That All Ultimiti
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Texting on a Smartwatch Versus a Smartphone: a Comparison of Their Effects on Driving Performance
TEXTING ON A SMARTWATCH VERSUS A SMARTPHONE: A COMPARISON OF THEIR EFFECTS ON DRIVING PERFORMANCE A Dissertation by Joel Persinger Master of Arts, Wichita State University, 2014 Bachelor of Science, Eastern Kentucky University, 2005 Submitted to the Department of Psychology and the faculty of the Graduate School of Wichita State University in partial fulfillment of the requirements for the degree of Doctor of Philosophy December 2017 ©Copyright 2017 by Joel A. Persinger All Rights Reserved TEXTING ON A SMARTWATCH VERSUS A SMARTPHONE: A COMPARISON OF THEIR EFFECTS ON DRIVING PERFORMANCE The following faculty members have examined the final copy of this dissertation for form and content, and recommend that it be accepted in partial fulfillment of the requirement for the degree of Doctor of Philosophy, with a major in Psychology. _____________________________________________ Rui Ni, Committee Chair _____________________________________________ Alex Chaparro, Committee Member _____________________________________________ Barbara Chaparro, Committee Member _____________________________________________ Jibo He, Committee Member _____________________________________________ Jeremy Patterson, Committee Member Accepted for the College of Liberal Arts and Sciences _______________________________________________ Ron Matson, Dean Accepted for the Graduate School _______________________________________________ Dennis Livesay, Dean iii DEDICATION To my beautiful wife, who has pushed me to go further than I ever thought I could. She has truly carried me though graduate school with love and encouragement. iv ABSTRACT The National Safety Council reports that 6 percent or more car crashes involved text messaging from a smartphone. In addition, many studies have found that cell phone while driving increases crash risk by 2.8–5 times (Klauer et al. 2006; Redelmeier and Tibshirani 1997; Violanti 1998; Violanti and Marshall 1996). -

Cross-Platform Analysis of Indirect File Leaks in Android and Ios Applications
Cross-Platform Analysis of Indirect File Leaks in Android and iOS Applications Daoyuan Wu and Rocky K. C. Chang Department of Computing, The Hong Kong Polytechnic University fcsdwu, [email protected] This paper was published in IEEE Mobile Security Technologies 2015 [47] with the original title of “Indirect File Leaks in Mobile Applications”. Victim App Abstract—Today, much of our sensitive information is stored inside mobile applications (apps), such as the browsing histories and chatting logs. To safeguard these privacy files, modern mobile Other systems, notably Android and iOS, use sandboxes to isolate apps’ components file zones from one another. However, we show in this paper that these private files can still be leaked by indirectly exploiting components that are trusted by the victim apps. In particular, Adversary Deputy Trusted we devise new indirect file leak (IFL) attacks that exploit browser (a) (d) parties interfaces, command interpreters, and embedded app servers to leak data from very popular apps, such as Evernote and QQ. Unlike the previous attacks, we demonstrate that these IFLs can Private files affect both Android and iOS. Moreover, our IFL methods allow (s) an adversary to launch the attacks remotely, without implanting malicious apps in victim’s smartphones. We finally compare the impacts of four different types of IFL attacks on Android and Fig. 1. A high-level IFL model. iOS, and propose several mitigation methods. four IFL attacks affect both Android and iOS. We summarize these attacks below. I. INTRODUCTION • sopIFL attacks bypass the same-origin policy (SOP), Mobile applications (apps) are gaining significant popularity which is enforced to protect resources originating from in today’s mobile cloud computing era [3], [4]. -

