NP-Completeness (Chapter 8)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Extended Branch Decomposition Graphs: Structural Comparison of Scalar Data
Eurographics Conference on Visualization (EuroVis) 2014 Volume 33 (2014), Number 3 H. Carr, P. Rheingans, and H. Schumann (Guest Editors) Extended Branch Decomposition Graphs: Structural Comparison of Scalar Data Himangshu Saikia, Hans-Peter Seidel, Tino Weinkauf Max Planck Institute for Informatics, Saarbrücken, Germany Abstract We present a method to find repeating topological structures in scalar data sets. More precisely, we compare all subtrees of two merge trees against each other – in an efficient manner exploiting redundancy. This provides pair-wise distances between the topological structures defined by sub/superlevel sets, which can be exploited in several applications such as finding similar structures in the same data set, assessing periodic behavior in time-dependent data, and comparing the topology of two different data sets. To do so, we introduce a novel data structure called the extended branch decomposition graph, which is composed of the branch decompositions of all subtrees of the merge tree. Based on dynamic programming, we provide two highly efficient algorithms for computing and comparing extended branch decomposition graphs. Several applications attest to the utility of our method and its robustness against noise. 1. Introduction • We introduce the extended branch decomposition graph: a novel data structure that describes the hierarchical decom- Structures repeat in both nature and engineering. An example position of all subtrees of a join/split tree. We abbreviate it is the symmetric arrangement of the atoms in molecules such with ‘eBDG’. as Benzene. A prime example for a periodic process is the • We provide a fast algorithm for computing an eBDG. Typ- combustion in a car engine where the gas concentration in a ical runtimes are in the order of milliseconds. -

Exploiting C-Closure in Kernelization Algorithms for Graph Problems
Exploiting c-Closure in Kernelization Algorithms for Graph Problems Tomohiro Koana Technische Universität Berlin, Algorithmics and Computational Complexity, Germany [email protected] Christian Komusiewicz Philipps-Universität Marburg, Fachbereich Mathematik und Informatik, Marburg, Germany [email protected] Frank Sommer Philipps-Universität Marburg, Fachbereich Mathematik und Informatik, Marburg, Germany [email protected] Abstract A graph is c-closed if every pair of vertices with at least c common neighbors is adjacent. The c-closure of a graph G is the smallest number such that G is c-closed. Fox et al. [ICALP ’18] defined c-closure and investigated it in the context of clique enumeration. We show that c-closure can be applied in kernelization algorithms for several classic graph problems. We show that Dominating Set admits a kernel of size kO(c), that Induced Matching admits a kernel with O(c7k8) vertices, and that Irredundant Set admits a kernel with O(c5/2k3) vertices. Our kernelization exploits the fact that c-closed graphs have polynomially-bounded Ramsey numbers, as we show. 2012 ACM Subject Classification Theory of computation → Parameterized complexity and exact algorithms; Theory of computation → Graph algorithms analysis Keywords and phrases Fixed-parameter tractability, kernelization, c-closure, Dominating Set, In- duced Matching, Irredundant Set, Ramsey numbers Funding Frank Sommer: Supported by the Deutsche Forschungsgemeinschaft (DFG), project MAGZ, KO 3669/4-1. 1 Introduction Parameterized complexity [9, 14] aims at understanding which properties of input data can be used in the design of efficient algorithms for problems that are hard in general. The properties of input data are encapsulated in the notion of a parameter, a numerical value that can be attributed to each input instance I. -

3.1 Matchings and Factors: Matchings and Covers
1 3.1 Matchings and Factors: Matchings and Covers This copyrighted material is taken from Introduction to Graph Theory, 2nd Ed., by Doug West; and is not for further distribution beyond this course. These slides will be stored in a limited-access location on an IIT server and are not for distribution or use beyond Math 454/553. 2 Matchings 3.1.1 Definition A matching in a graph G is a set of non-loop edges with no shared endpoints. The vertices incident to the edges of a matching M are saturated by M (M-saturated); the others are unsaturated (M-unsaturated). A perfect matching in a graph is a matching that saturates every vertex. perfect matching M-unsaturated M-saturated M Contains copyrighted material from Introduction to Graph Theory by Doug West, 2nd Ed. Not for distribution beyond IIT’s Math 454/553. 3 Perfect Matchings in Complete Bipartite Graphs a 1 The perfect matchings in a complete b 2 X,Y-bigraph with |X|=|Y| exactly c 3 correspond to the bijections d 4 f: X -> Y e 5 Therefore Kn,n has n! perfect f 6 matchings. g 7 Kn,n The complete graph Kn has a perfect matching iff… Contains copyrighted material from Introduction to Graph Theory by Doug West, 2nd Ed. Not for distribution beyond IIT’s Math 454/553. 4 Perfect Matchings in Complete Graphs The complete graph Kn has a perfect matching iff n is even. So instead of Kn consider K2n. We count the perfect matchings in K2n by: (1) Selecting a vertex v (e.g., with the highest label) one choice u v (2) Selecting a vertex u to match to v K2n-2 2n-1 choices (3) Selecting a perfect matching on the rest of the vertices. -

