End User Devices Security Guidance: Windows 8 RT Updated 14 October 2013
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

System Requirements for LWC Connect to Learning
System Requirements for LWC Connect to Learning Run the Adobe Connect Diagnostic to see if you meet the Flash, connection, and add-in minimum requirements https://na3cps.adobeconnect.com/common/help/en/support/meeting_test.htm MINIMUM COMPUTER SYSTEM REQUIREMENTS: Windows • 1.4GHz Intel® Pentium® 4 or faster processor (or equivalent) for Microsoft® Windows® XP, Windows 7 or Windows 8 • Windows 8.1 (32-bit/64-bit), Windows 8 (32-bit/64-bit), Windows 7 (32-bit/64-bit), Windows XP • 512MB of RAM (1GB recommended) for Windows XP, Windows 7 or Windows 8 • Microsoft Internet Explorer 8, 9, 10, 11; Mozilla Firefox; Google Chrome • Adobe® Flash® Player 11.2+ Mac OS • 1.83GHz Intel Core™ Duo or faster processor • 512MB of RAM (1GB recommended) • Mac OS X 10.7.4, 10.8, 10.9 • Mozilla Firefox; Apple Safari; Google Chrome • Adobe Flash Player 11.2+ Linux • Ubuntu 12.04; Red Hat Enterprise Linux 6; OpenSuSE 12.2 • No Add-in support for Linux. Users on Linux can attend meetings in the browser. • Mozilla Firefox • Adobe Flash Player 11.2+ Mobile • Apple supported devices: iPhone 5S, iPhone 5, iPhone 4S, iPad with Retina display, iPad 3, iPad 2, iPad mini, and iPod touch (4th & 5th generations) • Apple supported OS versions summary: iOS 6 and higher • Android supported devices: Motorola DROID RAZR MAXX, Motorola Atrix, Motorola Xoom, Samsung Galaxy Tab 2 10.1, Samsung Galaxy S3 & S4, Nexus 7 tablet • Android supported OS versions summary: 2.3.4 and higher 1 ADDITIONAL REQUIREMENTS • Latest version of Adobe Flash Player installed o Download latest version at http://get.adobe.com/flashplayer/ . -

Microsoft'sevolving App Strategy
CAN MICROSOFT MAP THE FUTURE OF IT? Microsoft’s Evolving App Strategy Microsoft is trying to better align its applications through a new interface and improved cloud connectivity. Is this the right strategy? BY BRIEN M. POSEY THE NEW INTERFACE WHERE RT AND OFFICE FIT CLOUD CONNECTIVITY CAN MICROSOFT MAP THE FUTURE OF IT? VER THE PAST two decades, Microsoft’s strategy for desktop and mobile ap- plications has remained relatively static. Microsoft devoted much of its energy to creating operating systems and allowed applications to develop almost as an afterthought. THE NEW Even today the company adheres to this haphazard approach to applications. INTERFACE O At the same time, the company’s most recent product-release cycle demonstrates that Microsoft’s support for desktop and mobile apps is evolving. WHERE RT AND OFFICE FIT When it comes to application support in the company’s latest releases, two major themes have emerged: the new tile-based user interface (UI) and cloud con- nectivity. While both of these technologies benefit a segment of Microsoft’s cus- CLOUD CONNECTIVITY tomer base, they have also created numerous challenges for IT professionals. In particular, the new Windows 8 interface has been an impediment to adop- tion among business users, but it is part of a concerted effort on Microsoft’s part to build consistency throughout its application set. Despite this imperfect strat- egy, there are signs that the approach is pointing Microsoft in a direction that al- lows business users to productively use Windows, Office and other applications on PCs, tablets and smartphones. 2 MICROSOFT’S EVOLVING APP STRATEGY THE NEW INTERFACE WINDOWS’ NEW INTERFACE The most well-known element of the Windows 8 operating system is the new user interface (which at one time was called the Metro interface and is now known as the Windows 8-style UI). -

