Sys/Sys/Bio.H 1 1 /* 65 Void *Bio Caller2; /* Private Use by the Caller
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Advanced Integration
ZFS: Advanced Integration Allan Jude -- [email protected] @allanjude Introduction: Allan Jude • 16 Years as FreeBSD Server Admin • FreeBSD src/doc committer (ZFS, installer, boot loader, GELI, bhyve, libucl, libxo) • FreeBSD Core Team (July 2016 - 2018) • Co-Author of “FreeBSD Mastery: ZFS” and “FreeBSD Mastery: Advanced ZFS” with Michael W. Lucas • Architect of the ScaleEngine CDN (HTTP and Video) • Host of weekly BSDNow.tv Podcast • Personally Responsible for 1000 TB of ZFS Storage ZFS: What Is It? • ZFS is a filesystem with a built in volume manager (combine multiple disks into a pool) • Space from the pool is thin-provisioned to multiple filesystems or block volumes (zvols) • All data and metadata is checksummed • Optional transparent compression • Copy-on-Write with snapshots and clones • Each filesystem is tunable with properties Snapshots and Clones • Copy-on-Write means snapshots are instant • Blocks referenced by a snapshot kept when they are removed from the live filesystem • Snapshots allows you to access the file- system as it was when snapshot was taken • No performance impact on reads/writes • Take no additional space until blocks change • Clones allow you to “fork” a filesystem Boot Environments • If the root filesystem is on ZFS, you can snapshot before an upgrade, then clone it • You now have 2 filesystems, one before the upgrade, and one after. Only takes the space of blocks that changed • FreeBSD boot loader allows you to select which one to use from a menu • Upgrade without fear, can always rollback Boot Environment Tooling • Existing tool: sysadmin/beadm • GSoC 2017: be(8) and libbe(3) • New tool supports better management of filesystem properties for boot integration • New tool will support “deep” boot environments. -

The Release Engineering of Freebsd 4.4
The Release Engineering of FreeBSD 4.4 Murray Stokely [email protected] Wind River Systems Abstract different pace, and with the general assumption that they This paper describes the approach used by the FreeBSD re- have first gone into FreeBSD-CURRENT and have been lease engineering team to make production-quality releases thoroughly tested by our user community. of the FreeBSD operating system. It details the methodol- In the interim period between releases, nightly snap- ogy used for the release of FreeBSD 4.4 and describes the shots are built automatically by the FreeBSD Project build tools available for those interested in producing customized machines and made available for download from ftp: FreeBSD releases for corporate rollouts or commercial pro- //stable.FreeBSD.org. The widespread availabil- ductization. ity of binary release snapshots, and the tendency of our user community to keep up with -STABLE development with CVSup and “make world”[8] helps to keep FreeBSD- 1 Introduction STABLE in a very reliable condition even before the qual- ity assurance activities ramp up pending a major release. The development of FreeBSD is a very open process. Bug reports and feature requests are continuously sub- FreeBSD is comprised of contributions from thousands of mitted by users throughout the release cycle. Problem people around the world. The FreeBSD Project provides reports are entered into our GNATS[9] database through anonymous CVS[1] access to the general public so that email, the send-pr(1) application, or via a web-based form. others can have access to log messages, diffs between de- In addition to the multitude of different technical mailing velopment branches, and other productivity enhancements lists about FreeBSD, the FreeBSD quality-assurance mail- that formal source code management provides. -

