Introduction Chapter 1: Roadmap
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Digital Subscriber Line (DSL) Technologies
CHAPTER21 Chapter Goals • Identify and discuss different types of digital subscriber line (DSL) technologies. • Discuss the benefits of using xDSL technologies. • Explain how ASDL works. • Explain the basic concepts of signaling and modulation. • Discuss additional DSL technologies (SDSL, HDSL, HDSL-2, G.SHDSL, IDSL, and VDSL). Digital Subscriber Line Introduction Digital Subscriber Line (DSL) technology is a modem technology that uses existing twisted-pair telephone lines to transport high-bandwidth data, such as multimedia and video, to service subscribers. The term xDSL covers a number of similar yet competing forms of DSL technologies, including ADSL, SDSL, HDSL, HDSL-2, G.SHDL, IDSL, and VDSL. xDSL is drawing significant attention from implementers and service providers because it promises to deliver high-bandwidth data rates to dispersed locations with relatively small changes to the existing telco infrastructure. xDSL services are dedicated, point-to-point, public network access over twisted-pair copper wire on the local loop (last mile) between a network service provider’s (NSP) central office and the customer site, or on local loops created either intrabuilding or intracampus. Currently, most DSL deployments are ADSL, mainly delivered to residential customers. This chapter focus mainly on defining ADSL. Asymmetric Digital Subscriber Line Asymmetric Digital Subscriber Line (ADSL) technology is asymmetric. It allows more bandwidth downstream—from an NSP’s central office to the customer site—than upstream from the subscriber to the central office. This asymmetry, combined with always-on access (which eliminates call setup), makes ADSL ideal for Internet/intranet surfing, video-on-demand, and remote LAN access. Users of these applications typically download much more information than they send. -

Lecture 10: Switching & Internetworking
Lecture 10: Switching & Internetworking CSE 123: Computer Networks Alex C. Snoeren HW 2 due WEDNESDAY Lecture 10 Overview ● Bridging & switching ◆ Spanning Tree ● Internet Protocol ◆ Service model ◆ Packet format CSE 123 – Lecture 10: Internetworking 2 Selective Forwarding ● Only rebroadcast a frame to the LAN where its destination resides ◆ If A sends packet to X, then bridge must forward frame ◆ If A sends packet to B, then bridge shouldn’t LAN 1 LAN 2 A W B X bridge C Y D Z CSE 123 – Lecture 9: Bridging & Switching 3 Forwarding Tables ● Need to know “destination” of frame ◆ Destination address in frame header (48bit in Ethernet) ● Need know which destinations are on which LANs ◆ One approach: statically configured by hand » Table, mapping address to output port (i.e. LAN) ◆ But we’d prefer something automatic and dynamic… ● Simple algorithm: Receive frame f on port q Lookup f.dest for output port /* know where to send it? */ If f.dest found then if output port is q then drop /* already delivered */ else forward f on output port; else flood f; /* forward on all ports but the one where frame arrived*/ CSE 123 – Lecture 9: Bridging & Switching 4 Learning Bridges ● Eliminate manual configuration by learning which addresses are on which LANs Host Port A 1 ● Basic approach B 1 ◆ If a frame arrives on a port, then associate its source C 1 address with that port D 1 ◆ As each host transmits, the table becomes accurate W 2 X 2 ● What if a node moves? Table aging Y 3 ◆ Associate a timestamp with each table entry Z 2 ◆ Refresh timestamp for each -

