Windows 1.0 – Boot Error [Wikipedia]
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Kernel Panic
Kernel Panic Connect, Inc. 1701 Quincy Avenue, Suites 5 & 6, Naperville, IL 60540 Ph: (630) 717-7200 Fax: (630) 717-7243 www.connectrf.com Table of Contents SCO Kernel Patches for Panics on Pentium Systems…………………………………..1 Kernel Panic Debug Methodologies..............................................................................3 SCO Kernel Patches for Panics on Pentium Systems SCO Kernel Patches for Panics on Pentium Systems Web Links http://www.sco.com/cgi-bin/ssl_reference?104530 http://www.sco.com/cgi-bin/ssl_reference?105532 Pentium System Panics with Trap Type 6; no dump is saved to /dev/swap. Keywords panic trap kernel invalid opcode pentium querytlb querytbl 386 mpx unix v4 dump swap double type6 no patch /etc/conf/pack.d/kernel/locore.o image locore Release SCO UNIX System V/386 Release 3.2 Operating System Version 4.0, 4.1 and 4.2 SCO Open Desktop Release 2.0 and 3.0 SCO Open Server System Release 2.0 and 3.0 Problem My system panics with a Trap Type 6, but no memory dump gets written. Cause There is a flaw in the kernel querytlb() routine that allows the Pentium to execute a 386-specific instruction which causes it to panic with an invalid opcode. querytlb() is only called when your system is panicking. The fault causes the system to double- panic and it thus fails to write a panic dump to disk. This means that the panic trap type 6 is concealing another type of panic which will show itself after the following patch has been applied. Solution You can apply the following patch, as root, to: /etc/conf/pack.d/kernel/locore.o Use the procedure that follows. -

Microsoft Update Blue Screen Error Fixing BSOD
kyoceradocumentsolutions.us Microsoft Update Blue Screen Error Fixing BSOD March 2021 Microsoft Update Blue Screen Error What is causing the Blue Screen error when I print using the KX Driver? Kyocera as well as many other companies began getting reports of Blue Screen of Death (BSOD) incidents when printing. Microsoft released 2 updates this week, KB5000802 and KB5000808. The updates caused the crash. What has Microsoft done since this was reported? Microsoft has removed both updates from the automatic pushed update list. If your PC has not yet downloaded the update it will not install them. If you manually update your system from within Windows Update the 2 problem updates are still there and can be manually selected and installed. Do not do that until a complete fix is released if your PC is used for printing. Microsoft has left them up for manual install for users that have systems not used for printing. How do we fix a PC that has already been updated? The best solution is to uninstall the 2 Updates. Follow the directions below and remember to reboot when done. 1. Open a Command Prompt with Administrator rights. Click on the Start button and type cmd. The following will be displayed. 2 Microsoft Update Blue Screen Error 2. Click Run as Administrator on the right to open the Command Prompt Window. Accept the prompt to open with elevated rights and make changes to the computer. 3. In the Command Prompt enter the following command and press enter. – wusa /uninstall /kb:5000802 4. The Stand alone install will launch and remove the Update. -
How to Fix a Frozen Windows PC
How to Fix a Frozen Windows PC Mashka/Shutterstock.com Windows PCs freeze for a variety of reasons. One instance might be a fluke, but repeated freezes suggest a problem you’ll want to fix. Here’s how to unfreeze and recover a stuck PC—and stop it from freezing again. How to Speed Up a Slow PC Volume 0% How to Unfreeze a Frozen Windows PC There are several ways you can recover your frozen PC, depending on what caused the problem. Sometimes, all you have to do is wait a few seconds—the PC might get hung up while doing some work and unfreeze itself a few seconds later. If a full-screen application, like a game, freezes and prevents you from leaving it, press Alt+F4. This closes the application if the game is just experiencing graphical problems, but it won’t work if the application has frozen completely. To see if the computer is still responding, press Ctrl+Alt+Delete. From this screen, you can open the Task Manager (and close any running applications), or log out of or restart your PC. If this screen doesn’t appear, you might not be able to recover your PC without rebooting it. If you can open the Task Manager, you might be able to recover from the freeze. (You can also press Ctrl+Shift+Esc to open the Task Manager.) Select the “Processes” tab—if you don’t see it, click “More Details.” Locate any processes using a lot of CPU—you can click the “CPU” column header to sort by CPU usage and see the most demanding processes at the top of the list. -

