Versatile Ipad Forensic Acquisition Using the Apple Camera
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ios Security
iOS Security May 2012 2 Contents Page 3 Introduction Page 4 System Architecture Secure Boot Chain System Software Personalization App Code Signing Runtime Process Security Page 7 Encryption and Data Protection Hardware Security Features File Data Protection Passcodes Classes Keychain Data Protection Keybags Page 13 Network Security SSL, TLS VPN Wi-Fi Bluetooth Page 15 Device Access Passcode Protection Configuration Enforcement Mobile Device Management Device Restrictions Remote Wipe Page 18 Conclusion A Commitment to Security Page 19 Glossary 3 Introduction Apple designed the iOS platform with security at its core. Keeping information secure on mobile devices is critical for any user, whether they’re accessing corporate and customer information or storing personal photos, banking information, and addresses. Because every user’s information is important, iOS devices are built to maintain a high level of security without compromising the user experience. Data Protection Class iOS devices provide stringent security technology and features, and yet also are easy to use. The devices are designed to make security as transparent as possible. Many security App Sandbox features are enabled by default, so IT departments don’t need to perform extensive configurations. And some key features, like device encryption, are not configurable, so Software User Partition users cannot disable them by mistake. For organizations considering the security of iOS devices, it is helpful to understand OS Partition how the built-in security features work together to provide a secure mobile computing platform. Encrypted File System iPhone, iPad, and iPod touch are designed with layers of security. Low-level hardware and firmware features protect against malware and viruses, while high-level OS features allow secure access to personal information and corporate data, prevent unauthorized Kernel use, and help thwart attacks. -

Isam: an Iphone Stealth Airborne Malware
iSAM: An iPhone Stealth Airborne Malware Dimitrios Damopoulos, Georgios Kambourakis, and Stefanos Gritzalis Info-Sec-Lab Laboratory of Information and Communications Systems Security, University of the Aegean, Samos, Greece {ddamop,gkamb,sgritz}@aegean.gr http://www.icsd.aegean.gr/info-sec-lab Abstract. Modern and powerful mobile devices comprise an attractive target for any potential intruder or malicious code. The usual goal of an attack is to acquire users’ sensitive data or compromise the device so as to use it as a stepping stone (or bot) to unleash a number of attacks to other targets. In this paper, we focus on the popular iPhone device. We create a new stealth and airborne malware namely iSAM able to wirelessly infect and self-propagate to iPhone devices. iSAM incorporates six different malware mechanisms, and is able to connect back to the iSAM bot master server to update its programming logic or to obey commands and unleash a synchronized attack. Our analysis unveils the internal mechanics of iSAM and discusses the way all iSAM components contribute towards achieving its goals. Although iSAM has been specifically designed for iPhone it can be easily modified to attack any iOS-based device. Keywords: Malware, iPhone, iOS, Jailbreak, Stealth, Airborne, Rootkit. 1 Introduction Mobile devices have evolved and experienced an immense popularity over the last few years. These devices have penetrated the market due to the variety of data services they offer, such as texting, emailing, browsing the Internet, documents editing, listening to music, watching videos and playing games in addition to the traditional voice services. As a result, analysts are expecting a mobile device population of 5 billion by 2015 [1]. -

