The Tactical and Strategic Use of Small Arms by Terrorists
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ellies 2018 Finalists Announced
Ellies 2018 Finalists Announced New York, The New Yorker top list of National Magazine Award nominees; CNN’s Don Lemon to host annual awards lunch on March 13 NEW YORK, NY (February 1, 2018)—The American Society of Magazine Editors today published the list of finalists for the 2018 National Magazine Awards for Print and Digital Media. For the fifth year, the finalists were first announced in a 90-minute Twittercast. ASME will celebrate the 53rd presentation of the Ellies when each of the 104 finalists is honored at the annual awards lunch. The 2018 winners will be announced during a lunchtime presentation on Tuesday, March 13, at Cipriani Wall Street in New York. The lunch will be hosted by Don Lemon, the anchor of “CNN Tonight With Don Lemon,” airing weeknights at 10. More than 500 magazine editors and publishers are expected to attend. The winners receive “Ellies,” the elephant-shaped statuettes that give the awards their name. The awards lunch will include the presentation of the Magazine Editors’ Hall of Fame Award to the founding editor of Metropolitan Home and Saveur, Dorothy Kalins. Danny Meyer, the chief executive officer of the Union Square Hospitality Group and founder of Shake Shack, will present the Hall of Fame Award to Kalins on behalf of ASME. The 2018 ASME Award for Fiction will also be presented to Michael Ray, the editor of Zoetrope: All-Story. The winners of the 2018 ASME Next Awards for Journalists Under 30 will be honored as well. This year 57 media organizations were nominated in 20 categories, including two new categories, Social Media and Digital Innovation. -

The United States and Democracy Promotion in Iraq and Lebanon in the Aftermath of the Events of 9/11 and the 2003 Iraq War
The United States and democracy promotion in Iraq and Lebanon in the aftermath of the events of 9/11 and the 2003 Iraq War A Thesis Submitted to the Institute of Commonwealth Studies, School of Advanced Study, University of London in fulfilment of the requirements for the Degree of PhD. in Political Science. By Abess Taqi Ph.D. candidate, University of London Internal Supervisors Dr. James Chiriyankandath (Senior Research Fellow, Institute of Commonwealth Studies, School of Advanced Study, University of London) Professor Philip Murphy (Director, Institute of Commonwealth Studies, School of Advanced Study, University of London) External Co-Supervisor Dr. Maria Holt (Reader in Politics, Department of Politics and International Relations, University of Westminster) © Copyright Abess Taqi April 2015. All rights reserved. 1 | P a g e DECLARATION I hereby declare that this thesis is my own work and effort and that it has not been submitted anywhere for any award. Where other sources of information have been used, they have been duly acknowledged. Signature: ………………………………………. Date: ……………………………………………. 2 | P a g e Abstract This thesis features two case studies exploring the George W. Bush Administration’s (2001 – 2009) efforts to promote democracy in the Arab world, following military occupation in Iraq, and through ‘democracy support’ or ‘democracy assistance’ in Lebanon. While reviewing well rehearsed arguments that emphasise the inappropriateness of the methods employed to promote Western liberal democracy in Middle East countries and the difficulties in the way of democracy being fostered by foreign powers, it focuses on two factors that also contributed to derailing the U.S.’s plans to introduce ‘Western style’ liberal democracy to Iraq and Lebanon. -

Iraq's Surprise: the Persistence of Democracy. by Yaroslav Trofimov *
Iraq's Surprise: The Persistence of Democracy. By Yaroslav Trofimov * In the years since the U.S. invasion of Iraq in 2003, American promises of turning the country into a model democracy, spreading freedom across the Middle East, have often seemed like cruel mockery. By the time the U.S. withdrew in 2011, Iraq had been ravaged by bloody insurgencies and sectarian massacres that killed hundreds of thousands of Iraqis and more than 4,500 American troops. In 2014, Iraq almost collapsed in the face of a blitzkrieg by Islamic State, as the extremist group reached the outskirts of Baghdad. There weren’t many takers in the region for the Iraqi model. Today Iraq’s prospects are looking brighter. A resurgent central government has defeated Islamic State, thanks in part to renewed American military involvement, and has taken back lands lost to the country’s Kurdistan autonomous region since 2003. And Iraq’s improbable political experiment has endured. In an increasingly repressive and authoritarian part of the world, this nation of 40 million people stands apart as a rare—though still deeply flawed—democracy. Iraq’s elected leaders insist that, despite their country’s many travails, it still has something to teach the rest of the Middle East. “I hope others in the region will see a lot of hope and positive tendencies in our democracy,” Iraqi Prime Minister Haider al-Abadi said in a recent interview in his palace in Baghdad’s Green Zone. He sees the country’s multiethnic, multi- confessional makeup not as a fatal weakness but as a source of pride. -

