Fundamental Limits on Key Rates in Device-Independent Quantum Key Distribution
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sudden Death and Revival of Gaussian Einstein–Podolsky–Rosen Steering
www.nature.com/npjqi ARTICLE OPEN Sudden death and revival of Gaussian Einstein–Podolsky–Rosen steering in noisy channels ✉ Xiaowei Deng1,2,4, Yang Liu1,2,4, Meihong Wang2,3, Xiaolong Su 2,3 and Kunchi Peng2,3 Einstein–Podolsky–Rosen (EPR) steering is a useful resource for secure quantum information tasks. It is crucial to investigate the effect of inevitable loss and noise in quantum channels on EPR steering. We analyze and experimentally demonstrate the influence of purity of quantum states and excess noise on Gaussian EPR steering by distributing a two-mode squeezed state through lossy and noisy channels, respectively. We show that the impurity of state never leads to sudden death of Gaussian EPR steering, but the noise in quantum channel can. Then we revive the disappeared Gaussian EPR steering by establishing a correlated noisy channel. Different from entanglement, the sudden death and revival of Gaussian EPR steering are directional. Our result confirms that EPR steering criteria proposed by Reid and I. Kogias et al. are equivalent in our case. The presented results pave way for asymmetric quantum information processing exploiting Gaussian EPR steering in noisy environment. npj Quantum Information (2021) 7:65 ; https://doi.org/10.1038/s41534-021-00399-x INTRODUCTION teleportation30–32, securing quantum networking tasks33, and 1234567890():,; 34,35 Nonlocality, which challenges our comprehension and intuition subchannel discrimination . about the nature, is a key and distinctive feature of quantum Besides two-mode EPR steering, the multipartite EPR steering world. Three different types of nonlocal correlations: Bell has also been widely investigated since it has potential application nonlocality1, Einstein–Podolsky–Rosen (EPR) steering2–6, and in quantum network. -
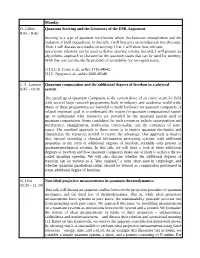
Monday O. Gühne 9:00 – 9:45 Quantum Steering and the Geometry of the EPR-Argument Steering Is a Type of Quantum Correlations
Monday O. Gühne Quantum Steering and the Geometry of the EPR-Argument 9:00 – 9:45 Steering is a type of quantum correlations which lies between entanglement and the violation of Bell inequalities. In this talk, I will first give an introduction into the topic. Then, I will discuss two results on steering: First, I will show how entropic uncertainty relations can be used to derive steering criteria. Second, I will present an algorithmic approach to characterize the quantum states that can be used for steering. With this, one can decide the problem of steerability for two-qubit states. [1] A.C.S. Costa et al., arXiv:1710.04541. [2] C. Nguyen et al., arXiv:1808.09349. J.-Å. Larsson Quantum computation and the additional degrees of freedom in a physical 9:45 – 10:30 system The speed-up of Quantum Computers is the current drive of an entire scientific field with several large research programmes both in industry and academia world-wide. Many of these programmes are intended to build hardware for quantum computers. A related important goal is to understand the reason for quantum computational speed- up; to understand what resources are provided by the quantum system used in quantum computation. Some candidates for such resources include superposition and interference, entanglement, nonlocality, contextuality, and the continuity of state- space. The standard approach to these issues is to restrict quantum mechanics and characterize the resources needed to restore the advantage. Our approach is dual to that, instead extending a classical information processing systems with additional properties in the form of additional degrees of freedom, normally only present in quantum-mechanical systems. -

