Security Standards Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

(With Pulse Output) Instruction Manual
Blank Page User’s Manual Positioning Modules (with Pulse Output) IM 34M6H56-02E Applicable Modules: Model Code Model Name F3NC32-0N Positioning Module (with Pulse Output) F3NC34-0N Positioning Module (with Pulse Output) IM 34M6H56-02E 2nd Edition Yokogawa Electric Corporation i Applicable Product: z Range-free Multi-controller FA-M3 - Model code : F3NC32-0N, F3NC34-0N - Name : Positioning Module (with pulse output) The document number and document model code for this manual are given below. Refer to the document number in all communications; also refer to the document number or the document model code when purchasing additional copies of this manual. - Document No. : IM 34M6H56-02E - Document Model Code : DOCIM Media No. IM 34M6H56-02E (YK) 2nd Edition : Jul., 2007 (AR) IM 34M6H56-02E 2nd Edition : Jul.15, 2007-00 All Rights Reserved Copyright © 2007, Yokogawa Electric Corporation ii Important About This Manual - This Manual should be passed on to the end user. - Before using the controller, read this manual thoroughly to have a clear understanding of the controller. - This manual explains the functions of this product, but there is no guarantee that they will suit the particular purpose of the user. - Under absolutely no circumstances may the contents of this manual be transcribed or copied, in part or in whole, without permission. - The contents of this manual are subject to change without prior notice. - Every effort has been made to ensure accuracy in the preparation of this manual. However, should any errors or omissions come to the attention of the user, please contact the nearest Yokogawa Electric representative or sales office. -

Hardware Manual
User’s Manual Hardware Manual IM 34M06C11-01E IM 34M06C11-01E Yokogawa Electric Corporation 23th Edition Blank Page i Applicable Product z Range-free Multi-controller FA-M3 The document number for this manual is given below. Refer to the document number in all communications, including when purchasing additional copies of this manual. Document No. : IM 34M06C11-01E Media No. IM 34M06C11-01E (CD) 23th Edition :Oct. 01, 2013 (YHQ) IM 34M06C11-01E 23th Edition : Oct. 01, 2013-00 All Rights Reserved Copyright © 2013, Yokogawa Electric Corporation ii Important About This Manual - This Manual should be passed on to the end user. - Before using the controller, read this manual thoroughly to have a clear understanding of the controller. - This manual explains the functions of this product, but there is no guarantee that they will suit the particular purpose of the user. - Under absolutely no circumstances may the contents of this manual be transcribed or copied, in part or in whole, without permission. - The contents of this manual are subject to change without prior notice. - Every effort has been made to ensure accuracy in the preparation of this manual. However, should any errors or omissions come to the attention of the user, please contact the nearest Yokogawa Electric representative or sales office. Safety symbols - Danger. This symbol on the product indicates that the operator must follow the instructions laid out in this user's manual to avoid the risk of personnel injuries, fatalities, or damage to the instrument. Where indicated by this symbol, the manual describes what special care the operator must exercise to prevent electrical shock or other dangers that may result in injury or the loss of life. -

