A Guide to Using Vbscript in Securecrt
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Adobe Introduction to Scripting
ADOBE® INTRODUCTION TO SCRIPTING © Copyright 2007 Adobe Systems Incorporated. All rights reserved. Adobe® Introduction to Scripting NOTICE: All information contained herein is the property of Adobe Systems Incorporated. No part of this publication (whether in hardcopy or electronic form) may be reproduced or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written consent of Adobe Systems Incorporated. The software described in this document is furnished under license and may only be used or copied in accordance with the terms of such license. This publication and the information herein is furnished AS IS, is subject to change without notice, and should not be construed as a commitment by Adobe Systems Incorporated. Adobe Systems Incorporated assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied, or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes, and non-infringement of third-party rights. Any references to company names in sample templates are for demonstration purposes only and are not intended to refer to any actual organization. Adobe®, the Adobe logo, Illustrator®, InDesign®, and Photoshop® are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apple®, Mac OS®, and Macintosh® are trademarks of Apple Computer, Inc., registered in the United States and other countries. Microsoft®, and Windows® are either registered trademarks or trademarks of Microsoft Corporation in the United States and other countries. JavaScriptTM and all Java-related marks are trademarks or registered trademarks of Sun Microsystems, Inc. -
Securecrt 7.3.6 Crack for Mac >>>
Securecrt 7.3.6 Crack For Mac >>> http://shurll.com/77o35 1 / 5 2 / 5 hash,,47850D6A1C717CEC4534B14525ED9BF2292DD905,,... VanDyke,,SecureCRT,,and,,SecureFX,,7 .3.6,,[Mac,,Os,,X],,[MAC599],,DOWNLOAD,,TORRENTSecureCRT,,for,,Mac,,OS,,X,,7.1... VanDyke,,Secu reCRT,,and,,SecureFX,,7.3.6,,[Mac,,Os,,X].torrent,,내부,,파일,,..Turn,,,your,,,computer,,,into,,,a,,,terminal,, ,server,,,using,,,Serial,,,to,,,Ethernet,,,Converter,,,with,,,its,,,amazing,,,capability,,,to,,,share,,,serial,,, devices,,,in,,,... Free,,,Download,,,SecureCRT,,,for,,,Mac,,,8.1.3,,,Build,,,1382,,,-,,,A,,,fully-featured,,,te rminal,,,emulator,,,as,,,well,,,as,,,a,,,SSH,,,and,,,Telnet,,,client,,,with,,,advanced,,,session,,,mana... Do wnload,,,VanDyke,,,SecureCRT,,,and,,,SecureFX,,,7.3.6,,,[Mac,,,Os,,,X],,,[MAC599],,,torrent,,,or,,,any,, ,other,,,torrent,,,from,,,Mac,,,category. SecureCRT®,,,7.3.6.963,,,for,,,MAC,,,|,,,40.7MbUsers,,,with,,,PCs,,,installed,,,with,,,Windows,,,8. Secu reCRT,,,provides,,,rock-solid,,,terminal,,,emulation,,,for,,,computing,,,professionals,,,,raising,,,product ivity,,,with,,,advanced,,,session,,,management,,,and,,,a,,,host,,,of,,,ways,,,to,,,save SecureCRT,,,for,,, Mac,,,,free,,,and,,,safe,,,downloadSecureCRT,,,supports,,,SSH2,,,,SSH1,,,,Telnet,,,,Telnet/SSL,,,,Serial, ,,,and,,,other,,,protocols..It,,,has,,,been,,,designed,,,to,,,be,,,used,,,during,,,the,,,high,,,stress,,,produc tion,,,... Torrentz,,,-,,,Fast,,,and,,,convenient,,,Torrents,,,Search,,,EngineApowersoft,,Screen,,Capture, ,Pro,,1.3.1,,InclTurn,,your,,computer,,into,,a,,terminal,,server,,using,,Serial,,to,,Ethernet,,Converter,, -