UPLC™ Universal Power-Line Carrier
UPLC™ Universal Power-Line Carrier CU4I-VER02 Installation Guide AMETEK Power Instruments 4050 N.W. 121st Avenue Coral Springs, FL 33065 1–800–785–7274 www.pulsartech.com THE BRIGHT STAR IN UTILITY COMMUNICATIONS March 2006 Trademarks All terms mentioned in this book that are known to be trademarks or service marks are listed below. In addition, terms suspected of being trademarks or service marks have been appropriately capital- ized. Ametek cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. This publication includes fonts and/or images from CorelDRAW which are protected by the copyright laws of the U.S., Canada and elsewhere. Used under license. IBM and PC are registered trademarks of the International Business Machines Corporation. ST is a registered trademark of AT&T Windows is a registered trademark of Microsoft Corp. Universal Power-Line Carrier Installation Guide ESD WARNING! YOU MUST BE PROPERLY GROUNDED, TO PREVENT DAMAGE FROM STATIC ELECTRICITY, BEFORE HANDLING ANY AND ALL MODULES OR EQUIPMENT FROM AMETEK. All semiconductor components used, are sensitive to and can be damaged by the discharge of static electricity. Be sure to observe all Electrostatic Discharge (ESD) precautions when handling modules or individual components. March 2006 Page i Important Change Notification This document supercedes the preliminary version of the UPLC Installation Guide. The following list shows the most recent publication date for the new information. A publication date in bold type indicates changes to that information since the previous publication. -

SMM Rootkits
SMM Rootkits: A New Breed of OS Independent Malware Shawn Embleton Sherri Sparks Cliff Zou University of Central Florida University of Central Florida University of Central Florida [email protected] [email protected] [email protected] ABSTRACT 1. INTRODUCTION The emergence of hardware virtualization technology has led to A rootkit consists of a set of programs that work to subvert the development of OS independent malware such as the Virtual control of an Operating System from its legitimate users [16]. If Machine based rootkits (VMBRs). In this paper, we draw one were asked to classify viruses and worms by a single defining attention to a different but related threat that exists on many characteristic, the first word to come to mind would probably be commodity systems in operation today: The System Management replication. In contrast, the single defining characteristic of a Mode based rootkit (SMBR). System Management Mode (SMM) rootkit is stealth. Viruses reproduce, but rootkits hide. They hide is a relatively obscure mode on Intel processors used for low-level by compromising the communication conduit between an hardware control. It has its own private memory space and Operating System and its users. Secondary to hiding themselves, execution environment which is generally invisible to code rootkits are generally capable of gathering and manipulating running outside (e.g., the Operating System). Furthermore, SMM information on the target machine. They may, for example, log a code is completely non-preemptible, lacks any concept of victim user’s keystrokes to obtain passwords or manipulate the privilege level, and is immune to memory protection mechanisms. -

Securing and Managing Wearables in the Enterprise
White Paper: Securing and Managing Wearables in the Enterprise Streamline deployment and protect smartwatch data with Samsung Knox Configure White Paper: Securing and Managing Wearables in the Enterprise 2 Introduction: Smartwatches in the Enterprise As the wearable device market heats up, wrist-worn devices Industries as varied as healthcare, such as smartwatches are leading the pack. According to CCS Insight, forecasts for global sales of smart wearable devices finance, energy, transportation, will grow strongly over the next five years, with the global public safety, retail and hospitality market reaching nearly $30 billion by 2023.1 are deploying smartwatches for While smartwatches for fitness and activity tracking are popular, consumer demand is only part of the equation. added business value. Enterprises are also seeing business value in wearable devices. In a report by Robert Half Technology, 81 percent of CIOs surveyed expect wearable devices like smartwatches to Samsung has been working to address these concerns and become common tools in the workplace.2 has developed the tools to make its Galaxy and Galaxy Active smartwatches customizable, easily manageable and highly secure for enterprise users. This white paper will look at how these tools address key wearable security and manageability challenges, as well as considerations for smartwatch 81% deployments. of CIOs surveyed expect wearable devices like smartwatches to become common tools in the workplace. Industries as varied as healthcare, finance, energy, transportation, public safety, retail and hospitality are deploying smartwatches for added business value, such as hands-free communication for maintenance workers, task management, as well as physical monitoring of field workers in dangerous or remote locations. -