Approximation Algorithms
Lecture 21 Approximation Algorithms 21.1 Overview Suppose we are given an NP-complete problem to solve. Even though (assuming P = NP) we 6 can’t hope for a polynomial-time algorithm that always gets the best solution, can we develop polynomial-time algorithms that always produce a “pretty good” solution? In this lecture we consider such approximation algorithms, for several important problems. Specific topics in this lecture include: 2-approximation for vertex cover via greedy matchings. • 2-approximation for vertex cover via LP rounding. • Greedy O(log n) approximation for set-cover. • Approximation algorithms for MAX-SAT. • 21.2 Introduction Suppose we are given a problem for which (perhaps because it is NP-complete) we can’t hope for a fast algorithm that always gets the best solution. Can we hope for a fast algorithm that guarantees to get at least a “pretty good” solution? E.g., can we guarantee to find a solution that’s within 10% of optimal? If not that, then how about within a factor of 2 of optimal? Or, anything non-trivial? As seen in the last two lectures, the class of NP-complete problems are all equivalent in the sense that a polynomial-time algorithm to solve any one of them would imply a polynomial-time algorithm to solve all of them (and, moreover, to solve any problem in NP). However, the difficulty of getting a good approximation to these problems varies quite a bit. In this lecture we will examine several important NP-complete problems and look at to what extent we can guarantee to get approximately optimal solutions, and by what algorithms. -

A New Spectral Bound on the Clique Number of Graphs
A New Spectral Bound on the Clique Number of Graphs Samuel Rota Bul`o and Marcello Pelillo Dipartimento di Informatica - University of Venice - Italy {srotabul,pelillo}@dsi.unive.it Abstract. Many computer vision and patter recognition problems are intimately related to the maximum clique problem. Due to the intractabil- ity of this problem, besides the development of heuristics, a research di- rection consists in trying to find good bounds on the clique number of graphs. This paper introduces a new spectral upper bound on the clique number of graphs, which is obtained by exploiting an invariance of a continuous characterization of the clique number of graphs introduced by Motzkin and Straus. Experimental results on random graphs show the superiority of our bounds over the standard literature. 1 Introduction Many problems in computer vision and pattern recognition can be formulated in terms of finding a completely connected subgraph (i.e. a clique) of a given graph, having largest cardinality. This is called the maximum clique problem (MCP). One popular approach to object recognition, for example, involves matching an input scene against a stored model, each being abstracted in terms of a relational structure [1,2,3,4], and this problem, in turn, can be conveniently transformed into the equivalent problem of finding a maximum clique of the corresponding association graph. This idea was pioneered by Ambler et. al. [5] and was later developed by Bolles and Cain [6] as part of their local-feature-focus method. Now, it has become a standard technique in computer vision, and has been employing in such diverse applications as stereo correspondence [7], point pattern matching [8], image sequence analysis [9]. -

Multi-Budgeted Matchings and Matroid Intersection Via Dependent Rounding
Multi-budgeted Matchings and Matroid Intersection via Dependent Rounding Chandra Chekuri∗ Jan Vondrak´ y Rico Zenklusenz Abstract ing: given a fractional point x in a polytope P ⊂ Rn, ran- Motivated by multi-budgeted optimization and other applications, domly round x to a solution R corresponding to a vertex we consider the problem of randomly rounding a fractional solution of P . Here P captures the deterministic constraints that we x in the (non-bipartite graph) matching and matroid intersection wish the rounding to satisfy, and it is natural to assume that polytopes. We show that for any fixed δ > 0, a given point P is an integer polytope (typically a f0; 1g polytope). Of course the important issue is what properties we need R to x can be rounded to a random solution R such that E[1R] = (1 − δ)x and any linear function of x satisfies dimension-free satisfy, and this is dictated by the application at hand. A Chernoff-Hoeffding concentration bounds (the bounds depend on property that is useful in several applications is that R sat- δ and the expectation µ). We build on and adapt the swap isfies concentration properties for linear functions of x: that n rounding scheme in our recent work [9] to achieve this result. is, for any vector a 2 [0; 1] , we want the linear function P 1 Our main contribution is a non-trivial martingale based analysis a(R) = i2R ai to be concentrated around its expectation . framework to prove the desired concentration bounds. In this Ideally, we would like to have E[1R] = x, which would P paper we describe two applications. -

