Amazon Codeguru Profiler
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lightweight Django USING REST, WEBSOCKETS & BACKBONE
Lightweight Django USING REST, WEBSOCKETS & BACKBONE Julia Elman & Mark Lavin Lightweight Django LightweightDjango How can you take advantage of the Django framework to integrate complex “A great resource for client-side interactions and real-time features into your web applications? going beyond traditional Through a series of rapid application development projects, this hands-on book shows experienced Django developers how to include REST APIs, apps and learning how WebSockets, and client-side MVC frameworks such as Backbone.js into Django can power the new or existing projects. backend of single-page Learn how to make the most of Django’s decoupled design by choosing web applications.” the components you need to build the lightweight applications you want. —Aymeric Augustin Once you finish this book, you’ll know how to build single-page applications Django core developer, CTO, oscaro.com that respond to interactions in real time. If you’re familiar with Python and JavaScript, you’re good to go. “Such a good idea—I think this will lower the barrier ■ Learn a lightweight approach for starting a new Django project of entry for developers ■ Break reusable applications into smaller services that even more… the more communicate with one another I read, the more excited ■ Create a static, rapid prototyping site as a scaffold for websites and applications I am!” —Barbara Shaurette ■ Build a REST API with django-rest-framework Python Developer, Cox Media Group ■ Learn how to use Django with the Backbone.js MVC framework ■ Create a single-page web application on top of your REST API Lightweight ■ Integrate real-time features with WebSockets and the Tornado networking library ■ Use the book’s code-driven examples in your own projects Julia Elman, a frontend developer and tech education advocate, started learning Django in 2008 while working at World Online. -

Sun Glassfish Enterprise Server V3 Scripting Framework Guide
Sun GlassFish Enterprise Server v3 Scripting Framework Guide Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A. Part No: 820–7697–11 December 2009 Copyright 2009 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. All rights reserved. Sun Microsystems, Inc. has intellectual property rights relating to technology embodied in the product that is described in this document. In particular, and without limitation, these intellectual property rights may include one or more U.S. patents or pending patent applications in the U.S. and in other countries. U.S. Government Rights – Commercial software. Government users are subject to the Sun Microsystems, Inc. standard license agreement and applicable provisions of the FAR and its supplements. This distribution may include materials developed by third parties. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, the Solaris logo, the Java Coffee Cup logo, docs.sun.com, Enterprise JavaBeans, EJB, GlassFish, J2EE, J2SE, Java Naming and Directory Interface, JavaBeans, Javadoc, JDBC, JDK, JavaScript, JavaServer, JavaServer Pages, JMX, JRE, JSP,JVM, MySQL, NetBeans, OpenSolaris, SunSolve, Sun GlassFish, ZFS, Java, and Solaris are trademarks or registered trademarks of Sun Microsystems, Inc. or its subsidiaries in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. -

Installation Guide
Oracle® Communications Session Monitor Installation Guide Release 4.3 F27697-02 July 2020 Oracle Communications Session Monitor Installation Guide, Release 4.3 F27697-02 Copyright © 2014, 2020, Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition -

(Cont'd) Current Trends
Scripting vs Systems Programming Languages (cont’d) Designed for gluing Designed for building Does application implement complex algorithms and data applications : flexibility applications : efficiency structures? Does application process large data sets (>10,000 items)? Interpreted Compiled Are application functions well-defined, fixed? Dynamic variable creation Variable declaration If yes, consider a system programming language. Data and code integrated : Data and code separated : meta-programming cannot create/run code on Is the main task to connect components, legacy apps? supported the fly Does the application manipulate a variety of things? Does the application have a GUI? Dynamic typing (typeless) Static typing Are the application's functions evolving rapidly? Examples: PERL, Tcl, Examples: PL/1, Ada, Must the application be extensible? Python, Ruby, Scheme, Java, C/C++, C#, etc Does the application do a lot of string manipulation? Visual Basic, etc If yes, consider a scripting language. cs480 (Prasad) LSysVsScipt 1 cs480 (Prasad) LSysVsScipt 2 Current Trends Jython (for convenient access to Java APIs) Hybrid Languages : Scripting + Systems Programming I:\tkprasad\cs480>jython – Recent JVM-based Scripting Languages Jython 2.1 on java1.4.1_02 (JIT: null) Type "copyright", "credits" or "license" for more information. »Jython : Python dialect >>> import javax.swing as swing >>> win = swing.JFrame("Welcome to Jython") »Clojure : LISP dialect >>> win.size = (200, 200) »Scala : OOP +Functional Hybrid >>> win.show() -