FTSE Japan ESG Low Carbon Select
2 FTSE Russell Publications 19 August 2021 FTSE Japan ESG Low Carbon Select Indicative Index Weight Data as at Closing on 30 June 2021 Constituent Index weight (%) Country Constituent Index weight (%) Country Constituent Index weight (%) Country ABC-Mart 0.01 JAPAN Ebara 0.17 JAPAN JFE Holdings 0.04 JAPAN Acom 0.02 JAPAN Eisai 1.03 JAPAN JGC Corp 0.02 JAPAN Activia Properties 0.01 JAPAN Eneos Holdings 0.05 JAPAN JSR Corp 0.11 JAPAN Advance Residence Investment 0.01 JAPAN Ezaki Glico 0.01 JAPAN JTEKT 0.07 JAPAN Advantest Corp 0.53 JAPAN Fancl Corp 0.03 JAPAN Justsystems 0.01 JAPAN Aeon 0.61 JAPAN Fanuc 0.87 JAPAN Kagome 0.02 JAPAN AEON Financial Service 0.01 JAPAN Fast Retailing 3.13 JAPAN Kajima Corp 0.1 JAPAN Aeon Mall 0.01 JAPAN FP Corporation 0.04 JAPAN Kakaku.com Inc. 0.05 JAPAN AGC 0.06 JAPAN Fuji Electric 0.18 JAPAN Kaken Pharmaceutical 0.01 JAPAN Aica Kogyo 0.07 JAPAN Fuji Oil Holdings 0.01 JAPAN Kamigumi 0.01 JAPAN Ain Pharmaciez <0.005 JAPAN FUJIFILM Holdings 1.05 JAPAN Kaneka Corp 0.01 JAPAN Air Water 0.01 JAPAN Fujitsu 2.04 JAPAN Kansai Paint 0.05 JAPAN Aisin Seiki Co 0.31 JAPAN Fujitsu General 0.01 JAPAN Kao 1.38 JAPAN Ajinomoto Co 0.27 JAPAN Fukuoka Financial Group 0.01 JAPAN KDDI Corp 2.22 JAPAN Alfresa Holdings 0.01 JAPAN Fukuyama Transporting 0.01 JAPAN Keihan Holdings 0.02 JAPAN Alps Alpine 0.04 JAPAN Furukawa Electric 0.03 JAPAN Keikyu Corporation 0.02 JAPAN Amada 0.01 JAPAN Fuyo General Lease 0.08 JAPAN Keio Corp 0.04 JAPAN Amano Corp 0.01 JAPAN GLP J-REIT 0.02 JAPAN Keisei Electric Railway 0.03 JAPAN ANA Holdings 0.02 JAPAN GMO Internet 0.01 JAPAN Kenedix Office Investment Corporation 0.01 JAPAN Anritsu 0.15 JAPAN GMO Payment Gateway 0.01 JAPAN KEWPIE Corporation 0.03 JAPAN Aozora Bank 0.02 JAPAN Goldwin 0.01 JAPAN Keyence Corp 0.42 JAPAN As One 0.01 JAPAN GS Yuasa Corp 0.03 JAPAN Kikkoman 0.25 JAPAN Asahi Group Holdings 0.5 JAPAN GungHo Online Entertainment 0.01 JAPAN Kinden <0.005 JAPAN Asahi Intecc 0.01 JAPAN Gunma Bank 0.01 JAPAN Kintetsu 0.03 JAPAN Asahi Kasei Corporation 0.26 JAPAN H.U. -

FA-M3 Temperature Control and Monitoring Modules and PID Control Module IM 34M6H61-01E 2Nd Edition
User’s Manual Temperature Control and Monitoring Modules and PID Control Module IM 34M6H61-01E IM 34M6H61-01E 2nd Edition Yokogawa Electric Corporation i Applicable Product: - Model Code : F3CT04-0N - Name : Temperature Control and Monitoring Module - Model Code : F3CT04-1N - Name : Temperature Control and Monitoring Module - Model Code : F3CR04-0N - Name : Temperature Control and Monitoring Module - Model Code : F3CR04-1N - Name : Temperature Control and Monitoring Module - Model Code : F3CV04-1N - Name : PID Control Module The document number and document model code for this manual are given below. Refer to the document number in all communications; also refer to the document number or the document model code when purchasing additional copies of this manual. - Document No. : IM 34M6H61-01E - Document Model Code : DOCIM Media No. IM 34M6H61-01E (FD) 2nd Edition : Aug, 2001 (CR) IM 34M6H61-01E 2nd Edition : Aug, 2001-00 All Rights Reserved, Copyright © 1999, Yokogawa Electric Corporation ii Important About This Manual - This Manual should be passed on to the end user. - Before using the controller, read this manual thoroughly to have a clear understanding of the controller. - This manual explains the functions of this product, but there is no guarantee that they will suit the particular purpose of the user. - Under absolutely no circumstances may the contents of this manual be transcribed or copied, in part or in whole, without permission. - The contents of this manual are subject to change without prior notice. - Every effort has been made to ensure accuracy in the preparation of this manual. However, should any errors or omissions come to the attention of the user, please contact the nearest Yokogawa Electric representative or sales office. -