Getting Started with Windows Scripting
Getting Started with Windows Scripting art I of the PowerShell, VBScript, and JScript Bible intro- IN THIS PART duces you to the powerful administrative tool that is Windows scripting. You’ll get an overview of Windows Chapter 1 P Introducing Windows Scripting scripting and its potential, and an introduction to three tech- nologies you can use for Windows scripting: VBScript, JScript, Chapter 2 and PowerShell. VBScript Essentials Chapter 3 JScript Essentials Chapter 4 PowerShell Fundamentals COPYRIGHTED MATERIAL 886804c01.indd6804c01.indd 1 11/21/09/21/09 11:16:17:16:17 PPMM 86804c01.indd 2 1/21/09 1:16:18 PM Introducing Windows Scripting indows scripting gives everyday users and administrators the ability to automate repetitive tasks, complete activities while IN THIS CHAPTER away from the computer, and perform many other time-saving W Introducing Windows scripting activities. Windows scripting accomplishes all of this by enabling you to create tools to automate tasks that would otherwise be handled manually, Why script Windows? such as creating user accounts, generating log files, managing print queues, or examining system information. By eliminating manual processes, you Getting to know can double, triple, or even quadruple your productivity and become more Windows Script Host effective and efficient at your job. Best of all, scripts are easy to create and Understanding the Windows you can rapidly develop prototypes of applications, procedures, and utili- scripting architecture ties; and then enhance these prototypes to get exactly what you need, or just throw them away and begin again. This ease of use gives you the flex- ibility to create the kinds of tools you need without a lot of fuss. -

Vbscript Programmer’S Reference Third Edition
VBScript Programmer’s Reference Third Edition Adrian Kingsley-Hughes Kathie Kingsley-Hughes Daniel Read Wiley Publishing, Inc. ffirs.indd iii 8/28/07 9:41:21 AM ffirs.indd vi 8/28/07 9:41:22 AM VBScript Programmer’s Reference Third Edition Introduction . xxv Chapter 1: A Quick Introduction to Programming . 1 Chapter 2: What VBScript Is — and Isn’t! . 31 Chapter 3: Data Types . 45 Chapter 4: Variables and Procedures . 83 Chapter 5: Control of Flow . 109 Chapter 6: Error Handling and Debugging . 129 Chapter 7: The Scripting Runtime Objects . 183 Chapter 8: Classes in VBScript (Writing Your Own COM Objects) . 209 Chapter 9: Regular Expressions . 233 Chapter 10: Client-Side Web Scripting . 261 Chapter 11: Windows Sidebars and Gadgets . 287 Chapter 12: Task Scheduler Scripting . 309 Chapter 13: PowerShell . 345 Chapter 14: Super-Charged Client-Side Scripting . 375 Chapter 15: Windows Script Host . 405 Chapter 16: Windows Script Components . 465 Chapter 17: Script Encoding . 489 Chapter 18: Remote Scripting . 509 Chapter 19: HTML Applications . 517 Chapter 20: Server-Side Web Scripting . 535 Chapter 21: Adding VBScript to Your VB and .NET Applications . 569 (Continued) ffirs.indd i 8/28/07 9:41:21 AM Appendix A: VBScript Functions and Keywords . 603 Appendix B: Variable Naming Convention . 675 Appendix C: Coding Conventions . 677 Appendix D: Visual Basic Constants Supported in VBScript . 681 Appendix E: VBScript Error Codes and the Err Object . 687 Appendix F: The Scripting Runtime Library Object Reference . 703 Appendix G: The Windows Script Host Object Model . 715 Appendix H: Regular Expressions . 723 Appendix I: The Variant Subtypes . -

