Detecting & Defeating the China Chopper Web Shell | Fireeye
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

NEWS: Fake Whatsapp App May Have Been Built to Spy on Iphone Users – What You Need to Know a Fake Version of the Whatsapp Mess
NEWS: Fake WhatsApp app may have been built to spy on iPhone users – what you need to know A fake version of the WhatsApp messaging app is suspected of being created by an Italian spyware company to snoop upon individuals and steal sensitive data. The bogus app, uncovered by cybersecurity researchers at Citizen Lab and journalists at Motherboard, appears to be linked to an Italian firm called Cy4gate which develops “lawful interception” technology. https://hotforsecurity.bitdefender.com/blog/fake-whatsapp-app-may-have-been-built-to-spy-on-iphone- users-what-you-need-to-know-25270.html SOC teams spend nearly a quarter of their day handling suspicious emails Security professionals know that responding to relentless, incoming streams of suspicious emails can be a labor-intensive task, but a new study shared exclusively with SC Media in advance indicates just how time- consuming it actually is. Researchers at email security firm Avanan claim to have authored the “first comprehensive research study” that quantifies the amount of time security operations center (SOC) employees spend preventing, responding to, and investigating emails that successfully bypassed default security and are flagged by end users or other reporting mechanisms. https://www.scmagazine.com/home/email-security/soc-teams-spend-nearly-a-quarter-of-their-day- handling-suspicious-emails/ How to motivate employees to take cybersecurity seriously How can we push employees / users to take cybersecurity to heart? Dr. Maria Bada, external behavioral scientist at AwareGO, has been working on the answer for years. After studying media psychology, focusing her Ph.D. on behavior change, and working towards the treatment of excessive internet use in children and adolescents, nearly ten years ago she opted to join Oxford University as a postdoctoral researcher on cyberculture and online behavior. -

Web Shell 101 Joe Schottman Infosecon 2018 Oct
Web Shell 101 Joe Schottman InfoSeCon 2018 Oct. 26, 2018 About Me Senior Security Analyst for BB&T Legal Stuff 2 How To Reach Me @JoeSchottman on Twitter [email protected] www.joeschottman.com Add me on LinkedIn Find me on local Slacks 3 Agenda What is a Web Shell? How do Web Shells work? How can you detect them? Not going to cover how to use them 4 Definitions for this talk 5 If you’re playing security conference bingo 6 First, a diversion Equifax hack ▪ ▪ ▪ 8 Equifax hack 9 Equifax hack 10 Equifax hack 11 “ 12 “ 13 What is a Web Shell? 14 A subset of malware that runs on web servers 15 Used by APT groups 16 But also script kiddies 17 Someone else’s code ▪ PHP ▪ JSP ▪ Perl ▪ Ruby ▪ Python ▪ Shell Scripts ▪ ASP 18 Mostly scripting languages 19 Designed to control your server via HTTP 20 Imagine an evil web application 21 Executes just like your web applications 22 Unless the attacker takes steps to avoid it... 23 Used for different purposes 24 Hidden in different ways 25 How do they get on systems? 26 Web Shells are not the initial attack 27 Why at least two problems? ▪ ▪ ▪ 28 Let’s consider where in the attack Web Shells are used ▪ ▪ 29 Cyber Kill Chain 30 ATT&CK Discovery Lateral movement Collection Exfiltration Command and control 31 ATT&CK 32 Time to engage incident response ▪ ▪ ▪ 33 A funny aside 34 Metasploit makes some Web Shells easy 35 Detecting Web Shells Strategies 38 39 You do get permission before doing research, right? VirusTotal 41 File integrity monitoring 42 In an ideal world.. -

" Detecting Malicious Code in a Web Server "
UNIVERSITY OF PIRAEUS DEPARTMENT OF DIGITAL SYSTEMS Postgraduate Programme "TECHNO-ECONOMIC MANAGEMENT & SECURITY OF DIGITAL SYSTEMS" " Detecting malicious code in a web server " Thesis of Soleas Agisilaos Α.Μ. : MTE14024 Supervisor Professor: Dr. Christoforos Ntantogian Athens, 2016 Table of Contents Abstract ....................................................................................................................................................... 3 1.Introduction .............................................................................................................................................. 4 2.What is a web shell .................................................................................................................................. 5 2.1.Web shell examples ................................................................................................................... 6 2.2.Web shell prevention .............................................................................................................. 24 2.3.What is a backdoor ................................................................................................................. 26 2.4.Known backdoors .................................................................................................................... 31 2.5.Prevent from backdoors ......................................................................................................... 32 3. NeoPi analysis ........................................................................................................................................ -