第 1 頁,共 5 頁 Hdmi :: ?喃? :: ? 熙? ?蝏 ? 2005/7/19
HDMI :: ?喃? :: ? 熙? ?蝏 ? 第 1 頁,共 5 頁 HDMI 组织 Hitachi, Ltd. Matsushita Electric Industrial Co., Ltd. (Panasonic) Sony Corporation Philips Consumer Electronics International B.V. Thomson, Inc. Silicon Image, Inc. Toshiba Corporation HDMI 许可采纳者 Last Updated on 7/18/2005 2Wire Inc Krell Industries 3S Digital Co Ltd Leader Electronics Corp. 690885 Ontario Inc. LeCroy Japan Corporation A&R Cambridge Ltd (Arcam) LG Electronics Advanced-Connectek Inc. Linktec Technologies Co Ltd Advanced Display Lab Inc. Linn Products Ltd Advanced Knowledge Associates Lin Shiung Enterprise Co Ltd Agilent Technologies Inc. Lite-On Corporation Akai Electric Co Ltd Loewe Opta GmbH Alco Digital Devices Limited Longwell Company Algolith Inc. LPS Device Co Ltd ALI Corporation Main Super Enterprises Co. Amoi Electronics Co Ltd Marshall Electronics AmTran Technology Master Co. LTD-Korea Analog Devices, Inc. Master Hill Electric Wire & Cable Analogix Semiconductor Inc MediaTek Corp. Anam Electronics Co Ltd Meridian Audio Limited Anchor Bay Technologies Metz-Werke GmbH & Co KG Asahi Kasei Microsystems Co Ltd Micronas GmbH http://cn.hdmi.org/about/adopters_founders.asp 2005/7/19 HDMI :: ?喃? :: ? 熙? ?蝏 ? 第 2 頁,共 5 頁 AstroDesign Inc. MIK21 Co., Ltd Asustek Computer Inc Y-S Electronic Co., Ltd ATI Technologies, Inc. Mitac Technology Corp Audio Partnership PLC Mitsubishi Electric Corporation Audio-Technica Corporation Mitsumi Electric Co., Ltd. Aurora Multimedia Corp Molex Incorporated Avid Technology Inc. Morning Star Industrial BAFO Technologies/TWN 1st Line Elect Cor Motorola, Inc. Bang & Olufsen MSL Enterprises Corp BBK AV Electronics Corp Ltd. Mstar Semiconductor, Inc. BenQ Corporation Murata Manufacturing Co.,Ltd. Beko Elektronik A.S. -

CORPORATE PROFILE Name KOUEI CO., LTD
CORPORATE PROFILE Name KOUEI CO., LTD. Company History President CEO Kazuhiro Yamaguchi Founded in Higashimizue, Edogawa-ku on 1977/3. Foundation Mar. 3, 1977 Moved to Chuo, Edogawa-ku on 1988/9. Established Oct. 3, 1978 Moved to the current location on 1997/7. Capital(JPY) 48(mil.) Saitama Factory operation started on 2009/5. Employee 86 (incl. directors) Headquarter New Bldg. Completion on 2020/10. Fiscal Year March 31 Kansai Branch opened on 2021/7. Certification ISO9001:2015 ISO14001:2015 Total Capital (JPY) H.Q. New 3-5-4, Chuo, Edogawa-ku, 1978 Oct. 3 (mil.) 1982 Jan. 6 (mil.) Bldg. Tokyo, 132-0021 JAPAN 1987 May. 12 (mil.) 1997 Jun. 24 (mil.) TEL +81-3-3674-5222 2001 Aug. 48(mil.) FAX +81-3-3656-0503 Annual Sales Amount (JPY) URL https://www.kabkouei.co.jp 2017 Mar. 4,177(mil.) 2018 Mar. 4,284(mil.) E-mail [email protected] 2019 Mar. 3,965(mil.) 2020 Mar. 3,977(mil.) H.Q. Main 3-5-6, Chuo, Edogawa-ku, Bank Bldg. Tokyo, 132-0021 JAPAN MUFJ Bank, Sumitomo Mitsui Banking Corporation, Risona Bank, Shoko Chukin Bank, Mizuho Bank, Kansai 2F, Akashiya Bldg., 2-5-13, The Chiba Bank, Kiraboshi Bank, Branch Koraibashi, Chuo-ku, Osaka The Tokyo Higashi Shinkin Bank, City, Osaka, 541-0043 JAPAN Business Line TEL +81-6-6786-8117 Raw material sales, Processing, Design and production for FAX +81-6-6786-8151 plant facility and machine, Processing of strip (rolling, Saitama 1450-10, Ohmidoh, slitting, annealing, clad), Trading of metal scrap Factory Kamisato-Machi, Kodama-gun, Sales Materials Saitama, 369-0315 JAPAN Pure nickel, Electric -

