Secured Wireless Content Transmission Over Cloud with Intelligibility
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Insight Notes Linked to the J.P. Morgan Quest 5G Thematic Basket (Jan 2021) Due February 18, 2022 Fully and Unconditionally Guaranteed by Jpmorgan Chase & Co
The information in this preliminary pricing supplement is not complete and may be changed. This preliminary pricing supplement is not an offer to sell nor does it seek an offer to buy these securities in any jurisdiction where the offer or sale is not permitted. Subject to completion dated December 15, 2020 January , 2021 Registration Statement Nos. 333-236659 and 333-236659-01; Rule 424(b)(2) JPMorgan Chase Financial Company LLC Structured Investments Insight Notes Linked to the J.P. Morgan Quest 5G Thematic Basket (Jan 2021) due February 18, 2022 Fully and Unconditionally Guaranteed by JPMorgan Chase & Co. The notes are designed for investors who seek exposure to the performance of the J.P. Morgan Quest 5G Thematic Basket (Jan 2021) of 32 unequally weighted Reference Stocks, which we refer to as the Basket, as reduced by the Basket Deduction of 1.50%. The Reference Stocks in the Basket represent the common stocks / common shares / American depositary shares / ordinary shares of 32 U.S.-listed companies associated with the ongoing roll-out of fifth-generation wireless technologies (“5G”). Investors should be willing to forgo interest and dividend payments and, if the Basket is flat, declines or does not increase by at least 1.50%, be willing to lose some or all of their principal amount at maturity. The notes are unsecured and unsubordinated obligations of JPMorgan Chase Financial Company LLC, which we refer to as JPMorgan Financial, the payment on which is fully and unconditionally guaranteed by JPMorgan Chase & Co. Any payment on the notes is subject to the credit risk of JPMorgan Financial, as issuer of the notes, and the credit risk of JPMorgan Chase & Co., as guarantor of the notes. -

Certain Semiconductor Devices and Consumer Audiovisual Products Containing the Same That Infringe U.S
UNITED STATES INTERNATIONAL TRADE COMMISSION Washington, D.C. In the Matter of CERTAIN SEMICONDUCTOR Investigation No. 337-TA-1047 DEVICES AND CONSUMER AUDIOVISUAL PRODUCTS CONTAINING THE SAME NOTICE OF COMMISSION DETERMINATION NOT TO REVIEW AN INITIAL DETERMINATION TERMINATING THE INVESTIGATION AS TO ONE RESPONDENT GROUP AGENCY: U.S. International Trade Commission. ACTION: Notice. SUMMARY: Notice is hereby given that the U.S. International Trade Commission has determined not to review an initial determination (“ID”) (Order No. 35) issued by the presiding administrative law judge (“ALJ”). FOR FURTHER INFORMATION CONTACT: Robert Needham, Office of the General Counsel, U.S. International Trade Commission, 500 E Street, SW., Washington, D.C. 20436, telephone (202) 708-5468. Copies of non-confidential documents filed in connection with this investigation are or will be available for inspection during official business hours (8:45 a.m. to 5:15 p.m.) in the Office of the Secretary, U.S. International Trade Commission, 500 E Street, SW., Washington, D.C. 20436, telephone (202) 205- 2000. General information concerning the Commission may also be obtained by accessing its Internet server (https://www.usitc.gov). The public record for this investigation may be viewed on the Commission's electronic docket (EDIS) at https://edis.usitc.gov. Hearing-impaired persons are advised that information on this matter can be obtained by contacting the Commission’s TDD terminal on (202) 205- 1810. SUPPLEMENTARY INFORMATION: The Commission instituted this investigation on April 12, 2017, based on a complaint filed by Broadcom Corporation (“Broadcom”) of Irvine, California. 82 FR 17688. The complaint alleges violations of section 337 of the Tariff Act of 1930, as amended, 19 U.S.C. -