Bepasty Documentation Release 0.3.0
bepasty Documentation Release 0.3.0 The Bepasty Team (see AUTHORS file) Jul 02, 2019 Contents 1 Contents 3 1.1 bepasty..................................................3 1.2 Using bepasty’s web interface......................................4 1.3 Using bepasty with non-web clients...................................6 1.4 Quickstart................................................7 1.5 Installation tutorial with Debian, NGinx and gunicorn......................... 10 1.6 ChangeLog................................................ 12 1.7 The bepasty software Project....................................... 14 1.8 License.................................................. 14 1.9 Authors.................................................. 15 Index 17 i ii bepasty Documentation, Release 0.3.0 bepasty is like a pastebin for every kind of file (text, image, audio, video, documents, . ). You can upload multiple files at once, simply by drag and drop. Contents 1 bepasty Documentation, Release 0.3.0 2 Contents CHAPTER 1 Contents 1.1 bepasty bepasty is like a pastebin for all kinds of files (text, image, audio, video, documents, . , binary). The documentation is there: http://bepasty-server.readthedocs.org/en/latest/ 1.1.1 Features • Generic: – you can upload multiple files at once, simply by drag and drop – after upload, you get a unique link to a view of each file – on that view, we show actions you can do with the file, metadata of the file and, if possible, we also render the file contents – if you uploaded multiple files, you can create a pastebin with the list -

Zope Documentation Release 5.3
Zope Documentation Release 5.3 The Zope developer community Jul 31, 2021 Contents 1 What’s new in Zope 3 1.1 What’s new in Zope 5..........................................4 1.2 What’s new in Zope 4..........................................4 2 Installing Zope 11 2.1 Prerequisites............................................... 11 2.2 Installing Zope with zc.buildout .................................. 12 2.3 Installing Zope with pip ........................................ 13 2.4 Building the documentation with Sphinx ............................... 14 3 Configuring and Running Zope 15 3.1 Creating a Zope instance......................................... 16 3.2 Filesystem Permissions......................................... 17 3.3 Configuring Zope............................................. 17 3.4 Running Zope.............................................. 18 3.5 Running Zope (plone.recipe.zope2instance install)........................... 20 3.6 Logging In To Zope........................................... 21 3.7 Special access user accounts....................................... 22 3.8 Troubleshooting............................................. 22 3.9 Using alternative WSGI server software................................. 22 3.10 Debugging Zope applications under WSGI............................... 26 3.11 Zope configuration reference....................................... 27 4 Migrating between Zope versions 37 4.1 From Zope 2 to Zope 4 or 5....................................... 37 4.2 Migration from Zope 4 to Zope 5.0.................................. -

Oracle Communications Operations Monitor Licensing Information User Manual Licensing Information
Oracle® Communications Operations Monitor Licensing Information User Manual Release 4.4.0 E99936-01 December 2020 Copyright © 2000, 2020, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are “commercial computer software” pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. -

Characteristics of Dynamic JVM Languages
Characteristics of Dynamic JVM Languages Aibek Sarimbekov Andrej Podzimek Lubomir Bulej University of Lugano Charles University in Prague University of Lugano fi[email protected] [email protected]ff.cuni.cz fi[email protected] Yudi Zheng Nathan Ricci Walter Binder University of Lugano Tufts University University of Lugano fi[email protected] [email protected] fi[email protected] Abstract However, since the JVM was originally conceived for The Java Virtual Machine (JVM) has become an execution a statically-typed language, the performance of the JVM platform targeted by many programming languages. How- and its JIT compiler with dynamically-typed languages is ever, unlike with Java, a statically-typed language, the per- often lacking, lagging behind purpose-built language-specific formance of the JVM and its Just-In-Time (JIT) compiler JIT compilers. Making the JVM perform well with various with dynamically-typed languages lags behind purpose-built statically- and dynamically-typed languages clearly requires language-specific JIT compilers. In this paper, we aim to significant effort, not only in optimizing the JVM itself, but contribute to the understanding of the workloads imposed on also, more importantly, in optimizing the bytecode-emitting the JVM by dynamic languages. We use various metrics to language compiler, instead of just relying on the original JIT characterize the dynamic behavior of a variety of programs to gain performance [8]. This in turn requires that developers written in three dynamic languages (Clojure, Python, and of both the language compilers and the JVM understand the Ruby) executing on the JVM. We identify the differences characteristics of the JVM workloads produced by various with respect to Java, and briefly discuss their implications. -

Debian Java Insights and Challenges
Debian Java Insights and challenges Markus Koschany FOSDEM 19 Brussels / Belgium February, 3rd 2019 Markus Koschany Debian Java: Insights and challenges FOSDEM 19 1/7 The importance of Java Source / binary packages maintained by the Java team: 1033 / 1644 (+10,84 % since Debian 9) Source lines of code (Rank 3) : 90,744,884 Popcon value OpenJDK-8 (installed): 78104 / 199604 Popular libraries: apache-commons-*, javamail, xerces2, bouncycastle Popular applications: libreoffice, netbeans, pdfsam, sweethome3d, freeplane, freecol Frequently used for scientific research, medical care and bioinformatics. Markus Koschany Debian Java: Insights and challenges FOSDEM 19 2/7 What is new in Buster? OpenJDK 11 transition completed. (required more than 400! package updates) Build tools: Ant and Maven are up-to-date. Gradle is stuck at the last pre-Kotlin version. SBT is still being worked on. JVM languages: Groovy 2.14, Scala 2.11.12 (2.12 requires SBT), Clojure 1.9, Jython 1.7.1, JRuby 9.1.13 (?), Kotlin is wanted but hard to bootstrap. IDE: Eclipse is gone (lack of maintainers) but there is Netbeans 10 now. Server: Jetty 9.4 and Tomcat 9 fully up-to-date with systemd integration. Reproducibility rate is at 85% (was 75%) https://reproducible-builds.org Markus Koschany Debian Java: Insights and challenges FOSDEM 19 3/7 Packaging challenges “None of the packages in the main archive area require software outside of that area to function” Internet downloads at build time are not allowed No prebuilt jar or class files! Java is version-centric. Every developer has to update every dependency themself in this model. -

