Tcpware for Openvms User's Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
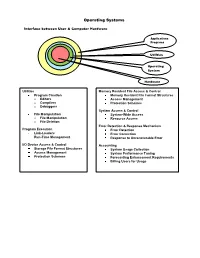
Operating Systems
Operating Systems Interface between User & Computer Hardware Applications Programs Utilities Operating System Hardware Utilities Memory Resident File Access & Control Program Creation Memory Resident File Format Structures o Editors Access Management o Compilers Protection Schemes o Debuggers System Access & Control File Manipulation System-Wide Access o File Manipulation Resource Access o File Deletion Error Detection & Response Mechanism Program Execution Error Detection Link-Loaders Error Correction Run-Time Management Response to Unrecoverable Error I/O Device Access & Control Accounting Storage File Format Structures System Usage Collection Access Management System Performance Tuning Protection Schemes Forecasting Enhancement Requirements Billing Users for Usage Resource Manager O/S KernelKernel I/O Controller Printers, Keyboards, I/O Controller Monitors, Portions of Cameras, the O/S Etc. currently in use Computer Main System Memory Portions of Various I/O Application Devices Programs Currently in use Operating System Data Application Programs I/O Controller Storage Processor Processor Data Processor Processor Operation Allocation of Main Memory is made jointly by both the O/S and Memory Management Hardware O/S controls access to I/O devices by Application Programs O/S controls access to and use of files O/S controls access to and use of the processors, i.e., how much time can be allocated to the execution of a particular Application Program Classification of Operating Systems Interactive O/S Keyboard & Monitor Access to O/S Immediate, -

Integrated Voice Evacuation System Vx-3000 Series
SETTING SOFTWARE INSTRUCTIONS For Authorized Advanced End User INTEGRATED VOICE EVACUATION SYSTEM VX-3000 SERIES Tip In this manual, the VX-3004F/3008F/3016F Voice Evacuation Frames are collectively referred to as "VX-3000F." Thank you for purchasing TOA’s Integrated Voice Evacuation System. Please carefully follow the instructions in this manual to ensure long, trouble-free use of your equipment. TABLE OF CONTENTS 1. SOFTWARE OUTLINE ................................................................................... 3 2. NOTES ON PERFORMING SETTINGS .............................................. 3 2.1. System Requirements .......................................................................................... 3 2.2. Notes .................................................................................................................... 3 3. SOFTWARE SETUP ........................................................................................ 4 3.1. Setting Software Installation ................................................................................. 4 3.2. Uninstallation ....................................................................................................... 6 4. STARTING THE VX-3000 SETTING SOFTWARE ....................... 7 5. SETTING ITEMS ................................................................................................ 8 5.1. Setting Item Button Configuration ........................................................................ 8 5.2. Menu Bar ............................................................................................................. -

Chapter 10 Introduction to Batch Files
Instructor’s Manual Chapter 10 Lecture Notes Introduction to Batch Files Chapter 10 Introduction to Batch Files LEARNING OBJECTIVES 1. Compare and contrast batch and interactive processing. 2. Explain how batch files work. 3. Explain the purpose and function of the REM, ECHO, and PAUSE commands. 4. Explain how to stop or interrupt the batch file process. 5. Explain the function and use of replaceable parameters in batch files. 6. Explain the function of pipes, filters, and redirection in batch files. STUDENT OUTCOMES 1. Use Edit to write batch files. 2. Use COPY CON to write batch files. 3. Write and execute a simple batch file. 4. Write a batch file to load an application program. 5. Use the REM, PAUSE, and ECHO commands in batch files. 6. Terminate a batch file while it is executing. 7. Write batch files using replaceable parameters. 8. Write a batch file using pipes, filters, and redirection. CHAPTER SUMMARY 1. Batch processing means running a series of instructions without interruption. 2. Interactive processing allows the user to interface directly with the computer and update records immediately. 3. Batch files allow a user to put together a string of commands and execute them with one command. 4. Batch files must have the .BAT or .CMD file extension. 5. Windows looks first internally for a command, then for a .COM files extension, then for a .EXE file extension, and finally for a .BAT or .CMD file extension. 6. Edit is a full-screen text editor used to write batch files. 7. A word processor, if it has a means to save files in ASCII, can be used to write batch files. -

