Posworld: Vulnerabilities Within Ingenico Telium 2 and Verifone VX and MX Series Point of Sales Terminals
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Annual Report
2017 Annual Report 2018 Notice & Proxy Statement February 8, 2018 Dear Fellow Stockholder: You are cordially invited to attend the 2018 Annual Meeting of Stockholders of VeriFone Systems, Inc. (“Verifone”). We will hold the meeting on Thursday, March 22, 2018 at 8:30 a.m., local time, at Verifone’s principal offices located at 88 W. Plumeria Drive, San Jose, CA 95134. We hope that you will be able to attend. Details of the business to be conducted at the Annual Meeting are provided in the attached Notice of 2018 Annual Meeting of Stockholders (the “Notice of Annual Meeting”) and Proxy Statement. As a stockholder, you will be asked to vote on a number of important matters. We encourage you to vote on all matters listed in the enclosed Notice of Annual Meeting. The Board of Directors recommends a vote FOR the proposals listed as proposals 1, 2 and 3 in the Notice of Annual Meeting. Board Oversight. As a Board of Directors, we are actively engaged in the oversight of Verifone. As directors, each of us makes a commitment to the extensive time and rigor required to serve on the Board. During 2017, the Board’s discussions focused in particular on the Company’s objectives of scaling its next-generation devices and in linking the Company’s device footprint to the Company’s cloud infrastructure. We also continued to focus on the Company’s strategy to return to growth. We believe that the Company has made significant progress on its transformation and look forward to the Company continuing to implement its growth strategy. -

VISA Europe AIS Certified Service Providers
Visa Europe Account Information Security (AIS) List of PCI DSS validated service providers Effective 08 September 2010 __________________________________________________ The companies listed below successfully completed an assessment based on the Payment Card Industry Data Security Standard (PCI DSS). 1 The validation date is when the service provider was last validated. PCI DSS assessments are valid for one year, with the next annual report due one year from the validation date. Reports that are 1 to 60 days late are noted in orange, and reports that are 61 to 90 days late are noted in red. Entities with reports over 90 days past due are removed from the list. It is the member’s responsibility to use compliant service providers and to follow up with service providers if there are any questions about their validation status. 2 Service provider Services covered by Validation date Assessor Website review 1&1 Internet AG Internet payment 31 May 2010 SRC Security www.ipayment.de processing Research & Consulting Payment gateway GmbH Payment processing a1m GmbH Payment gateway 31 October 2009 USD.de AG www.a1m.biz Internet payment processing Payment processing A6IT Limited Payment gateway 30 April 2010 Kyte Consultants Ltd www.A6IT.com Abtran Payment processing 31 July 2010 Rits Information www.abtran.com Security Accelya UK Clearing and Settlement 31 December 2009 Trustwave www.accelya.com ADB-UTVECKLING AB Payment gateway 30 November 2009 Europoint Networking WWW.ADBUTVECKLING.SE AB Adeptra Fraud Prevention 30 November 2009 Protiviti Inc. www.adeptra.com Debt Collection Card Activation Adflex Payment Processing 31 March 2010 Evolution LTD www.adflex.co.uk Payment Gateway/Switch Clearing & settlement 1 A PCI DSS assessment only represents a ‘snapshot’ of the security in place at the time of the review, and does not guarantee that those security controls remain in place after the review is complete. -

In This Issue
Welcome to the January edition of ACT News. This complimentary service is provided by ACT Canada; "building an informed marketplace". Please feel free to forward this to your colleagues. In This Issue 1. Editorial - payment innovation: where is the bar? 2. Desjardins and MasterCard bring new payment options to Canadians 3. Nanopay acquires MintChip from the Royal Canadian Mint 4. Canadian payments market transition: a study by the Canadian Payments Association 5. Suretap and EnStream take big steps forward with Societe de Transport de Montreal in mobile ticketing 6. New credit union association launches in Canada: Canadian Credit Union Association 7. Global study shows increasing security risks to payment data and lack of confidence in securing mobile payment methods 8. Samsung Pay to move online in 2016 9. Elavon delivers Apple Pay for Canadian businesses 10. Beware alleged experts’ scare tactics on mobile payments 11. Ingenico Group accelerates EMV and NFC acceptance in unattended environments with new partner program 12. Paynet delivers a safer payment service with Fraudxpert to its customers 13. VeriFone expands services offering for large retailers in the US and Canada with agreement to acquire AJB Software 14. VISA checkout added to Starbucks, Walmart, Walgreens 15. Gemalto is world's first vendor to receive complete MasterCard approval for cloud based payments 16. ICC Solutions offers a time-saving method and free guide for training staff to process card payments correctly ready for the new year! 17. Walmart adds masterpass as online payment method 18. Equinox and ACCEO partner to deliver integrated retail payment solution 19. UL receives UnionPay qualification for Chinese domestic market 20. -

