Blue Screen of Death (BSOD)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Kernel Panic
Kernel Panic Connect, Inc. 1701 Quincy Avenue, Suites 5 & 6, Naperville, IL 60540 Ph: (630) 717-7200 Fax: (630) 717-7243 www.connectrf.com Table of Contents SCO Kernel Patches for Panics on Pentium Systems…………………………………..1 Kernel Panic Debug Methodologies..............................................................................3 SCO Kernel Patches for Panics on Pentium Systems SCO Kernel Patches for Panics on Pentium Systems Web Links http://www.sco.com/cgi-bin/ssl_reference?104530 http://www.sco.com/cgi-bin/ssl_reference?105532 Pentium System Panics with Trap Type 6; no dump is saved to /dev/swap. Keywords panic trap kernel invalid opcode pentium querytlb querytbl 386 mpx unix v4 dump swap double type6 no patch /etc/conf/pack.d/kernel/locore.o image locore Release SCO UNIX System V/386 Release 3.2 Operating System Version 4.0, 4.1 and 4.2 SCO Open Desktop Release 2.0 and 3.0 SCO Open Server System Release 2.0 and 3.0 Problem My system panics with a Trap Type 6, but no memory dump gets written. Cause There is a flaw in the kernel querytlb() routine that allows the Pentium to execute a 386-specific instruction which causes it to panic with an invalid opcode. querytlb() is only called when your system is panicking. The fault causes the system to double- panic and it thus fails to write a panic dump to disk. This means that the panic trap type 6 is concealing another type of panic which will show itself after the following patch has been applied. Solution You can apply the following patch, as root, to: /etc/conf/pack.d/kernel/locore.o Use the procedure that follows. -

Microsoft Update Blue Screen Error Fixing BSOD
kyoceradocumentsolutions.us Microsoft Update Blue Screen Error Fixing BSOD March 2021 Microsoft Update Blue Screen Error What is causing the Blue Screen error when I print using the KX Driver? Kyocera as well as many other companies began getting reports of Blue Screen of Death (BSOD) incidents when printing. Microsoft released 2 updates this week, KB5000802 and KB5000808. The updates caused the crash. What has Microsoft done since this was reported? Microsoft has removed both updates from the automatic pushed update list. If your PC has not yet downloaded the update it will not install them. If you manually update your system from within Windows Update the 2 problem updates are still there and can be manually selected and installed. Do not do that until a complete fix is released if your PC is used for printing. Microsoft has left them up for manual install for users that have systems not used for printing. How do we fix a PC that has already been updated? The best solution is to uninstall the 2 Updates. Follow the directions below and remember to reboot when done. 1. Open a Command Prompt with Administrator rights. Click on the Start button and type cmd. The following will be displayed. 2 Microsoft Update Blue Screen Error 2. Click Run as Administrator on the right to open the Command Prompt Window. Accept the prompt to open with elevated rights and make changes to the computer. 3. In the Command Prompt enter the following command and press enter. – wusa /uninstall /kb:5000802 4. The Stand alone install will launch and remove the Update. -
How to Fix a Frozen Windows PC
How to Fix a Frozen Windows PC Mashka/Shutterstock.com Windows PCs freeze for a variety of reasons. One instance might be a fluke, but repeated freezes suggest a problem you’ll want to fix. Here’s how to unfreeze and recover a stuck PC—and stop it from freezing again. How to Speed Up a Slow PC Volume 0% How to Unfreeze a Frozen Windows PC There are several ways you can recover your frozen PC, depending on what caused the problem. Sometimes, all you have to do is wait a few seconds—the PC might get hung up while doing some work and unfreeze itself a few seconds later. If a full-screen application, like a game, freezes and prevents you from leaving it, press Alt+F4. This closes the application if the game is just experiencing graphical problems, but it won’t work if the application has frozen completely. To see if the computer is still responding, press Ctrl+Alt+Delete. From this screen, you can open the Task Manager (and close any running applications), or log out of or restart your PC. If this screen doesn’t appear, you might not be able to recover your PC without rebooting it. If you can open the Task Manager, you might be able to recover from the freeze. (You can also press Ctrl+Shift+Esc to open the Task Manager.) Select the “Processes” tab—if you don’t see it, click “More Details.” Locate any processes using a lot of CPU—you can click the “CPU” column header to sort by CPU usage and see the most demanding processes at the top of the list. -