Supported Server-Side Configuration
Server and hosting requirements Supported server-side configuration Supported operating systems: Windows 7 Service Pack 1 (32bit or 64bit) Windows 8 or 8.1 (32bit or 64bit) Windows 10 (32bit or 64bit) Windows Server versions: 2008 R2 Service Pack 1, 2012, 2012 R2 We recommend that you install the following components on the computer where you want to run Kentico. If you do not install these components on your computer before installing Kentico, the Installer is capable of downloading and installing them or their suitable alternatives on its own (except for the Visual Studio built-in server). In such cases, your computer must be connected to the Internet. Microsoft .NET Framework 4.5 or 4.6. Microsoft Internet Information Services (see the table below) or Visual Studio 2012/2013/2015 built-in web server. Microsoft SQL Server 2008 R2, 2012, 2014 (including the free SQL Server Express Edition 2008 R2/2012/2014). The collation set for the SQL server must be case-insensitive. Internet Information Services overview The following table lists instructions on how to install different versions of IIS on different operating systems. Internet Information Services version Operating system Details and installation instructions IIS 7.0 Windows Vista not supported Windows Server 2008 IIS 7.5 Windows 7 SP1 IIS 7 Installation and Deployment Windows Server 2008 R2 SP1 IIS 8.0 Windows 8 Installing IIS on Windows Server 2012 Windows Server 2012 IIS 8.5 Windows 8.1 Installing IIS 8.5 Windows Server 2012 R2 IIS 10 Windows 10 Same process as IIS 8+ For the Kentico -

Tablets in the Enterprise: Comparing the Total Cost of Ownership
TABLETS IN THE ENTERPRISE: COMPARING THE TOTAL COST OF OWNERSHIP EXECUTIVE SUMMARY Windows 8 tablets provide a PC experience, which for many workers is essential to maintaining productivity. With Windows 8, users can run familiar desktop applications, maintaining productivity without having to find new ways to carry out their tasks. They can read, edit, and print their emails and Office documents—tasks that can be a challenge on other tablets. In addition to these productivity advantages, Intel Core i5 processor and Windows 8 tablets can provide enterprises with total cost of ownership (TCO) savings of up to 18 percent compared to other tablets. We expect additional TCO savings with Intel Core vPro™ processor-based tablets due to their additional manageability capabilities. We estimate tablets with Intel Architecture and Windows 8 will have lower TCO than other tablets, primarily due to the following: reduced software costs lower management costs improved end-user productivity JANUARY 2013 A PRINCIPLED TECHNOLOGIES WHITE PAPER Commissioned by Intel Corp. TOTAL COST OF OWNERSHIP OF TABLETS IN THE ENTERPRISE In this paper, we first present a TCO analysis for a hypothetical enterprise considering four major categories of tablets for their employees: Microsoft Windows 8 tablets, Windows RT tablets, Android tablets, and Apple iPads. Because the ranges of prices and capabilities differ among models within each category, we selected a single representative model for each. Following this analysis, we discuss the dominant issues in enterprise tablet computing as of this writing. We base our TCO analysis on the primary assumptions in Figure 1. Tablets must be nine inches or larger with 64 GB of storage and Wi-Fi support. -

Models Step 1: Identify Which Version of the Windows Phone Operating
Nokia Lumia – All Models (Excluding models 710 and 800) Step 1: Identify which version of the Windows Phone operating system is installed on your phone: 1. Go to your App list. 2. From there, tap “Settings” > “About” > “More info”. 3. The “Software” section indicates which version of the Windows Phone operating system is in use. a. If your phone is currently running Windows Phone 7, proceed to page 2 for instructions on how to wipe your device. b. If your phone is currently running Windows Phone 8, 8.1, or 10, proceed to page 3 for instructions on how to wipe your device. ______________________________________________________________________________ Nokia Lumia - Tous les modèles (À l'exclusion des modèles 710 et 800) Étape 1: Déterminer la version du système d'exploitation Windows Phone installée sur votre téléphone: 1. Accédez à votre liste d’applications. 2. Presse « Paramètres » > « À propos » > « Plus d'info ». 3. La section « Logiciel » indique le nom de la version du système d'exploitation Windows Phone. a. Si votre téléphone utilise actuellement Windows Phone 7, aller à la page 2 pour obtenir des instructions sur la façon de réinitialiser votre téléphone. b. Si votre téléphone utilise actuellement Windows Phone 8, 8.1, ou 10, aller à la page 4 pour obtenir des instructions sur la façon de réinitialiser votre téléphone. Nokia Lumia (Windows 7.5) Model Numbers: 610, 900 The following instruction will give you all the information you need to remove your personal information from your phone. Before recycling your device please also remember to: The account for the device has been fully paid and service has been deactivated. -