Payment Solutions Built for Mobility
Payment Solutions Built for Mobility shift4.com | 800.265.5795 | [email protected] © 2020 Shift4 Payments, LLC. All rights reserved. Picking the Right Mobile Payment Solution for Your Business No matter what role you want mobility to play in your payment processing, you have choices from Shift4 Payments. We have put together a variety of solutions that support the latest mobile payment terminals and cover the most comprehensive set of features and implementation options. There are several supported options for ISVs and businesses that want to incorporate mobile payment processing into their offering. Below are several mobile payment solutions for your business: PAX Sleek and Modern. PAX’s line of mobile payment tablets — including their handheld A920 and A930 models — manages to pack an impressive amount of tech into its designs, including dual camera, 1D/2D scanner, and a built-in printer. These devices connect via 4G, Wi-Fi, or Bluetooth, and supports mobile acceptance of MSR, EMV, and NFC payments. ID TECH Versatile and Compact. ID TECH’s EMV Common Kernel family of devices includes OEM payment modules that are built into a variety of mobile hardware options, allowing businesses to expand their mobile payment capabilities to securely accept MSR, EMV, and NFC payments. Innowi Powerful and Portable. The ChecOut M from Innowi delivers an all-in-one mobile point of sale (mPOS) that fits in your pocket. This device supports Android and Windows OS and 4G, Wi-Fi, and Bluetooth connectivity options. Merchants of all types can accept MSR, EMV (w/chip & PIN), and NFC payments. Ingenico Advanced and Reliable. -

Frequently Asked Questions Converge Mobile – U.S
Frequently Asked Questions Converge Mobile – U.S. Features and Functionality Which mobile wallets does Converge Mobile support? Converge Mobile, using the NFC contactless capabilities of What is Converge Mobile? the Ingenico iCMP can accept: Converge Mobile is the mobile payment solution that offers • Apple Pay® you a way to accept payments securely while on-the-go. • Android Pay™ Simply download the Converge Mobile app from the Apple ® Store or the Google Play store. Purchase a supported card • Samsung Pay reader device and you’re ready to go! Converge Mobile can • PayPal® (when available) email receipts or it can be paired with one of two portable Does Converge Mobile print receipts? printers. Yes! The Converge Mobile app supports the Star SM‐T300i Which types of mobile devices are compatible with or Star SM‐T220i. Receipts can also be emailed to the Converge Mobile? consumer and a record of the transaction is accessible within Converge Mobile is supported on Android 5.0 (and higher) Converge Mobile and online at www.convergepay.com. and iOS 8.0 (and higher) devices including smartphones, Can my customers receive text receipts? tablets and iPads. Converge Mobile may work on lower Not at this time. We are working on adding this functionality versions but this is not supported by Elavon. in the future. Receipts can be delivered to your customer Can Converge Mobile run on a Windows or Blackberry via email. phone? Can a signature be captured in the app? Not at this time. Yes. A signature is accepted using the mobile app. The What card brands does Converge Mobile accept? signature is stored within Converge so if your customer Converge Mobile accepts Mastercard, Visa, Discover, and chooses to receive his/her receipt via email, a picture of the American Express. -
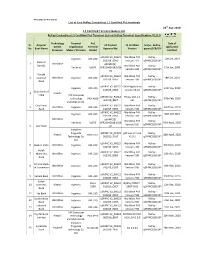
20Th Aug 2020 Sr. No. Acquirer Bank Name Technology Switch
NPCI/2020-21/RuPay/029 List of Live RuPay Contactless L3 Certified PoS terminals 20th Aug 2020 L3 Certified Terminal Models List RuPay Contactless L3 Certified PoS Terminal List on RuPay Terminal Specification V2.0.0 Technology Terminal PoS Date of Sr. Acquirer L2 Product L3 Certified Scope - RuPay- Switch /Application Terminal application No. Bank Name Approval No. Version qsparc/JCB/UPI Processor Maker / Provider Model Certified qSPARC.V2_ING22 Worldline PAY RuPay - Ingenico IWL 220 12th Jul, 2019 012019_0D55 Version 7.67 qSPARC/JCB/UPI Bank of 1 Worldline qSPARC(2)- Baroda Worldline PAY RuPay - Verifone Vx675 VER23042018:2018 17th Jan, 2020 Version 3.80 qSPARC/JCB/UPI 01 Punjab qSPARC.V2_ING22 Worldline PAY RuPay - 2 National Worldline Ingenico IWL 220 18th Jul, 2019 012019_0D55 Version 7.80 qSPARC/JCB/UPI Bank qSPARC.V2_ING22 CRDB Application RuPay - Ingenico IWL 220 14th Sep, 2019 012019_0D55 version V3.12 qSPARC/JCB/UPI State Bank of 3 Hitachi India PAX Computer qSPARC.V2_PAX18 Plutus V10.1.1 RuPay - Technology PAX A920 07th Feb, 2020 062018_8807 SBI qSPARC/JCB/UPI shenzhen co ltd. City Union qSPARC.V2_ING22 Worldline PAY RuPay - 4 Worldline Ingenico IWL 220 03rd Dec, 2019 Bank 012019_0D55 Version 7.80 qSPARC/JCB/UPI qSPARC.V2_ING22 Worldline PAY RuPay - Ingenico IWL 220 30th Oct 2019 012019_0D55 Version 7.80 qSPARC/JCB/UPI Worldline qSPARC(2)- Worldline PAY RuPay - Verifone Vx675 VER23042018:2018 05th April, 2020 Version 3.81 qSPARC/JCB/UPI 5 Axis Bank 01 Shenzhen Xinguodu qSPARC.V2_NEX20 g20inaxi Version RuPay - Hitachi NexGo G2 28th April, 2020 Technology Co. 052019_2A37 V1.0.2 qSPARC/JCB/UPI Ltd. -