Approximating Ground States by Neural Network Quantum States
Article Approximating Ground States by Neural Network Quantum States Ying Yang 1,2, Chengyang Zhang 1 and Huaixin Cao 1,* 1 School of Mathematics and Information Science, Shaanxi Normal University, Xi’an 710119, China; [email protected] (Y.Y.); [email protected] (C.Z.) 2 School of Mathematics and Information Technology, Yuncheng University, Yuncheng 044000, China * Correspondence: [email protected] Received: 16 December 2018; Accepted: 16 January 2019; Published: 17 January 2019 Abstract: Motivated by the Carleo’s work (Science, 2017, 355: 602), we focus on finding the neural network quantum statesapproximation of the unknown ground state of a given Hamiltonian H in terms of the best relative error and explore the influences of sum, tensor product, local unitary of Hamiltonians on the best relative error. Besides, we illustrate our method with some examples. Keywords: approximation; ground state; neural network quantum state 1. Introduction The quantum many-body problem is a general name for a vast category of physical problems pertaining to the properties of microscopic systems made of a large number of interacting particles. In such a quantum system, the repeated interactions between particles create quantum correlations [1–3], quantum entanglement [4–6], Bell nonlocality [7–9], Einstein-Poldolsky-Rosen (EPR) steering [10–12]. As a consequence, the wave function of the system is a complicated object holding a large amount of information, which usually makes exact or analytical calculations impractical or even impossible. Thus, many-body theoretical physics most often relies on a set of approximations specific to the problem at hand, and ranks among the most computationally intensive fields of science. -

A Radix-4 Chrestenson Gate for Optical Quantum Computation
A Radix-4 Chrestenson Gate for Optical Quantum Computation Kaitlin N. Smith, Tim P. LaFave Jr., Duncan L. MacFarlane, and Mitchell A. Thornton Quantum Informatics Research Group Southern Methodist University Dallas, TX, USA fknsmith, tlafave, dmacfarlane, mitchg @smu.edu Abstract—A recently developed four-port directional coupler is described in Section III followed by the realization of the used in optical signal processing applications is shown to be coupler with optical elements including its fabrication and equivalent to a radix-4 Chrestenson operator, or gate, in quantum characterization in Section IV. Demonstration of the four-port information processing (QIP) applications. The radix-4 qudit is implemented as a location-encoded photon incident on one of coupler as a radix-4 Chrestenson gate is presented in Section V the four ports of the coupler. The quantum informatics transfer and a summary with conclusions is found in Section VI. matrix is derived for the device based upon the conservation of energy equations when the coupler is employed in a classical II. QUANTUM THEORY BACKGROUND sense in an optical communications environment. The resulting transfer matrix is the radix-4 Chrestenson transform. This result A. The Qubit vs. Qudit indicates that a new practical device is available for use in the The quantum bit, or qubit, is the standard unit of information implementation of radix-4 QIP applications or in the construction for radix-2, or base-2, quantum computing. The qubit models of a radix-4 quantum computer. Index Terms—quantum information processing; quantum pho- information as a linear combination of two orthonormal basis tonics; qudit; states such as the states j0i and j1i. -

Electrical Characterisation of Ion Implantation Induced Defects in Silicon Based Devices for Quantum Applications
Electrical Characterisation of Ion Implantation Induced Defects in Silicon Based Devices for Quantum Applications Aochen Duan Supervised by Professor Jeffrey C. McCallum and Doctor Brett C. Johnson School of Physics The University of Melbourne Australia 1 Abstract Quantum devices that leverage the manufacturing techniques of silicon-based classical computers make them strong candidates for future quantum computers. However, the demands on device quality are much more stringent given that quantum states can de- cohere via interactions with their environment. In this thesis, a detailed investigation of ion implantation induced defects generated during device fabrication in a regime relevant to quantum device fabrication is presented. We identify different types of defects in Si using various advanced electrical characterisation techniques. The first experimental technique, electrical conductance, was used for the investigation of the interface state density of both n- and p-type MOS capacitors after ion implantation of various species followed by a rapid thermal anneal. As precise atomic placement is critical for building Si based quantum computers, implantation through the oxide in fully fabricated devices is necessary for some applications. However, implanting through the oxide might affect the quality of the Si/SiO2 interface which is in close proximity to the region in which manipulation of the qubits take place. Implanting ions in MOS capacitors through the oxide is a model for the damage that might be observed in other fabricated devices. It will be shown that the interface state density only changes significantly after a fluence of 1013 ions/cm2 except for Bi in p-type silicon, where significant increase in interface state density was observed after a fluence of 1011 Bi/cm2. -