MOVR Mobile Overview Report April – June 2017
MOVR Mobile Overview Report April – June 2017 The first step in a great mobile experience TBD 2 The first step in a great mobile experience TBD 3 The first step in a great mobile experience Q1 2017 to Q2 2017 Comparisons Top Smartphones Top Smartphones Africa Asia Europe N. America Oceania S. America • New to the list this Apple iPhone 5S 1.3% 2.9% 4.1% 3.5% 3.9% 3.1% quarter are the Apple Apple iPhone 6 2.2% 4.8% 5.6% 9.3% 10.1% 4.5% iPhone SE and the Apple iPhone 6 Plus 0.8% 2.4% 0.9% 3.7% 3.2% 1.0% Samsung J7 Prime. Apple iPhone 6S 1.7% 4.4% 6.3% 11.0% 13.9% 3.1% Apple iPhone 6S Plus 0.7% 2.6% 1.1% 6.1% 4.6% 0.9% • Dropping off the list Apple iPhone 7 1.2% 2.9% 4.0% 7.6% 9.3% 2.2% are the Motorola Moto Apple iPhone 7 Plus 0.7% 3.1% 1.3% 6.9% 6.2% 1.1% G4, Samsung Galaxy J2 Apple iPhone SE 0.3% 0.6% 2.4% 2.2% 2.1% 1.0% (2015), and the Huawei P8 Lite 2.2% 0.3% 2.1% 0.2% 0.2% 0.6% Vodafone Smart Kicka. Motorola Moto G 0.0% 0.0% 0.1% 0.2% 0.0% 2.1% Motorola Moto G (2nd Gen) 0.0% 0.1% 0.0% 0.1% 0.1% 2.6% • North America and Motorola MotoG3 0.0% 0.1% 0.1% 0.2% 0.1% 3.1% Oceania continue to be Samsung Galaxy A3 1.2% 0.9% 2.2% 0.1% 0.2% 0.5% concentrated markets Samsung Galaxy Grand Neo 1.8% 0.8% 0.8% 0.1% 0.1% 0.6% for brands, with the Samsung Galaxy Grand Prime 0.5% 1.0% 1.5% 0.9% 0.1% 3.5% top smartphones Samsung Galaxy J1 1.8% 0.6% 0.3% 0.1% 0.3% 0.8% accounting for 63.7% and 74.4% Samsung Galaxy J1 Ace 2.5% 0.2% 0.0% 0.1% 0.3% 0.7% respectively. -

Proposition De Stratégie
iOS applications auditing AppSec Forum Western Switzerland Julien Bachmann / [email protected] › Motivations › Quick review of the environment › Common flaws › Information gathering › Network analysis › Software reverse engineering Preamble › Security engineer @ SCRT › Teacher @ HEIG-VD › Areas of interest focused on reverse engineering, software vulnerabilities, mobile devices security and OS internals › Not an Apple fanboy › But like all the cool kids... › Goals › This presentation aims at sharing experience and knowledge in iOS apps pentesting › Contact › @milkmix_ motivations | why ? › More and more applications › Most of Fortune-500 are deploying iPads › Growth in mobile banking › Mobile eShop › Internal applications › Need for security › Access and storage of sensitive information › Online payments environment | devices › Latest devices › Apple A5 / A5X / A6 / A6X › Based on ARMv7 specifications › Processor › RISC › Load-store architecture › Fixed length 32-bits instructions environment | simulator › Beware › Simulator != emulator › More like a sandbox › Code compiled for Intel processors › 32-bits › ~/Library/Application Support/iPhone Simulator/<v>/Applications/<id>/ environment | applications › Localisation › ~/Music/iTunes/iTunes Music/Mobile Applications/ › /var/mobile/Applications/<guid>/<appname>.app/ › .ipa › Used to deploy applications › Zip file environment | applications › .plist › Used to store properties › XML files, sometimes in a binary format › Associates keys (CFString, CFNumber, …) with