Windows® Administration at the Command Line for Windows Vista™, Windows® 2003, Windows® XP, and Windows® 2000
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Current Capacity Reporter Installation Guide
CA Current Capacity Reporter Installation Guide Version 1.5 June, 2014 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and may not be disclosed by you or used for any purpose other than as may be permitted in (i) a separate agreement between you and CA governing your use of the CA software to which the Documentation relates; or (ii) a separate confidentiality agreement between you and CA. Notwithstanding the foregoing, if you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. -

Windows Package Manager (Winget)
Windows Package Manager (WinGet) Introduction Microsoft a mis en place un nouveau package pour l’installation de programme en ligne de commande (CMD ou PowerShell). Et suite aux nouvelles politiques de Mircrosoft le logiciel est disponible sur github. Attention, Windows Package Manager est en développement donc à vos risques et périls Installation Pour utiliser cette nouvelle fonctionnalité qui est encore en preview (actuellement en version v0.1.41331 Preview), il faut installer la dernière version disponible sur : github Microsoft Store Microsoft a déjà publié en français une documentation sur cette fonctionnalité : Gestionnaire de package Windows winget dans la pratique winget [<command>] [<options>] Commande Description search Rechercher une application install Installer une application show Affiche les informations d'une ou plusieurs applications source Permet de gérer les sources d'application hash Génère le hachage SHA256 pour le programme d’installation Valide un fichier manifeste pour l’envoi dans le dépôt du validate Gestionnaire de package Windows winget search winget search [[-q] <query>] [<options>] Commande Description -q,--query Requête utilisée pour rechercher une application --id Filtrer les résultats par identifiant --name Filtrer les résultats par nom --moniker Filtrer les résultats par nom d’application --tag Filtrer les résultats par mot-clé --command Filtrer les résultats par commande -s,--source Rechercher une application à l’aide de la source indiquée -n,--count Ne pas afficher plus de résultats que le nombre spécifié -

Dlplib Howto
DlpLib HowTo This article describes how to incorporate ID Parsing component (developed by IDScan.net) You can download free Example projects from our web-site http://www.IDScan.net/dlplib or http://www.IDScan.net/downloads C# 1. Install a Microsoft Visual Studio. You can download free Express Edition here http://www.microsoft.com/express/download/default.aspx 2. Create a new project. In this example it is Console Application: 3. Open Package Manager Console View->Other Windows->Package Manager Console 4. Select preferred method a. Type or copy and paste the following command Install-Package dlp-sdk –s https://www.myget.org/F/dlp-sdk/api/v2 b. Add reference to the library DlpLib.dll if you prefer to use a local copy. Under tab Browse select the file DlpLib.dll. www.IDScan.net Page 1 5. Now you are ready to write an application: static void Main(string[] args) { // Load a driver license text from a file. Don't forget to put testdl.txt next to your exe file. var scannedText = File.ReadAllText(@"testdl.txt"); // Parse the text and create an instance of DriverLicense. // All fields in DriverLicense are strings. // When the parser is not able to parse the text it returns null. Parser doesn't throw exceptions. var license = DriverLicense.ParseText(scannedText); if (license != null) { //This functions demonstrates a simple example Console.WriteLine("------Basic Usage--------"); BasicUsage(license); // If you need to enumerate all field you can use DataElementAttribute and reflection Console.WriteLine("------Print All Fields--------"); PrintAllFields(license); } // However, if you need typed variables or you need to know what was found in the license you should use DriverLicenseEx // It does the same job but the field types can be string, DataTime?, Char? or bool? // If a field was not present in the license string this field is null. -

Deltek Vision 7.6 Advanced Technical Administration Guide
Deltek Vision® 7.6 Advanced Technical Administration Guide July 29, 2016 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or technical errors may exist. The recipient of this document is solely responsible for all decisions relating to or use of the information provided herein. The information contained in this publication is effective as of the publication date below and is subject to change without notice. This publication contains proprietary information that is protected by copyright. All rights are reserved. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, or translated into another language, without the prior written consent of Deltek, Inc. This edition published July 2016. © Deltek, Inc. Deltek’s software is also protected by copyright law and constitutes valuable confidential and proprietary information of Deltek, Inc. and its licensors. The Deltek software, and all related documentation, is provided for use only in accordance with the terms of the license agreement. Unauthorized reproduction or distribution of the program or any portion thereof could result in severe civil or criminal penalties. All trademarks are the property of their respective owners. Advanced Technical Administration Guide ii Contents Overview ..................................................................................................................................... 1 Consulting Is Available ........................................................................................................... -