Freebsd Handbook
FreeBSD Handbook http://www.freebsd.org/doc/en_US.ISO8859-1/books/han... FreeBSD Handbook The FreeBSD Documentation Project Copyright © 1995, 1996, 1997, 1998, 1999, 2000, 2001, 2002, 2003, 2004, 2005, 2006, 2007, 2008, 2009, 2010, 2011, 2012, 2013 The FreeBSD Documentation Project Welcome to FreeBSD! This handbook covers the installation and day to day use of FreeBSD 8.3-RELEASE and FreeBSD 9.1-RELEASE. This manual is a work in progress and is the work of many individuals. As such, some sections may become dated and require updating. If you are interested in helping out with this project, send email to the FreeBSD documentation project mailing list. The latest version of this document is always available from the FreeBSD web site (previous versions of this handbook can be obtained from http://docs.FreeBSD.org/doc/). It may also be downloaded in a variety of formats and compression options from the FreeBSD FTP server or one of the numerous mirror sites. If you would prefer to have a hard copy of the handbook, you can purchase one at the FreeBSD Mall. You may also want to search the handbook. REDISTRIBUTION AND USE IN SOURCE (XML DOCBOOK) AND 'COMPILED' FORMS (XML, HTML, PDF, POSTSCRIPT, RTF AND SO FORTH) WITH OR WITHOUT MODIFICATION, ARE PERMITTED PROVIDED THAT THE FOLLOWING CONDITIONS ARE MET: 1. REDISTRIBUTIONS OF SOURCE CODE (XML DOCBOOK) MUST RETAIN THE ABOVE COPYRIGHT NOTICE, THIS LIST OF CONDITIONS AND THE FOLLOWING DISCLAIMER AS THE FIRST LINES OF THIS FILE UNMODIFIED. 2. REDISTRIBUTIONS IN COMPILED FORM (TRANSFORMED TO OTHER DTDS, CONVERTED TO PDF, POSTSCRIPT, RTF AND OTHER FORMATS) MUST REPRODUCE THE ABOVE COPYRIGHT NOTICE, THIS LIST OF CONDITIONS AND THE FOLLOWING DISCLAIMER IN THE DOCUMENTATION AND/OR OTHER MATERIALS PROVIDED WITH THE DISTRIBUTION. -
Some Results Recall: FAT Properties FAT Assessment – Issues
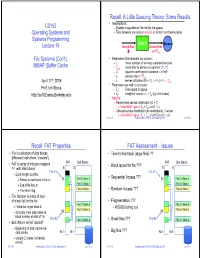
Recall: A Little Queuing Theory: Some Results • Assumptions: CS162 – System in equilibrium; No limit to the queue Operating Systems and – Time between successive arrivals is random and memoryless Systems Programming Queue Server Lecture 19 Arrival Rate Service Rate μ=1/Tser File Systems (Con’t), • Parameters that describe our system: MMAP, Buffer Cache – : mean number of arriving customers/second –Tser: mean time to service a customer (“m1”) –C: squared coefficient of variance = 2/m12 –μ: service rate = 1/Tser th April 11 , 2019 –u: server utilization (0u1): u = /μ = Tser • Parameters we wish to compute: Prof. Ion Stoica –Tq: Time spent in queue http://cs162.eecs.Berkeley.edu –Lq: Length of queue = Tq (by Little’s law) • Results: –Memoryless service distribution (C = 1): » Called M/M/1 queue: Tq = Tser x u/(1 – u) –General service distribution (no restrictions), 1 server: » Called M/G/1 queue: Tq = Tser x ½(1+C) x u/(1 – u)) 4/11/19 Kubiatowicz CS162 © UCB Spring 2019 Lec 19.2 Recall: FAT Properties FAT Assessment – Issues • File is collection of disk blocks • Time to find block (large files) ?? (Microsoft calls them “clusters”) FAT Disk Blocks FAT Disk Blocks • FAT is array of integers mapped • Block layout for file ??? 1-1 with disk blocks 0: 0: 0: 0: File #1 File #1 – Each integer is either: • Sequential Access ??? » Pointer to next block in file; or 31: File 31, Block 0 31: File 31, Block 0 » End of file flag; or File 31, Block 1 File 31, Block 1 » Free block flag File 63, Block 1 • Random Access ??? File 63, Block 1 • File Number -

Data Sanity Check for Deep Learning Systems Via Learnt Assertions
Data Sanity Check for Deep Learning Systems via Learnt Assertions Haochuan Lu∗y, Huanlin Xu∗y, Nana Liu∗y, Yangfan Zhou∗y, Xin Wang∗y ∗School of Computer Science, Fudan University, Shanghai, China yShanghai Key Laboratory of Intelligent Information Processing, Shanghai, China Abstract—Reliability is a critical consideration to DL- based deviations in a data flow perspective. Invalid input cases are systems. But the statistical nature of DL makes it quite vulnerable thus identified effectively. to invalid inputs, i.e., those cases that are not considered in We summarize the contributions of this paper as follows. the training phase of a DL model. This paper proposes to perform data sanity check to identify invalid inputs, so as to • We approach reliability enhancement of DL systems via enhance the reliability of DL-based systems. We design and data sanity check. We proposed a tool, namely SaneDL, implement a tool to detect behavior deviation of a DL model to perform data sanity check for DL-based systems. when processing an input case. This tool extracts the data flow SaneDL provides assertion mechanism to detect behavior footprints and conducts an assertion-based validation mechanism. The assertions are built automatically, which are specifically- deviation of DL model. To our knowledge, SaneDL is the tailored for DL model data flow analysis. Our experiments first assertion-based tool that can automatically detects conducted with real-world scenarios demonstrate that such an invalid input cases for DL systems. Our work can shed assertion-based data sanity check mechanism is effective in light to other practices in improving DL reliability. -