The Complexity of Multivariate Matching Polynomials
The Complexity of Multivariate Matching Polynomials Ilia Averbouch∗ and J.A.Makowskyy Faculty of Computer Science Israel Institute of Technology Haifa, Israel failia,[email protected] February 28, 2007 Abstract We study various versions of the univariate and multivariate matching and rook polynomials. We show that there is most general multivariate matching polynomial, which is, up the some simple substitutions and multiplication with a prefactor, the original multivariate matching polynomial introduced by C. Heilmann and E. Lieb. We follow here a line of investigation which was very successfully pursued over the years by, among others, W. Tutte, B. Bollobas and O. Riordan, and A. Sokal in studying the chromatic and the Tutte polynomial. We show here that evaluating these polynomials over the reals is ]P-hard for all points in Rk but possibly for an exception set which is semi-algebraic and of dimension strictly less than k. This result is analoguous to the characterization due to F. Jaeger, D. Vertigan and D. Welsh (1990) of the points where the Tutte polynomial is hard to evaluate. Our proof, however, builds mainly on the work by M. Dyer and C. Greenhill (2000). 1 Introduction In this paper we study generalizations of the matching and rook polynomials and their complexity. The matching polynomial was originally introduced in [5] as a multivariate polynomial. Some of its general properties, in particular the so called half-plane property, were studied recently in [2]. We follow here a line of investigation which was very successfully pursued over the years by, among others, W. Tutte [15], B. -
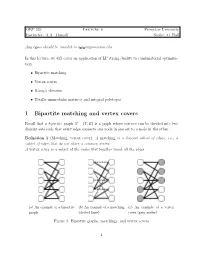
1 Bipartite Matching and Vertex Covers
ORF 523 Lecture 6 Princeton University Instructor: A.A. Ahmadi Scribe: G. Hall Any typos should be emailed to a a [email protected]. In this lecture, we will cover an application of LP strong duality to combinatorial optimiza- tion: • Bipartite matching • Vertex covers • K¨onig'stheorem • Totally unimodular matrices and integral polytopes. 1 Bipartite matching and vertex covers Recall that a bipartite graph G = (V; E) is a graph whose vertices can be divided into two disjoint sets such that every edge connects one node in one set to a node in the other. Definition 1 (Matching, vertex cover). A matching is a disjoint subset of edges, i.e., a subset of edges that do not share a common vertex. A vertex cover is a subset of the nodes that together touch all the edges. (a) An example of a bipartite (b) An example of a matching (c) An example of a vertex graph (dotted lines) cover (grey nodes) Figure 1: Bipartite graphs, matchings, and vertex covers 1 Lemma 1. The cardinality of any matching is less than or equal to the cardinality of any vertex cover. This is easy to see: consider any matching. Any vertex cover must have nodes that at least touch the edges in the matching. Moreover, a single node can at most cover one edge in the matching because the edges are disjoint. As it will become clear shortly, this property can also be seen as an immediate consequence of weak duality in linear programming. Theorem 1 (K¨onig). If G is bipartite, the cardinality of the maximum matching is equal to the cardinality of the minimum vertex cover. -

Exponential Family Bipartite Matching
The Problem The Model Model Estimation Experiments Exponential Family Bipartite Matching Tibério Caetano (with James Petterson, Julian McAuley and Jin Yu) Statistical Machine Learning Group NICTA and Australian National University Canberra, Australia http://tiberiocaetano.com AML Workshop, NIPS 2008 nicta-logo Tibério Caetano: Exponential Family Bipartite Matching 1 / 38 The Problem The Model Model Estimation Experiments Outline The Problem The Model Model Estimation Experiments nicta-logo Tibério Caetano: Exponential Family Bipartite Matching 2 / 38 The Problem The Model Model Estimation Experiments The Problem nicta-logo Tibério Caetano: Exponential Family Bipartite Matching 3 / 38 The Problem The Model Model Estimation Experiments Overview 1 1 2 2 6 6 3 5 5 3 4 4 nicta-logo Tibério Caetano: Exponential Family Bipartite Matching 4 / 38 The Problem The Model Model Estimation Experiments Overview nicta-logo Tibério Caetano: Exponential Family Bipartite Matching 5 / 38 The Problem The Model Model Estimation Experiments Assumptions Each couple ij has a pairwise happiness score cij Monogamy is enforced, and no person can be unmatched Goal is to maximize overall happiness nicta-logo Tibério Caetano: Exponential Family Bipartite Matching 6 / 38 The Problem The Model Model Estimation Experiments Applications Image Matching (Taskar 2004, Caetano et al. 2007) nicta-logo Tibério Caetano: Exponential Family Bipartite Matching 7 / 38 The Problem The Model Model Estimation Experiments Applications Machine Translation (Taskar et al. 2005) nicta-logo -