Nujj University of California, Berkeley School of Information Karen Hsu
Nujj University of California, Berkeley School of Information Karen Hsu Kesava Mallela Alana Pechon Nujj • Table of Contents Abstract 1 Introduction 2 Problem Statement 2 Objective 2 Literature Review 3 Competitive Analysis 4 Comparison matrix 4 Competition 5 Hypothesis 6 Use Case Scenarios 7 Overall System Design 10 Server-side 12 Design 12 Implementation 12 Twitter and Nujj 14 Client-side 15 Design 17 Implementation 17 Future Work 18 Extended Functionality in Future Implementations 18 Acknowledgements 19 Abstract Nujj is a location based service for mobile device users that enables users to tie electronic notes to physical locations. It is intended as an initial exploration into some of the many scenarios made possible by the rapidly increasing ubiquity of location-aware mobile devices. It should be noted that this does not limit the user to a device with a GPS embedded; location data can now also be gleaned through methods such as cell tower triangulation and WiFi IP address lookup. Within this report, both social and technical considerations associated with exposing a user’s location are discussed. The system envisioned addresses privacy concerns, as well as attempts to overcome the poor rate of adoption of current location based services already competing in the marketplace. Although several possible use cases are offered, it is the authors’ firm belief that a well-designed location- based service should not attempt to anticipate all, or even most, of the potential ways that users will find to take advantage of it. Rather, the service should be focused on building a system that is sufficiently robust yet flexible to allow users to pursue their own ideas. -

Apple and Nokia: the Transformation from Products to Services
9 Apple and Nokia: The Transformation from Products to Services In the mid- to late 2000s, Nokia flourished as the world’s dominant mobile phone – and mobile phone operating software – producer. Founded in 1871 originally as a rubber boots manufacturer, by 2007 Nokia produced more than half of all mobile phones sold on the planet, and its Symbian mobile operating system commanded a 65.6 percent global market share. 1 But within half a decade, Nokia would falter and be surpassed in the smartphone market not only by Apple’s revolu- tionary iPhone but also by competitors including Google and Samsung. And in September 2013, Nokia would sell its mobile phone business to Microsoft for $7 billion. 2 Apple literally came out of nowhere – it sold exactly zero mobile phones before the year 2007 (the year Nokia held more than half of the global market share) – but by the first quarter of 2013, Apple had captured almost 40 percent of the US smartphone market and over 50 percent of the operating profit in the global handset industry.3 In fiscal year 2013, Apple would sell five times more smart- phones than Nokia: 150 million iPhones compared to Nokia’s sales of 30 million Lumia Windows phones. 4 In contrast to Nokia, Apple real- ized it wasn’t just about the mobile device itself, it was about leveraging software to create a platform for developing compelling mobile experi- ences – including not just telephony but also music, movies, applica- tions, and computing – and then building a business model that allows partners to make money alongside the company (e.g., Apple’s iTunes and AppStore) and, in so doing, perpetuate a virtuous cycle of making the iPhone attractive to customers over multiple life cycles through ever-ex- panding feature sets. -

UI Design for Wearable Devices
FACULTY OF ENGINEERING UNIVERSITY OF PORTO UI Design for Wearable Devices Vitor Mota Master in Informatics and Computing Engineering Supervised by: Miguel Pimenta Monteiro (Assistant professor) Pedro Rocha (GlinttHS) January 2015 2 Abstract Smartwatches have been around for some time now (Ranger 2015), but 2015 is the year this wearable technology will finally get its boom in terms of popularity and growth. Technology giants like Apple, Google and Samsung are betting on their own-line of products such as the Apple Watch, Android Wear and Gear respectively (Apple Inc 2015a; Google Inc 2015b; SAMSUNG 2015). All of these devices are computation capable electronics with very small touch capacitive screens, limited number of hardware buttons with varying screen sizes and even shapes. Our research focused mainly on these constraints and how to successfully develop user friendly GUI’s for such small screens. The goal was to develop a model with guidelines to help developers provide easy to use and user friendly applications at a visual and interaction level to end users. To successfully achieve this, we first took a deep look at the available technology within these devices, including the framework each of the major platforms provide and the underlying hardware capabilities such as sensors like GPS, gyroscope, the use of the touch screen or microphone for user input and whether the shape of the device (round or squared) can have different effects on the design and usability. We also analyzed the impact of placement and arrangement of interface components having in mind that this technology, since it is a wearable watch, can be worn on both wrists and therefore will be used with only one hand that may obscure a different portion of the interface depending on which wrist the user uses it (Chandra and Raghunath 2000). -