Yeshiva of New Haven Edgewood Elm Housing
YESHIVA OF NEW HAVEN ·- EDGEWOOD ELM HOUSING Thirty-'Fifth cA"nniversary (jathering in honor of HONORABLE MARTIN M. LOONEY CONNECTICUT STATE SENATE MAJORITY LEADER Yale Peabody Museum of Natural History N ew Haven, Connecticut 29 Sivan 5772 j une 19, 2012 /\.~ ~'~' :>j>)l·~ ~ ,.$ 7·~. ODD _, ooo ~e. f, DOD .S DOD f. DOD J DOD ______________ .r DOD ~ ~ DOD DOD ~ ------------------------------------ DOD Program Greeting .... ............... ....................Rabbi Mordechai E. Feuerstein Spiritual Leader, Suburban Torah Center - Livingston, New Jersey Address ...........................................Robert C. 'Bud' McFarlane Chairman and CEO, McFarlane Associates, Inc. National Security Advisor to President Ronald Reagan Civic Achievement Award ........................ Honorable Martin M. Looney Connecticut State Senate Majority Leader Remarks ............. ............................... ....... .Clifford D. May President, Foundation for Defense of Democracies Presentation ....... .. ................................. .. Rabbi Daniel Greer Founder and President Edgewood Elm Housing & Yeshiva of New Haven Salutation ......................................Honorable John DeStefano, Jr. Mayor, City of New Haven Appreciation ............................................Rabbi Aviad S. Hack Joumal Chairman The Chairman of the Program this evening is Honorable John A. Keyes, Judge, New Haven Probate Court /\.~ ~'~' :>j>l>·~ ~ ..$' l·u ODD -!' ooo ~e DOD t 6 DOD ___________________________________________________________________ ? BBBDOD 4 The -
Supplemental Statement
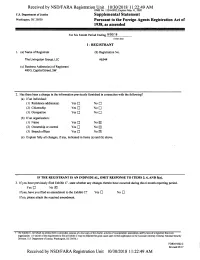
Received by NSD/FARA Registration Unit 10/30/2018 11:22:49 AM OMB No. 1124-0002; Expires May 31,2020 u.s. Department of Justice Supplemental Statement Washington, dc 20530 Pursuant to the Foreign Agents Registration Act of 1938, as amended For Six Month Period Ending 9/30/18...... (Insert date) I - REGISTRANT 1, (a) Name of Registrant (b) Registration No. The Livingston Group, LLC #6344 (c) Business Address(es) of Registrant 499 S. Capitol Street, SW 2. Has there been a change in the information previously furnished in connection with the following? (a) If an individual: (1) Residence address(es) Yes □ No □ (2) Citizenship Yes □ No □ (3) Occupation Yes □ No Q (b) If an organization: (1) Name Yes □ No H (2) Ownership or control Yes □ No 0 (3) Branch offices Yes □ No 0 (c) Explain fully all changes, if any, indicated in Items (a) and (b) above. IF THE REGISTRANT IS AN INDIVIDUAL, OMIT RESPONSE TO ITEMS 3,4, AND 5(a). 3. If you have previously filed Exhibit C*1, state whether any changes therein have occurred during this 6 month reporting period. Yes □ No 0 If yes, have you filed an amendment to the Exhibit C? Yes □ No □ If no, please attach the required amendment. 1 'Hie Exhibit C, for which no printed form is provided, consists of a true copy of the charter, articles of incorporation, association, and by laws of a registrant that is an organization. (A waiver of the requirement to file an Exhibit C may be obtained for good cause upon written application to the Assistant Attorney General, National Security Division, U.S. -