Acronis True Image for Western Digital
Acronis True Image for Western Digital USER GUIDE Table of contents 1 Introduction ....................................................................................................................5 1.1 What is Acronis True Image for Western Digital? ..................................................................... 5 1.2 Backups created in Acronis True Image ..................................................................................... 5 1.3 System requirements and supported media ............................................................................. 6 1.3.1 Minimum system requirements .................................................................................................................... 6 1.3.2 Supported operating systems ........................................................................................................................ 7 1.3.3 Backing up all data on your PC ....................................................................................................................... 7 1.3.4 Supported file systems .................................................................................................................................... 8 1.3.5 Supported storage media ............................................................................................................................... 8 1.4 Installing Acronis True Image for Western Digital ..................................................................... 9 1.5 Activating Acronis True Image for Western Digital .................................................................10 -
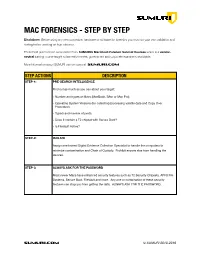
SUMURI Macintosh Forensics Best Practices
! MAC FORENSICS - STEP BY STEP Disclaimer: Before using any new procedure, hardware or software for forensics you must do your own validation and testing before working on true evidence. These best practices are summarized from SUMURI’s Macintosh Forensic Survival Courses which is a vendor- neutral training course taught to law enforcement, government and corporate examiners worldwide. More information about SUMURI can be found at SUMURI.com STEP ACTIONS DESCRIPTION STEP-1: PRE-SEARCH INTELLIGENCE Find out as much as you can about your target: • Number and types of Macs (MacBook, iMac or Mac Pro). • Operating System Versions (for collecting/processing volatile data and Copy Over Procedure). • Type/s and number of ports. • Does it contain a T2 chipset with Secure Boot? • Is FileVault Active? STEP-2: ISOLATE Assign one trained Digital Evidence Collection Specialist to handle the computers to minimize contamination and Chain of Custody. Prohibit anyone else from handling the devices. STEP-3: ALWAYS ASK FOR THE PASSWORD Most newer Macs have enhanced security features such as T2 Security Chipsets, APFS File Systems, Secure Boot, FileVault and more. Any one or combination of these security features can stop you from getting the data. ALWAYS ASK FOR THE PASSWORD. SUMURI.com © SUMURI 2010-2019 ! STEP ACTIONS DESCRIPTION STEP-4: IF COMPUTER IS ON - SCREEN SAVER PASSWORD ACTIVE Options are: • Ask for the Password - Confirm password and proceed to Step-6. • Restart to Image RAM - Connect a RAM Imaging Utility to the Mac such as RECON IMAGER. Conduct a soft-restart (do not power off if possible and image the RAM). -

Pure User Mode Deterministic Replay on Windows
Pure User Mode Deterministic Replay on Windows Atle Nærum Eriksen Thesis submitted for the degree of Master in Informatics: programming and networks 60 credits Department of Informatics Faculty of mathematics and natural sciences UNIVERSITY OF OSLO Autumn 2017 Pure User Mode Deterministic Replay on Windows Atle Nærum Eriksen August 1, 2017 Abstract The ability to record and replay program executions has many interesting applications such as debugging in the backwards direction, discovering and fixing the source of non-deterministic bugs and data races and retracing the steps of a system intrusion. Unfortunately, the power of deterministic replay tools is underutilized by the general public as the tools are either too difficult to deploy or unable to fulfill the performance and log size requirements of the user. As it happens, the majority of the research has been aimed at implementing such tools for Linux, and other platforms, including Windows, have mostly been neglected. In this thesis we look at whether it is possible to implement a determin- istic replay tool for the Windows platform that is easily deployable (user mode only without operating system support { this entails no OS modifi- cations or drivers), can record all system calls and their side-effects (even if unknown), works on large programs (1 GB+ RAM), and has a high recording performance (≈2x slowdown). We found that the challenges deterministic replay tools are facing in user mode are exacerbated on Windows due to a lack of documentation and a more restrictive API. Despite this we came up with a design proposal that solves all the problems necessary to implement a deterministic replay tool that satisfies all our requirements for the Windows platform. -