Mac OS 8 Update
K Service Source Mac OS 8 Update Known problems, Internet Access, and Installation Mac OS 8 Update Document Contents - 1 Document Contents • Introduction • About Mac OS 8 • About Internet Access What To Do First Additional Software Auto-Dial and Auto-Disconnect Settings TCP/IP Connection Options and Internet Access Length of Configuration Names Modem Scripts & Password Length Proxies and Other Internet Config Settings Web Browser Issues Troubleshooting • About Mac OS Runtime for Java Version 1.0.2 • About Mac OS Personal Web Sharing • Installing Mac OS 8 • Upgrading Workgroup Server 9650 & 7350 Software Mac OS 8 Update Introduction - 2 Introduction Mac OS 8 is the most significant update to the Macintosh operating system since 1984. The updated system gives users PowerPC-native multitasking, an efficient desktop with new pop-up windows and spring-loaded folders, and a fully integrated suite of Internet services. This document provides information about Mac OS 8 that supplements the information in the Mac OS installation manual. For a detailed description of Mac OS 8, useful tips for using the system, troubleshooting, late-breaking news, and links for online technical support, visit the Mac OS Info Center at http://ip.apple.com/infocenter. Or browse the Mac OS 8 topic in the Apple Technical Library at http:// tilsp1.info.apple.com. Mac OS 8 Update About Mac OS 8 - 3 About Mac OS 8 Read this section for information about known problems with the Mac OS 8 update and possible solutions. Known Problems and Compatibility Issues Apple Language Kits and Mac OS 8 Apple's Language Kits require an updater for full functionality with this version of the Mac OS. -

Linux Tutorial Last Updated: September 29 2021 for Windows Users
VLAAMS SUPERCOMPUTER Innovative Computing CENTRUM for A Smarter Flanders Linux Tutorial Last updated: September 29 2021 For Windows Users Authors: Jasper Devreker (UGent), Ewan Higgs (UGent), Kenneth Hoste (UGent) Acknowledgement: VSCentrum.be Audience: This document is a hands-on guide for using the Linux command line in the context of the UGent HPC infrastructure. The command line (sometimes called ’shell’) can seems daunting at first, but with a little understanding can be very easy to use. Everything you do startsatthe prompt. Here you have the liberty to type in any commands you want. Soon, you will be able to move past the limited point and click interface and express interesting ideas to the computer using the shell. Gaining an understanding of the fundamentals of Linux will help accelerate your research using the HPC infrastructure. You will learn about commands, managing files, and some scripting basics. Notification: In$ commands this tutorial specific commands are separated from the accompanying text: These should be entered by the reader at a command line in a terminal on the UGent-HPC. They appear in all exercises preceded by a $ and printed in bold. You’ll find those actions ina grey frame. Button are menus, buttons or drop down boxes to be pressed or selected. “Directory” is the notation for directories (called “folders” in Windows terminology) or specific files. (e.g., “/user/home/gent/vsc400/vsc40000”) “Text” Is the notation for text to be entered. Tip: A “Tip” paragraph is used for remarks or tips. They can also be downloaded from the VSC website at https://www.vscentrum.be. -

Xerox 4050/4090/4450/4650 Laser Printing Systems Message Guide
XEROX Xerox 4050/4090/4450/4650 Laser Printing Systems Message Guide April 1995 720P93980 Xerox Corporation 701 S. Aviation Boulevard El Segundo, CA 90245 © 1991, 1992, 1993, 1994, 1995 by Xerox Corporation. All rights reserved. Copyright protection claimed includes all forms and matters of copyrightable material and information now allowed by statutory or judicial law or hereinafter granted, including without limitation, material generated from the software programs which are displayed on the screen, such as icons, screen displays, looks, etc. Printed in the United States of America Publication number: 720P93980 Xerox® and all Xerox products mentioned in this publication are trademarks of Xerox Corporation. Products and trademarks of other companies are also acknowledged. Changes are periodically made to this document. Changes, technical inaccuracies, and typographic errors will be corrected in subsequent editions. This document was created on the Xerox 6085 Professional Computer System using GobalView software. The typeface is Optima. Table of contents Introduction vii Document conventions vii Related publications viii 1. Compress command messages 1-1 2. Data Capture Utility messages 2-1 System failure or reload messages 2-6 3. Disk Save and Restore command messages 3-1 4. File Conversion Utility messages 4-1 5. General Floppy Utility messages 5-1 FLF messages 5-15 6. Forms Description Language compilation messages 6-1 7. Host Interface Processor messages 7-1 8. Interpress Font Utility messages 8-1 9. Operating System Software messages 9-1 OS level 0: Confirmation messages 9-1 OS level 1: Informational messages 9-7 OS level 2: Routine maintenance messages 9-37 OS level 3: Printer problem messages 9-59 OS level 4: System or tape problem messages 9-64 OS level 6: Job integrity problem messages 9-68 OS level 7: System problem messages 9-88 OS level 8: Probable severe software errors 9-93 OS level 9: Probable severe hardware errors 9-99 10. -

