Deploy the Asav Auto Scale Solution on Microsoft Azure
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Azure Web Apps for Developers Microsoft Azure Essentials
Azure Web Apps for Developers Microsoft Azure Essentials Rick Rainey Visit us today at microsoftpressstore.com • Hundreds of titles available – Books, eBooks, and online resources from industry experts • Free U.S. shipping • eBooks in multiple formats – Read on your computer, tablet, mobile device, or e-reader • Print & eBook Best Value Packs • eBook Deal of the Week – Save up to 60% on featured titles • Newsletter and special offers – Be the first to hear about new releases, specials, and more • Register your book – Get additional benefits Hear about it first. Get the latest news from Microsoft Press sent to your inbox. • New and upcoming books • Special offers • Free eBooks • How-to articles Sign up today at MicrosoftPressStore.com/Newsletters Wait, there’s more... Find more great content and resources in the Microsoft Press Guided Tours app. The Microsoft Press Guided Tours app provides insightful tours by Microsoft Press authors of new and evolving Microsoft technologies. • Share text, code, illustrations, videos, and links with peers and friends • Create and manage highlights and notes • View resources and download code samples • Tag resources as favorites or to read later • Watch explanatory videos • Copy complete code listings and scripts Download from Windows Store PUBLISHED BY Microsoft Press A division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2015 Microsoft Corporation. All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. ISBN: 978-1-5093-0059-4 Microsoft Press books are available through booksellers and distributors worldwide. -

Microsoft Cloud Agreement
Microsoft Cloud Agreement This Microsoft Cloud Agreement is entered into between the entity you represent, or, if you do not designate an entity in connection with a Subscription purchase or renewal, you individually (“Customer”), and Microsoft Ireland Operations Limited (“Microsoft”). It consists of the terms and conditions below, Use Rights, SLA, and all documents referenced within those documents (together, the “agreement”). It is effective on the date that your Reseller provisions your Subscription. Key terms are defined in Section 10. 1. Grants, rights and terms. All rights granted under this agreement are non-exclusive and non-transferable and apply as long as neither Customer nor any of its Affiliates is in material breach of this agreement. a. Software. Upon acceptance of each order, Microsoft grants Customer a limited right to use the Software in the quantities ordered. (i) Use Rights. The Use Rights in effect when Customer orders Software will apply to Customer’s use of the version of the Software that is current at the time. For future versions and new Software, the Use Rights in effect when those versions and Software are first released will apply. Changes Microsoft makes to the Use Rights for a particular version will not apply unless Customer chooses to have those changes apply. (ii) Temporary and perpetual licenses. Licenses available on a subscription basis are temporary. For all other licenses, the right to use Software becomes perpetual upon payment in full. b. Online Services. Customer may use the Online Services as provided in this agreement. (i) Online Services Terms. The Online Services Terms in effect when Customer orders or renews a subscription to an Online Service will apply for the applicable subscription term. -
How Github Secures Open Source Software
How GitHub secures open source software Learn how GitHub works to protect you as you use, contribute to, and build on open source. HOW GITHUB SECURES OPEN SOURCE SOFTWARE PAGE — 1 That’s why we’ve built tools and processes that allow GitHub’s role in securing organizations and open source maintainers to code securely throughout the entire software development open source software lifecycle. Taking security and shifting it to the left allows organizations and projects to prevent errors and failures Open source software is everywhere, before a security incident happens. powering the languages, frameworks, and GitHub works hard to secure our community and applications your team uses every day. the open source software you use, build on, and contribute to. Through features, services, and security A study conducted by the Synopsys Center for Open initiatives, we provide the millions of open source Source Research and Innovation found that enterprise projects on GitHub—and the businesses that rely on software is now comprised of more than 90 percent them—with best practices to learn and leverage across open source code—and businesses are taking notice. their workflows. The State of Enterprise Open Source study by Red Hat confirmed that “95 percent of respondents say open source is strategically important” for organizations. Making code widely available has changed how Making open source software is built, with more reuse of code and complex more secure dependencies—but not without introducing security and compliance concerns. Open source projects, like all software, can have vulnerabilities. They can even be GitHub Advisory Database, vulnerable the target of malicious actors who may try to use open dependency alerts, and Dependabot source code to introduce vulnerabilities downstream, attacking the software supply chain. -