How America Went Haywire
Have Smartphones Why Women Bully Destroyed a Each Other at Work Generation? p. 58 BY OLGA KHAZAN Conspiracy Theories. Fake News. Magical Thinking. How America Went Haywire By Kurt Andersen The Rise of the Violent Left Jane Austen Is Everything The Whitest Music Ever John le Carré Goes SEPTEMBER 2017 Back Into the Cold THEATLANTIC.COM 0917_Cover [Print].indd 1 7/19/2017 1:57:09 PM TerTeTere msm appppply.ly Viistsits ameierier cancaanexpexpresre scs.cs.s com/om busbubusinesspsplatl inuummt to learnmn moreorer . Hogarth &Ogilvy Hogarth 212.237.7000 CODE: FILE: DESCRIPTION: 29A-008875-25C-PBC-17-238F.indd PBC-17-238F TAKE A BREAK BEFORE TAKING ONTHEWORLD ABREAKBEFORETAKING TAKE PUB/POST: The Atlantic -9/17issue(Due TheAtlantic SAP #: #: WORKORDER PRODUCTION: AP.AP PBC.17020.K.011 AP.AP al_stacked_l_18in_wide_cmyk.psd Art: D.Hanson AP17006A_003C_EarlyCheckIn_SWOP3.tif 008875 BLEED: TRIM: LIVE: (CMYK; 3881 ppi; Up toDate) (CMYK; 3881ppi;Up 15.25” x10” 15.75”x10.5” 16”x10.75” (CMYK; 908 ppi; Up toDate), (CMYK; 908ppi;Up 008875-13A-TAKE_A_BREAK_CMYK-TintRev.eps 008875-13A-TAKE_A_BREAK_CMYK-TintRev.eps (Up toDate), (Up AP- American Express-RegMark-4C.ai AP- AmericanExpress-RegMark-4C.ai (Up toDate), (Up sbs_fr_chg_plat_met- at americanexpress.com/exploreplatinum at PlatinumMembership Business of theworld Explore FineHotelsandResorts. hand-picked 975 atover head your andclear early Arrive TerTeTere msm appppply.ly Viistsits ameierier cancaanexpexpresre scs.cs.s com/om busbubusinesspsplatl inuummt to learnmn moreorer . Hogarth &Ogilvy Hogarth 212.237.7000 -

Foreign Military Weapons and Equipment
DEPARTMENT OF THE ARMY PAMPHLET NO. 30-7-4 FOREIGN MILITARY WEAPONS AND EQUIPMENT Vol. III INFANTRY WEAPONS DEPARTMENT OF THE ARMY DT WASHINGTON 25, D. C. FOREWORD The object in publishing the essential recognition features of weapons of Austrian, German, and Japanese origin as advance sections of DA Pam 30-7-4 is to present technical information on these weapons as they are used or held in significant quantities by the Soviet satellite nations (see DA Pam 30-7-2). The publication is in looseleaf form to facilitate inclusion of additional material when the remaining sections of DA Pam 30-7-4 are published. Items are presented according to country of manufacture. It should be noted that, although they may be in use or held in reserve by a satellite country, they may be regarded as obsolete in the country of manufacture. DA Pam 30-7-4 PAMPHLET DEPARTMENT OF THE ARMY No. 30-7-4 WASHINGTON 25, D. C., 24 November 1954 FOREIGN MILITARY WEAPONS AND EQUIPMENT VOL. III INFANTRY WEAPONS SECTION IV. OTHER COUNTRIES AUSTRIA: Page Glossary of Austrian terms--------------------------------------------------------- 4 A. Pistols: 9-mm Pistol M12 (Steyr) ---------------------------------------------------- 5 B. Submachine Guns: 9-mm Submachine Gun MP 34 (Steyr-Solothurn) ------------------------------- .7 C. Rifles and Carbines: 8-mm M1895 Mannlicher Rifle- - ____________________________________- - - - - - -- 9 GERMANY: Glossary of German terms___________________________________---------------------------------------------------------11 A. Pistols: 9-mm Walther Pistol M1938-- _______________________-- - --- -- -- 13 9-mm Luger Pistol M1908--------------------------------------------------15 7.65-mm Sauer Pistol M1938---------------------------------_ 17 7.65-mm Walther Pistol Model PP and PPK ---------------------------------- 19 7.63-mm Mauser Pistol M1932----------------------------------------------21 7.65-mm Mauser Pistol Model HSc ------------------------------------------ 23 B. -