values › plutil (1) › Convert binary plist file to its XML representation flaws | communication snooping › Secure by default › Well... at least if the developer is using URLs starting with HTTPS:// › Even if a fake certificate is presented ! › The DidFailWithError method is called flaws | communication snooping › Ok, but what about real life ? › A lot of development environments are using self-signed certificates › No built-in method to include certificates in the simulator › Obviously, what did the developers ? › Let's check what's on stackoverflow.com.. -

Apple, Inc. Collegiate Purchase Program Premier Price List January 11, 2011
Apple, Inc. Collegiate Purchase Program Premier Price List January 11, 2011 Revisions to the December 7, 2010 Collegiate Purchase Program Premier Price List Effective January 11, 2011 PRODUCTS ADDED TO THE PRICE LIST PRODUCTS REPRICED ON THE PRICE LIST PRODUCTS REMOVED FROM THE PRICE LIST This Price List supersedes all previous Price Lists. Products subject to discontinuation without notice. Prices subject to change without notice. Education Solutions Apple iPod Learning Lab The Apple iPod Learning Lab provides schools with the ideal solution for managing multiple iPod devices in the classroom. The solution includes (20) iPod touch 8GB devices housed in a durable and easy-to-use Apple-exclusive mobile cart capable of storing and charging up to 40 iPod devices. The cart's ability to sync up to 20 iPod devices at a time from one computer makes it quick and easy to set up the devices for student use. The mobile cart's secure, roll-top door can be locked for safe iPod storage. The cart also includes room for storage of up to four notebook computers and a variety of iPod accessories. And, because the cart is mobile, it can be easily shared among multiple classrooms. Choose one of the pre-configured solutions below, or build your own custom iPod lab by visiting http://edu1.apple.com/custom_ipod_lab/. Recommended add-ons: The MacBook is an ideal companion for the Apple iPod Learning Lab. Create compelling education content with iLife and organize and share that content via iTunes. Apple Professional Development prepares teachers to effectively integrate iPod devices and podcasting into their curriculum. -

1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27
Case5:12-cv-00630-LHK Document304 Filed11/21/12 Page1 of 13 1 QUINN EMANUEL URQUHART & STEPTOE & JOHNSON, LLP SULLIVAN, LLP John Caracappa (pro hac vice) 2 Charles K. Verhoeven (Bar No. 170151) [email protected] [email protected] 1330 Connecticut Avenue, NW 3 Kevin A. Smith (Bar No. 250814) [email protected] Washington, D.C. 20036 4 50 California Street, 22nd Floor Telephone: (202) 429-6267 San Francisco, California 94111 Facsimile: (202) 429-3902 5 Telephone: (415) 875-6600 Facsimile: (415) 875-6700 6 Kevin P.B. Johnson (Bar No. 177129 (CA)) 7 [email protected] Victoria F. Maroulis (Bar No. 202603) 8 [email protected] 555 Twin Dolphin Drive, 5th Floor 9 Redwood Shores, California 94065 Telephone: (650) 801-5000 10 Facsimile: (650) 801-5100 11 William C. Price (Bar No. 108542) [email protected] 12 Michael L. Fazio (Bar No. 228601) [email protected] 13 865 South Figueroa Street, 10th Floor Los Angeles, California 90017-2543 14 Telephone: (213) 443-3000 Facsimile: (213) 443-3100 15 Attorneys for SAMSUNG ELECTRONICS 16 CO., LTD., SAMSUNG ELECTRONICS AMERICA, INC. and SAMSUNG 17 TELECOMMUNICATIONS AMERICA, LLC 18 UNITED STATES DISTRICT COURT 19 NORTHERN DISTRICT OF CALIFORNIA, SAN JOSE DIVISION 20 APPLE INC., a California corporation, CASE NO. 12-CV-00630-LHK (PSG) 21 Plaintiff, 22 SAMSUNG'S NOTICE OF MOTION AND vs. MOTION FOR LEAVE TO AMEND AND 23 SUPPLEMENT ITS INFRINGEMENT SAMSUNG ELECTRONICS CO., LTD., a CONTENTIONS 24 Korean corporation; SAMSUNG ELECTRONICS AMERICA, INC., a New Date: January 8, 2012 25 York corporation; SAMSUNG Time: 10:00 a.m. -