Case Study: Internet Explorer 1994..1997
Case Study: Internet Explorer 1994..1997 Ben Slivka General Manager Windows UI [email protected] Internet Explorer Chronology 8/94 IE effort begins 12/94 License Spyglass Mosaic source code 7/95 IE 1.0 ships as Windows 95 feature 11/95 IE 2.0 ships 3/96 MS Professional Developer’s Conference AOL deal, Java license announced 8/96 IE 3.0 ships, wins all but PC Mag review 9/97 IE 4.0 ships, wins all the reviews IE Feature Chronology IE 1.0 (7/14/95) IE 2.0 (11/17/95) HTML 2.0 HTML Tables, other NS enhancements HTML <font face=> Cell background colors & images Progressive Rendering HTTP cookies (arthurbi) Windows Integration SSL Start.Run HTML (MS enhancements) Internet Shortcuts <marquee> Password Caching background sounds Auto Connect, in-line AVIs Disconnect Active VRML 1.0 Navigator parity MS innovation Feature Chronology - continued IE 3.0 (8/12/96) IE 3.0 - continued... IE 4.0 (9/12/97) Java Accessibility Dynamic HTML (W3C) HTML Frames PICS (W3C) Data Binding Floating frames HTML CSS (W3C) 2D positioning Componentized HTML <object> (W3C) Java JDK 1.1 ActiveX Scripting ActiveX Controls Explorer Bars JavaScript Code Download Active Setup VBScript Code Signing Active Channels MSHTML, SHDOCVW IEAK (corporations) CDF (XML) WININET, URLMON Internet Setup Wizard Security Zones DocObj hosting Referral Server Windows Integration Single Explorer ActiveDesktop™ Navigator parity MS innovation Quick Launch, … Wins for IE • Quality • CoolBar, Explorer Bars • Componetization • Great Mail/News Client • ActiveX Controls – Outlook Express – vs. Nav plug-ins -

Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5
Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5 Copyright 2003, The Center for Internet Security www.cisecurity.org Page 2 of 32 Terms of Use Agreement Background. CIS provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the Products (“Recommendations”) result from a consensus-building process that involves many security experts and are generally generic in nature. The Recommendations are intended to provide helpful information to organizations attempting to evaluate or improve the security of their networks, systems and devices. Proper use of the Recommendations requires careful analysis and adaptation to specific user requirements. The Recommendations are not in any way intended to be a “quick fix” for anyone’s information security needs. No representations, warranties and covenants. CIS makes no representations, warranties or covenants whatsoever as to (i) the positive or negative effect of the Products or the Recommendations on the operation or the security of any particular network, computer system, network device, software, hardware, or any component of any of the foregoing or (ii) the accuracy, reliability, timeliness or completeness of any Product or Recommendation. CIS is providing the Products and the Recommendations “as is” and “as available” without representations, warranties or covenants of any kind. User agreements. By using the Products and/or the Recommendations, I and/or my organization (“we”) agree and acknowledge that: 1. No network, system, device, hardware, software or component can be made fully secure; 2. -