A Technology Comparison Adopting Ultra-Wideband for Memsen’S File Sharing and Wireless Marketing Platform
A Technology Comparison Adopting Ultra-Wideband for Memsen’s file sharing and wireless marketing platform What is Ultra-Wideband Technology? Memsen Corporation 1 of 8 • Ultra-Wideband is a proposed standard for short-range wireless communications that aims to replace Bluetooth technology in near future. • It is an ideal solution for wireless connectivity in the range of 10 to 20 meters between consumer electronics (CE), mobile devices, and PC peripheral devices which provides very high data-rate while consuming very little battery power. It offers the best solution for bandwidth, cost, power consumption, and physical size requirements for next generation consumer electronic devices. • UWB radios can use frequencies from 3.1 GHz to 10.6 GHz, a band more than 7 GHz wide. Each radio channel can have a bandwidth of more than 500 MHz depending upon its center frequency. Due to such a large signal bandwidth, FCC has put severe broadcast power restrictions. By doing so UWB devices can make use of extremely wide frequency band while emitting very less amount of energy to get detected by other narrower band devices. Hence, a UWB device signal can not interfere with other narrower band device signals and because of this reason a UWB device can co-exist with other wireless devices. • UWB is considered as Wireless USB – replacement of standard USB and fire wire (IEEE 1394) solutions due to its higher data-rate compared to USB and fire wire. • UWB signals can co-exists with other short/large range wireless communications signals due to its own nature of being detected as noise to other signals. -
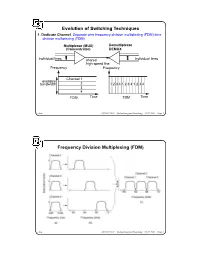
Evolution of Switching Techniques Frequency Division Multiplexing
Evolution of Switching Techniques 1. Dedicate Channel. Separate wire frequency division multiplexing (FDM) time division multiplexing (TDM) Multiplexor (MUX) Demultiplexor (Concentrator) DEMUX individual lines shared individual lines high speed line Frequency Frequency Channel 1 available bandwidth 2 1 2 3 4 1 2 3 4 1 2 3 4 3 4 FDM Time TDM Time chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 1 Frequency Division Multiplexing (FDM) chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 2 Wavelength Division Multiplexing chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 3 Impact of WDM z Many big organizations are starting projects to design WDM system or DWDN (Dense Wave Division Mutiplexing Network). We may see products appear in next three years.In Fujitsu and CCL/Taiwan, 128 different wavelengthes on the same strand of fiber was reported working in the lab. z We may have optical routers between end systems that can take one wavelenght signal, covert to different wavelenght, send it out on different links. Some are designing traditional routers that covert optical signal to electronical signal, and use time slot interchange based on high speed memory to do the switching, the convert the electronic signal back to optical signal. z With this type of optical networks, we will have a virtual circuit network, where each connection is assigned some wave length. Each connection can have 2.4 gbps tremedous bandwidth. z With inital 128 different wavelength, we can have about 10 end users. If each pair of end users needs to communicate simultaneously, it will use 10*10=100 different wavelength. -

A Comparison of Mechanisms for Improving TCP Performance Over Wireless Links
A Comparison of Mechanisms for Improving TCP Performance over Wireless Links Hari Balakrishnan, Venkata N. Padmanabhan, Srinivasan Seshan and Randy H. Katz1 {hari,padmanab,ss,randy}@cs.berkeley.edu Computer Science Division, Department of EECS, University of California at Berkeley Abstract the estimated round-trip delay and the mean linear deviation from it. The sender identifies the loss of a packet either by Reliable transport protocols such as TCP are tuned to per- the arrival of several duplicate cumulative acknowledg- form well in traditional networks where packet losses occur ments or the absence of an acknowledgment for the packet mostly because of congestion. However, networks with within a timeout interval equal to the sum of the smoothed wireless and other lossy links also suffer from significant round-trip delay and four times its mean deviation. TCP losses due to bit errors and handoffs. TCP responds to all reacts to packet losses by dropping its transmission (conges- losses by invoking congestion control and avoidance algo- tion) window size before retransmitting packets, initiating rithms, resulting in degraded end-to-end performance in congestion control or avoidance mechanisms (e.g., slow wireless and lossy systems. In this paper, we compare sev- start [13]) and backing off its retransmission timer (Karn’s eral schemes designed to improve the performance of TCP Algorithm [16]). These measures result in a reduction in the in such networks. We classify these schemes into three load on the intermediate links, thereby controlling the con- broad categories: end-to-end protocols, where loss recovery gestion in the network. is performed by the sender; link-layer protocols, that pro- vide local reliability; and split-connection protocols, that Unfortunately, when packets are lost in networks for rea- break the end-to-end connection into two parts at the base sons other than congestion, these measures result in an station. -

Wifi Direct Internetworking
WiFi Direct Internetworking António Teólo∗† Hervé Paulino João M. Lourenço ADEETC, Instituto Superior de NOVA LINCS, DI, NOVA LINCS, DI, Engenharia de Lisboa, Faculdade de Ciências e Tecnologia, Faculdade de Ciências e Tecnologia, Instituto Politécnico de Lisboa Universidade NOVA de Lisboa Universidade NOVA de Lisboa Portugal Portugal Portugal [email protected] [email protected] [email protected] ABSTRACT will enable WiFi communication range and speed even in cases of: We propose to interconnect mobile devices using WiFi-Direct. Hav- network infrastructure congestion, which may happen in highly ing that, it will be possible to interconnect multiple o-the-shelf crowded venues (such as sports and cultural events); or temporary, mobile devices, via WiFi, but without any supportive infrastructure. or permanent, absence of infrastructure, as may happen in remote This will pave the way for mobile autonomous collaborative sys- locations or disaster situations. tems that can operate in any conditions, like in disaster situations, WFD allows devices to form groups, with one of them, called in very crowded scenarios or in isolated areas. This work is relevant Group Owner (GO), acting as a soft access point for remaining since the WiFi-Direct specication, that works on groups of devices, group members. WFD oers node discovery, authentication, group does not tackle inter-group communication and existing research formation and message routing between nodes in the same group. solutions have strong limitations. However, WFD communication is very constrained, current imple- We have a two phase work plan. Our rst goal is to achieve mentations restrict group size 9 devices and none of these devices inter-group communication, i.e., enable the ecient interconnec- may be a member of more than one WFD group. -

