangian interpolation is praised for analytic utility and beauty but deplored for numerical practice.” This heading, from the extended table of contents of one of the most enjoyable textbooks of numerical analysis [1], expresses a widespread view. In the present work we shall show that, on the contrary, the Lagrange approach is in most cases the method of choice for dealing with polynomial interpolants. The key is that the Lagrange polynomial must be manipulated through the formulas of barycentric interpolation. Barycentric interpolation is not new, but most students, most mathematical scientists, and even many numerical analysts do not knowabout it. This simple and powerful idea deserves a place at the heart of introductory courses and textbooks in numerical analysis.1 As always with polynomial interpolation, unless the degree of the polynomial is low, it is usually not a good idea to use uniformly spaced interpolation points. Instead one should use Chebyshev points or other systems of points clustered at the boundary of the interval of approximation. 2. Lagrange and Newton Interpolation. Let n + 1 distinct interpolation points (nodes) xj, j =0,...,n, be given, together with corresponding numbers fj, which may or may not be samples of a function f. -

Polynomial Interpolation
Polynomial Interpolation MAT 2310 Computational Mathematics Wm C Bauldry November, 2011 ASU-MSD 1 Contents 1. Polynomial Interpolation 2. Lagrange Interpolation 3. Interlude: Bernstein Polynomials 4. Newton Interpolation 5. Two Comparisons 6. Interlude: Splines 7. Exercises 8. Links and Others ASU-MSD 2 Polynomial Interpolation What is Polynomial Interpolation? An interpolating polynomial p(x) for a set of points is a polynomial S that goes through each point of . That is, for each point Pi = (xi; yi) S in the set, p(xi) = yi. Applications include: Approximating Functions TrueType Fonts (2nd deg) Fast Multiplication Cryptography PostScript Fonts (3rd deg) Data Compression Since each data point determines one polynomial coefficient, an n-point data set has an n 1 degree interpolating polynomial. − [ 2, 1] − [ 1, 1] 2 4 8 2 8 − − 9 p4(x)= x x +1 = > [0, 1] > 3 − 3 S > > <> [1, 1] => [2,−1] > > > > :> ;> ASU-MSD 3 Free Sample Finding an Interpolating Polynomial Let = [ 2; 1]; [ 1; 1]; [0; 1]; [1; 1]; [2; 1] . S f − − − − g 1. Since has 5 points, we compute a 4th degree polynomial S 2 3 4 p4(x) = a0 + a1x + a2x + a3x + a4x 2. Substitute the values of into p4; write the results as a system of linear equations. S 2 3 2 3 2 3 2 3 1 a0 − 2a1 + 4a2 − 8a3 + 16a4 1 −2 4 −8 16 a0 6−17 6 a0 − a1 + a2 − a3 + a4 7 61 −1 1 −1 1 7 6a17 6 7 6 7 6 7 6 7 6 17 = 6 a0 7 = 61 0 0 0 0 7 6a27 6 7 6 7 6 7 6 7 4−15 4 a0 + a1 + a2 + a3 + a4 5 41 1 1 1 1 5 4a35 1 a0 + 2a1 + 4a2 + 8a3 + 16a4 1 2 4 8 16 a4 3.