Windows® Scripting Secrets®
4684-8 FM.f.qc 3/3/00 1:06 PM Page i ® WindowsSecrets® Scripting 4684-8 FM.f.qc 3/3/00 1:06 PM Page ii 4684-8 FM.f.qc 3/3/00 1:06 PM Page iii ® WindowsSecrets® Scripting Tobias Weltner Windows® Scripting Secrets® IDG Books Worldwide, Inc. An International Data Group Company Foster City, CA ♦ Chicago, IL ♦ Indianapolis, IN ♦ New York, NY 4684-8 FM.f.qc 3/3/00 1:06 PM Page iv Published by department at 800-762-2974. For reseller information, IDG Books Worldwide, Inc. including discounts and premium sales, please call our An International Data Group Company Reseller Customer Service department at 800-434-3422. 919 E. Hillsdale Blvd., Suite 400 For information on where to purchase IDG Books Foster City, CA 94404 Worldwide’s books outside the U.S., please contact our www.idgbooks.com (IDG Books Worldwide Web site) International Sales department at 317-596-5530 or fax Copyright © 2000 IDG Books Worldwide, Inc. All rights 317-572-4002. reserved. No part of this book, including interior design, For consumer information on foreign language cover design, and icons, may be reproduced or transmitted translations, please contact our Customer Service in any form, by any means (electronic, photocopying, department at 800-434-3422, fax 317-572-4002, or e-mail recording, or otherwise) without the prior written [email protected]. permission of the publisher. For information on licensing foreign or domestic rights, ISBN: 0-7645-4684-8 please phone +1-650-653-7098. Printed in the United States of America For sales inquiries and special prices for bulk quantities, 10 9 8 7 6 5 4 3 2 1 please contact our Order Services department at 1B/RT/QU/QQ/FC 800-434-3422 or write to the address above. -
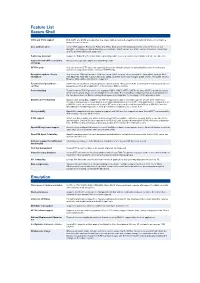
Feature List Secure Shell
Feature List Secure Shell SSH1 and SSH2 support Both SSH1 and SSH2 are supported in a single client, providing the maximum in flexibility when connecting to a range of remote servers. User authentication SecureCRT supports Password, Public Key (RSA, DSA, and X.509 including Smart Cards), Kerberos v5 (via GSSAPI), and Keyboard Interactive when connecting to SSH2 servers. For SSH1 servers, Password, Public Key, and TIS authentications are supported. Public Key Assistant Support for Public Key Assistant makes uploading public keys to an SSH2 server simple and safe for end users. Support for GSSAPI secured key Mechanisms supported depend on GSSAPI provider. exchange SFTP in a tab You can open an SFTP tab to the same SSH2 session without having to re-authenticate to perform file transfer operations using an interactive, text-based SFTP utility. Encryption ciphers: Strong The maximum 2048 bits length of DSA keys under SSH2 provides strong encryption. SecureCRT supports AES- encryption 128, AES-192, AES-256, Twofish, Blowfish, 3DES, and RC4 when connecting to SSH2 servers. For SSH1 servers, Blowfish, DES, 3DES, and RC4 are supported. Password and passphrase SSH2 session passwords and passphrases can be cached, letting SecureCRT and SecureFX share passwords and caching passphrases while either application or the Activator utility is running. Port forwarding Tunnel common TCP/IP protocols (for example, POP3, IMAP4, HTTP, SMTP) via SecureCRT to a remote Secure Shell server using a single, secure, multiplexed connection. Port forwarding configuration has been integrated into the tree-based Session Options dialog allowing easier configuration for securing TCP/IP application data. Dynamic port forwarding Dynamic port forwarding simplifies how TCP/IP application data is routed through the Secure Shell connection. -

Automatic Online Evaluation of Intelligent Assistants
Automatic Online Evaluation of Intelligent Assistants Jiepu Jiang1*, Ahmed Hassan Awadallah2, Rosie Jones2, Umut Ozertem2, Imed Zitouni2, Ranjitha Gurunath Kulkarni2 and Omar Zia Khan2 1 Center for Intelligent Information Retrieval, University of Massachusetts Amherst 2 Microsoft Redmond, WA USA [email protected], {hassanam, rosie.jones, umuto, izitouni, raguruna, omarzia.khan}@microsoft.com ABSTRACT These applications are usually evaluated by comparing system-gen- Voice-activated intelligent assistants, such as Siri, Google Now, erated answers with “correct” answers labeled by human annota- and Cortana, are prevalent on mobile devices. However, it is chal- tors. For example, in web search, we annotate relevant webpages lenging to evaluate them due to the varied and evolving number of and evaluate using metrics such as mean average precision (MAP) tasks supported, e.g., voice command, web search, and chat. Since and normalized discounted cumulative gain (nDCG) [14]. each task may have its own procedure and a unique form of correct However, intelligent assistants differ from these applications in answers, it is expensive to evaluate each task individually. This pa- that they can involve a wide variety of tasks, ranging from making per is the first attempt to solve this challenge. We develop con- phone calls and managing calendars, to finding places, finding an- sistent and automatic approaches that can evaluate different tasks swers to general questions, and web search. These tasks have dif- in voice-activated intelligent assistants. We use implicit feedback ferent forms of “correct” answers. It is expensive to evaluate each from users to predict whether users are satisfied with the intelligent task separately using different human judgments and metrics. -