Who Owns the Eyeballs? Backbone Interconnection As a Network Neutrality Issue Jonas from Soelberg
Who Owns the Eyeballs? Backbone interconnection as a network neutrality issue Jonas From Soelberg Name: Jonas From Soelberg CPR: - Date: August 1, 2011 Course: Master’s thesis Advisor: James Perry Pages: 80,0 Taps: 181.999 Table of Contents 1 Introduction ..................................................................................................................... 4 1.1 Methodology ....................................................................................................................................... 6 2 Understanding the Internet ........................................................................................ 9 2.1 The History of the Internet ............................................................................................................ 9 2.1.1 The Internet protocol ................................................................................................................................. 9 2.1.2 The privatization of the Internet ......................................................................................................... 11 2.2 The Architecture of the Internet ................................................................................................ 12 2.2.1 A simple Internet model .......................................................................................................................... 12 2.2.2 The e2e principle and deep-packet inspection ............................................................................. 14 2.2.3 Modern challenges to e2e ...................................................................................................................... -

Volume 1, Section 5.1: Managed Tiered Security
Enterprise SM VOLUME 1, SECTION 5.1: MANAGED TIERED SECURITY SERVICES Enterprise SM 5.1 MANAGED TIERED SECURITY SERVICES [C.2.7.4, M.2.1.3] Level 3 will support the GSA’s Multi-Tier Security Profiles (MTSP) initiative in accordance with Tier-2 – Protected Service specifications. We teamed with one of the world’s leading Managed Security Services providers, , to offer one of the most complete and reliable Managed Security Solutions available. Our solution is designed to meet or exceed the Government’s requirements for MTSP Tier 2 service, as defined in RFP Section C.2.7.4.1.1.2. A description of our offering is provided below. Responses to the requirements of RFP Section L.34.1.6 follow. The Level 3 MTSP Tier 2 solution includes the Help Desk function specified for Tier 1 service, and additional technical and management components to support security needs of Sensitive but Unclassified (SBU) mission functions and information. Our Managed Tiered Security Service (MTSS) offering will provide a vehicle for agencies to order individual managed security services a la carte or in a bundle. The components include: Volume 1, Section 5.1 Page 667 Rev. 3-5-2007 Managed Tiered Security Services TQC-JTB-05-0002 © 2007 Level 3 Communications, Inc. All rights reserved. Use or disclosure of data contained on this sheet is subject to the restric ions on the title page of this proposal. Enterprise SM Agencies will gain efficiencies and cost savings through service bundling, versus ordering any of the Managed Security Services a la carte. -

Cable Modem/Router with Wireless-N
DOCSIS 3.0 Model 5352 Cable Modem/Router with Wireless-N The Zoom 5352 Cable Modem/Router with Wireless-N supports cable modem speeds up to 343 Mbps. With its high speed and IPv4 and IPv6 networking support, this is a product designed and built for use today and for years to come. The embedded router with Wireless-N support continues the high-performance with 300 Mbps 2 X 2 MIMO for the range, wireless speeds and networking support needed for multimedia, Internet video and high-performance networking in a home or office. DOCSIS 3.0 cable performance allows bonding of up to eight channels on downloads and four channels on uploads when used with the latest cable systems. DOCSIS 2.0 and 1.1 support provides compatibility with older cable systems. Cable modem performance has been tested and approved by CableLabs, the industry's non-profit test and certification authority. Additonal testing and approvals have been obtained from Cox, Comcast, Time Warner Cable and other leading cable service providers. Features of the Model 5352 include: n DOCSIS 3.0 performance with CableLabs certification n Up to 8 Downstream channels and 4 Upstream channels, for speeds as high as 343 Mbps on downloads and 123 Mbps on uploads with full band capture front end n Provides shared high-speed Internet over cable to: - WiFi compatible wireless 802.11n, g, and b devices - Devices with an Ethernet port, including computers and game stations n Easy setup and management with Universal Plug and Play (UPnP), WPS wireless security setup, and browser-based management n -