Proposal of a Data Processing Guideline for Realizing Automatic Measurement Process with General Geometrical Tolerances and Contactless Laser Scanning
Proposal of a data processing guideline for realizing automatic measurement process with general geometrical tolerances and contactless laser scanning 2018/4/4 Atsuto Soma Hiromasa Suzuki Toshiaki Takahashi Copyright (c)2014, Japan Electronics and Information Technology Industries Association, All rights reserved. 1 Contents • Introduction of the Project • Problem Statements • Proposed Solution – Proposal of New General Geometric Tolerance (GGT) – Data Processing Guidelines for point cloud • Next Steps Copyright (c)2014, Japan Electronics and Information Technology Industries Association, All rights reserved. 2 Contents • Introduction of the Project • Problem Statements • Proposed Solution – Proposal of New General Geometric Tolerance (GGT) – Data Processing Guidelines for Point Cloud • Next Steps Copyright (c)2014, Japan Electronics and Information Technology Industries Association, All rights reserved. 3 Introduction of JEITA What is JEITA? The objective of the Japan Electronics and Information Technology Industries Association (JEITA) is to promote healthy manufacturing, international trade and consumption of electronics products and components in order to contribute to the overall development of the electronics and information technology (IT) industries, and thereby to promote further Japan's economic development and cultural prosperity. JEITA’s Policy and Strategy Board > Number of full members: 279> Number of associate members: 117(as of May 13, 2014) - Director companies and chair/subchair companies - Policy director companies (alphabetical) Fujitsu Limited (chairman Masami Yamamoto) Asahi Glass Co., Ltd. Nichicon Corporation Sharp Corporation Azbil Corporation IBM Japan, Ltd. Hitachi, Ltd. Advantest Corporation Nippon Chemi-Con Corporation Panasonic Corporation Ikegami Tsushinki Co., Ltd. Japan Aviation Electronics Industry, Ltd. SMK Corporation Mitsubishi Electric Corporation Nihon Kohden Corporation Omron Corporation NEC Corporation JRC Nihon Musen Kyocera Corporation Sony Corporation Hitachi Metals, Ltd KOA Corporation Fuji Xerox Co., Ltd. -

YOKOGAWA with EPLAN
More Familiar More Efficient More Convenient Y K AWA wi h EPLAN t OG YOKOGAWA with EPLAN Efficient Design and Engineering EPLAN provides a web-based engineering tool to improve engineering work and documentation quality. With the EPLAN Data Portal, you can easily find complete drawings of devices or components of Yokogawa’s offerings, which include FA-M3, UTAdvanced, and SMARTDAC+. This tool ensures that you can address vast engineering documents more efficiently when developing a comprehensive project design. LF 04L01A10-01EN Y K AWA wi h EPLAN t OG YOKOGAWA with EPLAN Product Line-up Programmable Logic Controllers The FA-M3 is designed and best known for its speed so it's only natural that the new series be named FA-M3V, where V stands for "Vitesse", which means speed in French. From day one, FA-M3 has relentlessly pursued higher speeds as the most effective means to solving customer challenges. www.yokogawa.com/solutions/products-platforms/control-system/programmable-logic-controllers-plc-pac/ Temperature PID Controllers UTAdvanced Temperature Controller employs an easy-to-read, 14-segment large color LCD display, along with navigation keys, thus greatly increasing the monitoring and operating capabilities. It also supports open networks such as Ethernet communication. DIN rail mounting controllers have been added. www.yokogawa.com/solutions/products-platforms/control-system/controllers-indicators/temperature-controllers/ Paperless Recorders The GX10/GX20 is a paperless recorder that provides intuitive operation through a touch screen. Its modular architecture supports a wide array of input/output modules, with even more modules available soon. Its custom graphics accommodates application or process-specific displays. -

