Alice and Bob in Wonderland a First Glimpse in the World of Security and Cryptography
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Models and Algorithms for Physical Cryptanalysis
MODELS AND ALGORITHMS FOR PHYSICAL CRYPTANALYSIS Dissertation zur Erlangung des Grades eines Doktor-Ingenieurs der Fakult¨at fur¨ Elektrotechnik und Informationstechnik an der Ruhr-Universit¨at Bochum von Kerstin Lemke-Rust Bochum, Januar 2007 ii Thesis Advisor: Prof. Dr.-Ing. Christof Paar, Ruhr University Bochum, Germany External Referee: Prof. Dr. David Naccache, Ecole´ Normale Sup´erieure, Paris, France Author contact information: [email protected] iii Abstract This thesis is dedicated to models and algorithms for the use in physical cryptanalysis which is a new evolving discipline in implementation se- curity of information systems. It is based on physically observable and manipulable properties of a cryptographic implementation. Physical observables, such as the power consumption or electromag- netic emanation of a cryptographic device are so-called `side channels'. They contain exploitable information about internal states of an imple- mentation at runtime. Physical effects can also be used for the injec- tion of faults. Fault injection is successful if it recovers internal states by examining the effects of an erroneous state propagating through the computation. This thesis provides a unified framework for side channel and fault cryptanalysis. Its objective is to improve the understanding of physi- cally enabled cryptanalysis and to provide new models and algorithms. A major motivation for this work is that methodical improvements for physical cryptanalysis can also help in developing efficient countermea- sures for securing cryptographic implementations. This work examines differential side channel analysis of boolean and arithmetic operations which are typical primitives in cryptographic algo- rithms. Different characteristics of these operations can support a side channel analysis, even of unknown ciphers. -

Effects of Architecture on Information Leakage of a Hardware Advanced Encryption Standard Implementation Eric A
Air Force Institute of Technology AFIT Scholar Theses and Dissertations Student Graduate Works 9-13-2012 Effects of Architecture on Information Leakage of a Hardware Advanced Encryption Standard Implementation Eric A. Koziel Follow this and additional works at: https://scholar.afit.edu/etd Part of the Computer and Systems Architecture Commons, and the Information Security Commons Recommended Citation Koziel, Eric A., "Effects of Architecture on Information Leakage of a Hardware Advanced Encryption Standard Implementation" (2012). Theses and Dissertations. 1127. https://scholar.afit.edu/etd/1127 This Thesis is brought to you for free and open access by the Student Graduate Works at AFIT Scholar. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of AFIT Scholar. For more information, please contact [email protected]. EFFECTS OF ARCHITECTURE ON INFORMATION LEAKAGE OF A HARDWARE ADVANCED ENCRYPTION STANDARD IMPLEMENTATION THESIS Eric A. Koziel AFIT/GCO/ENG/12-25 DEPARTMENT OF THE AIR FORCE AIR UNIVERSITY AIR FORCE INSTITUTE OF TECHNOLOGY Wright-Patterson Air Force Base, Ohio APPROVED FOR PUBLIC RELEASE; DISTRIBUTION UNLIMITED The views expressed in this thesis are those of the author and do not reflect the official policy or position of the United States Air Force, Department of Defense, or the United States Government. This material is declared a work of the U.S. Government and is not subject to copyright protection in the United States. AFIT/GCO/ENG/12-25 EFFECTS OF ARCHITECTURE ON INFORMATION LEAKAGE OF A HARDWARE ADVANCED ENCRYPTION STANDARD IMPLEMENTATION THESIS Presented to the Faculty Department of Electrical & Computer Engineering Graduate School of Engineering and Management Air Force Institute of Technology Air University Air Education and Training Command In Partial Fulfillment of the Requirements for the Degree of Master of Science in Cyber Operations Eric A. -