Beginners Guide to Developing for a Jailbroken Ios Plaxorm
Beginners Guide to Developing for a Jailbroken iOS Plaorm Priya Rajagopal Twier: @rajagp Blog: hp://www.priyaontech.com CocoaHeads, Jan 2012 Jailbreaking is Legal (..at least in the US) Priya Rajagopal, CocoaHeads,2012 Why develop for a jailbroken plaorm? • Develop run-Ume patches (.dylibs) that can be automacally loaded and shared across apps – Link with third part dylibs (eg- BTStack) • Hook into “system” apps and control plaorm behavior – Eg. Mobile Safari, Springboard • UUlize features not exposed through SDK’s public APIs to build something really cool Priya Rajagopal, CocoaHeads,2012 3 Why develop for a jailbroken plaorm? • More control over the plaorm – Terminal window, ssh, scp, rm etc. It’s a unix system. • Don’t need an Apple developer’s license – Self signed apps, pseudo signed apps • You don’t even need a Mac – You can even develop on the phone (Cool!) • Opons : – Distribute through Cydia – Internal Enterprise apps – Personal use. If you can’t find it, you can build it! Priya Rajagopal, CocoaHeads,2012 4 Tethered vs. Untethered Jailbreak • Tethered – You need to tether your device to your PC to reboot it. Quite inconvenient • Untethered – You don’t need to tether your device to your PC to reboot it. • ParUal Untethered – Tethered but you can reboot untethered to enable minimal funcUonality Priya Rajagopal, CocoaHeads,2012 5 Jailbreak Sogware (If its not free, it’s a scam) • RedSn0w (Mac /Windows) • Jailbreakme.com (Web) • PwnageTool (Mac) • GreenPois0n (Mac/Windows) Priya Rajagopal, CocoaHeads,2012 6 Status of iOS Jailbreak -
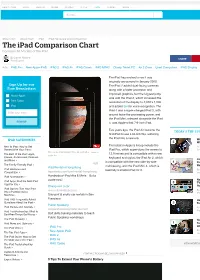
The Ipad Comparison Chart Compare All Models of the Ipad
ABOUT.COM FOOD HEALTH HOME MONEY STYLE TECH TRAVEL MORE Search... About.com About Tech iPad iPad Hardware and Competition The iPad Comparison Chart Compare All Models of the iPad By Daniel Nations SHARE iPad Expert Ads iPAD Pro New Apple iPAD iPAD 2 iPAD Air iPAD Cases iPAD MINI2 Cheap Tablet PC Air 2 Case Used Computers iPAD Display The iPad has evolved since it was originally announced in January 2010. Sign Up for our The iPad 2 added dual-facing cameras Free Newsletters along with a faster processor and improved graphics, but the biggest jump About Apple was with the iPad 3, which increased the Tech Today resolution of the display to 2,048 x 1,536 iPad and added Siri for voice recognition. The iPad 4 was a super-charged iPad 3, with Enter your email around twice the processing power, and the iPad Mini, released alongside the iPad SIGN UP 4, was Apple's first 7.9-inch iPad. Two years ago, the iPad Air became the TODAY'S TOP 5 PICKS IN TECH first iPad to use a 64-bit chip, ushering IPAD CATEGORIES the iPad into a new era. We Go Hands-On 5 With the OnePlus X New to iPad: How to Get The latest in Apple's lineup include the By Faryaab Sheikh Started With Your iPad iPad Pro, which super-sizes the screen to Smartphones Expert The entire iPad family: Pro, Air and Mini. Image © 12.9 inches and is compatible with a new The Best of the iPad: Apps, Apple, Inc. -