Fitzgerald Subpoenas and Server Crashes
FITZGERALD SUBPOENAS AND SERVER CRASHES CREW reports something that I demonstrated clearly some time ago: materials subpoenaed by Patrick Fitzgerald in his CIA Leak Investigation were lost in the White House’s seemingly intractable problems with email. (h/t Laura Rozen) But CREW’s got new documents proving the case, including this Microsoft Post-Mortem documenting its efforts to conduct an email search in February 2004, in what is almost certainly the series of subpoenas Fitz issued shortly after taking over the investigation (the date referred to in the post-mortem–January 22–is the date Fitz issued his subpoenas). Here’s a summary of the key subpoenaed material: February 6 was Abu Gonzales’ deadline to turn third batch of documents over to DOJ, including "records on administration contacts with more than two dozen journalists and news media outlets." The journalists, with my best take of what the investigators were looking for in brackets, include: Robert Novak, "Crossfire," "Capital Gang" and the Chicago Sun-Times [duh!] Knut Royce and Timothy M. Phelps, Newsday [source for their confirmation of Plame’s status] Walter Pincus [Libby conversation, July 12 Plame conversation], Richard Leiby {background for profile], Mike Allen [identity of SAO], Dana Priest [identity of SAO] and Glenn Kessler [conversation with Libby], The Washington Post Matthew Cooper [duh!], John Dickerson [possible additional source, Ari’s "walk-up" conversation], Massimo Calabresi [possible additional source, Wilson interview], Michael Duffy [earlier article] and James Carney [earlier article], Time magazine Evan Thomas, Newsweek [why Evan Thomas? was he the "they’re coming after you" journalist?] Andrea Mitchell [see Tom Maguire], "Meet the Press," NBC Chris Matthews ["your wife is fair game"], "Hardball," MSNBC Tim Russert [Libby complaint], Campbell Brown [why Campbell Brown?], NBC Nicholas D. -

Entire Issue (PDF 2MB)
E PL UR UM IB N U U S Congressional Record United States th of America PROCEEDINGS AND DEBATES OF THE 111 CONGRESS, FIRST SESSION Vol. 155 WASHINGTON, MONDAY, NOVEMBER 2, 2009 No. 161 House of Representatives The House met at 12:30 p.m. and was they should be fearful. And I believe who wrote a 1,990-page health care bill called to order by the Speaker pro tem- that the greatest fear that we all which is very difficult to read. pore (Ms. EDWARDS of Maryland). should have to our freedom comes from Page 1183—section 1904 provides $750 million in Federal funding for a new f this room, this very room, and what may happen later this week in terms of entitlement program to offer, quote, DESIGNATION OF SPEAKER PRO a tax increase bill masquerading as a knowledge of realistic expectations of TEMPORE health care bill. I believe we have more age-appropriate child behaviors and The SPEAKER pro tempore laid be- to fear from the potential of that bill skills for parents to interact with their fore the House the following commu- passing than we do from any terrorist child. nication from the Speaker: right now in any country. Page 1255—sections 2231–2235 makes In order to help explain some of why veterinary students eligible for up to WASHINGTON, DC, $283 million in Federal scholarship and November 2, 2009. we should be fearful, the Republican student loan forgiveness funding. I hereby appoint the Honorable DONNA F. Conference has gone through Speaker Page 1432—section 2531 provides in- EDWARDS to act as Speaker pro tempore on PELOSI’s bill—tax bill masquerading as this day. -

