Owner's Manual Invoke
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C
Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C. 20554 In the Matter of ) ) PN Comments – Accessibility of ) CG Docket No. 10-213 Communications Technologies ) To: Consumer & Governmental Affairs Bureau COMMENTS OF MICROSOFT CORPORATION Accessibility is a business imperative for Microsoft, as both a matter of compliance and an area ripe for innovation. We are investing in design principles and natural user interfaces that help individuals of all abilities,1 and innovating in touch, gesture, and speech recognition that can be used to improve communications services available to people with disabilities. Some of our innovations were not designed exclusively for accessibility, such as the work we’ve done on the Windows touch interface, or Bing’s voice-activated search for our Windows Phone digital personal assistant Cortana. Other innovation is focused on helping people with disabilities, such as Microsoft’s partnership with the UK non-profit “Guide Dogs for the Blind” to enable better independent mobility, which we discuss below. In implementing the Twenty-First Century Communications and Video Accessibility Act of 2010 (“CVAA”), the Commission has left space for such innovation to occur by avoiding overly prescriptive regulations and setting reasonable compliance deadlines that provide industry time to research break-through solutions. For a company like Microsoft, that is already investing 1 Microsoft, Digital Inclusion and Natural User Interface Technology: A Policy Framework, http://download.microsoft.com/download/C/1/A/C1AA2411-C3AE-4D21-8C46- F33CE49BBFCF/Digital-Inclusion-Natural-User-Interface-Technology.pdf. in accessibility solutions and offers a multitude of devices, software and services to a wide range of customers around the world, that space is key for us to best use our technological know-how to deliver accessibility advancements that benefit people with disabilities. -

FIT to WORK: IMPROVING the SECURITY of MONITORED EMPLOYEES' HEALTH DATA Elizabeth A. Brown INTRODUCTION Imagine Coming to Work
FIT TO WORK: IMPROVING THE SECURITY OF MONITORED EMPLOYEES' HEALTH DATA Elizabeth A. Brown1 INTRODUCTION Imagine coming to work one day and finding that your employer has given everyone in the company a wearable FitBit health monitor, free of charge. You pop the FitBit on, grateful for another bit of help in managing the health concerns that nag at you persistently but which never quite rise to the top of your priority list. At your next performance review, your supervisor expresses concern about your anxiety levels. Although your work output is slightly off, she notes, there has been a correlation in your lack of sleep and exercise, and she suspects you are depressed. You wonder how your employer might know these things, whether or not they are true, and then you remember the FitBit. Your supervisor then tells you that the promotion you had wanted is going to a colleague who is “better equipped to handle the demands of the job.” You interview for another job, and are asked to provide the password to the HealthDrive account that centralizes the fitness data all the apps on your iPhone collect about you during the day. Similar scenarios are playing out now in workplaces across the country, and will do so more frequently as the personal health sensor market and employee monitoring trends continue to grow. Employers are making key decisions based on employees’ biometric data, collected from specialized devices like a FitBit or the health-related apps installed on mobile phones. BP, for example, adjusts its employees’ health care premiums depending on how much physical activity their wearable FitBit devices monitor – devices that BP provides to thousands of employees, their spouses, and retirees for free. -

Your Voice Assistant Is Mine: How to Abuse Speakers to Steal Information and Control Your Phone ∗ †
Your Voice Assistant is Mine: How to Abuse Speakers to Steal Information and Control Your Phone ∗ y Wenrui Diao, Xiangyu Liu, Zhe Zhou, and Kehuan Zhang Department of Information Engineering The Chinese University of Hong Kong {dw013, lx012, zz113, khzhang}@ie.cuhk.edu.hk ABSTRACT General Terms Previous research about sensor based attacks on Android platform Security focused mainly on accessing or controlling over sensitive compo- nents, such as camera, microphone and GPS. These approaches Keywords obtain data from sensors directly and need corresponding sensor invoking permissions. Android Security; Speaker; Voice Assistant; Permission Bypass- This paper presents a novel approach (GVS-Attack) to launch ing; Zero Permission Attack permission bypassing attacks from a zero-permission Android application (VoicEmployer) through the phone speaker. The idea of 1. INTRODUCTION GVS-Attack is to utilize an Android system built-in voice assistant In recent years, smartphones are becoming more and more popu- module – Google Voice Search. With Android Intent mechanism, lar, among which Android OS pushed past 80% market share [32]. VoicEmployer can bring Google Voice Search to foreground, and One attraction of smartphones is that users can install applications then plays prepared audio files (like “call number 1234 5678”) in (apps for short) as their wishes conveniently. But this convenience the background. Google Voice Search can recognize this voice also brings serious problems of malicious application, which have command and perform corresponding operations. With ingenious been noticed by both academic and industry fields. According to design, our GVS-Attack can forge SMS/Email, access privacy Kaspersky’s annual security report [34], Android platform attracted information, transmit sensitive data and achieve remote control a whopping 98.05% of known malware in 2013. -