Android Programming Introduction
Android Programming Introduction Riya Jacob K Dept of BCA 2020 - 21 Modules 5 Modules 1 Module: Introduction & installation of Android(12 T+3L) 2 Module : Understanding Android Resources(12 T + 3L) 3 Module : UI development in Android (12 T + 3L) 4 Module : Android Menus (12 T+ 3L) 5Module : Data storing &file saving concept (12 T + 3 L) Module 1 History of Android Android software stack Developing end user application using android SDK Android java packages, Setting up the development environment, Installing android development tools (ADT) Fundamental components Android virtual devices, Running on real device Structure of android application Application life cycle. Introduction Android is an open source and Linux- based Operating System for mobile devices such as smartphones and tablet computers. Android was developed by the Open Handset Alliance, led by Google, and other companies. Android offers a unified approach to application development for mobile devices which means developers need only develop for Android, and their applications should be able to run on different devices powered by Android. Intro. The first beta version of the Android Software Development Kit (SDK) was released by Google in 2007 where as the first commercial version, Android 1.0, was released in September 2008. On June 27, 2012, at the Google I/O conference, Google announced the next Android version, 4.1 Jelly Bean. Jelly Bean is an incremental update, with the primary aim of improving the user interface, both in terms of functionality and performance. The source code for Android is available under free and open source software licenses. Google publishes most of the code under the Apache License version 2.0 and the rest, Linux kernel changes, under the GNU General Public License version 2. -

2 XI November 2014
2 XI November 2014 www.ijraset.com Volume 2 Issue XI, November 2014 ISSN: 2321-9653 International Journal for Research in Applied Science & Engineering Technology (IJRASET) Android Operating System Birender Singh Rawat1, Brijesh Aggarwal2, Dishant Passi3 Computer science Department, Dronacharya College of Engineering Abstract — The android operating system is basically an operating system for mobiles and is rapidly gaining market share, with dozens of smart phones and tablets either released or set to be released. It is mobile operating system that uses a modified version of the Linux kernel 2.6. Google developed Android as part of the Open Handset Alliance, a group of more than 30 mobile and technology companies working to open up the mobile handset environment. Android's development kit supports many of the standard packages used by Jetty, due to that fact and Jetty's modularity and light weight foot print, it was possible to port Jetty to it so that it will be able to run on the Android platform. Keywords— android, operating system, alliance, Google, Linux I. INTRODUCTION Android is a software platform and operating system for mobile devices, based on the Linux kernel, and developed by Google and later the Open Handset Alliance. It allows developers to write managed code in the Java language, controlling the device via GoogledevelopedJava libraries. Android is available as open source. Android is freely downloadable open source software stack for mobile devices that includes an operating system, middleware and key applications based on Linux and Java. Google purchased the developer of Android in 2005, and Android was unveiled in 2007. -
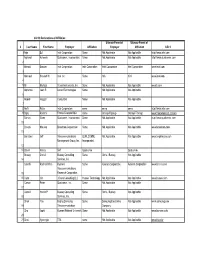
0 Last Name First Name Employer Affiliation Ultimate Parent Of
802.20 Declarations of Affiliation Ultimate Parent of Ultimate Parent of 0 Last Name First Name Employer Affiliation Employer Affiliation URL1 1 Agis Ed Intel Corporation Same Not Applicable Not Applicable http://www.intel.com Agrawal Avneesh Qualcomm, Incorporated Same Not Applicable Not Applicable http://www.qualcomm. com 2 Ahmadi Sassan Intel Corporation Intel Corporation Intel Corporation Intel Corporation www.intel.com 3 Alamouti Siavash M. Intel Inc. Same N/A N?A www.intel.com 4 5 Ali Murtaza Texas Instruments, Inc. Same Not Applicable Not Applicable www.ti.com Alphonse Jean R. Lucent Technologies Same Not Applicable Not Applicable 6 Alsaleh Haggar Consultant Same Not Applicable Not Applicable 7 8 Arefi Reza Intel Corporation same same same http://www.intel.com 9 Bajaj Rashmi France Telecom R&D same Orange Ftgroup OrangeFTGroup www.francetelecom.com/en Barriac Gwen Qualcomm, Incorporated Same Not Applicable Not Applicable http://www.qualcomm. com 10 Bavafa Moussa Broadcom Corporation Same Not Applicable Not Applicable www.broadcom.com 11 Bernstein Jeff Telecommunications QUALCOMM, Not Applicable Not Applicable www.tmgtelecom.com Management Group, Inc. Incorporated 12 13 Bravin Nancy Self Qualcomm Qualcomm Bussey Chris J. Bussey Consulting Same Chris J Bussey Not Applicable 14 Services, Inc. Canchi Radhakrishna Kyocera Same Kyocera Corporation. Kyocera Corporation www.ktrc-na.com Telecommunications 15 Research Corporation. 16 Carlo Jim J.Carlo Consulting LLC Huawei Technology Not Applicable Not Applicable www.huawei.com Carson Peter -