A Fast Algorithm for the Maximum Clique Problem � Patric R
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector Discrete Applied Mathematics 120 (2002) 197–207 A fast algorithm for the maximum clique problem Patric R. J. Osterg%# ard ∗ Department of Computer Science and Engineering, Helsinki University of Technology, P.O. Box 5400, 02015 HUT, Finland Received 12 October 1999; received in revised form 29 May 2000; accepted 19 June 2001 Abstract Given a graph, in the maximum clique problem, one desires to ÿnd the largest number of vertices, any two of which are adjacent. A branch-and-bound algorithm for the maximum clique problem—which is computationally equivalent to the maximum independent (stable) set problem—is presented with the vertex order taken from a coloring of the vertices and with a new pruning strategy. The algorithm performs successfully for many instances when applied to random graphs and DIMACS benchmark graphs. ? 2002 Elsevier Science B.V. All rights reserved. 1. Introduction We denote an undirected graph by G =(V; E), where V is the set of vertices and E is the set of edges. Two vertices are said to be adjacent if they are connected by an edge. A clique of a graph is a set of vertices, any two of which are adjacent. Cliques with the following two properties have been studied over the last three decades: maximal cliques, whose vertices are not a subset of the vertices of a larger clique, and maximum cliques, which are the largest among all cliques in a graph (maximum cliques are clearly maximal). -

Map-Matching Using Shortest Paths
Map-Matching Using Shortest Paths Erin Chambers Brittany Terese Fasy Department of Computer Science School of Computing and Dept. Mathematical Sciences Saint Louis University Montana State University Saint Louis, Missouri, USA Montana, USA [email protected] [email protected] Yusu Wang Carola Wenk Department of Computer Science and Engineering Department of Computer Science The Ohio State University Tulane University Columbus, Ohio, USA New Orleans, Louisianna, USA [email protected] [email protected] ABSTRACT desired path Q should correspond to the actual path in G that the We consider several variants of the map-matching problem, which person has traveled. Map-matching algorithms in the literature [1, seeks to find a path Q in graph G that has the smallest distance to 2, 6] consider all possible paths in G as potential candidates for Q, a given trajectory P (which is likely not to be exactly on the graph). and apply similarity measures such as Hausdorff or Fréchet distance In a typical application setting, P models a noisy GPS trajectory to compare input curves. from a person traveling on a road network, and the desired path Q We propose to restrict the set of potential paths in G to a natural should ideally correspond to the actual path in G that the person subset: those paths that correspond to shortest paths, or concatena- has traveled. Existing map-matching algorithms in the literature tions of shortest paths, in G. Restricting the set of paths to which consider all possible paths in G as potential candidates for Q. We a path can be matched makes sense in many settings. -

Lecture 3: Approximation Algorithms 1 1 Set Cover, Vertex Cover, And
Advanced Algorithms 02/10, 2017 Lecture 3: Approximation Algorithms 1 Lecturer: Mohsen Ghaffari Scribe: Simon Sch¨olly 1 Set Cover, Vertex Cover, and Hypergraph Matching 1.1 Set Cover Problem (Set Cover) Given a universe U of elements f1; : : : ; ng, and collection of subsets S = fS1;:::;Smg of subsets of U, together with cost a cost function c(Si) > 0, find a minimum cost subset of S, that covers all elements in U. The problem is known to be NP-Complete, therefore we are interested in algorithms that give us a good approximation for the optimum. Today we will look at greedy algorithms. Greedy Set Cover Algorithm [Chv79] Let OPT be the optimal cost for the set cover problem. We will develop a simple greedy algorithm and show that its output will differ by a certain factor from OPT. The idea is simply to distribute the cost of picking a set Si over all elements that are newly covered. Then we always pick the set with the lowest price-per-item, until we have covered all elements. In pseudo-code have have C ; Result ; while C 6= U c(S) S arg minS2S jSnCj c(S) 8e 2 (S n C) : price-per-item(e) jSnCj C C [ S Result Result [ fSg end return Result Theorem 1. The algorithm gives us a ln n + O(1) approximation for set cover. Proof. It is easy to see, that all n elements are covered by the output of the algorithm. Let e1; : : : ; en be the elements in the order they are covered by the algorithm.