Nokia Lumia 635 User Guide
User Guide Nokia Lumia 635 Issue 1.0 EN-US Psst... This guide isn't all there is... There's a user guide in your phone – it's always with you, available when needed. Check out videos, find answers to your questions, and get helpful tips. On the start screen, swipe left, and tap Nokia Care. If you’re new to Windows Phone, check out the section for new Windows Phone users. Check out the support videos at www.youtube.com/NokiaSupportVideos. For info on Microsoft Mobile Service terms and Privacy policy, go to www.nokia.com/privacy. First start-up Your new phone comes with great features that are installed when you start your phone for the first time. Allow some minutes while your phone sets up. © 2014 Microsoft Mobile. All rights reserved. 2 User Guide Nokia Lumia 635 Contents For your safety 5 Camera 69 Get started 6 Get to know Nokia Camera 69 Keys and parts 6 Change the default camera 69 Insert the SIM and memory card 6 Camera basics 69 Remove the SIM and memory card 9 Advanced photography 71 Switch the phone on 11 Photos and videos 75 Charge your phone 12 Maps & navigation 79 Transfer content to your Nokia Lumia 14 Switch location services on 79 Lock the keys and screen 16 Positioning methods 79 Connect the headset 17 Internet 80 Antenna locations 18 Define internet connections 80 Basics 19 Connect your computer to the web 80 Get to know your phone 19 Use your data plan efficiently 81 Accounts 28 Web browser 81 Personalize your phone 32 Search the web 83 Cortana 36 Close internet connections 83 Take a screenshot 37 Entertainment 85 Extend battery life 38 Watch and listen 85 Save on data roaming costs 39 FM radio 86 Write text 40 MixRadio 87 Scan codes or text 43 Sync music and videos between your phone and computer 87 Clock and calendar 44 Games 88 Browse your SIM apps 47 Office 90 Store 47 Microsoft Office Mobile 90 People & messaging 50 Write a note 92 Calls 50 Continue with a document on another Contacts 55 device 93 Social networks 59 Use the calculator 93 Messages 60 Use your work phone 93 Mail 64 Tips for business users 94 © 2014 Microsoft Mobile. -

Adobe Introduction to Scripting
ADOBE® INTRODUCTION TO SCRIPTING © Copyright 2007 Adobe Systems Incorporated. All rights reserved. Adobe® Introduction to Scripting NOTICE: All information contained herein is the property of Adobe Systems Incorporated. No part of this publication (whether in hardcopy or electronic form) may be reproduced or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written consent of Adobe Systems Incorporated. The software described in this document is furnished under license and may only be used or copied in accordance with the terms of such license. This publication and the information herein is furnished AS IS, is subject to change without notice, and should not be construed as a commitment by Adobe Systems Incorporated. Adobe Systems Incorporated assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied, or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes, and non-infringement of third-party rights. Any references to company names in sample templates are for demonstration purposes only and are not intended to refer to any actual organization. Adobe®, the Adobe logo, Illustrator®, InDesign®, and Photoshop® are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apple®, Mac OS®, and Macintosh® are trademarks of Apple Computer, Inc., registered in the United States and other countries. Microsoft®, and Windows® are either registered trademarks or trademarks of Microsoft Corporation in the United States and other countries. JavaScriptTM and all Java-related marks are trademarks or registered trademarks of Sun Microsystems, Inc. -
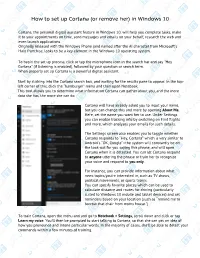
How to Set up Cortana (Or Remove Her) in Windows 10
How to set up Cortana (or remove her) in Windows 10 Cortana, the personal digital assistant feature in Windows 10, will help you complete tasks, make it to your appointments on time, send messages and emails on your behalf, research the web and even launch applications. Orignally released with the Windows Phone (and named after the AI character from Microsoft's Halo franchise, looks to be a key element in the Windows 10 operating system. To begin the set up process, click or tap the microphone icon in the search bar and say "Hey Cortana" (if listening is enabled), followed by your question or search term. When properly set up Cortana is a powerful digital assistant. Start by clicking into the Cortana search box, and waiting for the results pane to appear. In the top- left corner of this, click the “hamburger” menu and then open Notebook. This tool allows you to determine what information Cortana can gather about you, and the more data she has, the more she can do. Cortana will have already asked you to input your name, but you can change this and more by opening About Me. Here, set the name you want her to use. Under Settings you can enable tracking info by switching on Find flights and more, which analyses your emails for such details. The Settings screen also enables you to toggle whether Cortana responds to “Hey, Cortana” which is very similar to Android’s “OK, Google“–the system will constantly be on the look-out for you saying this phrase, and will open Cortana when it is detected. -