Ipados 15, Anteprima Completa Un Vestito Cucito Su Misura
n.248 / 21 12 LUGLIO 2021 MAGAZINE Nuova gamma di TV Nuova Nintendo Switch TIM Vision, Champions LG CordZero A9 Samsung: 5 cose con schermo OLED da inclusa e DTT: offerta Prestazioni top, che non sapevamo 13 7”. Arriva l’8 ottobre 15 aperta a tutti 20 prezzo anche 23 iPadOS 15, anteprima completa Un vestito cucito su misura per iPad Con iPadOS 15 finalmente si inizia a parlare davvero di sistema operativo cucito su misura per il tablet Apple. L’anteprima super completa con tante novità 02 Bonus Rottamazione TV: ecco 27 come funzionerà l’incentivo Tutte le domande e le risposte sul nuovo Bonus TV Sconto del 20% fino a 100 euro per chi rottama un Digiquest Q60 vecchio TV. Il vecchio Bonus TV però passa a 30 euro La recensione 12 del decoder combo Windows 11, prime impressioni 44 Guardare avanti restando se stessi Le nostre prime impressioni su Windows 11, utilizzando la Renault, torna la R5 versione beta. Windows 11 è lo stesso Windows di sempre Rinasce elettrica e ci fa sentire “a casa”, anche se l’aspetto ora è diverso e marchiata Alpine 17 IN PROVA IN QUESTO NUMERO 29 33 35 38 TV OLED LG G1 Rotel+B&W+ Pro-Ject Asus ROG Flow X13 Huawei Watch 3 Pro Ecco l’OLED “Evo” Sistema equilibrato Game changer Cuore HarmonyOS 2 n.248 / 21 12 LUGLIO 2021 MAGAZINE MOBILE Abbiamo provato la beta 2 di iPadOS 15. Il tablet di Apple ora pare avere un sistema operativo che gli cade meglio addosso iPadOS 15, anteprima completa del tablet Apple iPad ha finalmente un vestito cucito su misura Divisione dello schermo, note rapide, modalità Concentrazione e riepilogo notifiche rendono l’iPad ancora più vicino all’utente di Sergio DONATO PadOS 13.1 nacque nel settembre del 2019 per dare al tablet di Apple un sistema operativo che potesse isfruttare le agilità del dispositivo che con il meno dedicato iOS non riuscivano a manifestarsi. -