Reading the Runes for Java Runtimes the Latest IBM Java Sdks
Java Technology Centre Reading the runes for Java runtimes The latest IBM Java SDKs ... and beyond Tim Ellison [email protected] © 2009 IBM Corporation Java Technology Centre Goals . IBM and Java . Explore the changing landscape of hardware and software influences . Discuss the impact to Java runtime technology due to these changes . Show how IBM is leading the way with these changes 2 Mar 9, 2009 © 2009 IBM Corporation Java Technology Centre IBM and Java . Java is critically important to IBM – Provides fundamental infrastructure to IBM software portfolio – Delivers standard development environment – Enables cost effective multi platform support – Delivered to Independent Software Vendors supporting IBM server platforms . IBM is investing strategically in virtual machine technology – Since Java 5.0, a single Java platform technology supports ME, SE and EE – Technology base on which to delivery improved performance, reliability and serviceability • Some IBM owned code (Virtual machine, JIT compiler, ...) • Some open source code (Apache XML parser, Apache Core libraries, Zlib, ...) • Some Sun licensed code (class libraries, tools, ...) . Looking to engender accelerated and open innovation in runtime technologies – Support for Eclipse, Apache (Harmony, XML, Derby, Geronimo, Tuscany) – Broad participation of relevant standards bodies such as JCP and OSGi 3 Mar 9, 2009 © 2009 IBM Corporation Java Technology Centre IBM Java – 2009 key initiatives . Consumability – Deliver value without complexity. – Ensure that problems with our products can be addressed quickly, allowing customers to keep focus on their own business issues. – Deliver a consistent model for solving customer problems. “Scaling Up” - Emerging hardware and applications – Provide a Java implementation that can scale to the most demanding application needs. -

Glassfish Server 3.0.1 Scripting Framework Guide
Oracle® GlassFish Server 3.0.1 Scripting Framework Guide Part No: 821–1760–10 June 2010 Copyright © 2010, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related software documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are “commercial computer software” or “commercial technical data” pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms setforth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). Oracle America, Inc., 500 Oracle Parkway, Redwood City, CA 94065. -
Hitachi Cloud Accelerator Platform Product Manager HCAP V 1
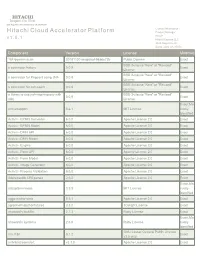
HITACHI Inspire the Next 2535 Augustine Drive Santa Clara, CA 95054 USA Contact Information : Hitachi Cloud Accelerator Platform Product Manager HCAP v 1 . 5 . 1 Hitachi Vantara LLC 2535 Augustine Dr. Santa Clara CA 95054 Component Version License Modified 18F/domain-scan 20181130-snapshot-988de72b Public Domain Exact BSD 3-clause "New" or "Revised" a connector factory 0.0.9 Exact License BSD 3-clause "New" or "Revised" a connector for Pageant using JNA 0.0.9 Exact License BSD 3-clause "New" or "Revised" a connector for ssh-agent 0.0.9 Exact License a library to use jsch-agent-proxy with BSD 3-clause "New" or "Revised" 0.0.9 Exact sshj License Exact,Ma activesupport 5.2.1 MIT License nually Identified Activiti - BPMN Converter 6.0.0 Apache License 2.0 Exact Activiti - BPMN Model 6.0.0 Apache License 2.0 Exact Activiti - DMN API 6.0.0 Apache License 2.0 Exact Activiti - DMN Model 6.0.0 Apache License 2.0 Exact Activiti - Engine 6.0.0 Apache License 2.0 Exact Activiti - Form API 6.0.0 Apache License 2.0 Exact Activiti - Form Model 6.0.0 Apache License 2.0 Exact Activiti - Image Generator 6.0.0 Apache License 2.0 Exact Activiti - Process Validation 6.0.0 Apache License 2.0 Exact Addressable URI parser 2.5.2 Apache License 2.0 Exact Exact,Ma adzap/timeliness 0.3.8 MIT License nually Identified aggs-matrix-stats 5.5.1 Apache License 2.0 Exact agronholm/pythonfutures 3.3.0 3Delight License Exact ahoward's lockfile 2.1.3 Ruby License Exact Exact,Ma ahoward's systemu 2.6.5 Ruby License nually Identified GNU Lesser General Public License ai's