Technology-Dependent Quantum Logic Synthesis and Compilation
Southern Methodist University SMU Scholar Electrical Engineering Theses and Dissertations Electrical Engineering Fall 12-21-2019 Technology-dependent Quantum Logic Synthesis and Compilation Kaitlin Smith Southern Methodist University, [email protected] Follow this and additional works at: https://scholar.smu.edu/engineering_electrical_etds Part of the Other Electrical and Computer Engineering Commons Recommended Citation Smith, Kaitlin, "Technology-dependent Quantum Logic Synthesis and Compilation" (2019). Electrical Engineering Theses and Dissertations. 30. https://scholar.smu.edu/engineering_electrical_etds/30 This Dissertation is brought to you for free and open access by the Electrical Engineering at SMU Scholar. It has been accepted for inclusion in Electrical Engineering Theses and Dissertations by an authorized administrator of SMU Scholar. For more information, please visit http://digitalrepository.smu.edu. TECHNOLOGY-DEPENDENT QUANTUM LOGIC SYNTHESIS AND COMPILATION Approved by: Dr. Mitchell Thornton - Committee Chairman Dr. Jennifer Dworak Dr. Gary Evans Dr. Duncan MacFarlane Dr. Theodore Manikas Dr. Ronald Rohrer TECHNOLOGY-DEPENDENT QUANTUM LOGIC SYNTHESIS AND COMPILATION A Dissertation Presented to the Graduate Faculty of the Lyle School of Engineering Southern Methodist University in Partial Fulfillment of the Requirements for the degree of Doctor of Philosophy with a Major in Electrical Engineering by Kaitlin N. Smith (B.S., EE, Southern Methodist University, 2014) (B.S., Mathematics, Southern Methodist University, 2014) (M.S., EE, Southern Methodist University, 2015) December 21, 2019 ACKNOWLEDGMENTS I am grateful for the many people in my life who made the completion of this dissertation possible. First, I would like to thank Dr. Mitch Thornton for introducing me to the field of quantum computation and for directing me during my graduate studies. -

Arxiv:Quant-Ph/0512071 V1 9 Dec 2005 Contents I.Ipoeet Ntekmprotocol KLM the on Improvements III
Linear optical quantum computing Pieter Kok,1,2, ∗ W.J. Munro,2 Kae Nemoto,3 T.C. Ralph,4 Jonathan P. Dowling,5,6 and G.J. Milburn4 1Department of Materials, Oxford University, Oxford OX1 3PH, UK 2Hewlett-Packard Laboratories, Filton Road Stoke Gifford, Bristol BS34 8QZ, UK 3National Institute of Informatics, 2-1-2 Hitotsubashi, Chiyoda-ku, Tokyo 101-8430, Japan 4Centre for Quantum Computer Technology, University of Queensland, St. Lucia, Queensland 4072, Australia 5Hearne Institute for Theoretical Physics, Dept. of Physics and Astronomy, LSU, Baton Rouge, Louisiana 6Institute for Quantum Studies, Department of Physics, Texas A&M University (Dated: December 9, 2005) Linear optics with photo-detection is a prominent candidate for practical quantum computing. The protocol by Knill, Laflamme and Milburn [Nature 409, 46 (2001)] explicitly demonstrates that efficient scalable quantum computing with single photons, linear optical elements, and projec- tive measurements is possible. Subsequently, several improvements on this protocol have started to bridge the gap between theoretical scalability and practical implementation. We review the original proposal and its improvements, and we give a few examples of experimental two-qubit gates. We discuss the use of realistic components, the errors they induce in the computation, and how they can be corrected. PACS numbers: 03.67.Hk, 03.65.Ta, 03.65.Ud Contents References 36 I. Quantum computing with light 1 A. Linear quantum optics 2 B. N-port interferometers and optical circuits 3 C. Qubits in linear optics 4 I. QUANTUM COMPUTING WITH LIGHT D. Early optical quantum computers and nonlinearities 5 Quantum computing has attracted much attention over II. -