Some Words on Cryptanalysis of Stream Ciphers Maximov, Alexander
Some Words on Cryptanalysis of Stream Ciphers Maximov, Alexander 2006 Link to publication Citation for published version (APA): Maximov, A. (2006). Some Words on Cryptanalysis of Stream Ciphers. Department of Information Technology, Lund Univeristy. Total number of authors: 1 General rights Unless other specific re-use rights are stated the following general rights apply: Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal Read more about Creative commons licenses: https://creativecommons.org/licenses/ Take down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. LUND UNIVERSITY PO Box 117 221 00 Lund +46 46-222 00 00 Some Words on Cryptanalysis of Stream Ciphers Alexander Maximov Ph.D. Thesis, June 16, 2006 Alexander Maximov Department of Information Technology Lund University Box 118 S-221 00 Lund, Sweden e-mail: [email protected] http://www.it.lth.se/ ISBN: 91-7167-039-4 ISRN: LUTEDX/TEIT-06/1035-SE c Alexander Maximov, 2006 Abstract n the world of cryptography, stream ciphers are known as primitives used Ito ensure privacy over a communication channel. -
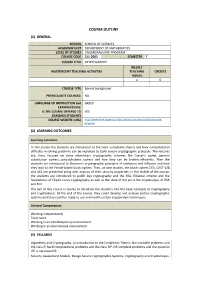
Cryptography Weekly Independent Teaching Activities Teaching Credits Hours 4 6
COURSE OUTLINE (1) GENERAL SCHOOL SCHOOL OF SCIENCES ACADEMIC UNIT DEPARTMENT OF MATHEMATICS LEVEL OF STUDIES UNDERGRADUATE PROGRAM COURSE CODE 311-2003 SEMESTER F COURSE TITLE CRYPTOGRAPHY WEEKLY INDEPENDENT TEACHING ACTIVITIES TEACHING CREDITS HOURS 4 6 COURSE TYPE Special background PREREQUISITE COURSES: NO LANGUAGE OF INSTRUCTION and GREEK EXAMINATIONS: IS THE COURSE OFFERED TO YES ERASMUS STUDENTS COURSE WEBSITE (URL) http://www.math.aegean.gr/index.php/en/academics/undergraduate- programs (2) LEARNING OUTCOMES Learning outcomes In this course the students are introduced to the basic complexity theory and how computational difficulty in solving problems can be exploited to build secure cryptographic protocols. The lectures are, then, focused on some elementary cryptographic schemes like Caesar’s cipher, general substitution ciphers, polyalphabetic ciphers and how they can be broken efficiently. Then the students are introduced to Shannon’s cryptographic principles of confusion and diffusion and how they lead to the Feistel-based block ciphers. Then, as case studies, the block ciphers DES, CAST-128 and AES are presented along with analysis of their security properties. In the middle of the course, the students are introduced to public key cryptography and the RSA, ElGamal scheme and the foundations of Elliptic Curve Cryptography as well as the state of the art in the cryptanalysis of RSA and ECC. The aim of this course is mainly to introduce the students into the basic concepts of cryptography and cryptanalysis. At the end of the course, they could develop and analyse certain cryptographic systems and they could be ready to use and modify certain cryptanalysis techniques. -

CE441: Data and Network Security Cryptography — Symmetric
CE441: Data and Network Security Cryptography — Symmetric Behnam Momeni, PhD Department of Computer Engineering Sharif University of Technology Fall 2019 . B. Momeni (Sharif Univ. of Tech.) CE441: Data and Network Security Fall 2019 1 / 94 Cryptology: Cryptography and Cryptanalysis Review: What Does Security Mean? Outline 1 Cryptology: Cryptography and Cryptanalysis Review: What Does Security Mean? Cryptography: Definition and Models Classic Cryptography Cryptanalysis: A Glimpse 2 Confidentiality-Providing Schemes 3 Integrity-Providing Schemes 4 Full Fledged Schemes . B. Momeni (Sharif Univ. of Tech.) CE441: Data and Network Security Fall 2019 2 / 94 Cryptology: Cryptography and Cryptanalysis Review: What Does Security Mean? Security Goals Availability CIA Triad Confidentiality Integrity . B. Momeni (Sharif Univ. of Tech.) CE441: Data and Network Security Fall 2019 3 / 94 Cryptology: Cryptography and Cryptanalysis Review: What Does Security Mean? Definition Defining an scheme has two main parts Syntax: specifies operations which can be performed by honest participants of the scheme e.g. The symmetric encryption scheme, SE = (K; E; D), contains a key generation function K, an encryption function E, and a decryption function D k K : 8m : Dk (Ek (m)) = m The scheme is modeled here Semantic: specifies conditions which must be met by a secure scheme The security definition is formalized here . B. Momeni (Sharif Univ. of Tech.) CE441: Data and Network Security Fall 2019 4 / 94 Cryptology: Cryptography and Cryptanalysis Review: What Does Security Mean? Game-based Definition Model the scheme operations normally Then, devise a game between an adversary and a challenger Adversary tries to break the security definition Challenger wants to demonstrate inability of the adversary Adversary is trying to obtain some advantage e.g. -