Secure Configuration and Management of Linux Systems
Secure Configuration and Management of Linux Systems using a Network Service Orchestrator Vijay Satti A Thesis in The Department of Concordia Institute for Information Systems Engineering Presented in Partial Fulfillment of the Requirements for the Degree of Master of Applied Science at Concordia University Montréal, Québec, Canada May 2019 c Vijay Satti, 2019 CONCORDIA UNIVERSITY School of Graduate Studies This is to certify that the thesis prepared By: Vijay Satti Entitled: Secure Configuration and Management of Linux Systems using a Network Service Orchestrator and submitted in partial fulfillment of the requirements for the degree of Master of Applied Science complies with the regulations of this University and meets the accepted standards with respect to originality and quality. Signed by the Final Examining Committee: Chair Dr. Walter Lucia Examiner Dr. Anjali Agarwal Examiner Dr. Amr Youssef Supervisor Dr. J. William Atwood Approved by Dr. Chadi Assi, Graduate Program Director Department of Concordia Institute for Information Systems Engineering 2019 Dr. Amir Asif, Dean Faculty of Engineering and Computer Science Abstract Secure Configuration and Management of Linux Systems using a Network Service Orchestrator Vijay Satti Manual management of the configuration of network devices and computing devices (hosts) is an error-prone task. Centralized automation of these tasks can lower the costs of management, but can also introduce unknown or unanticipated security risks. Miscon- figuration (deliberate (by outsiders) or inadvertent (by insiders)) can expose a system to significant risks. Centralized network management has seen significant progress in recent years, result- ing in model-driven approaches that are clearly superior to previous "craft" methods. Host management has seen less development. -

Vbscript Basics Page 1 of 52 [email protected]
Chapter 03 Scripting Quicktest Professional Page 1 VBS CRIPT – THE BASICS ............................................................................................................ 2 WHAT IS A VARIABLE ?........................................................................................................... 3 VARIABLES NAMING RESTRICTIONS ..................................................................................... 3 HOW DO I CREATE A VARIABLE ?.......................................................................................... 3 DECLARATION STATEMENTS AND HIGHILIGTS ..................................................................... 3 Dim Statement .................................................................................................................... 3 Overriding Standard Variable Naming Conventions.......................................................... 4 Declaring Variables Explicit and Implicit .......................................................................... 4 Option Explicit Statement................................................................................................... 5 WORKING WITH ARRAYS ........................................................................................................... 5 SCALAR VARIABLES AND ARRAY VARIABLES ...................................................................... 6 CREATING ARRAYS ................................................................................................................ 6 Fixed Length Arrays.......................................................................................................... -

Preview Vbscript Tutorial (PDF Version)
VBScript About the Tutorial Microsoft VBScript (Visual Basic Script) is a general-purpose, lightweight and active scripting language developed by Microsoft that is modelled on Visual Basic. Nowadays, VBScript is the primary scripting language for Quick Test Professional (QTP), which is a test automation tool. This tutorial will teach you how to use VBScript in your day-to-day life of any Web-based or automation project development. Audience This tutorial has been prepared for beginners to help them understand the basic-to- advanced functionality of VBScript. After completing this tutorial, you will find yourself at a moderate level of expertise in using Microsoft VBScript from where you can take yourself to the next levels. Prerequisites You need to have a good understanding of any computer programming language in order to make the most of this tutorial. If you have done programming in any client-side languages like Javascript, then it will be quite easy for you to learn the ropes of VBScript. Copyright & Disclaimer © Copyright 2015 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute, or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher. We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness, or completeness of our website or its contents including this tutorial.