Using Web Honeypots to Study the Attackers Behavior
i 2017 ENST 0065 EDITE - ED 130 Doctorat ParisTech THÈSE pour obtenir le grade de docteur délivré par TELECOM ParisTech Spécialité « Informatique » présentée et soutenue publiquement par Onur CATAKOGLU le 30 Novembre 2017 Using Web Honeypots to Study the Attackers Behavior Directeur de thèse : Davide BALZAROTTI T H Jury È William ROBERTSON, Northeastern University Rapporteur Magnus ALMGREN, Chalmers University of Technology Rapporteur S Yves ROUDIER, University of Nice Sophia Antipolis Examinateur Albert LEVI, Sabanci University Examinateur E Leyla BILGE, Symantec Research Labs Examinateur TELECOM ParisTech École de l’Institut Télécom - membre de ParisTech Using Web Honeypots to Study the Attackers Behavior Thesis Onur Catakoglu [email protected] École Doctorale Informatique, Télécommunication et Électronique, Paris ED 130 November 30, 2017 Advisor: Prof. Dr. Davide Balzarotti Examiners: EURECOM, Sophia-Antipolis Prof. Dr. Yves ROUDIER, University of Nice Sophia Antipolis Reviewers: Prof. Dr. William ROBERTSON, Prof. Dr. Albert LEVI, Northeastern University Sabanci University Prof. Dr. Magnus ALMGREN, Dr. Leyla BILGE, Chalmers University of Technology Symantec Research Labs Acknowledgements First and foremost I would like to express my gratitude to my supervisor, Davide Balzarotti. He was always welcoming whenever I need to ask questions, discuss any ideas and even when he was losing in our long table tennis matches. I am very thankful for his guidance throughout my PhD and I will always keep the mental image of him staring at me for various reasons as a motivation to move on when things will get tough in the future. I would also like to thank my reviewers for their constructive comments regarding this thesis. -

User's Guide • Oracle Enterprise Manager Licensing Information User Manual 2.9.2 Integrating Compliance Check Results with Third-Party Tool
Autonomous Health Framework User’s Guide 21c F31833-01 November 2020 Autonomous Health Framework User’s Guide, 21c F31833-01 Copyright © 2016, 2020, Oracle and/or its affiliates. Primary Authors: Nirmal Kumar, Janet Stern Contributing Authors: Richard Strohm, Mark Bauer, Douglas Williams, Aparna Kamath, Subhash Chandra Contributors: Girdhari Ghantiyala, Gareth Chapman, Robert Caldwell, Vern Wagman, Mark Scardina, Ankita Khandelwal, Girish Adiga, Walter Battistella, Jesus Guillermo Munoz Nunez, Sahil Kumar, Daniel Semler, Carol Colrain This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. -

Mitigating Webshell Attacks Through Machine Learning Techniques
future internet Article Mitigating Webshell Attacks through Machine Learning Techniques You Guo 1, Hector Marco-Gisbert 2,* and Paul Keir 2 1 School of Computing Science and Engineering, Xi’an Technological University, Xi’an 710021, China 2 School of Computing, Engineering and Physical Sciences, University of the West of Scotland, High Street, Paisley PA1 2BE, UK * Correspondence: [email protected]; Tel.:+44-141-849-4418 Received: 10 December 2019; Accepted: 2 January 2020; Published: 14 January 2020 Abstract: A webshell is a command execution environment in the form of web pages. It is often used by attackers as a backdoor tool for web server operations. Accurately detecting webshells is of great significance to web server protection. Most security products detect webshells based on feature-matching methods—matching input scripts against pre-built malicious code collections. The feature-matching method has a low detection rate for obfuscated webshells. However, with the help of machine learning algorithms, webshells can be detected more efficiently and accurately. In this paper, we propose a new PHP webshell detection model, the NB-Opcode (naïve Bayes and opcode sequence) model, which is a combination of naïve Bayes classifiers and opcode sequences. Through experiments and analysis on a large number of samples, the experimental results show that the proposed method could effectively detect a range of webshells. Compared with the traditional webshell detection methods, this method improves the efficiency and accuracy of webshell detection. Keywords: webshell attacks; machine learning; naïve Bayes; opcode sequence 1. Introduction With the development of web technology and the explosive growth of information, web security becomes more and more important. -
List Drive Using Cmd
List drive using cmd click here to download You can display or list drives in CMD / Command Prompt or PowerShell, using wmic, diskpart, fsutil, psdrive command line, in Windows 10 / 8. The command that erases the drive during this process is "Clean". In this article " Clean" From the diskpart prompt, type list disk and press Enter. Shows the. If you want to use it in a script, then wrap it in for /f with the skip=1 . that whenever typed will run the given command and list all volume letters. How to create a partition from Command Prompt. First of all, open the To view the available disks on your system, use the command list disk. Diskpart is a separate suite of commands that runs in the command window in a particular disk, partition, or volume it must first be selected with the "list disk". You can manually assign permanent drive letters in Windows Type the following command to list all the volumes on your computer and. How does one get a list of the drives connected from the command line? For instance, sometimes I need to run chkdsk on a hdd, so I pop the. See drives in MS-DOS and the Windows command to list all available drives on the computer through. We can run the below command from windows command prompt to get the list of local drives. wmic logicaldisk get description,name | findstr /C:”Local” We can. Diskpart assign and remove drive letter with its syntax in the command prompt. There are And you can type list volume to see the details. -