Lecture 8: Overview of Computer Networking Roadmap
Lecture 8: Overview of Computer Networking Slides adapted from those of Computer Networking: A Top Down Approach, 5th edition. Jim Kurose, Keith Ross, Addison-Wesley, April 2009. Roadmap ! what’s the Internet? ! network edge: hosts, access net ! network core: packet/circuit switching, Internet structure ! performance: loss, delay, throughput ! media distribution: UDP, TCP/IP 1 What’s the Internet: “nuts and bolts” view PC ! millions of connected Mobile network computing devices: server Global ISP hosts = end systems wireless laptop " running network apps cellular handheld Home network ! communication links Regional ISP " fiber, copper, radio, satellite access " points transmission rate = bandwidth Institutional network wired links ! routers: forward packets (chunks of router data) What’s the Internet: “nuts and bolts” view ! protocols control sending, receiving Mobile network of msgs Global ISP " e.g., TCP, IP, HTTP, Skype, Ethernet ! Internet: “network of networks” Home network " loosely hierarchical Regional ISP " public Internet versus private intranet Institutional network ! Internet standards " RFC: Request for comments " IETF: Internet Engineering Task Force 2 A closer look at network structure: ! network edge: applications and hosts ! access networks, physical media: wired, wireless communication links ! network core: " interconnected routers " network of networks The network edge: ! end systems (hosts): " run application programs " e.g. Web, email " at “edge of network” peer-peer ! client/server model " client host requests, receives -

Mapping Networks and Services Proc
Mapping Networks and Services Proc. INET ´93 J.S. Quarterman Mapping Networks and Services John S. Quarterman1 Smoot Carl-Mitchell2 Gretchen Phillips3 Abstract I . Introduction Four global networks carry most of the Computer networking is widespread, supported by international network traffic; FidoNet, UUCP, the global Matrix of interconnected computer BITNET, and the Internet. The first step in networks such as the Internet, BITNET, UUCP, looking at these networks involves collecting and FidoNet. Perhaps 20,000,000 people use this appropriate data for each and performing some global Matrix of computer networks, and several consistency checking. The data for these maps major global computer networks are growing was initially derived from their node lists exponentially, rapidly reaching new countries and (BITNET and FidoNet) or host lists (UUCP). The new classes of users. This growth prompts Internet data came from a domain walk by Mark network users and service providers to ask Lottor. questions like: The data available from the node lists, public d Where are these users? maps and the domain walk is not in a format that d What is the magnitude of the various network is readily usable for this type of mapping. Each communities? map or other source of network information tends d What are the available services? to include different details. We have correlated the d How are services distributed? data by using telephone country codes, area codes d And, finally, how can this data be represented and local exchanges for determining locations. A in a meaningful graphical way? more complete discussion of the methods is We have chosen Latin America and the Caribbean available in issues of Matrix News[5-7] (ALyC) as the geographic region for discussing these issues and demonstrating the mapping of II . -

Br-Asi01 Br-Asx01
BR-ASI01 BR-ASX01 Data Comm for Business, Inc. 807 Pioneer Street Champaign, IL 61820 217-352-3207 Rev. Date: October 17, 1996 This manual applies to both the “I” and “X” router models. The “I” model (BR-ASI01) is single protocol TCP/IP only. The “X” model (BR-ASX01) is a multi-protocol router that routes TCP/IP, IPX, DECnet, and Appletalk. When using this manual with “I” model router, ignore the manual sections pertaining to protocols other than TCP/IP. CHAPTER 1 - INTRODUCTION 7 ABOUT THE BR ROUTER 7 Getting Started 7 Hardware Installation 7 RouterView Software Installation 8 Command Line Preparation 8 Quickstart Configuration 8 Appendices and Index 8 CHAPTER 2 - GETTING STARTED 9 A FEW NOTES 9 Please Read The Manuals 9 Warranty and Service 9 Getting Help With the BR Router 9 WHAT YOU WILL NEED TO GET STARTED 9 Supplied with the BR Router 9 Needed For Installation 10 Ethernet Connection Requirements 10 Thick Ethernet 10 Thin Ethernet 10 10Base-T Twisted-Pair Ethernet 10 Telco Line Connection Requirements 11 RS-232 Port 11 CHAPTER 3 - HARDWARE INSTALLATION 13 Mounting the Router 13 Connecting the Router to the Ethernet 14 Connecting to Thick Ethernet 14 Connecting to Thin Ethernet 14 Connecting to Twisted-Pair Ethernet 14 Connecting a Line Device to the BR Router 14 Connecting Devices to the RS-232C Port 15 Connecting an Out-of-Band Management Console 15 Powering Up the Router 15 CHAPTER 4 - ROUTERVIEW SOFTWARE INSTALLATION 17 RouterView for Windows 17 System Requirements 17 Installing and Running RouterView for Windows 17 RouterView