Released, and Do Not Use the Link in the Prompt to Avoid Asset Losses
It is worth mentioning that electrums below version 3.3.4 are vulnerable to such phishing attacks, and users of Electrum wallets are requested to update to the latest version of Electrum3.3.8 via the official website (electrum.org), which has not yet been officially released, and do not use the links in the prompts to avoid asset losses. Install the Solidity Compiler (SolC) through "Chocolatey" (Windows' Package Manager) Another approach is to use virtualization software and install Linux in it. This way, you can install Linux distributions in Windows (with a graphical interface) and like regular Windows. Use Windows-Build-Tools to automatically install dependency tools. In December 2018, Slow Fog first discovered and alerted an attacker to a messaging flaw using the Electrum Wallet client to force an "update prompt" to pop up when a user transfers money, inducing users to update and download malware to carry out a currency theft attack. Although electrum officials said in early 2019 that some security mechanisms were in place to prevent this "update phishing", many users of Electrum are still in the old version (less than 3.3.4) and the old version is still under threat. However, we do not rule out a similar threat to the new version. vcpkg.exe install simdjson: x64-windows-static. pip install scikit-image (Windows) DeViable Security Labs hereby suggests that versions of Electrum below 3.3.4 are vulnerable to such phishing attacks, and users using Electrum Wallet are requested to update to the latest version of Electrum 3.3.8 via the official website (electrum.org), which has not yet been officially released, and do not use the link in the prompt to avoid asset losses. -
Spring Semester 2020 - Week 12
Comp 324/424 - Client-side Web Design Spring Semester 2020 - Week 12 Dr Nick Hayward JS Server-side considerations - save data save JSON in travel notes app need to be able to save our simple notes now load from a JSON file as the app starts also we can add new notes, delete existing notes… not as simple as writing to our existing JSON file direct from JS security implications if that was permitted directly from the browser need to consider a few server-side options could use a combination of PHP on the server-side with AJAX jQuery on the client-side traditional option with a simple ajax post to a PHP file on the server-side consider JavaScript options on the client and server-side brief overview of working with Node.js Server-side considerations - intro normally define computer programs as either client-side or server- side programs server-side programs normally abstract a resource over a network enabling many client-side programs to access at the same time a common example is file requests and transfers we can think of the client as the web browser a web server as the remote machine abstracting resources abstracts them via hypertext transfer protocol HTTP for short designed to help with the transfer of HTML documents HTTP now used as an abstracted wrapper for many different types of resources may include documents, media, databases… Image - Client-side and server-side computing client-side & server-side Server-side considerations - Node.js intro - what is Node.js? Node.js is, in essence, a JavaScript runtime environment designed to -
El Cómputo En Los Cursos De La Facultad De Ciencias, UNAM
El Cómputo en los Cursos de la Facultad de Ciencias, UNAM Antonio Carrillo Ledesma y Karla Ivonne González Rosas Facultad de Ciencias, UNAM http://academicos.fciencias.unam.mx/antoniocarrillo Una copia de este trabajo se puede descargar de la página: https://sites.google.com/ciencias.unam.mx/acl/en-desarrollo Con…namiento 2020-2021, Versión 1.0 1 1El presente trabajo está licenciado bajo un esquema Creative Commons Atribución CompartirIgual (CC-BY-SA) 4.0 Internacional. Los textos que compo- nen el presente trabajo se publican bajo formas de licenciamiento que permiten la copia, la redistribución y la realización de obras derivadas siempre y cuando éstas se distribuyan bajo las mismas licencias libres y se cite la fuente. ¡Copiaeste libro! ... Compartir no es delito. El Cómputo en los Cursos de la Facultad de Ciencias, UNAM Índice 1 Introducción 7 1.1 Software Propietario y Libre ................... 7 1.1.1 Software Propietario ................... 8 1.1.2 Software Libre ....................... 9 1.2 El Cómputo en las Carreras de Ciencias ............ 11 1.2.1 Algunos Cursos que Usan Cómputo ........... 14 1.3 Paquetes de Cómputo de Uso Común .............. 17 1.3.1 Sistemas Operativos ................... 21 1.3.2 Paquetes de Cálculo Numérico .............. 21 1.3.3 Paquetes de Cálculo Simbólico .............. 22 1.3.4 Paquetes Estadísticos ................... 23 1.3.5 Paquetes O…máticos ................... 24 1.3.6 Lenguajes de Programación y Entornos de Desarrollo . 24 1.3.7 Otros Programas de Cómputo .............. 24 1.4 Sobre los Ejemplos de este Trabajo ............... 25 1.5 Agradecimientos .......................... 25 2 Sistemas Operativos 26 2.1 Windows ............................. -
ITM Graduate Student Information Fall 2021
COVID-19 Disclaimer: Policy, conditions, and practices described here may vary due to contingencies related to the COVID-19 pandemic. ITM Graduate Student Information Fall 2021 Department of Information Technology & Management Master’s Degrees Contents Page # Contents Page # Information Technology & Management Mission ........................................................1 Advising and Registration ..................................................................................................9 About the Department of Information Technology & Management .......................1 Independent Study, Research, and Thesis...................................................................11 Course Philosophy................................................................................................................1 Recognition of Academic Achievement........................................................................11 Program Objectives .............................................................................................................1 ITM Student Organizations...............................................................................................12 Graduate Bulletin..................................................................................................................2 Funding: Scholarships,Internships, Coops, Graduate Course Differentiation.......................................................................................2 Job Placement, and Student Employment..................................................................12 -