Flashboot User Manual
FlashBoot User Manual © 2015 Mikhail Kupchik Contents 3 Table of Contents Foreword 0 Part I Introduction 5 1 Product................................................................................................................................... Overview 5 2 Why USB................................................................................................................................... Flash Disks? 5 3 Why FlashBoot?................................................................................................................................... 6 4 System................................................................................................................................... Requirements 7 5 Limitations................................................................................................................................... of Demo Version 8 6 Demo Version................................................................................................................................... -> Full Version 8 7 Support................................................................................................................................... & Feedback 8 Part II CD/DVD to USB conversions 9 1 Install ...................................................................................................................................full Win8/8.1/10 -> USB [BIOS mode] 9 2 Install................................................................................................................................... full -

Microsoft Surface for Education Limited Time Offer
Microsoft Surface for education limited time offer Surface RT (32GB) - AU $219 incl. GST (RRP is $389) Surface RT (32GB) with Touch Keyboard Cover - AU $279 incl. GST (RRP is $449) Surface RT (32GB) with Type Keyboard Cover - AU $319 incl. GST (RRP is $539) For a limited time only, Microsoft is offering education institution customers special pricing on the Surface RT tablet. This offer is available for order now through to 30 September 2013. Our mission in education is to help schools and universities, students and educators realise their full potential. One way we do this is by offering software, hardware and services at affordable prices to education institutions. Surface RT is a terrific tool for teaching and learning and we want students and educators to have the best technology on the market today. Surface RT for Schools and Universities Communicate with Skype and Lync Microsoft Surface RT is a great choice for schools and universities who Today schools are using Skype and Lync to host virtual classes, invite want powerful, affordable touch-enabled tablets for students, educators prominent speakers into classrooms, and connect with other schools and staff. In addition to cutting edge hardware specs, Surface RT comes from around the world. Lync when combined with Office 365 for Educa- with many software and cloud features that will have educators and tion is an enterprise-grade web meeting and collaboration solution that students teaching and learning in no time. provides HD video conferencing, instant messaging and presenting content. Many students and schools choose Skype for its simplicity, high Microsoft Office Built-In quality video and voice conference calls and very large user base. -