Security System on Data Encryption & Decryption
International Research Journal of Engineering and Technology (IRJET)e-ISSN: 2395-0056 Volume: 07 Issue: 04 | Apr 2020 www.irjet.net p-ISSN: 2395-0072 Security System on Data Encryption & Decryption Mr. Mukul Aggarwal1, Mr. Deepak Kumar Yadav2, Dr. Himanshu Arora3 and Mr. Sudhanshu Vashistha4 1B. Tech Student, Department of CSE, Arya College of Engineering and Research Center, Jaipur 2B. Tech Student, Department of CSE, Arya College of Engineering and Research Center, Jaipur 3Professor, Department of CSE, Arya College of Engineering and Research Center, Jaipur 4Assistant Professor, Department of CSE, Arya College of Engineering and Research Center, Jaipur ---------------------------------------------------------------------- ***--------------------------------------------------------- Abstract— Now’s a day’s security is a feature or factor which is most services attack. It is the attack in which third- person important about any sector which ensures the protection of data. It directly access the server. prevents unauthorized persons, thieves, hackers, etc. In this field, Access Control: It is the process in which only authorized there are three main feature which is essential for data security i.e. person can only access the data resources confidentiality, integrity, availability, these three main features which prevent from unauthorized any other third person. Confidentiality TABLE I basically if we send the data from one person to another person then FONT SIZES FOR PAPERS only authorized person can access & integrity if we transfer the information from one to another then no one can change. The availability of the resources should be available 24/7 hour or data should be available on demand. Process of communication using Encryption and Decryption over data. To convert the plain text into ciphertext is Encryption and convert the ciphertext into plain text is Decryption and both methods called as a Cryptology. -

When Encryption Is Not Enough Effective Concealment of Communication Pattern, Even Existence (Bitgrey, Bitloop)
When Encryption is Not Enough Effective Concealment of Communication Pattern, even Existence (BitGrey, BitLoop) Gideon Samid Department of Electrical Engineering and Computer Science Case Western Reserve University, Cleveland, OH [email protected] Abstract: How much we say, to whom, and when, is inherently telling, even if the contents of our communication is unclear. In other words: encryption is not enough; neither to secure privacy, nor to maintain confidentiality. Years ago Adi Shamir already predicted that encryption will be bypassed. And it has. The modern dweller of cyber space is routinely violated via her data behavior. Also, often an adversary has the power to compel release of cryptographic keys over well-exposed communication. The front has shifted, and now technology must build cryptographic shields beyond content, and into pattern, even as to existence of communication. We present here tools, solutions, methods to that end. They are based on equivocation. If a message is received by many recipients, it hides the intended one. If a protocol calls for decoy messages, then it protects the identity of the sender of the contents-laden message. BitGrey is a protocol that creates a "grey hole" (of various shades) around the communicating community, so that very little information leaks out. In addition the BitLoop protocol constructs a fixed rate circulating bit flow, traversing through all members of a group. The looping bits appear random, and effectively hide the pattern, even the existence of communication within the group. 1 Introduction We have fought for freedom in the physical world, and now the war moved to cyber space. -