Characterizing Smartwatch Usage in the Wild
Characterizing Smartwatch Usage In The Wild Xing Liu1 Tianyu Chen1 Feng Qian1 Zhixiu Guo23 Felix Xiaozhu Lin4 Xiaofeng Wang1 Kai Chen25 1Indiana University Bloomington 2SKLOIS, Institute of Information Engineering, Chinese Academy of Sciences 3Beijing Jiaotong University 4Purdue ECE 5School of Cyber Security, University of Chinese Academy of Sciences ABSTRACT participants, we conduct an in-depth characterization of three key Smartwatch has become one of the most popular wearable aspects of smartwatch usage “in the wild”: usage patterns, energy computers on the market. We conduct an IRB-approved consumption, and network traffic characteristics. This is to our measurement study involving 27 Android smartwatch users. Using knowledge the most comprehensive and in-depth crowd-sourced a 106-day dataset collected from our participants, we perform in- study of smartwatches. Our key measurement results consist of depth characterization of three key aspects of smartwatch usage “in the following. the wild”: usage patterns, energy consumption, and network traffic. • We characterize the smartwatch usage patterns. An Android Based on our findings, we identify key aspects of the smartwatch watch can stay in one of the four states with diverse power ecosystem that can be further improved, propose recommendations, characteristics: fully awake, dozing (with dimmed watch face and point out future research directions. display and restricted system activity), sleeping (screen further turned off), and charging. We find that smartwatch’s wake-up CCS Concepts period accounts for only 2% of the overall usage period among • → the four states. The wake-up sessions are not only short, but Human-centered computing Ubiquitous and mobile also frequent (72 times per day on average). -