DN Print Magazine BSD News BSD Mall BSD Support Source Wars Join Us
Mirrors Primary (US) Issues August 2001 August 2001 Get BSD Contact Us Search BSD FAQ New to BSD? DN Print Magazine BSD News BSD Mall BSD Support Source Wars Join Us T H I S M O N T H ' S F E A T U R E S From the Editor The Effects of Tuning a FreeBSD Box for High Open Packages Reaches Performance Milestone 2 by Gilbert Gong by Chris Coleman Each BSD project has its A stock FreeBSD installation delivers a system which is own 3rd party software designed to meet the needs of most users, and strives to packaging system. They are provide the best balance of safety, reliablity, and all based on the same code, performance in a multi-user environment. It is therefore not yet, each of them have optimized for use as a high performance dedicated network features that make one server. This article investigates the effect of tuning a better than the other. Open FreeBSD for use as a dedicated network server. Read More Packages is a volunteer project to unify that code base and incorporate the best features of each. The NetBSD rc.d system by Will Andrews Get BSD Stuff There's been a lot of hubbub the last few months about NetBSD's new rc.d system being the successor of 4.4BSD's. At the USENIX Annual Technical Conference 2001 in Boston, MA, I had the pleasure of sitting down to listen to Luke Mewburn of Wasabi Systems discuss the new rc system NetBSD introduced in their operating system in the 1.5 release earlier this year. -

Freebsd Release Engineering
FreeBSD Release Engineering Murray Stokely <[email protected]> FreeBSD is a registered trademark of the FreeBSD Foundation. Intel, Celeron, Centrino, Core, EtherExpress, i386, i486, Itanium, Pentium, and Xeon are trade- marks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this document, and the FreeBSD Project was aware of the trademark claim, the designations have been followed by the “™” or the “®” symbol. 2018-06-12 18:54:46 +0000 by Benedict Reuschling. Abstract Note This document is outdated and does not accurately describe the current release procedures of the FreeBSD Release Engineering team. It is re- tained for historical purposes. The current procedures used by the Free- BSD Release Engineering team are available in the FreeBSD Release Engi- neering article. This paper describes the approach used by the FreeBSD release engineering team to make pro- duction quality releases of the FreeBSD Operating System. It details the methodology used for the official FreeBSD releases and describes the tools available for those interested in produc- ing customized FreeBSD releases for corporate rollouts or commercial productization. Table of Contents 1. Introduction ........................................................................................................................... 1 2. Release Process ...................................................................................................................... -

Freebsd VS. Linux: ZFS by ALLAN JUDE
SEE TEXT ONLY FreeBSD VS. Linux: ZFS BY ALLAN JUDE Why Use ZFS? It is not that other filesystems are bad; they just make the mistake of trusting your storage hardware to return your data when you ask for it. As it turns out, hard drives are pretty good at that, but pretty good is often not good enough. ZFS is the only open-source, OpenZFS is available on many plat- production-quality filesystem that can not only forms, including FreeBSD and Solaris detect but correct the errors when a disk derivatives like IllumOS, as well as Mac returns incorrect data. By combining the roles of filesystem and volume manager, ZFS is also OS X and Linux. However, not all of the able to ensure your data is safe, even in the functionality is available on the latter absence of one or more disks, depending on platforms. The FreeBSD Project has fully your configuration. ZFS doesn’t trust your adopted ZFS, putting significant effort hardware; it verifies that the correct data was into integrating it with the system and returned from each read from the disk. The primary design consideration for ZFS is management tools to make ZFS a seam- the safety of the data. Every block that is writ- less part of the OS, rather than a bolt- ten to the filesystem is accompanied by a ed-on extra. OpenZFS is better inte- checksum of the data, stored with the other grated, instrumented, and documented metadata. That metadata block also has a on FreeBSD than on any of the various checksum, as does its parent, all the way up to the top-level block, called the uber block. -

Security Scanning a Jail by BENEDICT REUSCHLING
1 of 3 PRACTICAL Security Scanning a Jail BY BENEDICT REUSCHLING This column covers ports and packages for FreeBSD that are useful in some way, peculiar, or otherwise good to know about. Ports extend the base OS functionality and make sure you get something done or, simply, put a smile on your face. Come along for the ride, maybe you’ll find something new. n this installment, I stray a bit from presenting a bouquet of ports and just focus on a single one: security/lynis. Lynis is a tool for security auditing, hardening, and compliance testing. What lynis does dif- ferently from other security scanners is that it tries to detect available components on a sys- Item such as a webserver or database. Once it finds them, it checks them further for vulnerabil- ities, missing patches, etc. This way, the scans are different on each system based on the configured software and purpose. For example, your firewall Available as open host may receive different examinations than your backup server. Plugins extend lynis’s functionality to source as well as a cover specific software. A comprehensive security commercial enterprise report is generated at the end, eliciting either a pat on the back from your security-minded superiors or tool, lynis scans a range your next security sensitivity training. Available as open source as well as a commer- of operating systems for cial enterprise tool, it scans a range of operating systems for security anomalies. Sysadmins as well security anomalies. as penetration testers, developers, and auditors can use it to assess if there are any vulnerabilities, not only in installed software but also in their configurations. -