Arxiv:1903.12615V1
Encoding an oscillator into many oscillators Kyungjoo Noh,1, 2, ∗ S. M. Girvin,1, 2 and Liang Jiang1, 2, y 1Departments of Applied Physics and Physics, Yale University, New Haven, Connecticut 06520, USA 2Yale Quantum Institute, Yale University, New Haven, Connecticut 06520, USA Gaussian errors such as excitation losses, thermal noise and additive Gaussian noise errors are key challenges in realizing large-scale fault-tolerant continuous-variable (CV) quantum information processing and therefore bosonic quantum error correction (QEC) is essential. In many bosonic QEC schemes proposed so far, a finite dimensional discrete-variable (DV) quantum system is encoded into noisy CV systems. In this case, the bosonic nature of the physical CV systems is lost at the error-corrected logical level. On the other hand, there are several proposals for encoding an infinite dimensional CV system into noisy CV systems. However, these CV-into-CV encoding schemes are in the class of Gaussian quantum error correction and therefore cannot correct practically relevant Gaussian errors due to established no-go theorems which state that Gaussian errors cannot be corrected by Gaussian QEC schemes. Here, we work around these no-go results and show that it is possible to correct Gaussian errors using GKP states as non-Gaussian resources. In particular, we propose a family of non-Gaussian quantum error-correcting codes, GKP-repetition codes, and demonstrate that they can correct additive Gaussian noise errors. In addition, we generalize our GKP-repetition codes to an even broader class of non-Gaussian QEC codes, namely, GKP-stabilizer codes and show that there exists a highly hardware-efficient GKP-stabilizer code, the two-mode GKP-squeezed-repetition code, that can quadratically suppress additive Gaussian noise errors in both the position and momentum quadratures. -

G53NSC and G54NSC Non Standard Computation Research Presentations
G53NSC and G54NSC Non Standard Computation Research Presentations March the 23rd and 30th, 2010 Tuesday the 23rd of March, 2010 11:00 - James Barratt • Quantum error correction 11:30 - Adam Christopher Dunkley and Domanic Nathan Curtis Smith- • Jones One-Way quantum computation and the Measurement calculus 12:00 - Jack Ewing and Dean Bowler • Physical realisations of quantum computers Tuesday the 30th of March, 2010 11:00 - Jiri Kremser and Ondrej Bozek Quantum cellular automaton • 11:30 - Andrew Paul Sharkey and Richard Stokes Entropy and Infor- • mation 12:00 - Daniel Nicholas Kiss Quantum cryptography • 1 QUANTUM ERROR CORRECTION JAMES BARRATT Abstract. Quantum error correction is currently considered to be an extremely impor- tant area of quantum computing as any physically realisable quantum computer will need to contend with the issues of decoherence and other quantum noise. A number of tech- niques have been developed that provide some protection against these problems, which will be discussed. 1. Introduction It has been realised that the quantum mechanical behaviour of matter at the atomic and subatomic scale may be used to speed up certain computations. This is mainly due to the fact that according to the laws of quantum mechanics particles can exist in a superposition of classical states. A single bit of information can be modelled in a number of ways by particles at this scale. This leads to the notion of a qubit (quantum bit), which is the quantum analogue of a classical bit, that can exist in the states 0, 1 or a superposition of the two. A number of quantum algorithms have been invented that provide considerable improvement on their best known classical counterparts, providing the impetus to build a quantum computer. -

An Introduction to Blind Quantum Computing and Related Protocols
www.nature.com/npjqi REVIEW ARTICLE OPEN Private quantum computation: an introduction to blind quantum computing and related protocols Joseph F. Fitzsimons1,2 Quantum technologies hold the promise of not only faster algorithmic processing of data, via quantum computation, but also of more secure communications, in the form of quantum cryptography. In recent years, a number of protocols have emerged which seek to marry these concepts for the purpose of securing computation rather than communication. These protocols address the task of securely delegating quantum computation to an untrusted device while maintaining the privacy, and in some instances the integrity, of the computation. We present a review of the progress to date in this emerging area. npj Quantum Information (2017) 3:23 ; doi:10.1038/s41534-017-0025-3 INTRODUCTION from the server executing them, and to ensure the correctness of For almost as long as programmable computers have existed, the result. there has been a strong motivation for users to run calculations on In recent years, a number of protocols have emerged which hardware that they do not personally control. Initially, this was due seek to tackle the privacy issues raised by delegated quantum to the high cost of such devices coupled with the need for computation. Going under the broad heading of blind quantum specialised facilities to house them. Universities, government computation (BQC), these provide a way for a client to execute a agencies and large corporations housed computers in central quantum computation using one or more remote quantum locations where they ran jobs for their users in batches. -