Arxiv:Quant-Ph/0601207V3 2 May 2006 Acmdtraid Atcooi,Ad.Cnlol´Impic, S/ Canal Avda
E. WOLF, PROGRESS IN OPTICS VVV c 199X ALL RIGHTS RESERVED X QUANTUM CRYPTOGRAPHY BY Miloslav Duˇsek Department of Optics, Palack´yUniversity 17. listopadu 50, 77200 Olomouc, Czech Republic Norbert Lutkenhaus¨ Institut f¨ur Optik, Information und Photonik Universit¨at Erlangen-N¨urnberg Staudtstr. 7/B3, 91058 Erlangen, Germany Martin Hendrych ICFO - Institut de Ci`encies Fot`oniques Parc Mediterrani de la Tecnologia, Avda. Canal Ol´ımpic, s/n 08860 Castelldefels (Barcelona), Spain arXiv:quant-ph/0601207v3 2 May 2006 1 CONTENTS1 PAGE 1. CIPHERING 3 § 2. QUANTUM KEY DISTRIBUTION 9 § 3. SOMEOTHERDISCRETEPROTOCOLSFORQKD 14 § 4. EXPERIMENTS 18 § 5. TECHNOLOGY 26 § 6. LIMITATIONS 34 § 7. SUPPORTING PROCEDURES 35 § 8. SECURITY 38 § 9. PROSPECTS 51 REFERENCES§ 52 1Run LaTeX twice for up-to-date contents. 2 1. CIPHERING 3 1. Ciphering §§§ 1.1. INTRODUCTION, CRYPTOGRAPHIC TASKS There is no doubt that electronic communications have become one of the main pillars of the modern society and their ongoing boom requires the development of new methods and techniques to secure data transmission and data storage. This is the goal of cryptography. Etymologically derived from Greek κρυπτoς´ , hidden or secret, and γραϕη´, writing, cryptography may generally be defined as the art of writing (encryption) and deciphering (decryption) messages in code in order to ensure their confidentiality, authenticity, integrity and non-repudiation. Cryptog- raphy and cryptanalysis, the art of codebreaking, together constitute cryptology (λoγoς´ , a word). Nowadays many paper-based communications have already been replaced by elec- tronic means, raising the challenge to find electronic counterparts to stamps, seals and hand-written signatures. The growing variety of applications brings many tasks that must be solved. -
Evaluation of Anonymity and Confidentiality Protocols Using
Form Methods Syst Des (2015) 47:265–286 DOI 10.1007/s10703-015-0232-5 Evaluation of anonymity and confidentiality protocols using theorem proving Tarek Mhamdi1 · Osman Hasan1 · Sofiène Tahar1 Published online: 20 June 2015 © Springer Science+Business Media New York 2015 Abstract Anonymity and confidentiality protocols constitute crucial parts in many net- work applications as they ensure anonymous communications between entities in a network or provide security in insecure communication channels. Evaluating the properties of these protocols is therefore of paramount importance, especially in the case of safety-critical appli- cations. However, traditional analysis techniques, like simulation, cannot ascertain accurate analysis in this domain. We propose to overcome this limitation by conducting an informa- tion leakage analysis of anonymity and cryptographic protocols within the trusted kernel of a higher-order-logic theorem prover. For this purpose, we first introduce two novel measures of information leakage, namely the information leakage degree and the conditional information leakage degree and then present a higher-order-logic formalization of information measures and the underlying required theories of measure, probability and information. For illustration purposes, we use the proposed framework to evaluate the security properties of the one-time pad encryption system as well as the properties of an anonymity-based single MIX. We show how this formal analysis allowed us to find a counter-example for a theorem that was reported in the -

Preuves De Connaissances Interactives Et Non-Interactives Olivier Blazy
Preuves de connaissances interactives et non-interactives Olivier Blazy To cite this version: Olivier Blazy. Preuves de connaissances interactives et non-interactives. Cryptographie et sécurité [cs.CR]. Université Paris-Diderot - Paris VII, 2012. Français. tel-00768787 HAL Id: tel-00768787 https://tel.archives-ouvertes.fr/tel-00768787 Submitted on 24 Dec 2012 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Ecole´ Normale Sup´erieure D´epartement d’Informatique Universit´eParis 7 Denis Diderot Preuves de connaissance interactives et non-interactives Th`ese pr´esent´eeet soutenue publiquement le 27 septembre 2012 par Olivier Blazy pour l’obtention du Doctorat de l’Universit´eParis Diderot (sp´ecialit´einformatique) Devant le jury compos´ede : Directeur de th`ese: David Pointcheval (CNRS, Ecole´ Normale Sup´erieure) Rapporteurs : Jean-S´ebastien Coron (Universit´edu Luxembourg) Marc Fischlin (Universit´ede Darmstadt) Fabien Laguillaumie (CNRS, LIP) Examinateurs : Michel Abdalla (CNRS, Ecole´ Normale Sup´erieure) Antoine Joux (DGA, Universit´ede Versailles) Eike Kiltz (Universit´ede la Ruhr, Bochum) Damien Vergnaud (CNRS, Ecole´ Normale Sup´erieure) Travaux effectu´es au Laboratoire d’Informatique de l’Ecole´ Normale Sup´erieure Remerciements Bien des gens ont contribu´ede pr`es ou de loin `al’accomplissement de ce m´emoire. -