FTSE Publications
2 FTSE Russell Publications 20 May 2020 FTSE Japan Indicative Index Weight Data as at Closing on 31 March 2020 Constituent Index weight (%) Country Constituent Index weight (%) Country Constituent Index weight (%) Country 77 Bank 0.03 JAPAN Denso Corporation 0.45 JAPAN Isetan Mitsukoshi Holdings 0.06 JAPAN ABC-Mart 0.04 JAPAN Dentsu Inc 0.13 JAPAN Isuzu Motors 0.1 JAPAN Acom 0.05 JAPAN DIC 0.06 JAPAN Ito En 0.09 JAPAN Advantest Corp 0.24 JAPAN Disco 0.17 JAPAN Itochu Corp 0.87 JAPAN Aeon 0.48 JAPAN DMG Mori Seiki 0.03 JAPAN Itochu Techno Solutions 0.08 JAPAN AEON Financial Service 0.04 JAPAN Dowa Holdings 0.04 JAPAN Itoham Yonekyu Holdings 0.02 JAPAN Aeon Mall 0.05 JAPAN East Japan Railway 0.84 JAPAN Iyo Bank 0.04 JAPAN AGC 0.14 JAPAN Ebara 0.06 JAPAN Izumi Co Ltd 0.03 JAPAN Aica Kogyo 0.05 JAPAN Eisai 0.6 JAPAN J Front Retailing 0.06 JAPAN Ain Pharmaciez 0.05 JAPAN Electric Power Development 0.1 JAPAN Japan Airlines 0.06 JAPAN Air Water 0.08 JAPAN Ezaki Glico 0.07 JAPAN Japan Airport Terminal 0.06 JAPAN Aisin Seiki Co 0.13 JAPAN FamilyMart 0.13 JAPAN Japan Aviation Electronics 0.02 JAPAN Ajinomoto Co 0.28 JAPAN Fancl Corp 0.05 JAPAN Japan Exchange Group 0.29 JAPAN Alfresa Holdings 0.1 JAPAN Fanuc 0.8 JAPAN Japan Petroleum Exploration 0.02 JAPAN Alps Alpine 0.06 JAPAN Fast Retailing 0.65 JAPAN Japan Post Bank 0.12 JAPAN Amada 0.08 JAPAN FP Corporation 0.05 JAPAN Japan Post Holdings 0.32 JAPAN Amano Corp 0.05 JAPAN Fuji Electric 0.09 JAPAN Japan Post Insurance 0.07 JAPAN ANA Holdings 0.08 JAPAN Fuji Media Holdings 0.01 JAPAN Japan Steel -
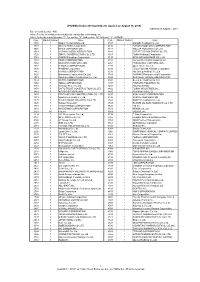
"JPX-Nikkei Index 400"
JPX-Nikkei Index 400 Constituents (applied on August 30, 2019) Published on August 7, 2019 No. of constituents : 400 (Note) The No. of constituents is subject to change due to de-listing. etc. (Note) As for the market division, "1"=1st section, "2"=2nd section, "M"=Mothers, "J"=JASDAQ. Code Market Divison Issue Code Market Divison Issue 1332 1 Nippon Suisan Kaisha,Ltd. 3107 1 Daiwabo Holdings Co.,Ltd. 1333 1 Maruha Nichiro Corporation 3116 1 TOYOTA BOSHOKU CORPORATION 1605 1 INPEX CORPORATION 3141 1 WELCIA HOLDINGS CO.,LTD. 1719 1 HAZAMA ANDO CORPORATION 3148 1 CREATE SD HOLDINGS CO.,LTD. 1720 1 TOKYU CONSTRUCTION CO., LTD. 3167 1 TOKAI Holdings Corporation 1721 1 COMSYS Holdings Corporation 3197 1 SKYLARK HOLDINGS CO.,LTD. 1801 1 TAISEI CORPORATION 3231 1 Nomura Real Estate Holdings,Inc. 1802 1 OBAYASHI CORPORATION 3254 1 PRESSANCE CORPORATION 1803 1 SHIMIZU CORPORATION 3288 1 Open House Co.,Ltd. 1808 1 HASEKO Corporation 3289 1 Tokyu Fudosan Holdings Corporation 1812 1 KAJIMA CORPORATION 3291 1 Iida Group Holdings Co.,Ltd. 1820 1 Nishimatsu Construction Co.,Ltd. 3349 1 COSMOS Pharmaceutical Corporation 1821 1 Sumitomo Mitsui Construction Co., Ltd. 3360 1 SHIP HEALTHCARE HOLDINGS,INC. 1824 1 MAEDA CORPORATION 3382 1 Seven & I Holdings Co.,Ltd. 1860 1 TODA CORPORATION 3391 1 TSURUHA HOLDINGS INC. 1861 1 Kumagai Gumi Co.,Ltd. 3401 1 TEIJIN LIMITED 1878 1 DAITO TRUST CONSTRUCTION CO.,LTD. 3402 1 TORAY INDUSTRIES,INC. 1881 1 NIPPO CORPORATION 3405 1 KURARAY CO.,LTD. 1893 1 PENTA-OCEAN CONSTRUCTION CO.,LTD. 3407 1 ASAHI KASEI CORPORATION 1911 1 Sumitomo Forestry Co.,Ltd. -