Uni Hamburg – Mainframe Summit 2010 Z/OS – the Mainframe Operating System
Uni Hamburg – Mainframe Summit 2010 z/OS – The Mainframe Operating System Appendix 2 – JES and Batchprocessing Redelf Janßen IBM Technical Sales Mainframe Systems [email protected] © Copyright IBM Corporation 2010 Course materials may not be reproduced in whole or in part without the prior written permission of IBM. 4.0.1 Introduction to the new mainframe Chapter 7: Batch processing and the Job Entry Subsystem (JES) © Copyright IBM Corp., 2010. All rights reserved. Introduction to the new mainframe Chapter 7 objectives Be able to: • Give an overview of batch processing and how work is initiated and managed in the system. • Explain how the job entry subsystem (JES) governs the flow of work through a z/OS system. © Copyright IBM Corp., 2010. All rights reserved. 3 Introduction to the new mainframe Key terms in this chapter • batch processing • procedure • execution • purge • initiator • queue • job • spool • job entry subsystem (JES) • symbolic reference • output • workload manager (WLM) © Copyright IBM Corp., 2010. All rights reserved. 4 Introduction to the new mainframe What is batch processing? Much of the work running on z/OS consists of programs called batch jobs. Batch processing is used for programs that can be executed: • With minimal human interaction • At a scheduled time or on an as-needed basis. After a batch job is submitted to the system for execution, there is normally no further human interaction with the job until it is complete. © Copyright IBM Corp., 2010. All rights reserved. 5 Introduction to the new mainframe What is JES? In the z/OS operating system, JES manages the input and output job queues and data. -

Approaches to Optimize Batch Processing on Z/OS
Front cover Approaches to Optimize Batch Processing on z/OS Apply the latest z/OS features Analyze bottlenecks Evaluate critical path Alex Louwe Kooijmans Elsie Ramos Jan van Cappelle Lydia Duijvestijn Tomohiko Kaneki Martin Packer ibm.com/redbooks Redpaper International Technical Support Organization Approaches to Optimize Batch Processing on z/OS October 2012 REDP-4816-00 Note: Before using this information and the product it supports, read the information in “Notices” on page v. First Edition (October 2012) This edition applies to all supported z/OS versions and releases. This document created or updated on October 24, 2012. © Copyright International Business Machines Corporation 2012. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . .v Trademarks . vi Preface . vii The team who wrote this paper . vii Now you can become a published author, too! . viii Comments welcome. viii Stay connected to IBM Redbooks . ix Chapter 1. Getting started . 1 1.1 The initial business problem statement. 2 1.2 How to clarify the problem statement . 3 1.3 Process to formulate a good problem statement . 3 1.4 How to create a good business case . 5 1.5 Analysis methodology . 6 1.5.1 Initialization . 6 1.5.2 Analysis. 6 1.5.3 Implementation . 10 Chapter 2. Analysis steps. 13 2.1 Setting the technical strategy . 14 2.2 Understanding the batch landscape . 15 2.2.1 Identifying where batch runs and the available resources . 15 2.2.2 Job naming conventions . 15 2.2.3 Application level performance analysis. -

HP Decset for Openvms Guide to the Module Management System
HP DECset for OpenVMS Guide to the Module Management System Order Number: AA–P119J–TE July 2005 This guide describes the Module Management System (MMS) and explains how to get started using its basic features. Revision/Update Information: This is a revised manual. Operating System Version: OpenVMS I64 Version 8.2 OpenVMS Alpha Version 7.3–2 or 8.2 OpenVMS VAX Version 7.3 Windowing System Version: DECwindows Motif for OpenVMS I64 Version 1.5 DECwindows Motif for OpenVMS Alpha Version 1.3–1 or 1.5 DECwindows Motif for OpenVMS VAX Version 1.2–6 Software Version: HP DECset Version 12.7 for OpenVMS Hewlett-Packard Company Palo Alto, California © Copyright 2005 Hewlett-Packard Development Company, L.P. Confidential computer software. Valid license from HP required for possession, use or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s standard commercial license. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein. Intel and Itanium are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. Java is a US trademark of Sun Microsystems, Inc. Microsoft, Windows, and Windows NT are U.S. registered trademarks of Microsoft Corporation. -