Than a Year Has Passed Since Three Giant Mergers Promised to Change the Payments World
More than a year has passed since three giant mergers promised to change the payments world. Change has come, but not where many expected to see it. Volume Eighteen, Number Two • DigitalTransactions.net • February 2021 ALSO IN THIS ISSUE: Walmart’s New Fintech An Upshift for Parking Apps Ransomware Runs Rampant A Checklist for Bill Pay DigitalTransactions.net brings you the most important payments market news, in one place, updated the moment it happens Breaking news from the payments market, posted daily Concise, clean interface is easy to navigate Calendar of industry events Complete current and past issues of Digital Transactions magazine Detailed listings of payments market suppliers 13 years of payments news and analysis FEBRUARY 2021 • VOLUME 18, NUMBER 2 The Megamergers’ Subtle Impact 22 More than a year has passed since three giant mergers promised to change the payments world. Change has come, but not where many expected to see it. THE GIMLET EYE The Digital Dollar Revisited 4 TRENDS & TACTICS 6 Walmart Launches The Megamerger Green Dot’s PayPal vs. CFPB: It Trump’s Parting Shot: a Fintech That Wasn’t Latest Bid for the Ain’t Over Til It’s Over A Puzzling Ban on Unlike most startups, A potential FIS-Global Unbanked The U.S. District Court China-Based Apps this one will be a Payments deal blew up, Go2Bank is the latest handed PayPal a The departing president formidable player from but it showed merger initiative from one of big win, but it’s far barred Alipay and the get-go. fever hasn’t subsided. -