Game Enforcer Is Just a Group of People Providing You with Information and Telling You About the Latest Games
magazine you will see the coolest ads and Letter from The the most legit info articles you can ever find. Some of the ads include Xbox 360 skins Editor allowing you to customize your precious baby. Another ad is that there is an amazing Ever since I decided to do a magazine I ad on Assassins Creed Brotherhood and an already had an idea in my head and that idea amazing ad on Clash Of Clans. There is is video games. I always loved video games articles on a strategy game called Sid Meiers it gives me something to do it entertains me Civilization 5. My reason for this magazine and it allows me to think and focus on that is to give you fans of this magazine a chance only. Nowadays the best games are the ones to learn more about video games than any online ad can tell you and also its to give you a chance to see the new games coming out or what is starting to be making. Game Enforcer is just a group of people providing you with information and telling you about the latest games. We have great ads that we think you will enjoy and we hope you enjoy them so much you buy them and have fun like so many before. A lot of the games we with the best graphics and action. Everyone likes video games so I thought it would be good to make a magazine on video games. Every person who enjoys video games I expect to buy it and that is my goal get the most sales and the best ratings than any other video game magazine. -

Windows 10-New Features & Apps
Windows 10-New Features & Apps By Tom Krauser This article discusses some of the new features and apps that come packaged in Windows 10. It is only a brief summary of these features. For more information you can search the internet or check YouTube for instructional videos on your topic of interest. The following links provide some good basic information on Windows 10 and should be helpful to you. https://support.microsoft.com/en-us/products/windows?os=windows-10 https://support.microsoft.com/en-us/help/4043948/windows-10-whats-new-in-fall-creators-update-1709 The following article from PC World Magazine provides articles on a lot of new features in Windows 10. https://www.pcworld.com/tag/windows10/ The following article by CNET discusses some of new features in the latest update to Windows 10. https://www.cnet.com/how-to/windows-10-tips-best-features/ Alarms & Clocks: A combination of alarm clock, world clock, timer, and stopwatch. Set alarms and reminders, check times around the world, and time your activities, including laps and splits. The following link discusses how to set timers, alarms, and stopwatches: https://www.howtogeek.com/225211/how-to-set-timers-alarms-and-stopwatches-in-windows-10/ Camera: Many modern devices with Windows include a webcam and, to use it, you need an app that helps you take pictures, record videos or stream video while video chatting. For this purpose, Microsoft has built an app called Camera, which is available by default in Windows 10. Connect: Use Connect App to Cast Your Smartphone Screen to Your PC. -
Quick Guide Page | 1
Quick Guide Page | 1 Contents Welcome to Windows 10 ................................................................................................................................................................................................... 3 Key innovations ...................................................................................................................................................................................................................... 3 Cortana ................................................................................................................................................................................................................................. 3 Microsoft Edge .................................................................................................................................................................................................................. 4 Gaming & Xbox ................................................................................................................................................................................................................ 5 Built-in apps ....................................................................................................................................................................................................................... 7 Enterprise-grade secure and fast ................................................................................................................................................................................... -