Cyber AI Security for Microsoft Azure
Data Sheet Cyber AI Security for Microsoft Azure Powered by self-learning Cyber AI, Darktrace brings real-time visibility and autonomous defense to your Azure cloud. Key Benefits Cyber AI Defense for Dynamic Protecting Azure Cloud From Novel Workforces and Workloads and Advanced Threats ✔ Learns ‘on the job’ to offer The Darktrace Immune System provides a unified, AI-native Data Exfiltration and Destruction continuous, context-based platform for autonomous threat detection, investigation, defense and response in Azure and across the enterprise, ensuring Detects anomalous device connections and user your dynamic workforce is always protected. access, as well as unusual resource deletion, ✔ Offers complete real-time visibility modification, and movement. of your organization’s Azure With advanced Cyber AI, Darktrace builds a deep environment understanding of normal behavior in your Azure cloud Critical Misconfigurations environment to identify even the most subtle deviations ✔ Autonomously neutralizes novel from usual activity that point to a threat – no matter how Identifies unusual permission changes and and advanced threats sophisticated or novel. anomalous activity around compliance-related data ✔ Cyber AI Analyst automates and devices. threat investigation, reducing time to triage by up to 92% Compromised credentials Spots brute-force attempts, unusual login source or time, and unusual user behavior including rule changes and password resets. “Darktrace complements Microsoft’s security products Insider Threat and Admin Abuse with -

Use Chef Automate and Microsoft Azure for Speed, Scale and Consistency
Use Chef Automate and Microsoft Azure for speed, scale and consistency Together, Chef Automate and Microsoft Azure give you everything you need to deliver infrastructure and applications quickly and safely. You can give your operations and development teams a common pipeline for building, testing, and deploying infrastructure and applications. Use Chef Automate on Azure and take advantage of the flexibility, scalability and reliability that Azure offers. Chef Automate on the Azure Marketplace makes it easy to deploy a fully-featured Chef Automate instance into your own Azure subscription. workflow. When compliance is code you can find problems early in the development process. Chef. With the Chef server and client, you describe your infrastructure as code, which means it’s versionable, human-readable, and testable. You can take advantage of cookbooks provided by the Chef community, which contain code for managing your infrastructure. Habitat. Habitat is automation that travels with the app. Habitat packages contain everything the Chef Automate is the leader in Continuous app needs to run with no outside dependencies. Automation. With Chef Automate, you have Habitat apps are isolated, immutable, and auditable. everything you need to build, deploy and manage They are atomically deployed, with self-organizing your applications and infrastructure at speed. peer relationships. With Habitat, your apps behave Collaborate. Chef Automate provides a pipeline for consistently in any runtime environment. It’s an the continuous deployment of infrastructure and ideal approach for deploying containers using the applications. Chef Automate also includes tools for Azure Container Service (ACS) or managing legacy local development and can integrate with a variety of application stacks using virtual machine instances in third-party products for developer workflows. -

Getting Started with Microsoft Azure Virtual Machines
Getting Started with Microsoft Azure Virtual Machines Introduction You can use a Microsoft Azure Virtual Machine when you need a scalable, cloud-based server running a Windows or Linux operating system and any application of your choosing. By taking advantage of Microsoft Azure Infrastructure as a Service (IaaS), you can run a virtual machine on an ongoing basis, or you can stop and restart it later with no loss to your data or server settings. You can quickly provision a new virtual machine from one of the images available from Microsoft Azure. On the other hand, if you are already running applications in a VMware or Hyper-V virtualized environment, you can easily migrate your virtual machine to Microsoft Azure. Once you have created your virtual machine and added it to Microsoft Azure, you can work with it much like an on-premises server by attaching more disks for data storage or by installing and running applications on it. Virtual machines rely on Microsoft Azure Storage for high availability. When your virtual machine is provisioned, it is replicated to three separate locations within the data center to which you assign it. You have the option to enable geo-replication to have copies of your virtual machine available in a remote data center region. Considering Scenarios for a Virtual Machine Microsoft Azure gives you not only the flexibility to support many application platforms, but also the flexibility to scale up and scale down to suit your requirements. Furthermore, you can quickly provision a new virtual machine in a few minutes. A Microsoft Azure virtual machine is simply a fresh machine preloaded with an operating system of your choice—you can add any needed application easily. -
Microsoft Azure Azure Services
Microsoft Azure Microsoft Azure is supplier of more than 600 integrated Cloud services used to develop, deploy, host, secure and manage software apps. Microsoft Azure has been producing unrivaled results and benets for many businesses throughout recent years. With 54 regions, it is leading all cloud providers to date. With more than 70 compliance oerings, it has the largest portfolio in the industry. 95% of Fortune 500 companies trust their business on the MS cloud. Azure lets you add cloud capabilities to your existing network through its platform as a service (PaaS) model, or entrust Microsoft with all of your computing and network needs with Infrastructure as a Service (IaaS). Either option provides secure, reliable access to your cloud hosted data—one built on Microsoft’s proven architecture. Kinetix Solutions provides clients with “Software as a Service” (SaaS), “Platform as a Service” (PaaS) and “Infrastructure as a Service” (IaaS) for small to large businesses. Azure lets you add cloud capabilities to your existing network through its platform as a service (PaaS) model, or entrust Microsoft with all of your computing and network needs with Infrastructure as a Service (IaaS). Azure provides an ever expanding array of products and services designed to meet all your needs through one convenient, easy to manage platform. Below are just some of the many capabilities Microsoft oers through Azure and tips for determining if the Microsoft cloud is the right choice for your organization. Become more agile, exible and secure with Azure and -