Ingenico Group Registration Document 2016
2016 REGISTRATION DOCUMENT INCLUDING THE ANNUAL FINANCIAL REPORT CONTENTS CHAIRMAN'S MESSAGE 3 CONSOLIDATED FINANCIAL PROFILE 4 5 STATEMENTS DECEMBER 31, 2016 131 KEY FIGURES 6 5.1 Consolidated income statement 132 INGENICO GROUP IN THE WORLD IN 2016 8 5.2 Consolidated statement of comprehensive income 133 5.3 Consolidated statement of fi nancial position 134 2016 IN 8 HIGHLIGHTS 10 5.4 Consolidated cash fl ow statement 136 HISTORY 12 5.5 Consolidated statement of change in equity 138 ORGANIZATIONAL CHART 5.6 Notes to the consolidated fi nancial statements 139 (AS AT DECEMBER 31, 2016) 14 5.7 Statutory auditors’ report on the consolidated fi nancial statements 193 PRESENTATION 1 OF THE GROUP 17 PARENT COMPANY FINANCIAL 6 STATEMENTS AT DECEMBER 31, 2016 195 1.1 Activity & strategy 18 1.2 Risk factors 28 6.1 Assets 196 6.2 Liabilities 197 6.3 Profi t and loss account 198 6.4 Notes to the parent company fi nancial statements 199 CORPORATE SOCIAL 2 RESPONSIBILITY 37 6.5 Statutory auditors’ report on the parent company annual fi nancial statements 219 2.1 CSR for Ingenico Group 38 6.6 Five-year fi nancial summary 220 2.2 Reporting scope and method 42 2.3 The Ingenico Group community 45 2.4 Ingenico Group’s contribution to society 53 COMBINED ORDINARY AND 2.5 Ingenico Group’s environmental approach 64 7 EXTRAORDINARY SHAREHOLDERS’ 2.6 Report by the independent third party, on the MEETING OF MAY 10, 2017 221 consolidated human resources, environmental and social information included in the management report 75 7.1 Draft agenda and proposed resolutions -

Heartland Acquisition
Dec. 18th, 2015 Edition #485 TSG Analysis of Global - Heartland Acquisition Subscribers: Please complete this brief 2 minute survey and help us improve NewsFilter! Thank you! Categories Featured Mobile Payments & This week, Global Payments' announced their acquisition of Bitcoin Heartland Payment Systems for $4.3B. The Strawhecker Regulation & Security Group (TSG) has since put together an analysis of the acquisition from the US merchant acquiring perspective. Economy Additionally, a comparison to 22 other transactions that have occurred in the Payments Industry over the last 5 years is Payments Press illustrated. Want to Advertise in NF? Save Up to 50% on Select eReports until 12/30 Still have research dollars to spend as 2015 winds down? Click here to learn Looking to kick-off the new year with a high ROI? more. Take a look at popular eReportsTSG published this year and save up to 50% until the end of the year. It's your research dollars TSG Resources - use it or lose it! TheStrawGroup.com TSG Resource Center PaymentsPulse.com TSG Overview Transaction Advisory Featured Global Payments to Acquire Heartland Payment Systems for Merchant Aggregation $4.3 Billion, Combining Leading Payments Technology Companies Case Study: Driving Value Through 12/15/15 Business Wire Competitive Bidding Global Payments Inc. (NYSE: GPN), a leading worldwide provider of payment technology services, announced today that it has entered into a definitive What Benefits Me By agreement to acquire Heartland Payment Systems, Inc. (NYSE: HPY), one of Paying a Credit Card the nation's largest payment companies. The transaction significantly Swipe Fee? expands Global Payments' U.S. -

VERIFONE E315 the PAY- ANYWHERE POS Retailers Can Securely Extend Their Reach with the Next-Generation Verifone E315
MOBILE HARDWARE VERIFONE e315 VERIFONE.COM VERIFONE e315 THE PAY- ANYWHERE POS Retailers can securely extend their reach with the next-generation Verifone e315. The device pairs with the Apple® iPhone® 5S and 5th generation iPod touch® to create a POS anywhere. It accommodates all transactions including mag-stripe, EMV chip and PIN and NFC/contactless payment. The innovative design ensures that the rear-facing camera, audio jack and other key controls remain available – while also providing longer battery life, improved ergonomics and durability. LEAD THE RETAIL REVOLUTION • Create a POS wherever the sale takes place • Check inventory or prices on the spot with integrated barcode scanner Works • Future-proof mobile POS is ready for all types of payments including EMV and with Apple iPod touch 5 NFC/contactless • Securely locks onto iPhone or iPod, keeping access to all ports and controls • Provides extended battery life, up to 12 hours depending on usage model – with up to 120 hours of standby time • Tactile keypad to support accessibility requirements Integrated Barcode Scanner SPECIFICATIONS for Quick Processor 400 MHz | ARM11 32-bit RISC processor Look-up Memory 128MB Flash | 64MB SDRAM Display 128 x 32, monochrome Connectivity Apple Lightning connector Card Readers Triple track bi-directional MSR | landed smart card Accepts ISO14443 A&B | MiFare | ISO18082 | EMVCo L1 & L2 certification | Contactless Mag-stripe, supports major NFC/contactless schemes EMV and Other Standard 1 SAM slot | 1D/2D barcode imager, Class 2 laser radiation Features -