Distributed Tuning of Boundary Resources: the Case of Apple's Ios Service System
Ben Eaton, Silvia Elaluf-Calderwood, Carsten Sørensen and Youngjin Yoo Distributed tuning of boundary resources: the case of Apple's iOS service system Article (Published version) (Refereed) Original citation: Eaton, Ben, Elaluf-Calderwood, Silvia, Sorensen, Carsten and Yoo, Youngjin (2015) Distributed tuning of boundary resources: the case of Apple's iOS service system. MIS Quarterly, 39 (1). pp. 217-243. ISSN 0276-7783 Reuse of this item is permitted through licensing under the Creative Commons: © 2015 The Authors CC-BY This version available at: http://eprints.lse.ac.uk/63272/ Available in LSE Research Online: August 2015 LSE has developed LSE Research Online so that users may access research output of the School. Copyright © and Moral Rights for the papers on this site are retained by the individual authors and/or other copyright owners. You may freely distribute the URL (http://eprints.lse.ac.uk) of the LSE Research Online website. SPECIAL ISSUE: SERVICE INNOVATION IN THE DIGITAL AGE DISTRIBUTED TUNING OF BOUNDARY RESOURCES: THE CASE OF APPLE’S IOS SERVICE SYSTEM1 Ben Eaton Department of IT Management, Copenhagen Business School, Copenhagen, DENMARK {[email protected]} Silvia Elaluf-Calderwood and Carsten Sørensen Department of Management, The London School of Economics and Political Science, London, GREAT BRITAIN {[email protected]} {[email protected]} Youngjin Yoo Fox School of Business, Temple University, Philadelphia, PA 19140 UNITED STATES {[email protected]} The digital age has seen the rise of service systems involving highly distributed, heterogeneous, and resource- integrating actors whose relationships are governed by shared institutional logics, standards, and digital technology. -

Investigation Numérique & Terminaux Apple
Investigation numérique & terminaux Apple iOS Acquisition de données Mathieu RENARD ANSSI/LAM mathieu.renard[à]ssi.gouv.fr 1 Constat # Démocratisation de l’usage terminaux mobile en entreprise – Stockage d’informations professionnelles – Sécurité, management des terminaux mal ou non maitrisé # Men aces – Accès illégitimes au données professionnelles / réseau de l’entité – Usurpation d’identité – Atteinte à la disponibilité du terminal # Risques accentués par le caractère mobile des terminaux (perte, vol) # Les terminaux mobiles sont des cibles de choix pour les attaquants 2 Investigation numérique iOS Outils # Framework iPhoneDataProtection – Acquisition physique (iPhone 4 et inférieur) # iPhone Backup analyzer2 – Analyse des sauvegardes iOS # Celebrite UFED – Solution commerciale – Acquisition physique (iPhone 4 et inférieur) – Acquisition Logique (backup & AFC) 3 Investigation numérique & terminaux Apple iOS # La liste d’outils d’investigation numérique pour iOS est limitée # Aucun outil ne permet d’infirmer ou confirmer une compromission # Nécessité de développer des méthodes et outils 4 iPhone Architecture et sécurité http://iphoneroot.com/ipad-mini-gets-x-rayed-photo/#more-18711 5 Architecture matérielle Let’s open the box BCM43342 Wi-Fi SoC SK Hynix H2JTDG8UD3MBR 16 GB NAND Apple A7 APL0698 SoC Qualcomm MDM9615M LTE Modem (BaseBand) NXP LPC1800 Qualcomm WTR1605L M7 Motion coprocessor LTE/HSPA+/CDMA2K/TDSCDMA/EDGE/GPS (Cortex M3) (Tranceiver) http://www.chipworks.com/en/technical-competitive-analysis/resources/blog/inside-the-iphone-5s/ -