Automatic Detection of Weak Cipher Usage in Aircraft Communications
Automatic detection of weak cipher usage in aircraft communications Francesco Intoci, Mattia Mariantoni, Theresa Stadler Department of Computer Science, EPFL, Switzerland - Supervised by Kasra Edalatnejadkhamene SPRING Lab, EPFL, Switzerland Abstract—The Aircraft Communications Addressing and Re- sufficiently tech-savvy user to intercept ACARS-transmitted porting System (ACARS) allows aircraft to communicate with en- messages. This development increases the risk of eavesdrop- tities on the ground via short messages. To provide confidentiality ping attacks as potential adversaries need less resources and for sensitive information communicated via the ACARS network, some operators started to deploy proprietary cryptography to specialist knowledge to intercept communications [2]. encrypt message contents. This is highly problematic, however, A recent measurement study on the privacy of sensitive as all of the observed approaches in practice offer next to no content submitted on the ACARS channel found a significant communication security but give a false sense of it. Authorities information leakage [2]. The study demonstrates that ACARS hence would like to filter out weak ciphers at the network level to alert operators of their risks. messages submitted in the clear undermine efforts to hide This project explored the use of deep convolutional neural sensitive location information and cause major privacy issues networks (CNN) for automatic detection of weakly encrypted to business, military, and government aircraft. message contents on the ACARS data link network. We con- Many of the described issues are a result of cleartext message structed a labelled dataset of plaintext and ciphertext messages contents being freely accessible to passive eavesdroppers. The and experimentally evaluated the performance of a deep CNN for message classification. -

IT8761 Security Laboratory Manual
IT8761 SECURITY LABORATORY REGULATION – 2017 DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING DEPARTMENT OF INFORMATION TECHNOLOGY LAB INCHARGE HOD PRINCIPAL LIST OF EXPERIMENTS Ex. Name of the Experiment No. 1. Perform encryption, decryption using the following substitution techniques i. Ceaser cipher ii. Playfair cipher iii. Hill Cipher iv. Vigenere cipher 2. Perform encryption and decryption using following transposition techniques i. Rail fence ii. Row & Column Transformation 3. Apply DES algorithm for practical applications. 4. Apply AES algorithm for practical applications. 5. Implement RSA Algorithm using HTML and JavaScript 6. Implement the Diffie-Hellman Key Exchange algorithm for a given problem. 7. Calculate the message digest of a text using the SHA-1 algorithm. 8. Implement the SIGNATURE SCHEME - Digital Signature Standard. 9. Demonstrate intrusion detection system (ids) using any tool eg. Snort or any other s/w. 10. Automated Attack and Penetration Tools Exploring N-Stalker, a Vulnerability Assessment Tool 11. Defeating Malware i. Building Trojans ii. Rootkit Hunter Software Download Links: Visual Studio Code: https://code.visualstudio.com/download Snort - https://www.snort.org/downloads N-Stalker - https://www.nstalker.com/products/editions/free/download/ GMER - http://www.gmer.net/ JAVA - https://www.java.com/en/download/ Ex. No : 1(a) Encryption and Decryption Using Ceaser Cipher Date : AIM: To encrypt and decrypt the given message by using Ceaser Cipher encryption algorithm. ALGORITHMS: 1. In Ceaser Cipher each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. 2. For example, with a left shift of 3, D would be replaced by A, E would become B, and so on.