BROADCOM CORPORATION (Exact Name of Registrant As Specified in Its Charter)
As filed with the Securities and Exchange Commission on January 29, 2015 Registration No. 333- UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM S-8 REGISTRATION STATEMENT Under The Securities Act of 1933 BROADCOM CORPORATION (Exact name of registrant as specified in its charter) California 33-0480482 (State or other jurisdiction of (IRS Employer incorporation or organization) Identification No.) 5300 California Avenue, Irvine, California 92617 (Address of principal executive offices) (Zip code) Broadcom Corporation 1998 Employee Stock Purchase Plan, as amended and restated Broadcom Corporation 2007 International Employee Stock Purchase Plan, as amended and restated (Full title of the Plans) Arthur Chong, Esq. Executive Vice President, General Counsel and Secretary Broadcom Corporation 5300 California Avenue, Irvine, California 92617 (Name and address of agent for service) (949) 926-5000 (Telephone number, including area code, of agent for service) Copies to: Joseph M. Yaffe Skadden, Arps, Slate, Meagher & Flom LLP 525 University Avenue, Suite 1100 Palo Alto, California 94301 (650) 470-4500 Indicate by check mark whether the registrant is a large accelerated filer, an accelerated filer, a non-accelerated filer, or a smaller reporting company. See the definitions of “large accelerated filer,” “accelerated filer,” and “smaller reporting company” in Rule 12b-2 of the Exchange Act. (Check one): Large accelerated filer x Accelerated filer ¨ Non-accelerated filer ¨ (Do not check if a smaller reporting company) Smaller -
Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google. -

Android (Operating System) 10.1 Introduction: Android Is a Mobile
Page 1 of 9 Android (operating system) 10.1 Introduction: Android is a mobile operating system (OS) based on the Linux kernel and currently developed by Google. With a user interface based on direct manipulation, Android is designed primarily for touchscreen mobile devices such as smartphones and tablet computers, with specialized user interfaces for televisions (Android TV), cars (Android Auto), and wrist watches (Android Wear). The OS uses touch inputs that loosely correspond to real-world actions, like swiping, tapping, pinching, and reverse pinching to manipulate on-screen objects, and a virtual keyboard. Despite being primarily designed for touchscreen input, it also has been used in game consoles, digital cameras, and other electronics. Android is the most popular mobile OS. As of 2013, Android devices sell more than Windows, iOS, and Mac OS devices combined,[14][15][16][17] with sales in 2012, 2013 and 2014[18] close to the installed base of all PCs.[19] As of July 2013 the Google Play store has had over 1 million Android apps published, and over 50 billion apps downloaded.[20] A developer survey conducted in April–May 2013 found that 71% of mobile developers develop for Android.[21] At Google I/O 2014, the company revealed that there were over 1 billion active monthly Android users (that have been active for 30 days), up from 538 million in June 2013.[22] Android's source code is released by Google under open source licenses, although most Android devices ultimately ship with a combination of open source and proprietary software.[3] -

Broadcom Corporation (Name of Registrant As Specified in Its Charter)
Table of Contents SCHEDULE 14A INFORMATION PROXY STATEMENT PURSUANT TO SECTION 14(a) OF THE SECURITIES EXCHANGE ACT OF 1934 Filed by the Registrant þ Filed by a Party other than the Registrant ¨ Check the appropriate box: ¨ Preliminary Proxy Statement þ Definitive Proxy Statement ¨ Confidential, for Use of the Commission Only (as permitted by Rule 14a-6(e)(2)) ¨ Definitive Additional Materials ¨ Soliciting Material Pursuant to §240.14a-12 Broadcom Corporation (Name of Registrant as Specified In Its Charter) (Name of Person(s) Filing Proxy Statement, if other than the Registrant) Payment of Filing Fee (Check the appropriate box): þ Fee not required. ¨ Fee computed on table below per Exchange Act Rules 14a-6(i)(4) and 0-11. (1) Title of each class of securities to which transaction applies: (2) Aggregate number of securities to which transaction applies: (3) Per unit price or other underlying value of transaction computed pursuant to Exchange Act Rule 0-11 (set forth the amount on which the filing fee is calculated and state how it was determined): (4) Proposed maximum aggregate value of transaction: (5) Total fee paid: ¨ Fee paid previously with preliminary materials. ¨ Check box if any part of the fee is offset as provided by Exchange Act Rule 0-11(a)(2) and identify the filing for which the offsetting fee was paid previously. Identify the previous filing by registration statement number, or the Form or Schedule and the date of its filing. (1) Amount Previously Paid: (2) Form, Schedule or Registration Statement No.: (3) Filing Party: (4) Date Filed: Table of Contents BROADCOM CORPORATION 5300 California Avenue Irvine, California 92617-3038 March 29, 2013 Dear Fellow Shareholder: You are cordially invited to attend our 2013 Annual Meeting of Shareholders, which will be held at Broadcom’s corporate headquarters, 5300 California Avenue, Irvine, California, at 10:00 a.m. -