Windows Virtual Desktop to Horizon Cloud on Microsoft Azure
DATASHEET VMware Horizon Cloud on Microsoft Azure Extending Microsoft Windows Virtual Desktop AT A GLANCE Horizon Cloud on Microsoft Azure gives organizations the ability to connect their VMware Horizon® Cloud on Microsoft own instance of Azure to the simple, intuitive Horizon Cloud control plane, creating Azure extends Windows Virtual Desktop a secure, comprehensive, cloud-hosted solution for delivering virtualized Windows functionality into Horizon Cloud desktops applications and desktops. With the release of Windows Virtual Desktop, VMware running on Microsoft Azure. Customers can has partnered with Microsoft to extend the functionality of Windows Virtual Desktop leverage the benefits of Windows Virtual to customers using Horizon Cloud on Microsoft Azure. Desktop—including Windows 10 Enterprise multi-session and FSLogix—in addition Organizations extending Windows Virtual Desktop to Horizon Cloud on Microsoft to the simplified management, enhanced Azure receive all the benefits of Windows Virtual Desktop, such as Windows 10 remote experience, and native cloud Enterprise multi-session and FSLogix capabilities. In addition, organizations benefit architecture that Horizon Cloud on from all the following the modern, enterprise-class features of Horizon Cloud. Microsoft Azure provides. Broad Endpoint Support with Enhanced Remote Experience LEARN MORE Horizon Cloud supports a large and diverse array of client platforms and endpoints, To find out more about how Horizon Cloud allowing users to access their desktops and applications from any common desktop or on Microsoft Azure extending Windows mobile OS, thin client, or web browser. Users can expect a feature-rich experience, Virtual Desktop can help you, visit with support for USB, camera, printer, and smart card redirection on most platforms, http://vmware.com/go/HorizonCloud. -
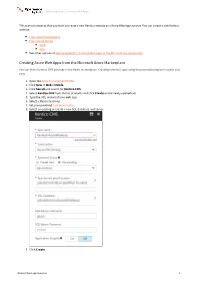
Creating Azure Web Apps from the Microsoft Azure Marketplace
Setting up Kentico in Azure Web Apps This scenario expects that you want to create a new Kentico website as a Azure Web Apps service. You can create a new Kentico website: From Azure Marketplace From Visual Studio 2015 2017 See other options of deploying Kentico to Azure Web Apps in the Microsoft documentation Creating Azure Web Apps from the Microsoft Azure Marketplace You can find a Kentico CMS package in the Azure marketplace. Creating new web apps using the provided template is quick and easy. 1. Open the Azure Management Portal. 2. Click New -> Web + Mobile. 3. Click See all and search for Kentico CMS. 4. Select Kentico CMS from the list of results and click Create on the newly opened tab. 5. Type the URL (name) of your web app. 6. Select a Resource Group. 7. Set your preferred App Service plan. 8. Select an existing or create a new SQL database and server. 9. Click Create. Database installation https://docs.xperience.io 1 Setting up Kentico in Azure Web Apps Database installation 1. Access the created website. 2. Provide the server name and credentials for the server where you created the database. 3. Click Next. 4. Select Use an existing database and type the name of the database created for the website. 5. Click Next. 6. Click Next without filling in any fields. 7. Select Create a new site or import an existing Kentico site and click Next. The installer redirects you to the Kentico administration interface. 8. Switch to the Licenses tab and add the license for the website domain. -