WINDOWS POWERSHELL LOGGING CHEAT SHEET - Win 7/Win 2008 Or Later
WINDOWS POWERSHELL LOGGING CHEAT SHEET - Win 7/Win 2008 or later This “Windows PowerShell Logging Cheat Sheet” is intended to help you get started setting up basic and necessary PowerShell (Windows Management Framework) command and command line logging. This list includes some very common items that should be enabled, configured, gathered and harvested for any Log Management program. Start with these settings and add to it as you understand better what is in your logs and what you need. DEFINITIONS:: ENABLE: Things you must do to enable logging to start collecting and keeping events. CONFIGURE: Configuration that is needed to refine what events you will collect. GATHER: Tools/Utilities that you can use locally on the system to set or gather log related information – AuditPol, WEvtUtil, Find, etc. HARVEST : Events that you would want to harvest into some centralized Event log management solution like syslog, SIEM, Splunk, etc. RESOURCES: Places to get information on PowerShell Logging PS 2,3,4 Command Line Logging - http://technet.microsoft.com/en-us/library/hh847796.aspx PowerShell Transcript information - https://technet.microsoft.com/en-us/library/hh849687.aspx PS 4 - https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html PS 4 & 5 - https://blogs.msdn.microsoft.com/powershell/2015/06/09/powershell-the-blue-team - KEY for PS 5 https://www.blackhat.com/docs/us-14/materials/us-14-Kazanciyan-Investigating-Powershell-Attacks-WP.pdf http://learn-powershell.net/2014/08/26/more-new-stuff-in-powershell-v5-extra-powershell-auditing http://www.redblue.team/2016/01/powershell-traceless-threat-and-how- to.html?showComment=1464099315089#c3589963557794199352 https://www.carbonblack.com/wp-content/uploads/2016/04/Cb-Powershell-Deep-Dive-A-United-Threat-Research-Report-1.pdf INFORMATION:: 1. -

Windows Tool Reference
AppendixChapter A1 Windows Tool Reference Windows Management Tools This appendix lists sets of Windows management, maintenance, configuration, and monitor- ing tools that you may not be familiar with. Some are not automatically installed by Windows Setup but instead are hidden away in obscure folders on your Windows Setup DVD or CD- ROM. Others must be downloaded or purchased from Microsoft. They can be a great help in using, updating, and managing Windows. We’ll discuss the following tool kits: ■ Standard Tools—Our pick of handy programs installed by Windows Setup that we think are unappreciated and not well-enough known. ■ Support Tools—A set of useful command-line and GUI programs that can be installed from your Windows Setup DVD or CD-ROM. ■ Value-Added Tools—Several more sets of utilities hidden away on the Windows Setup CD-ROM. ■ Windows Ultimate Extras and PowerToys for XP—Accessories that can be downloaded for free from microsoft.com. The PowerToys include TweakUI, a program that lets you make adjustments to more Windows settings than you knew existed. ■ Resource Kits—A set of books published by Microsoft for some versions of Windows that includes a CD-ROM containing hundreds of utility programs. What you may not have known is that in some cases you can download the Resource Kit program toolkits with- out purchasing the books. ■ Subsystem for UNIX-Based Applications (SUA)—A package of network services and command-line tools that provide a nearly complete UNIX environment. It can be installed only on Windows Vista Ultimate and Enterprise, and Windows Server 2003. -
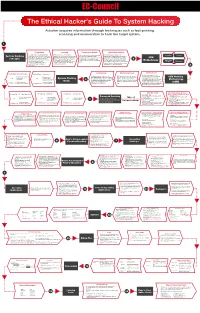
Download the Ethical Hacker's Guide to System Hacking
The Ethical Hacker's Guide To System Hacking Attacker acquires information through techniques such as foot printing, scanning and enumeration to hack the target system. 1 Footprinting Scanning Enumeration Module Vulnerability Analysis It is the process of accumulating data Vulnerability Assessment is an This is a procedure for identifying This is a method of intrusive probing, Footprinting Scanning System Hacking regarding a specific network environment. active hosts, open ports, and unnecessary through which attackers gather examination of the ability of a system or In this phase, the attacker creates a profile services enabled on ports. Attackers use information such as network user lists, application, including current security CEH concepts of the target organization, obtaining different types of scanning, such as port routing tables, security flaws, and procedures, and controls to with stand 2 information such as its IP address range, scanning network scanning, and simple network protocol data (SNMP) assault. Attackers perform this analysis Methodology Vulnerability namespace and employees. Enumeration vulnerability, scanning of target networks data. to identify security loopholes, in the target Analysis Footprinting eases the process of or systems which help in identifying organization’s network, communication system hacking by revealing its possible vulnerabilities. infrastructure, and end systems. vulnerabilities 3 Clearing Logs Maintaining Access Gaining Access Hacking Stage Escalating Privileges Hacking Stage Gaining Access It involves gaining access to To maintain future system access, After gaining access to the target low-privileged user accounts by To acquire the rights of To bypass access CEH Hacking attackers attempt to avoid recognition system, attackers work to maintain cracking passwords through Goal another user or Goal controls to gain System Hacking by legitimate system users. -