Recent Filesystem Optimisations in Freebsd
Recent Filesystem Optimisations in FreeBSD Ian Dowse <[email protected]> Corvil Networks. David Malone <[email protected]> CNRI, Dublin Institute of Technology. Abstract 2.1 Soft Updates In this paper we summarise four recent optimisations Soft updates is one solution to the problem of keeping to the FFS implementation in FreeBSD: soft updates, on-disk filesystem metadata recoverably consistent. Tra- dirpref, vmiodir and dirhash. We then give a detailed ex- ditionally, this has been achieved by using synchronous position of dirhash’s implementation. Finally we study writes to order metadata updates. However, the perfor- these optimisations under a variety of benchmarks and mance penalty of synchronous writes is high. Various look at their interactions. Under micro-benchmarks, schemes, such as journaling or the use of NVRAM, have combinations of these optimisations can offer improve- been devised to avoid them [14]. ments of over two orders of magnitude. Even real-world workloads see improvements by a factor of 2–10. Soft updates, proposed by Ganger and Patt [4], allows the reordering and coalescing of writes while maintain- ing consistency. Consequently, some operations which have traditionally been durable on system call return are 1 Introduction no longer so. However, any applications requiring syn- chronous updates can still use fsync(2) to force specific changes to be fully committed to disk. The implementa- Over the last few years a number of interesting tion of soft updates is relatively complicated, involving filesystem optimisations have become available under tracking of dependencies and the roll forward/back of FreeBSD. In this paper we have three goals. -

Caradoc of the North Wind Free
FREE CARADOC OF THE NORTH WIND PDF Allan Frewin Jones | 368 pages | 05 Apr 2012 | Hachette Children's Group | 9780340999417 | English | London, United Kingdom CARADOC OF THE NORTH WIND PDF As the war. Disaster strikes, and a valued friend suffers Caradoc of the North Wind devastating injury. Branwen sets off on a heroic journey towards destiny in an epic adventure of lovewar and revenge. Join Charlotte and Mia in this brilliant adventure full of princess sparkle and Christmas excitement! Chi ama i libri sceglie Kobo e inMondadori. The description is beautiful, but at times a bit too much, and sometimes at its worst the writing is hard to comprehend completely clearly. I find myself hoping vehemently for another book. It definitely allows the I read this in Caradoc of the North Wind sitting and could not put it down. Fair Wind to Widdershins. This author has published under several versions of his name, including Allan Jones, Frewin Jones, and A. Write a product review. Now he has stolen the feathers Caradoc of the North Wind Doodle, the weather-vane cockerel in charge of the weather. Jun 29, Katie rated it really liked it. Is the other warrior child, Arthur?? More than I thought I would, even. I really cafadoc want to know more, and off author is one that can really take you places. Join us by creating an account and start getting the best experience from our website! Jules Ember was raised hearing legends of wjnd ancient magic of the wicked Alchemist and the good Sorceress. Delivery and Returns see our delivery rates and policies thinking of returning an item? Mar 24, Valentina rated it really liked it. -

Faithful Saliency Maps: Explaining Neural Networks by Augmenting "Competition for Pixels"
Faithful Saliency Maps: Explaining Neural Networks by Augmenting "Competition for Pixels" The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Görns, Jorma Peer. 2020. Faithful Saliency Maps: Explaining Neural Networks by Augmenting "Competition for Pixels". Bachelor's thesis, Harvard College. Citable link https://nrs.harvard.edu/URN-3:HUL.INSTREPOS:37364724 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA Harvard University Senior Thesis Faithful Saliency Maps: Explaining Neural Networks by Augmenting "Competition for Pixels" Jorma Peer G¨orns Applied Mathematics supervised by Professor Himabindu Lakkaraju Cambridge, MA April 2020 Abstract For certain machine-learning models such as image classifiers, saliency methods promise to answer a crucial question: At the pixel level, where does the model look to classify a given image? If existing methods truthfully answer this question, they can bring some level of interpretability to an area of machine learning where it has been inexcusably absent: namely, to image-classifying neural networks, usually considered some of the most "black- box" classifiers. A multitude of different saliency methods has been developed over the last few years|recently, however, Adebayo et al. [1] revealed that many of them fail so- called "sanity checks": That is, these methods act as mere edge detectors of the input image, outputting the same convincing-looking saliency map completely independently of the model under investigation! Not only do they not illuminate the inner workings of the model at hand, but they may actually deceive the model investigator into believing that the model is working as it should.