Quantum Technology: Advances and Trends
American Journal of Engineering and Applied Sciences Review Quantum Technology: Advances and Trends 1Lidong Wang and 2Cheryl Ann Alexander 1Institute for Systems Engineering Research, Mississippi State University, Vicksburg, Mississippi, USA 2Institute for IT innovation and Smart Health, Vicksburg, Mississippi, USA Article history Abstract: Quantum science and quantum technology have become Received: 30-03-2020 significant areas that have the potential to bring up revolutions in various Revised: 23-04-2020 branches or applications including aeronautics and astronautics, military Accepted: 13-05-2020 and defense, meteorology, brain science, healthcare, advanced manufacturing, cybersecurity, artificial intelligence, etc. In this study, we Corresponding Author: Cheryl Ann Alexander present the advances and trends of quantum technology. Specifically, the Institute for IT innovation and advances and trends cover quantum computers and Quantum Processing Smart Health, Vicksburg, Units (QPUs), quantum computation and quantum machine learning, Mississippi, USA quantum network, Quantum Key Distribution (QKD), quantum Email: [email protected] teleportation and quantum satellites, quantum measurement and quantum sensing, and post-quantum blockchain and quantum blockchain. Some challenges are also introduced. Keywords: Quantum Computer, Quantum Machine Learning, Quantum Network, Quantum Key Distribution, Quantum Teleportation, Quantum Satellite, Quantum Blockchain Introduction information and the computation that is executed throughout a transaction (Humble, 2018). The Tokyo QKD metropolitan area network was There have been advances in developing quantum established in Japan in 2015 through intercontinental equipment, which has been indicated by the number of cooperation. A 650 km QKD network was established successful QKD demonstrations. However, many problems between Washington and Ohio in the USA in 2016; a still need to be fixed though achievements of QKD have plan of a 10000 km QKD backbone network was been showcased. -

High Fidelity Readout of Trapped Ion Qubits
High Fidelity Readout of Trapped Ion Qubits A thesis submitted for the degree of Doctor of Philosophy Alice Heather Burrell Trinity Term Exeter College 2010 Oxford ii Abstract High Fidelity Readout of Trapped Ion Qubits A thesis submitted for the degree of Doctor of Philosophy, Trinity Term 2010 Alice Heather Burrell Exeter College, Oxford This thesis describes experimental demonstrations of high-fidelity readout of trapped ion quantum bits (“qubits”) for quantum information processing. We present direct single-shot measurement of an “optical” qubit stored in a single 40Ca+ ion by the process of resonance fluorescence with a fidelity of 99.991(1)% (sur- passing the level necessary for fault-tolerant quantum computation). A time-resolved maximum likelihood method is used to discriminate efficiently between the two qubit states based on photon-counting information, even in the presence of qubit decay from one state to the other. It also screens out errors due to cosmic ray events in the detec- tor, a phenomenon investigated in this work. An adaptive method allows the 99.99% level to be reached in 145 µs average detection time. The readout fidelity is asymmetric: 99.9998% is possible for the “bright” qubit state, while retaining 99.98% for the “dark” state. This asymmetry could be exploited in quantum error correction (by encoding the “no-error” syndrome of the ancilla qubits in the “bright” state), as could the likelihood values computed (which quantify confidence in the measurement outcome). We then extend the work to parallel readout of a four-ion string using a CCD camera and achieve the same 99.99% net fidelity, limited by qubit decay in the 400 µs exposure time.