Hacking Exposed: Melting Down Memory
#RSAC SESSION ID: EXP=W04 HACKING EXPOSED: MELTING DOWN MEMORY George Kurtz Dmitri Alperovitch Elia Zaitsev Co-Founder & President/CEO Co-Founder & CTO Director CrowdStrike Inc. CrowdStrike Inc. Solutions Architecture @George_Kurtz @DAlperovitch CrowdStrike Inc. #RSAC THE HACKING EXPOSED OSCARS ARE BACK #RSAC THE NOMINEES FOR BEST TECHNIQUES ARE… #RSAC CATEGORY: CREDENTIAL THEFT DELIVERY: STRATEGIC WEB COMPROMISE USING SMB TECHNICAL BREAKDOWN #RSAC Variations of remote source Javascript + Dean Edwards Packer obfuscation Tiny image Hidden in JQuery related Javascript files #RSAC DEMO 6 REAL WORLD EXAMPLES #RSAC - Massive BERSERK BEAR credential harvesting campaign - Targeted numerous sectors — Chemical – Sept 2017 — Financial – Sept 2017 — Hospitality – Sept 2017 — Oil & Gas – April 2017 — Technology – April 2017 — Engineering – April 2017 — Education – April 2017 REAL WORLD EXAMPLES #RSAC Another variation used spear-phishing emails. Word Docs contain code that attempts to retrieve doc template from remote source over WebDAV 8 REAL WORLD EXAMPLES #RSAC - Post Harvesting Activity - Offline hash cracking - Pass the hash tools - Public facing services most vulnerable - Webmail - VPN - Remote conferencing software COUNTERMEASURES #RSAC - Implement Two-Factor Authentication (2FA) - Restrict or monitor SMB connectivity to remote servers - Robust password policies (length/duration/reuse) - Restrict or monitor remote user authentication - Leverage threat intel to track known SMB C2s #RSAC CATEGORY: WHITELISTING BYPASS DELIVERY: INSTALLUTIL TECHNICAL -

Web Shells in PHP, ASP, JSP, Perl, and Coldfusion
Web Shells In PHP, ASP, JSP, Perl, And ColdFusion by Joseph Giron 2009 [email protected] Web shells come in many shapes and sizes. From the most complex of shells such as r57 and c99 to something you came up with while toying around with variables and functions. This paper is to discuss ways of uploading and executing web shells on web servers. We will discuss web shells for: PHP, ASP, Java, Perl, and ColdfFusion. A lot of these sections look the same because they are essentially the same. In a broad generalization of things, exploiting java is no different from exploiting Perl - we're watching certain variables and functions. The main emphasis of this paper however will be on ASP and PHP as they are the most common languages used in web applications today. We will also discuss how I've been able to place web shells on web servers in each language, as well as provide vulnerable code to look for to aid on placing a web shell on the box. With that said, lets get this show on the road! Sections: $ Intro to PHP Web Shells $ RFI's in PHP $ LFI's in PHP $ File Upload Vulnerabilities (covers all languages) $ Web Shells in ASP $ Command Execution Vulnerabilities in ASP $ Web Shells in Perl $ Command Execution Vulnerabilities in Perl $ Web Shells in JSP $ Command Execution Vulnerabilities in JSP $ Web Shells in Cold Fusion $ Command Execution Vulnerabilities in Cold Fusion ############################ Intro to PHP Web Shells ############################ PHP web shells are vital to us hackers if we want to elevate our access or even retain it.