Parallel Processing Here at the School of Statistics
Parallel Processing here at the School of Statistics Charles J. Geyer School of Statistics University of Minnesota http://www.stat.umn.edu/~charlie/parallel/ 1 • batch processing • R package multicore • R package rlecuyer • R package snow • grid engine (CLA) • clusters (MSI) 2 Batch Processing This is really old stuff (from 1975). But not everyone knows it. If you do the following at a unix prompt nohup nice -n 19 some job & where \some job" is replaced by an actual job, then • the job will run in background (because of &). • the job will not be killed when you log out (because of nohup). • the job will have low priority (because of nice -n 19). 3 Batch Processing (cont.) For example, if foo.R is a plain text file containing R commands, then nohup nice -n 19 R CMD BATCH --vanilla foo.R & executes the commands and puts the printout in the file foo.Rout. And nohup nice -n 19 R CMD BATCH --no-restore foo.R & executes the commands, puts the printout in the file foo.Rout, and saves all created R objects in the file .RData. 4 Batch Processing (cont.) nohup nice -n 19 R CMD BATCH foo.R & is a really bad idea! It reads in all the objects in the file .RData (if one is present) at the beginning. So you have no idea whether the results are reproducible. Always use --vanilla or --no-restore except when debugging. 5 Batch Processing (cont.) This idiom has nothing to do with R. If foo is a compiled C or C++ or Fortran main program that doesn't have command line arguments (or a shell, Perl, Python, or Ruby script), then nohup nice -n 19 foo & runs it. -

Linux-Kernel
linux-kernel #linux- kernel Table of Contents About 1 Chapter 1: Getting started with linux-kernel 2 Remarks 2 Versions 2 Examples 2 Installation or Setup 2 Download extract and enter to the kernel directory 2 Build the dependencies, compile the kernel and modules. 3 Chapter 2: Creation and usage of Kernel Threads 4 Introduction 4 Examples 4 Creation of kernel threads 4 Chapter 3: Event Tracing 6 Examples 6 Tracing I2C Events 6 Chapter 4: Fork System call 7 Examples 7 fork() system call 7 Chapter 5: How to find the right person for help. 9 Introduction 9 Examples 9 Find the "likely" maintainers for the FTDI USB serial converter 9 Chapter 6: Linux Hello World Device driver 10 Examples 10 An empty kernel module 10 Building and running the module 10 Chapter 7: Linux: Named Pipes(FIFO) 12 Examples 12 What is Named Pipe (FIFO) 12 Credits 13 About You can share this PDF with anyone you feel could benefit from it, downloaded the latest version from: linux-kernel It is an unofficial and free linux-kernel ebook created for educational purposes. All the content is extracted from Stack Overflow Documentation, which is written by many hardworking individuals at Stack Overflow. It is neither affiliated with Stack Overflow nor official linux-kernel. The content is released under Creative Commons BY-SA, and the list of contributors to each chapter are provided in the credits section at the end of this book. Images may be copyright of their respective owners unless otherwise specified. All trademarks and registered trademarks are the property of their respective company owners. -

The Big Picture So Far Today: Process Management
The Big Picture So Far From the Architecture to the OS to the User: Architectural resources, OS management, and User Abstractions. Hardware abstraction Example OS Services User abstraction Processor Process management, Scheduling, Traps, Process protection, accounting, synchronization Memory Management, Protection, virtual memory Address spaces I/O devices Concurrency with CPU, Interrupt Terminal, mouse, printer, handling system calls File System File management, Persistence Files Distributed systems Networking, security, distributed file Remote procedure calls, system network file system System calls Four architectures for designing OS kernels Computer Science CS377: Operating Systems Lecture 4, page 1 Today: Process Management • A process as the unit of execution. • How are processes represented in the OS? • What are possible execution states and how does the system move from one state to another? • How are processes created in the system? • How do processes communicate? Is this efficient? Computer Science CS377: Operating Systems Lecture 4, page 2 What's in a Process? • Process: dynamic execution context of an executing program • Several processes may run the same program, but each is a distinct process with its own state (e.g., MS Word). • A process executes sequentially, one instruction at a time • Process state consists of at least: ! the code for the running program, ! the static data for the running program, ! space for dynamic data (the heap), the heap pointer (HP), ! the Program Counter (PC), indicating the next instruction, ! an execution stack with the program's call chain (the stack), the stack pointer (SP) ! values of CPU registers ! a set of OS resources in use (e.g., open files) ! process execution state (ready, running, etc.). -