Microsoft Build 2020 Book of News (PDF)
Build Book of News Table of contents 09 1. Azure AI 1.1. Azure Hybrid & Azure Infrastructure 1.1.1. Azure Hybrid: Azure Arc 1.1.1.1. Azure Arc-enabled Kubernetes clusters now in public preview 1.1.1.2. Azure Arc-enabled SUSE Linux Enterprise Server now in public preview 1.1.2. Azure Hybrid: Azure Stack 1.1.2.1. Azure Stack Hub updates will simplify fleet and resource management and enable graphic-heavy scenarios 1.1.2.2. Azure Stack expands solutions and partner ecosystem 1.1.3. Azure Infrastructure 1.1.3.1. Network service tiers with new Routing Preference option now in preview 1.1.3.2. Azure Peering Service, now generally available, enhances connectivity to Microsoft cloud services 1.1.3.3. Azure Resource Manager template enhancements increase accuracy and streamline customer process 1.1.4. Azure Monitor Updates 1.1.4.1. Azure Monitor telemetry tools maximize cloud and on-premises resources and apps 1.2. Azure Data 1.2.1. Azure Cosmos DB 1.2.1.1. Azure Cosmos DB serverless addresses intermittent traffic and “bursty” workloads for small apps 1.2.1.2. Azure Cosmos DB features offer enhanced key and data recovery options for enterprise and mission-critical apps Table of contents 15 1. Azure AI (Continued) 1.2.1.3. Azure Cosmos DB autoscale provisioned throughput offers scalability for largescale workloads 1.2.2. Azure Database 1.2.2.1. Microsoft Azure introduces new PostgreSQL and MySQL capabilities, reasserting commitment to community 1.2.3. Azure SQL Edge 1.2.3.1. -

Installshield New and Enhanced Features Added by Release
DATA SHEET InstallShield New and Enhanced Features Added by Release InstallShield 2021 R1 InstallShield Premier InstallShield Support for Cloud Builds Modern and Simple Installers Install Packages from Windows Package Manager MSIX Updates Enhanced Support for Windows 11 InstallShield 2020 R3 InstallShield Premier InstallShield MSIX – Support for Fonts Build InstallShield Projects in an Azure DevOps Pipeline InstallShield 2020 R2 InstallShield Premier InstallShield MSIX Bundles MSIX – Support for Services Copyright © 2021Copyright Revenera © LLC.2020 All Flexera other brand Software and LLC. product All other names brand mentioned and product herein names may be mentioned the trademarks herein 1.800.809.5659 | +44.870.871.1111 | revenera.com and registered trademarksmay of betheir the respective trademarks owners. and registered | 741_C_IS_Launch2021_CmprVrsns_DataSheet trademarks of their respective owners. DATA SHEET InstallShield 2020 R1 InstallShield Premier InstallShield MSIX – Modification Packages MSIX – Support for MSIX Core Pure 64 Installers AWS CloudHSM-based Digital Signing InstallShield 2019 R3 InstallShield Premier InstallShield Simplified Builds Within Docker Automated Patch Design InstallShield 2019 InstallShield Premier InstallShield Create Native MSIX Packages Identify Existing Installshield Projects Requiring Changes to Meet Microsoft MSIX Standards Expands Installation Suites to Include MSIX Packages Easily Convert Any MSI File into an MSIX Package Microsoft Visual Studio 2019 Integration InstallShield 2018 R2 InstallShield -
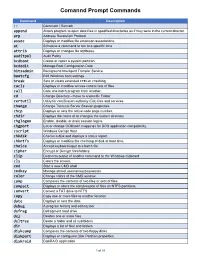
Comannd Prompt Commands
Comannd Prompt Commands Command Description :: Comment / Remark append Allows program to open data files in spedified directories as if they were in the current director. arp Address Resolution Protocol assoc Displays or modifies file extension associations. at Schedule a command to run at a specific time attrib Displays or changes file attributes. auditpol Audit Policy bcdboot Create or repair a system partition bcdedit Manage Boot Configuration Data bitsadmin Background Intelligent Transfer Service bootcfg Edit Windows boot settings break Sets or clears extended CTRL+C checking. cacls Displays or modifies access control lists of files call Calls one batch program from another. cd Change Directory - move to a specific Folder certutil Utility for certification authority (CA) files and services change Change Terminal Server Session properties chcp Displays or sets the active code page number. chdir Displays the name of or changes the current directory chglogon Enable, disable, or drain session logins. chgport List or change COM port mappings for DOS application compatibility. cscript Windows Cscript Host chkdsk Checks a disk and displays a status report. chkntfs Displays or modifies the checking of disk at boot time. choice Accept keyboard input to a batch file cipher Encrypt or Decrypt files/folders clip Dedirects output of another command to the Windows clipboard cls Clears the screen. cmd Start a new CMD shell cmdkey Manage stored usernames/passwords color Change colors of the CMD window comp Compares the contents of two files or sets of files. compact Displays or alters the compression of files on NTFS partitions. convert Convert a FAT drive to NTFS copy Copy one or more files to another location date Displays or sets the date.