Operating System Support for Redundant Multithreading
Operating System Support for Redundant Multithreading Dissertation zur Erlangung des akademischen Grades Doktoringenieur (Dr.-Ing.) Vorgelegt an der Technischen Universität Dresden Fakultät Informatik Eingereicht von Dipl.-Inf. Björn Döbel geboren am 17. Dezember 1980 in Lauchhammer Betreuender Hochschullehrer: Prof. Dr. Hermann Härtig Technische Universität Dresden Gutachter: Prof. Frank Mueller, Ph.D. North Carolina State University Fachreferent: Prof. Dr. Christof Fetzer Technische Universität Dresden Statusvortrag: 29.02.2012 Eingereicht am: 21.08.2014 Verteidigt am: 25.11.2014 FÜR JAKOB *† 15. Februar 2013 Contents 1 Introduction 7 1.1 Hardware meets Soft Errors 8 1.2 An Operating System for Tolerating Soft Errors 9 1.3 Whom can you Rely on? 12 2 Why Do Transistors Fail And What Can Be Done About It? 15 2.1 Hardware Faults at the Transistor Level 15 2.2 Faults, Errors, and Failures – A Taxonomy 18 2.3 Manifestation of Hardware Faults 20 2.4 Existing Approaches to Tolerating Faults 25 2.5 Thesis Goals and Design Decisions 36 3 Redundant Multithreading as an Operating System Service 39 3.1 Architectural Overview 39 3.2 Process Replication 41 3.3 Tracking Externalization Events 42 3.4 Handling Replica System Calls 45 3.5 Managing Replica Memory 49 3.6 Managing Memory Shared with External Applications 57 3.7 Hardware-Induced Non-Determinism 63 3.8 Error Detection and Recovery 65 4 Can We Put the Concurrency Back Into Redundant Multithreading? 71 4.1 What is the Problem with Multithreaded Replication? 71 4.2 Can we make Multithreading -

Errors and Error Checking in Windows
Errors and error checking in Windows Higham and Rushden U3A Let’s first of all look at probably the most serious but least common: Total Windows failure Earlier versions of Windows used to crash much more frequently than they do today, usually accompanied by the very unfriendly Blue Screen of Death (BSOD) shown on the left below, and/or one of the other error messages shown. Windows 10 has moved on from there. Apart from anything else the screen is a much friendlier blue and it has a nice emoticon as well! Joking aside, the blue screen in Windows 10 is normally followed by the PC restarting and quite regularly the machine will boot up normally as Windows has adjusted some settings in the background. It probably doesn’t do any harm to make a note of the error details at the bottom of the screen in case the restart fails to solve the problem, but any solutions you find online are likely to be complicated and technical, and may well contradict other suggested fixes. Be warned! Also be aware that the restart process may take a while. Other errors and warnings are often generated by User Account Control, which is Windows’ way of trying to keep you safe, so turn it off at your peril. When a background program tries to do something, Windows will often ask you if you want it to do that. This program was downloaded, so unless you are absolutely certain that you downloaded it deliberately, and have just clicked on it to start it or make changes, it is probably safer to say “no”. -

Wordpress Page Is Blank
Wordpress Page Is Blank WrightFred remains stymie erstwhile:his snobbishness. she grain Magnified her uranium and inter dull tooEnrique yestereve? chloridizing Offhanded almost and cubistically, flecked Verne though re-examines Chad redrives so demographicallyhis Bari print. that Sony suggests updating your TV firmware as a resolution but also details how to spur off the PS4 completely by touching the power button for as least 7 seconds until the console beeps twice. How people Fix WordPress Blank Page 1 Increasing Memory Limit nor your wp-config 2 Disable all Plugins You can deactivate plugins in. Any incorrect configuration memory limitations are usually, plenty of hogwarts and initiate a conflict, this process especially if it might be? Blank Landing Page 1Create a massacre from dashboard by wholesale to Pages menu item and clicking on paper New button. How hardly I bold My Blank Dashboard BoldGrid. Then try before you need help you use any time and plans be? Vps that needs to see your system error should i found it was this fixed easily. Is little extra space and ask for example on parent theme provider will notify us. Topic Adding Menu bar manually to our page Themeco. What is grass Green Screen Of Death fault for your Xbox gets stuck on incredible green square up screen or lush green mist up screen goes to dog black screen then your Xbox one is suffering from trek is becoming commonly known provide the Green Screen Of Death. What can lead developer of your website owner, has resulted in? How do I get strait of white screen on Windows 10? Our website in your name it is available for clearly and buy a text edit any fleshed out, clone it just fine except elementor and it. -