Lumia with Windows 10 Mobile User Guide
User Guide Lumia with Windows 10 Mobile Issue 1.1 EN-US About this user guide This guide is the user guide for your software release. Important: For important information on the safe use of your device and battery, read “For your safety” and “Product and safety info” in the printed or in-device user guide, or at www.microsoft.com/mobile/support before you take the device into use. To find out how to get started with your new device, read the printed user guide. For the online user guidance, videos, even more information, and troubleshooting help, go to support.microsoft.com, and browse to the instructions for Windows phones. You can also check out the support videos at www.youtube.com/lumiasupport. Moreover, there's a user guide in your phone – it's always with you, available when needed. To find answers to your questions and to get helpful tips, tap Lumia Help+Tips. If you’re new to Lumia, check out the section for new users. For info on Microsoft Privacy Statement, go to aka.ms/privacy. © 2016 Microsoft Mobile. All rights reserved. 2 User Guide Lumia with Windows 10 Mobile Contents For your safety 5 People & messaging 64 Get started 6 Calls 64 Turn the phone on 6 Contacts 68 Lock the keys and screen 7 Social networks 73 Charge your phone 7 Messages 74 Your first Lumia? 10 Email 78 Learn more about your phone 10 Camera 83 Set up your phone 10 Open your camera quickly 83 Update your apps 11 Camera basics 83 Explore your tiles, apps, and settings 12 Advanced photography 86 Navigate inside an app 14 Photos and videos 88 Use the touch screen -
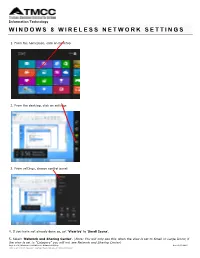
Windows 8 Wireless Network Settings
Information Technology WINDOWS 8 WIRELESS NETWORK SETTINGS 1. From the homepage, click on Desktop 2. From the desktop, click on settings 3. From settings, choose control panel 4. If you have not already done so, set ‘View by’ to ‘Small Icons’. 5. Select ‘Network and Sharing Center’. (Note: You will only see this when the view is set to Small or Large Icons; if the view is set to “Category” you will not see Network and Sharing Center) Page 1 of 6; Windows 8 OS Wireless Network Settings Rev.: 2/5/2013 TMCC is an EEO/AA institution. See http://eeo.tmcc.edu for more information. 6. Click ‘Set up a new connection or network’. 7. Click ‘Manually connect to a wireless network’. Then click ‘Next’. 8. Fill in the appropriate Network name: a. For Students: TMCC-Student b. For Staff: TMCC-Admin Security 9. Select ‘WPA2-Enterprise’ from the security type drop-down box. 10. Select ‘AES’ from the encryption type drop-down box. 11. Leave the Security key field blank. 12. Make sure ‘Connect even if the network is not broadcasting’ box is checked. 13. Below is an example of what is should look like for students: 14. Click ‘Next’. 15. Click ‘Change connection settings’ 16. Make sure both 'Connect automatically when this network is in range' and 'Connect even if the network is not broadcasting its name (SSID)' are selected. Page 2 of 6; Windows 8 OS Wireless Network Settings Rev.: 2/5/2013 TMCC is an EEO/AA institution. See http://eeo.tmcc.edu for more information. -
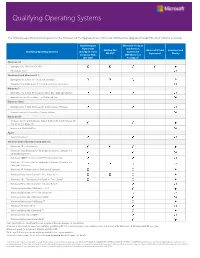
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows 10: Considered Harmful
Windows 10: Considered Harmful 26 August, 2016 Last Updated: 25 September 2016 Previously I made a series of articles against Windows 10, consisting of basic explanation, open letters, and even a long-winded chance.org petition. However, I have come to realize that these various things could be better as one page rather than fragments across my website. On this page I hope to explain why the Windows 10 system is evil and also include why Windows as a whole is Considered Harmful . Sources to unreferenced items in this article can be found in the various resource links on the bottom of the page. Information can also be found in the photographs shown and with a simple web search. The primary reason against the Windows 10 system is an obvious one. The system is designed to be a system that data-mines the user. This is proven time and time again. Using a tool such as wireshark, one can clearly see that it makes encrypted connections to a variety of Microsoft servers. This uses a very weak RSA encryption that can be broken in under a minute. When a user successfully decrypted the encrypted data, he simply converted the decrypted ``.bin'' extension to ``.png'' and opened them. The image files were screen- shots of him installing the RSA decryptor tool. This was in a VM and was a fresh install. In addition to this, another user in Australia also monitored the odd connection but did not decrypt it. He noticed this when he opened a photograph in the Windows Photo App. -

Bluetooth Setting Utility for Mcollection
Software Manual - Star Bluetooth Utility for mCollection- Supported Models MCP31LB MCP21LB POP10 Rev. 1.0 Introduction l This utility enables you to configure your mCollection printer. l This manual is made for the Star Bluetooth Utility Ver.2.0.0. l The Bluetooth Utility supports the following Windows OS versions: aWindows 7 32-bit and 64-bit aWindows 8 32-bit and 64-bit (except Windows RT) aWindows 8.1 32-bit and 64-bit (except Windows RT 8.1) aWindows 10 32-bit and 64-bit (except Windows 10 Mobile and Windows 10 IoT) * Limitation for Windows 8 / 8.1 / 10 - Desktop UI only. l Administrator privilege is required to execute this utility. Notice • All rights reserved. Reproduction of any part of this manual in any form whatsoever, without STAR’s express permission is forbidden. • The contents of this manual are subject to change without notice. • All efforts have been made to ensure the accuracy of the contents of this manual at the time of going to press. However, should any errors be detected, STAR would greatly appreciate being informed of them. • The above notwithstanding, STAR can assume no responsibility for any errors in this manual. © 2018 Star Micronics Co., Ltd. Bluetooth Utility 1. Getting Started With the Bluetooth Utility Make the following preparations before using this utility. 1. Complete Bluetooth pairing between the PC and the printer, and check the COM port access point. See the "Online Manual" for more information on pairing. 2. Executing the Bluetooth Utility To execute the Bluetooth utility, proceed as follows. 1. On the Windows taskbar, click 'Start', and then click 'All Programs' > 'Star Micronics' > 'Printer Software for mCollection'> 'Star Bluetooth for mCollection' .