What NET Developers Need to Know About Azure
What .NET developers need to know about Azure Contents Microsoft Azure: A History ..................................................................................... 3 Shifting Perspectives for Microsoft Azure .................................................. 7 Impact on the Development Life Cycle ......................................................10 Introduction to the Latest Azure Innovations ...........................................14 01 Microsoft Azure: A History 3 Launched in January 2010, Microsoft Azure is now more than seven Azure has been through many rounds of changes that have significantly years old. Like all seven-year-olds, Azure has been through some affected the ways in which .NET and other developers interact with the memorable teething troubles over the years, as well as some incredible platform. growth and change. In this section, we’ll look back at the history of Microsoft Azure, including the ways in which Microsoft’s strategy for the The shift in strategy has been rocky at times. In 2011, technology reviewers platform and for the company as a whole have shifted in recent years. described Microsoft Azure as a confusing platform with a difficult to use Recently, Microsoft has focused on opening up the Azure environment web-based interface and incomprehensible documentation. Since then, to widen its appeal to all kinds of developers, including those working in the teams working on the platform have gradually improved it, resulting in non-Microsoft frameworks and languages. a much more user-friendly platform that offers a well-organized array of services. Microsoft’s History From the 80s to One of the biggest changes for the Microsoft Azure platform was its evolution from a Silverlight application to a web portal written in the new the 2000s HTML5 standard. -

Precog™: Physical Threat Detection
PreCog™: Physical Threat Detection Real-time prediction, defence and response to criminal behaviour Why use PreCog™? PreCog™ is a crime intelligence solution that leverages IoT hardware sensors and A.I. to help enterprise organisations • Take back control of crime identify and combat damage to their businesses from shoplifting, in your environment. in-store theft, burglary and violence towards staff. • Protect people, profit and PreCog™ is also for Law enforcement agencies seeking to assets from loss and locate criminals in real-time and to reduce costs, increase damage. efficiencies and improve KPIs. • Create a safer PreCog™ gives unique identities to mobile devices and captures environment for visitors and analyses their behaviour which can be linked to the owner of and colleagues. the device. This enables the presence of known persons of interest to be highlighted, located, and with behavioural profiling, • Low cost, high return criminality to be anticipated, identified and disrupted in real time. functionality. • Latest technology solution. • Provides visibility into areas precluded by other solutions. • Fully GDPR compliant. Real Time Intelligent Protection • Alert to previous offenders • Continuous adaptive learning • Colleague safety • White list / blacklist • Automatic threat alerting • Collaborative ecosystem • Continuous threat assessment • Threat level activated • No blind spots responses • 24hr/ 365 data collection • Historic reconnaissance • Multi-location intelligence visits PreCog™ Requires the deployment of a network of hardware each of which sends data to the Azure cloud every 5 seconds! “PreCog™ adds a powerful new capability to protect and defend against the evolving threats to people and infrastructure ” Head of Security, National Infrastructure, UK. Real time threat analysis, identification & response The first and only deployable Crime Intelligence Solution built with Microsoft Azure Sphere Device to-device and device to-cloud communication through certificate-based authentication validation, providing accuracy and scale. -

Enterprise Azure Quick Start Guide
Enterprise Azure Quick Start Guide v7.6.3 rev. 1.0.7 Copyright © 2002 – 2015 Load%a&ancer.org' Inc 1 Table of Contents Introduction.................................................................................................................................................. 3 About Enterprise Azure................................................................................................................................ 3 Version 7.6.x........................................................................................................................................... 3 Main Differences to the Non-Cloud Product............................................................................................3 Why use Enterprise Azure?....................................................................................................................4 Azure Terminology....................................................................................................................................... 4 Getting Started............................................................................................................................................. 4 Deployment Concepts................................................................................................................................. 5 Overview................................................................................................................................................. 5 Virtual Networks in Azure.......................................................................................................................