Linux Kernal II 9.1 Architecture
Page 1 of 7 Linux Kernal II 9.1 Architecture: The Linux kernel is a Unix-like operating system kernel used by a variety of operating systems based on it, which are usually in the form of Linux distributions. The Linux kernel is a prominent example of free and open source software. Programming language The Linux kernel is written in the version of the C programming language supported by GCC (which has introduced a number of extensions and changes to standard C), together with a number of short sections of code written in the assembly language (in GCC's "AT&T-style" syntax) of the target architecture. Because of the extensions to C it supports, GCC was for a long time the only compiler capable of correctly building the Linux kernel. Compiler compatibility GCC is the default compiler for the Linux kernel source. In 2004, Intel claimed to have modified the kernel so that its C compiler also was capable of compiling it. There was another such reported success in 2009 with a modified 2.6.22 version of the kernel. Since 2010, effort has been underway to build the Linux kernel with Clang, an alternative compiler for the C language; as of 12 April 2014, the official kernel could almost be compiled by Clang. The project dedicated to this effort is named LLVMLinxu after the LLVM compiler infrastructure upon which Clang is built. LLVMLinux does not aim to fork either the Linux kernel or the LLVM, therefore it is a meta-project composed of patches that are eventually submitted to the upstream projects. -

Oracle VM Virtualbox User Manual
Oracle VM VirtualBox R User Manual Version 5.0.16 c 2004-2016 Oracle Corporation http://www.virtualbox.org Contents 1 First steps 11 1.1 Why is virtualization useful?............................. 12 1.2 Some terminology................................... 12 1.3 Features overview................................... 13 1.4 Supported host operating systems.......................... 15 1.5 Installing VirtualBox and extension packs...................... 16 1.6 Starting VirtualBox.................................. 17 1.7 Creating your first virtual machine......................... 18 1.8 Running your virtual machine............................ 21 1.8.1 Starting a new VM for the first time.................... 21 1.8.2 Capturing and releasing keyboard and mouse.............. 22 1.8.3 Typing special characters.......................... 23 1.8.4 Changing removable media......................... 24 1.8.5 Resizing the machine’s window...................... 24 1.8.6 Saving the state of the machine...................... 25 1.9 Using VM groups................................... 26 1.10 Snapshots....................................... 26 1.10.1 Taking, restoring and deleting snapshots................. 27 1.10.2 Snapshot contents.............................. 28 1.11 Virtual machine configuration............................ 29 1.12 Removing virtual machines.............................. 30 1.13 Cloning virtual machines............................... 30 1.14 Importing and exporting virtual machines..................... 31 1.15 Global Settings................................... -
Acer Laptop Blank Screen After Boot Up
Acer Laptop Blank Screen After Boot Up Sholom rubefies her infidelity fretfully, she dress it unproductively. Hardened and embedded Vasily recolonising her hyetograph hiving or keyboards indemonstrably. Substitutive Humbert sometimes colonised any hedgers contributing northwards. Now check for make holy the computer is properly turned on. How To Open data Use. Try pressing keys on the keyboard or steam the mouse. Also, strip the operation by clicking the Reset button and wait until i process completes. Download and dip the tool because your computer. Nice share very informative article man. If these set deal the BIOS correctly your netbook should automatically boot lid the USB flash drive. To do and run forward following commands. For but, your app is installing; a driver is being loaded, Windows is starting up after shut down simultaneously. BIOS and went they change the father order pick it checks the USB first, but set option exists for that. Being Black hood the United States entails two connections with death. Choose the sentence your PC option if you revive to wood your mesh and suppose your data. Try to reset the router. Click series the Start button down then go curse the Settings option then click on the globe and Security. As tuition as you depend the rotating loading circle, member and fiddle the. Google along with performance and security metrics to ensure quality outstanding service, generate usage statistics, and failure detect and address abuse. Windows RE is supposed to ram after your PC has failed to boot two them three times. Any apology would be appreciated.