United States District Court, D. Delaware. INTEL
Untitled Document 3/3/10 12:53 AM United States District Court, D. Delaware. INTEL CORPORATION, Plaintiff. v. BROADCOM CORPORATION, Defendant. No. 00-796-RRM Nov. 6, 2001. In construing claims of patent for computer communications system including a communication medium, a plurality of nodes coupled to the communication medium, and a transfer format selection means for selecting a format for the transfer of data between nodes, the District Court, McKelvie, J., held that: (1) phrase "communication medium" was a collection of connections in a communication system over which information could be transmitted; (2) "plurality of nodes" did not have to be coupled, or electronically connected, to the communication medium; and (3) preamble language was language of intended use and did not serve to limit the meaning of the claim. Claims construed. 4,823,201, 4,975,830, 5,079,630, 5,134,478, 5,894,410. Cited. J. Andrew Huffman, Esquire, Fish & Richardson P.C., Wilmington, DE, John E. Gartman, Esquire and Juanita Brooks, Esquire, Fish & Richardson P.C., San Diego, CA, for Plaintiff. Richard H. Morse, Esquire and John W. Shaw, Esquire, Young Conaway Stargatt & Taylor, LLP, Wilmington, DE, Ron E. Shulman, Esquire, Michael A. Ladra, Esquire, Irwin R. Gross, Esquire, and James C. Yoon, Esquire, Wilson Sonsini Goodrich & Rosati, Palo Alto, CA, Raphael L. Lupo, Esquire and Vera Elson, Esquire, McDermott, Will & Emery, Washington DC, for Defendant. MEMORANDUM OPINION MCKELVIE, District Judge. This is a patent case. Plaintiff Intel Corporation is a Delaware corporation with its principal place of business in Santa Clara, California. Intel owns U.S. -

Qualcomm Inc. V. Broadcom Corp.: 9,259,985 Reasons to Comply with Discovery Requests
Richmond Journal of Law & Technology Volume XV, Issue 3 QUALCOMM INC. V. BROADCOM CORP.: 9,259,985 REASONS TO COMPLY WITH DISCOVERY REQUESTS By: Kristen McNeal∗ Cite as: Kristen McNeal, Note, Qualcomm Inc. v. Broadcom Corp.: 9,259,985 Reasons To Comply with Discovery Requests, 15 RICH. J.L. & TECH. 10, http://law.richmond.edu/jolt/v15i3/article10.pdf. I. INTRODUCTION [1] Evolving technology has advanced communication throughout the business industry. Corporations use various communication methods to initiate conversation, propose business ventures, and relay correspondence from one place to another. Quite naturally, with the development of different means of communication, various innovations in the legal profession have materialized and gained popularity. One of these innovations is electronic discovery.1 [2] When compared to conventional discovery means, electronic discovery is more proficient, less time consuming, and more easily organized;2 however, in some circumstances, it can pose difficulties if performed inefficiently or improperly. Under these circumstances, courts ∗ University of Richmond, T.C. Williams School of Law, J.D. candidate 2010. 1 FED. R. CIV. P. 26(f)(3)(C) (labeling electronic discovery as “disclosure or discovery of electronically stored information, including the form or forms in which it should be produced”); see Junk v. Aon Corp., No. 07 Civ. 4640(LMM)(GWG), 2007 WL 4292034, at *1 n.1 (S.D.N.Y. Dec. 3, 2007) (stating that a party referred to electronic discovery as “software capable of ‘retriev[ing], preserv[ing], documenting and produc[ing] electronic communications, records, and files’”). 2 See The E-Discovery Standard, APPLIED DISCOVERY’S ELECTRONIC DISCOVERY NEWSLETTER (LexisNexis Applied Discovery), Apr.