An Environmental Management System (EMS) Designed for Global Deployment the Yokogawa Group Is Deploying an EMS Globally with the Aim of Building a Sustainable Society
Building a Sustainable Society Yo kogawa Group Environmental Management Report 2005 Yokogawa Electric Corporation Yo k ogawa Group Profile Group ogawa 2004 Special ReportYear Fiscal Management Environmental Yo kogawa Group Environmental Management Report Building a Sustainable Society A Message from Management Editorial Policy Yokogawa Group Profile Corporate Profile Environmental Management Practices Fiscal Year 2004 Special Report The Yokogawa Group’s Contribution to Reducing the Environmental Impact of Its Customer’s Operations Environmental Management Environmental Management Activities Overview of Environmental Impact Environmental Accounting Indicators and Achievements Environmentally Friendly Products and Solutions Green Procurement and Purchasing Products and Solutions Products Friendly Environmentally Environmentally Friendly Products Development of Environmentally Friendly Products Environmental Solutions Improving Environmental Performance Green Production Lines Preventing Global Warming Protecting the Air and Water Soil Cleaning Comprehensive Management of Chemical Substances P Environmental Improving erformance Reduced Use of Hazardous Substances Zero Emissions Logistics Relations with Customers, Employees and Communities (for enhancing CSR) Employee Relations Customer Relations Community Relations Environmental Communication (for enhancing CSR) (for and Communities Employees Relations with Customers, Supplementary Information A History of Caring for Our Environment From the Editor Yo k A Message from Management Profile Group -

FA-M3 Sequence CPU – Functions (For F3SP66-4S, F3SP67-6S) IM 34M6P14-01E 1St Edition
User’s Manual Sequence CPU – Functions (for F3SP66-4S, F3SP67-6S) IM 34M6P14-01E IM 34M6P14-01E 1st Edition Yokogawa Electric Corporation Blank Page i Applicable Product z Range-free-controller FA-M3 - Model Name: F3SP66-4S, F3SP67-6S - Name: Sequence CPU Module (with network functions) The document number and document model code for this manual are given below. Refer to the document number in all communications; also refer to the document number or the document model code when purchasing additional copies of this manual. Document No. : IM 34M6P14-01E Document Model Code : DOCIM Media No. IM 34M6P14-01E (CD) 1st Edition : Jun. 15, 2007-00 (AR) IM 34M6P14-01E 1st Edition : Jun. 15, 2007-00 All Rights Reserved Copyright © 2007, Yokogawa Electric Corporation ii Important About This Manual - This Manual should be passed on to the end user. - Before using the controller, read this manual thoroughly to have a clear understanding of the controller. - This manual explains the functions of this product, but there is no guarantee that they will suit the particular purpose of the user. - Under absolutely no circumstances may the contents of this manual be transcribed or copied, in part or in whole, without permission. - The contents of this manual are subject to change without prior notice. - Every effort has been made to ensure accuracy in the preparation of this manual. However, should any errors or omissions come to the attention of the user, please contact the nearest Yokogawa Electric representative or sales office. Safety Precautions when Using/Maintaining the Product - The following safety symbols are used on the product as well as in this manual.