Acronis True Image for Western Digital
Acronis True Image for Western Digital USER GUIDE Table of contents 1 Introduction ....................................................................................................................5 1.1 What is Acronis True Image for Western Digital? ..................................................................... 5 1.2 Backups created in Acronis True Image ..................................................................................... 5 1.3 System requirements and supported media ............................................................................. 6 1.3.1 Minimum system requirements .................................................................................................................... 6 1.3.2 Supported operating systems ........................................................................................................................ 7 1.3.3 Backing up all data on your PC ....................................................................................................................... 7 1.3.4 Supported file systems .................................................................................................................................... 8 1.3.5 Supported storage media ............................................................................................................................... 8 1.4 Installing Acronis True Image for Western Digital ..................................................................... 9 1.5 Activating Acronis True Image for Western Digital .................................................................10 -
SUMURI Macintosh Forensics Best Practices
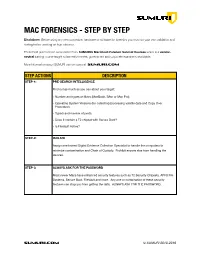
! MAC FORENSICS - STEP BY STEP Disclaimer: Before using any new procedure, hardware or software for forensics you must do your own validation and testing before working on true evidence. These best practices are summarized from SUMURI’s Macintosh Forensic Survival Courses which is a vendor- neutral training course taught to law enforcement, government and corporate examiners worldwide. More information about SUMURI can be found at SUMURI.com STEP ACTIONS DESCRIPTION STEP-1: PRE-SEARCH INTELLIGENCE Find out as much as you can about your target: • Number and types of Macs (MacBook, iMac or Mac Pro). • Operating System Versions (for collecting/processing volatile data and Copy Over Procedure). • Type/s and number of ports. • Does it contain a T2 chipset with Secure Boot? • Is FileVault Active? STEP-2: ISOLATE Assign one trained Digital Evidence Collection Specialist to handle the computers to minimize contamination and Chain of Custody. Prohibit anyone else from handling the devices. STEP-3: ALWAYS ASK FOR THE PASSWORD Most newer Macs have enhanced security features such as T2 Security Chipsets, APFS File Systems, Secure Boot, FileVault and more. Any one or combination of these security features can stop you from getting the data. ALWAYS ASK FOR THE PASSWORD. SUMURI.com © SUMURI 2010-2019 ! STEP ACTIONS DESCRIPTION STEP-4: IF COMPUTER IS ON - SCREEN SAVER PASSWORD ACTIVE Options are: • Ask for the Password - Confirm password and proceed to Step-6. • Restart to Image RAM - Connect a RAM Imaging Utility to the Mac such as RECON IMAGER. Conduct a soft-restart (do not power off if possible and image the RAM). -

Pure User Mode Deterministic Replay on Windows
Pure User Mode Deterministic Replay on Windows Atle Nærum Eriksen Thesis submitted for the degree of Master in Informatics: programming and networks 60 credits Department of Informatics Faculty of mathematics and natural sciences UNIVERSITY OF OSLO Autumn 2017 Pure User Mode Deterministic Replay on Windows Atle Nærum Eriksen August 1, 2017 Abstract The ability to record and replay program executions has many interesting applications such as debugging in the backwards direction, discovering and fixing the source of non-deterministic bugs and data races and retracing the steps of a system intrusion. Unfortunately, the power of deterministic replay tools is underutilized by the general public as the tools are either too difficult to deploy or unable to fulfill the performance and log size requirements of the user. As it happens, the majority of the research has been aimed at implementing such tools for Linux, and other platforms, including Windows, have mostly been neglected. In this thesis we look at whether it is possible to implement a determin- istic replay tool for the Windows platform that is easily deployable (user mode only without operating system support { this entails no OS modifi- cations or drivers), can record all system calls and their side-effects (even if unknown), works on large programs (1 GB+ RAM), and has a high recording performance (≈2x slowdown). We found that the challenges deterministic replay tools are facing in user mode are exacerbated on Windows due to a lack of documentation and a more restrictive API. Despite this we came up with a design proposal that solves all the problems necessary to implement a deterministic replay tool that satisfies all our requirements for the Windows platform. -