6.087 Practical Programming in C, Lecture 14
Outline Review Inter process communication Signals Fork Pipes FIFO Spotlights 1 6.087 Lecture 14 – January 29, 2010 Review Inter process communication Signals Fork Pipes FIFO Spotlights 2 Review: multithreading • Race conditions • non-determinism in thread order. • can be prevented by synchronization • atomic operations necessary for synchronization • Mutex: Allows a single thread to own it • Semaphores: Generalization of mutex, allows N threads to acquire it at a time. • P(s) : acquires a lock • V(s) : releases lock • sem_init(),sem_destroy() • sem_wait(),sem_trywait(),sem_post() • Other problems: deadlock, starvation 2 Sockets • <sys/socket.h> • enables client-server computing • Client: connect() • Server: bind(),listen(),accept() • I/O: write(),send(),read(),recv() 3 6.087 Lecture 14 – January 29, 2010 Review Inter process communication Signals Fork Pipes FIFO Spotlights 4 Preliminaries • Each process has its own address space. Therefore, individual processes cannot communicate unlike threads. • Interprocess communication: Linux/Unix provides several ways to allow communications • signal • pipes • FIFO queues • shared memory • semaphores • sockets 4 <signals.h> • Unix/Linux allows us to handle exceptions that arise during execution (e.g., interrupt, floating point error, segmentation fault etc.). • A process recieves a signal when such a condition occurs. void (∗signal(int sig,void(∗handler)(int )))( int ) • determines how subsequent signals will be handled. • pre-defined behavior: SIG_DFL (default), SIG_IGN (ignore) • returns the previous handler. 5 <signal.h> Valid signals: SIGABRT abnormal termination SIGFPE floating point error SIGILL illegal instruction SIGINT interrupt SIGSEGV segmentation fault SIGTERM termination request SIGBUS bus error SIGQUIT quit The two signals SIGSTOP,SIGKILL cannot be handled. 6 <signal.h> int raise( int sig) can be used to send signal sig to the program. -

Lecture 4: September 13 4.1 Process State
CMPSCI 377 Operating Systems Fall 2012 Lecture 4: September 13 Lecturer: Prashant Shenoy TA: Sean Barker & Demetre Lavigne 4.1 Process State 4.1.1 Process A process is a dynamic instance of a computer program that is being sequentially executed by a computer system that has the ability to run several computer programs concurrently. A computer program itself is just a passive collection of instructions, while a process is the actual execution of those instructions. Several processes may be associated with the same program; for example, opening up several windows of the same program typically means more than one process is being executed. The state of a process consists of - code for the running program (text segment), its static data, its heap and the heap pointer (HP) where dynamic data is kept, program counter (PC), stack and the stack pointer (SP), value of CPU registers, set of OS resources in use (list of open files etc.), and the current process execution state (new, ready, running etc.). Some state may be stored in registers, such as the program counter. 4.1.2 Process Execution States Processes go through various process states which determine how the process is handled by the operating system kernel. The specific implementations of these states vary in different operating systems, and the names of these states are not standardised, but the general high-level functionality is the same. When a process is first started/created, it is in new state. It needs to wait for the process scheduler (of the operating system) to set its status to "new" and load it into main memory from secondary storage device (such as a hard disk or a CD-ROM). -

Secrets of Powershell Remoting
Secrets of PowerShell Remoting The DevOps Collective, Inc. This book is for sale at http://leanpub.com/secretsofpowershellremoting This version was published on 2018-10-28 This is a Leanpub book. Leanpub empowers authors and publishers with the Lean Publishing process. Lean Publishing is the act of publishing an in-progress ebook using lightweight tools and many iterations to get reader feedback, pivot until you have the right book and build traction once you do. © 2016 - 2018 The DevOps Collective, Inc. Also By The DevOps Collective, Inc. Creating HTML Reports in Windows PowerShell A Unix Person’s Guide to PowerShell The Big Book of PowerShell Error Handling DevOps: The Ops Perspective Ditch Excel: Making Historical and Trend Reports in PowerShell The Big Book of PowerShell Gotchas The Monad Manifesto, Annotated Why PowerShell? Windows PowerShell Networking Guide The PowerShell + DevOps Global Summit Manual for Summiteers Why PowerShell? (Spanish) Secrets of PowerShell Remoting (Spanish) DevOps: The Ops Perspective (Spanish) The Monad Manifesto: Annotated (Spanish) Creating HTML Reports in PowerShell (Spanish) The Big Book of PowerShell Gotchas (Spanish) The Big Book of PowerShell Error Handling (Spanish) DevOps: WTF? PowerShell.org: History of a Community Contents Secrets of PowerShell Remoting ..................................... 1 Remoting Basics ................................................ 3 What is Remoting? ............................................ 3 Examining Remoting Architecture .................................. 3 Enabling