Digital Forensic Analysis of Smart Watches
TALLINN UNIVERSITY OF TECHNOLOGY School of Information Technologies Kehinde Omotola Adebayo (174449IVSB) DIGITAL FORENSIC ANALYSIS OF SMART WATCHES Bachelor’s Thesis Supervisor: Hayretdin Bahsi Research Professor Tallinn 2020 TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Kehinde Omotola Adebayo (174449IVSB) NUTIKELLADE DIGITAALKRIMINALISTIKA Bachelor’s Thesis Juhendaja: Hayretdin Bahsi Research Professor Tallinn 2020 Author’s declaration of originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Kehinde Omotola Adebayo 30.04.2020 3 Abstract As wearable technology is becoming increasingly popular amongst consumers and projected to continue to increase in popularity they become probable significant source of digital evidence. One category of wearable technology is smart watches and they provide capabilities to receive instant messaging, SMS, email notifications, answering of calls, internet browsing, fitness tracking etc. which can be a great source of digital artefacts. The aim of this thesis is to analyze Samsung Gear S3 Frontier and Fitbit Versa Smartwatches, after which we present findings alongside the limitations encountered. Our result shows that we can recover significant artefacts from the Samsung Gear S3 Frontier, also more data can be recovered from Samsung Gear S3 Frontier than the accompanying mobile phone. We recovered significant data that can serve as digital evidence, we also provided a mapping that would enable investigators and forensic examiners work faster as they are shown where to look for information in the course of an investigation. We also presented the result of investigating Fitbit Versa significant artefacts like Heart rate, sleep, exercise and personal data like age, weight and height of the user of the device, this shows this device contains artefacts that might prove useful for forensic investigators and examiners. -
API Diagrams
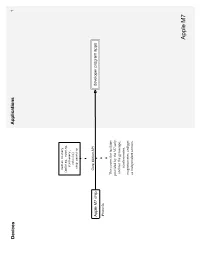
Devices Applications 1 motion history (walking, running, stationary, vehicle) step counting Core Motion API Apple M7 chip developer program apps iPhone 5s This covers the facilities provided by the M7 only, and not the gyroscope, accelerometer, magnetometer, and gps as independent sensors. Apple M7 Devices Applications Services 2 Runkeeper Argus Fitbit bluetooth 4.0 Withings LifeTrak Move C300 iOS Argus uses each New Balance LifeTRNr Watches services’ Pebble SmartWatch Sleep Time respective API. Mio Alpha Data is only viewable in the Wahoo Blue HR Heart Rate Strap iOS/Android Argus app, not in the website Stress Check iOS/Android Instant Heart Rate CSV Azumio cloud CSV premium feature or text iOS/Android/Windows table Phone/Windows 8 Cardio Buddy Data is not available for for Argus (steps only), iOS viewing from website, but Instant Heart Rate, Stress can sync to multiple Check and Sleep Time devices. Instant Fitness iOS CSV or text Fitness Buddy table iOS/Android text Glucose Buddy CSV table Glucose Buddy iOS/Android Azumio Devices Applications Services 3 Viera is Panasonic’s Smart TV platform that runs 3rd- party apps App requires Link Armband armband and API is active to subscription current developers but closed off to activity Bluetooth 2.0 new development heart rate food sleep BodyMedia FIT nutrients steps iOS/Android/Viera BodyMedia FIT API partner Armband Advantage Activity Manager program USB web dashboard BodyMedia SYNC Jawbone UP API apps Windows/Mac The desktop software only location CORE Armband transfers data to the registered image “Activity Manager” developers cardiac service. It does not allow oauth 2.0 food users to view data json goals mood activity sleep RF workout Since the armbands do not have displays, the Display Device is a Display way to show the data. -

The Myth of the Superuser: Fear, Risk, and Harm Online
The Myth of the Superuser: Fear, Risk, and Harm Online ∗ Paul Ohm Fear of the powerful computer user, the “Superuser,” dominates debates about online conflict. He is a mythic figure: difficult to find, immune to technological constraints, and aware of legal loopholes. Policymakers, fearful of his power, too often overreact by passing overbroad, ambiguous laws intended to ensnare the Superuser but which are instead used against inculpable, ordinary users. This response is unwarranted because the Superuser is often a marginal figure whose power has been greatly exaggerated. The exaggerated focus on the Superuser reveals a pathological characteristic of the study of power, crime, and security online, which springs from a widely held fear of the Internet. Building on the social science fear literature, this Article challenges the conventional wisdom and ∗ Associate Professor of Law and Telecommunications, University of Colorado Law School. Thanks to Tim Wu, Orin Kerr, Phil Weiser, Julie Cohen, Pierre Schlag, Brett Frischmann, Victor Fleischer, Miranda Fleischer, Viva Moffat, and Jean Camp for their helpful comments. Thanks also for suggestions and support from participants in the University of Colorado Law School Faculty Workshop, including Clare Huntington, Nestor Davidson, Scott Peppett, Mimi Wesson, Amy Schmitz, Sarah Krakoff, and Brad Bernthal; the Intellectual Property Scholars Conference; and the Telecommunications Policy Research Conference. Thanks also to Todd Blair and Michael Beylkin for outstanding research assistance. 1327 1328 University of California, Davis [Vol. 41:1327 standard assumptions about the role of experts. Unlike dispassionate experts in other fields, computer experts are as susceptible as laypeople to exaggerate the power of the Superuser.