Errors and Error Checking in Windows
Errors and error checking in Windows Higham and Rushden U3A Let’s first of all look at probably the most serious but least common: Total Windows failure Earlier versions of Windows used to crash much more frequently than they do today, usually accompanied by the very unfriendly Blue Screen of Death (BSOD) shown on the left below, and/or one of the other error messages shown. Windows 10 has moved on from there. Apart from anything else the screen is a much friendlier blue and it has a nice emoticon as well! Joking aside, the blue screen in Windows 10 is normally followed by the PC restarting and quite regularly the machine will boot up normally as Windows has adjusted some settings in the background. It probably doesn’t do any harm to make a note of the error details at the bottom of the screen in case the restart fails to solve the problem, but any solutions you find online are likely to be complicated and technical, and may well contradict other suggested fixes. Be warned! Also be aware that the restart process may take a while. Other errors and warnings are often generated by User Account Control, which is Windows’ way of trying to keep you safe, so turn it off at your peril. When a background program tries to do something, Windows will often ask you if you want it to do that. This program was downloaded, so unless you are absolutely certain that you downloaded it deliberately, and have just clicked on it to start it or make changes, it is probably safer to say “no”. -

Critical Vulnerabilities Bulletin
January 18th, 2021 Critical Vulnerabilities Bulletin Confidential | Cyberint Copyright © All Rights Reserved 2020 CRITICAL VULNERABILITIES BULLETIN | INDUSTRY SECURITY BULLETIN JANUARY 14, 2021 EXECUTIVE SUMMARY Due to an unusual increase in Critical vulnerabilities found on Windows operating systems, Cyberint's Research Team has decided to release this bulletin to alert our customers of the potential impact. This bulletin will be expanded at the end of the month, as part of the Monthly Vulnerability bulletin we plan on releasing. The reason for this bulletin lies at 2 newly discovered vulnerabilities: 1. <No CVE assigned yet> - Corrupt NTFS OS partition without user interaction. 2. <No CVE assigned yet> - Trigger a BSOD by trying to access a system path. 3. CVE-2020-1398 - Potential bypass of Bitlocker protected systems, including Lock Screen bypass. We suspect that threat actors and updated malware may attempt to exploit these vulnerabilities to further impact potential victims. Confidential | Cyberint Copyright © All Rights Reserved 2020 2 CRITICAL VULNERABILITIES BULLETIN | INDUSTRY SECURITY BULLETIN JANUARY 14, 2021 NTFS CORRUPTION VULNERABILITY Published by a known vulnerability researcher, jonasLyk, it is possible to cause disk partition corruption by executing a cd command as a low privilege user, to a unique path, which causes the Windows Operating System to alert the user to a corrupted partition and force a restart. Whilst technical details are scarce, and the exact reason for the issue being unknown at this time, affected Windows builds using the NTFS file system include those from 1803 all the way to 20H2. According to SANS, the $bitmap is an attribute reserved for files marked as deleted, while $i30 is marked as an NTFS index attribute. -

UNIX X Command Tips and Tricks David B
SESUG Paper 122-2019 UNIX X Command Tips and Tricks David B. Horvath, MS, CCP ABSTRACT SAS® provides the ability to execute operating system level commands from within your SAS code – generically known as the “X Command”. This session explores the various commands, the advantages and disadvantages of each, and their alternatives. The focus is on UNIX/Linux but much of the same applies to Windows as well. Under SAS EG, any issued commands execute on the SAS engine, not necessarily on the PC. X %sysexec Call system Systask command Filename pipe &SYSRC Waitfor Alternatives will also be addressed – how to handle when NOXCMD is the default for your installation, saving results, and error checking. INTRODUCTION In this paper I will be covering some of the basics of the functionality within SAS that allows you to execute operating system commands from within your program. There are multiple ways you can do so – external to data steps, within data steps, and within macros. All of these, along with error checking, will be covered. RELEVANT OPTIONS Execution of any of the SAS System command execution commands depends on one option's setting: XCMD Enables the X command in SAS. Which can only be set at startup: options xcmd; ____ 30 WARNING 30-12: SAS option XCMD is valid only at startup of the SAS System. The SAS option is ignored. Unfortunately, ff NOXCMD is set at startup time, you're out of luck. Sorry! You might want to have a conversation with your system administrators to determine why and if you can get it changed.