Megacity Security Conference Speaker and Participant Bios
Megacity Security Conference Monday, November 22, 2015 – Tuesday, November 23, 2015 Speaker and Participant Bios Mumbai, India Gov. John M. Hunstman, Jr. Former Governor of Utah; Former Ambassador to China; Chairman, Atlantic Council Governor Jon M. Huntsman, Jr. is Chairman of the Atlantic Council Board of Directors. He began his career in public service as a Staff Assistant to President Ronald Reagan. He has served each of the four US presidents since then in critical roles around the world, including as Ambassador to Singapore, Deputy Assistant Secretary of Commerce for Asia, US Trade Ambassador, and most recently, US Ambassador to China. In all three Senate confirmations, he received unanimous votes. Twice elected Governor of Utah, Governor Huntsman brought about strong economic reforms, tripled the state's rainy day fund, and helped bring unemployment rates to historic lows. During his tenure, Utah was named the best managed state in America. Recognized by others for his service, Governor Huntsman was elected as Chairman of the Western Governors Association, serving nineteen states throughout the region. He currently serves on the boards of Ford Motor Company, Caterpillar Corporation, Chevron Corporation, Huntsman Corporation, the US Naval Academy Foundation, and the University of Pennsylvania. In addition, he serves as a Distinguished Fellow at the Brookings Institute, a Trustee of the Carnegie Endowment for International Peace, a Trustee of the Reagan Presidential Foundation, and Chairman of the Huntsman Cancer Foundation. Governor Huntsman has served as a Visiting Fellow at Harvard University’s John F. Kennedy School of Government as well as a Distinguished Lecturer at Duke University's Sanford School of Public Policy. -

Sectarianism in the Middle East
Sectarianism in the Middle East Implications for the United States Heather M. Robinson, Ben Connable, David E. Thaler, Ali G. Scotten C O R P O R A T I O N For more information on this publication, visit www.rand.org/t/RR1681 Library of Congress Cataloging-in-Publication Data is available for this publication. ISBN: 978-0-8330-9699-9 Published by the RAND Corporation, Santa Monica, Calif. © Copyright 2018 RAND Corporation R® is a registered trademark. Cover: Sunni and Shi’ite Muslims attend prayers during Eid al-Fitr as they mark the end of the fasting month of Ramadan, at the site of a suicide car bomb attack over the weekend at the shopping area of Karrada, in Baghdad, Iraq, July 6, 2016. REUTERS/Thaier Al-Sudani Limited Print and Electronic Distribution Rights This document and trademark(s) contained herein are protected by law. This representation of RAND intellectual property is provided for noncommercial use only. Unauthorized posting of this publication online is prohibited. Permission is given to duplicate this document for personal use only, as long as it is unaltered and complete. Permission is required from RAND to reproduce, or reuse in another form, any of its research documents for commercial use. For information on reprint and linking permissions, please visit www.rand.org/pubs/permissions. The RAND Corporation is a research organization that develops solutions to public policy challenges to help make communities throughout the world safer and more secure, healthier and more prosperous. RAND is nonprofit, nonpartisan, and committed to the public interest. RAND’s publications do not necessarily reflect the opinions of its research clients and sponsors. -

Owen Submachine Gun.Nomination
Nomination of OWEN SUBMACHINE GUN for an Engineering Heritage National Marker Owen Gun Mark 1/42 - skeleton stock, cooling fins on barrel source gunshows.com.nz Owen Gun Mark 1/43 - wooden stock, camouflage finish by Doug Boleyn Engineering Heritage Sydney January 2017 Table of Contents Page 1. Introduction 2 2. Nomination Letter 4 3. Nomination Support Information Basic Data 5 4. Basic History 8 5. Engineering Heritage Assessment 11 6. Interpretation Plan 14 7. References & Acknowledgements 15 Appendices 1. Statement of Support for Engineering Heritage Recognition 16 2. History Time Line of the Owen Submachine Gun 17 3. Photos of the Owen Submachine Gun and other submachine guns used 28 in World War 2 4. Drawings of the Owen Submachine Gun 34 5. Statistics of the various models of the Owen Gun and Comparison Table 35 6. Biographies of Companies and People Associated with the Owen Gun 39 7. Glossary Terminology and Imperial Unit Conversions 44 8. Author's Assessment of Engineering Heritage Significance Check List 45 Rev 05 01 17 Page 1 1. Introduction. The Owen submachine gun [SMG] (1) that bears its designer's name was the only weapon of World War 2 used by Australian troops that was wholly designed and manufactured in Australia. Conceptually designed by Evelyn Owen, a committed young inventor, the concept was further developed to production stage by Gerard Wardell Chief Engineer Lysaght's Newcastle Works Pty Limited - Port Kembla Branch (2) [Lysaghts] with the assistance of Evelyn Owen ( and Fred Kunzler a Lysaght employee who had been a gunsmith in his native Switzerland.