Why Merchants Keep Failing to Protect Card Data Fines
May/June 2018 www.isoandagent.com Why merchants keep failing to protect card data Fines. Bad publicity. Class actions. Are any of these penalties severe enough to stop data breaches? 001_ISO050618 1 4/24/18 4:16 PM Your Payment Partner of Choice E800 E500 E600 A920 Smart Retail Solutions Introducing PAX’s new Smart Retail Solutions. Sleek designs that make them look more like a tablet than a payment terminal. PAX has launched an application management platform for resellers and partners to manage applications with the PAX Smart Retail Solutions. US Headquarters: Regional O ce: 4901 Belfort Road, Suite 130 40 West Baseline Road, Suite 210 Jacksonville, FL 32256 Tempe, AZ 85283 +1-877-859-0099 | [email protected] +1-877-859-0099 | [email protected] © 2017 PAX Technology Limited. All Rights Reserved. PAX’s name and PAX’s logo are registered trademarks of PAX Technology Limited. All other products or services mentioned in this advertisement are trademarks, service marks, registered trademarks or registered service marks of their respective owners. pax-smart-retail-iso&agent.indd002_ISO050618 2 1 4/23/20184/23/18 5:10:10 8:02 AMPM Contents 10 Why merchants fail to protect data Are the incentives for protecting card data so lopsided that merchants feel little need to do more? Or is it wrong to ask merchants to fix the faults in a payment card ecosystem they had little hand in creating? Processing Cards Processing 04 14 20 An African startup builds on bitcoin A cryptocurrency debit card looks Why Verifone needs to be taken Bitpesa’s founder saw bitcoin as the next past the card networks’ limits private, despite its turnaround big thing, and stuck with her plan even The idea of a crypto debit card has been Verifone has worked hard to recover as the craze around cryptocurrencies done before — and in some cases, has from its self-inflicted wounds. -

Contactless Terminals - February 2018
Amex Enabled Acquiring Solutions -Contactless Terminals - February 2018 Terminal Vendor Amex Enabled Terminal Model Amex L2 Kernel/Firmware Version L2 Approval Status TP Version Expresspay L2 Approval Date Month Year Expresspay L2 Expiry Date LoA Issue date Advanced Mobile Payment Inc. Yes AMP 3000 1.2.6 Approved 1.3 7/18/2016 9 2016 7/18/2019 9/1/2016 Advanced Mobile Payment Inc. Yes AMP 7000 Version 1.2 1.2.6 Approved 1.3 7/18/2016 8 2016 7/18/2019 8/1/2016 Advanced Mobile Payment Inc. Yes AMP 9000 1.2.6 Approved 1.3 7/18/2016 9 2016 7/18/2019 9/1/2016 AEVI International GmbH Yes Albert MTPT10 v1.1.0e Approved 1.3 10/1/2015 10 2015 10/1/2018 10/30/2015 Arcelik No BEKO 220TR CBM-EMVCL-AEP v1.0.1 Approved 1.4.6 4/13/2017 4 2017 4/12/2020 8/10/2017 Atos Worldline Yes Yomani xpEng01.00.00 Approved 12/9/2015 11 2015 12/9/2018 11/5/2015 Atos Worldline Yes Yonami AR/ML xpEng 01.00.00 Approved 1/24/2016 11 2015 1/24/2019 11/5/2015 Atos Worldline Yes YONEO Master Version A0 xpEng 01.00.00 Approved 6/4/2016 4 2016 6/4/2019 4/27/2016 Atos Worldline Yes YONEO Slave Version A0 xpEng 01.00.00 Approved 6/11/2016 4 2016 6/11/2019 4/27/2016 Atos Worldline Yes YOXIMO Version AA xpEng 01.00.00 Approved 5/27/2016 4 2016 5/27/2019 4/27/2016 BBPOS International Limited Yes Chipper 2X 1.01 Approved 1.3 3/11/2016 3 2016 3/11/2019 3/17/2016 BBPOS International Limited Yes WisePad 2 1.0 Approved 1.3 3/2/2016 3 2016 3/2/2019 3/17/2016 BBPOS International Limited Yes WisePad 2 Plus 1.0 Approved 1.3 7/20/2016 8 2016 7/20/2019 8/1/2016 BBPOS International Limited Yes WisePOS 1.0 Approved 1.3 7/22/2016 8 2016 7/22/2019 8/2/2016 Castles Technology Co., Ltd.