Understanding and Mitigating Security Risks of Voice-Controlled Third-Party Functions on Virtual Personal Assistant Systems
Dangerous Skills: Understanding and Mitigating Security Risks of Voice-Controlled Third-Party Functions on Virtual Personal Assistant Systems Nan Zhang∗, Xianghang Mi∗, Xuan Fengy∗, XiaoFeng Wang∗, Yuan Tianz and Feng Qian∗ ∗Indiana University, Bloomington Email: fnz3, xmi, xw7, [email protected] yBeijing Key Laboratory of IOT Information Security Technology, Institute of Information Engineering, CAS, China Email: [email protected] zUniversity of Virginia Email: [email protected] Abstract—Virtual personal assistants (VPA) (e.g., Amazon skills by Amazon and actions by Google1) to offer further Alexa and Google Assistant) today mostly rely on the voice helps to the end users, for example, order food, manage bank channel to communicate with their users, which however is accounts and text friends. In the past year, these ecosystems known to be vulnerable, lacking proper authentication (from the user to the VPA). A new authentication challenge, from the VPA are expanding at a breathtaking pace: Amazon claims that service to the user, has emerged with the rapid growth of the VPA already 25,000 skills have been uploaded to its skill market to ecosystem, which allows a third party to publish a function (called support its VPA (including the Alexa service running through skill) for the service and therefore can be exploited to spread Amazon Echo) [1] and Google also has more than one thousand malicious skills to a large audience during their interactions actions available on its market for its Google Home system with smart speakers like Amazon Echo and Google Home. In this paper, we report a study that concludes such remote, large- (powered by Google Assistant). -
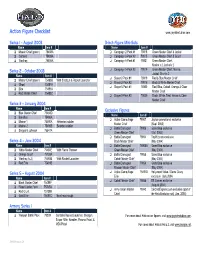
Action Figure Checklist
Action Figure Checklist www.joyridestudios.com Series 1 - August 2003 3-inch Figure Mini-Sets Name Item # Name Item # Master Chief (green) 75488A Campaign 2-Pack #1 78918 Green Master Chief & Jackal Cortana 75489A Campaign 2-Pack #2 79015 Green Master Chief & Grunt Warthog 75485A Campaign 5-Pack #1 78921 Green Master Chief, Marine x 2, Jackal x 2 Series 2 - October 2003 Campaign 5-Pack #2 79019 Green Master Chief, Marine, Jackal, Grunt x 2 Name Item # Slayer 2-Pack #1 78919 Red & Blue Master Chief Master Chief (green) 75488B With Shotgun & Rocket Launcher Slayer 2-Pack #2 79016 Black & White Master Chief Ghost 75487A Slayer 5-Pack #1 78920 Red, Blue, Cobalt, Orange & Clear Elite 75491A Master Chief Red Master Chief 75488C Slayer 5-Pack #2 79020 Black, White, Teal, Yellow & Clear Master Chief Series 3 ă January 2004 Name Item # Exclusive Figures Blue Master Chief 75488D Name Item # Banshee 75486A Active Camouflage 78907 Joyride promotional exclusive Marine 1 75490A Helmeted soldier Master Chief (Sept. 2003) Marine 2 75490B Bearded soldier Battle Damaged 78906 GameStop exclusive Sergeant Johnson 75547A Green Master Chief (Oct. 2003) Battle Damaged 79054 ToyWiz.com exclusive Series 4 ă June 2004 Black Master Chief (May 2004) Name Item # Battle Damaged 76908A GameStop exclusive White Master Chief 75488E With Flame Thrower Green Master Chief (May 2004) Orange Grunt 75739A Battle Damaged 79055 GameStop exclusive Warthog (v.2) 75485B With Rocket Launcher Cobalt Master Chief (May 2004) Red Elite 75491B Battle Damaged 79056 GameStop exclusive Maroon Master Chief (May 2004) Series 5 ă August 2004 Active Camouflage 75491D Hollywood Video / Game Crazy Elite exclusive (July 2004) Name Item # Cobalt Master Chief 79055 EB Games exclusive Black Master Chief 75488F (August 2004) Flood Carrier Form 75745A Army Green Master 79242 DieCastExpress.com exclusive (part of Red Grunt 75739B Chief the Halo Evolution set) (Jan. -

Vbscript Programmer’S Reference Third Edition
VBScript Programmer’s Reference Third Edition Adrian Kingsley-Hughes Kathie Kingsley-Hughes Daniel Read Wiley Publishing, Inc. ffirs.indd iii 8/28/07 9:41:21 AM ffirs.indd vi 8/28/07 9:41:22 AM VBScript Programmer’s Reference Third Edition Introduction . xxv Chapter 1: A Quick Introduction to Programming . 1 Chapter 2: What VBScript Is — and Isn’t! . 31 Chapter 3: Data Types . 45 Chapter 4: Variables and Procedures . 83 Chapter 5: Control of Flow . 109 Chapter 6: Error Handling and Debugging . 129 Chapter 7: The Scripting Runtime Objects . 183 Chapter 8: Classes in VBScript (Writing Your Own COM Objects) . 209 Chapter 9: Regular Expressions . 233 Chapter 10: Client-Side Web Scripting . 261 Chapter 11: Windows Sidebars and Gadgets . 287 Chapter 12: Task Scheduler Scripting . 309 Chapter 13: PowerShell . 345 Chapter 14: Super-Charged Client-Side Scripting . 375 Chapter 15: Windows Script Host . 405 Chapter 16: Windows Script Components . 465 Chapter 17: Script Encoding . 489 Chapter 18: Remote Scripting . 509 Chapter 19: HTML Applications . 517 Chapter 20: Server-Side Web Scripting . 535 Chapter 21: Adding VBScript to Your VB and .NET Applications . 569 (Continued) ffirs.indd i 8/28/07 9:41:21 AM Appendix A: VBScript Functions and Keywords . 603 Appendix B: Variable Naming Convention . 675 Appendix C: Coding Conventions . 677 Appendix D: Visual Basic Constants Supported in VBScript . 681 Appendix E: VBScript Error Codes and the Err Object . 687 Appendix F: The Scripting Runtime Library Object Reference . 703 Appendix G: The Windows Script Host Object Model . 715 Appendix H: Regular Expressions . 723 Appendix I: The Variant Subtypes .