Apple, Inc. Collegiate Purchase Program Premier Price List March 11, 2011
Apple, Inc. Collegiate Purchase Program Premier Price List March 11, 2011 Revisions to the February 15, 2011 Collegiate Purchase Program Premier Price List Effective March 11, 2011 PRODUCTS ADDED TO THE PRICE LIST D5889LL/A APS APD Expert On Call (up to 4 hours) 680.00 MC939LL/A iPad Smart Cover - Polyurethane - Gray 39.00 MC940ZM/A iPad 2 Dock 29.00 MC941LL/A iPad Smart Cover - Polyurethane - Pink 39.00 MC942LL/A iPad Smart Cover - Polyurethane - Blue 39.00 MC944LL/A iPad Smart Cover - Polyurethane - Green 39.00 MC945LL/A iPad Smart Cover - Polyurethane - Orange 39.00 MC947LL/A iPad Smart Cover - Leather - Black 69.00 MC948LL/A iPad Smart Cover Leather - Tan 69.00 MC949LL/A iPad Smart Cover Leather - Navy 69.00 MC952LL/A iPad Smart Cover Leather - Cream 69.00 MC953ZM/A Digital AV Adapter (HDMI) 39.00 MC769LL/A iPad Wi-Fi 16GB Black 499.00 MC770LL/A iPad Wi-Fi 32GB Black 599.00 MC916LL/A iPad Wi-Fi 64GB Black 699.00 MC979LL/A iPad Wi-Fi 16GB White 499.00 MC980LL/A iPad Wi-Fi 32GB White 599.00 MC981LL/A iPad Wi-Fi 64GB White 699.00 MC773LL/A iPad Wi-Fi + 3G 16GB Black 629.00 MC774LL/A iPad Wi-Fi + 3G 32GB Black 729.00 MC775LL/A iPad Wi-Fi + 3G 64GB Black 829.00 MC982LL/A iPad Wi-Fi + 3G 16GB White 629.00 MC983LL/A iPad Wi-Fi + 3G 32GB White 729.00 MC984LL/A iPad Wi-Fi + 3G 64GB White 829.00 PRODUCTS REPRICED ON THE PRICE LIST PRODUCTS REMOVED FROM THE PRICE LIST MA407LL/A Mac mini 110W power adapter MB595LL/A AppleCare Premium Service and Support Plan - Enrollment Kit for Xserve This Price List supersedes all previous Price Lists. -

Die Meilensteine Der Computer-, Elek
Das Poster der digitalen Evolution – Die Meilensteine der Computer-, Elektronik- und Telekommunikations-Geschichte bis 1977 1977 1978 1979 1980 1981 1982 1983 1984 1985 1986 1987 1988 1989 1990 1991 1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 2018 2019 2020 und ... Von den Anfängen bis zu den Geburtswehen des PCs PC-Geburt Evolution einer neuen Industrie Business-Start PC-Etablierungsphase Benutzerfreundlichkeit wird gross geschrieben Durchbruch in der Geschäftswelt Das Zeitalter der Fensterdarstellung Online-Zeitalter Internet-Hype Wireless-Zeitalter Web 2.0/Start Cloud Computing Start des Tablet-Zeitalters AI (CC, Deep- und Machine-Learning), Internet der Dinge (IoT) und Augmented Reality (AR) Zukunftsvisionen Phasen aber A. Bowyer Cloud Wichtig Zählhilfsmittel der Frühzeit Logarithmische Rechenhilfsmittel Einzelanfertigungen von Rechenmaschinen Start der EDV Die 2. Computergeneration setzte ab 1955 auf die revolutionäre Transistor-Technik Der PC kommt Jobs mel- All-in-One- NAS-Konzept OLPC-Projekt: Dass Computer und Bausteine immer kleiner, det sich Konzepte Start der entwickelt Computing für die AI- schneller, billiger und energieoptimierter werden, Hardware Hände und Finger sind die ersten Wichtige "PC-Vorläufer" finden wir mit dem werden Massenpro- den ersten Akzeptanz: ist bekannt. Bei diesen Visionen geht es um die Symbole für die Mengendarstel- schon sehr früh bei Lernsystemen. iMac und inter- duktion des Open Source Unterstüt- möglichen zukünftigen Anwendungen, die mit 3D-Drucker zung und lung. Ägyptische Illustration des Beispiele sind: Berkley Enterprice mit neuem essant: XO-1-Laptops: neuen Technologien und Konzepte ermöglicht Veriton RepRap nicht Ersatz werden.