Lab 7: Breaking Windows Passwords
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Analysis of Password Cracking Methods & Applications
The University of Akron IdeaExchange@UAkron The Dr. Gary B. and Pamela S. Williams Honors Honors Research Projects College Spring 2015 Analysis of Password Cracking Methods & Applications John A. Chester The University Of Akron, [email protected] Please take a moment to share how this work helps you through this survey. Your feedback will be important as we plan further development of our repository. Follow this and additional works at: http://ideaexchange.uakron.edu/honors_research_projects Part of the Information Security Commons Recommended Citation Chester, John A., "Analysis of Password Cracking Methods & Applications" (2015). Honors Research Projects. 7. http://ideaexchange.uakron.edu/honors_research_projects/7 This Honors Research Project is brought to you for free and open access by The Dr. Gary B. and Pamela S. Williams Honors College at IdeaExchange@UAkron, the institutional repository of The nivU ersity of Akron in Akron, Ohio, USA. It has been accepted for inclusion in Honors Research Projects by an authorized administrator of IdeaExchange@UAkron. For more information, please contact [email protected], [email protected]. Analysis of Password Cracking Methods & Applications John A. Chester The University of Akron Abstract -- This project examines the nature of password cracking and modern applications. Several applications for different platforms are studied. Different methods of cracking are explained, including dictionary attack, brute force, and rainbow tables. Password cracking across different mediums is examined. Hashing and how it affects password cracking is discussed. An implementation of two hash-based password cracking algorithms is developed, along with experimental results of their efficiency. I. Introduction Password cracking is the process of either guessing or recovering a password from stored locations or from a data transmission system [1]. -

Cryptanalytic Tools
Cryptanalytic Tools Authors: Prof. Dr.-Ing. Tim Güneysu Dipl. Ing. Alexander Wild B. Sc. Tobias Schneider Ruhr-Universität Bochum Module Cryptanalytic Tools Chapter 3: Introduction to Cryptanalysis Chapter 4: Computational Complexity and Parallelism Chapter 5: Secret Parameters and Keys Chapter 6: Tools for Symmetric Cryptanalysis Chapter 7: Tools for Asymmetric Cryptanalysis Authors: Prof. Dr.-Ing. Tim Güneysu Dipl. Ing. Alexander Wild B. Sc. Tobias Schneider 1. edition Ruhr-Universität Bochum © 2015 Ruhr-Universität Bochum Universitätsstraße 150 44801 Bochum 1. edition (31. March 2015) Das Werk einschließlich seiner Teile ist urheberrechtlich geschützt. Jede Ver- wendung außerhalb der engen Grenzen des Urheberrechtsgesetzes ist ohne Zustimmung der Verfasser unzulässig und strafbar. Das gilt insbesondere für Vervielfältigungen, Übersetzungen, Mikroverfilmungen und die Einspe- icherung und Verarbeitung in elektronischen Systemen. Um die Lesbarkeit zu vereinfachen, wird auf die zusätzliche Formulierung der weiblichen Form bei Personenbezeichnungen verzichtet. Wir weisen deshalb darauf hin, dass die Verwendung der männlichen Form explizit als geschlechtsunabhängig verstanden werden soll. Das diesem Bericht zugrundeliegende Vorhaben wurde mit Mitteln des Bundesministeriums für Bildung, und Forschung unter dem Förderkennze- ichen 16OH12026 gefördert. Die Verantwortung für den Inhalt dieser Veröf- fentlichung liegt beim Autor. Contents Page3 Contents Introduction to the module books 5 I. Icons and colour codes . 5 Chapter 3 Introduction to Cryptanalysis 7 3.1 Definition of Security . 7 3.1.1 Security of Cryptographic Systems . 7 3.1.2 Categories of Attacks . 8 3.1.3 Categories of Attackers . 9 3.1.4 Secret Key Lengths . 10 3.2 Outline of this Lecture . 11 3.3 Further Reading Materials . 11 Chapter 4 Computational Complexity and Parallelism 13 4.1 Asymptotic Computational Complexity . -

Windows 95, Windows 98, Windows 98SE, and Windows ME Courtesy of Nashville Home Linux Solutions
Important information for users of Windows 95, Windows 98, Windows 98SE, and Windows ME courtesy of Nashville Home Linux Solutions FACT: As of July 2006, Microsoft has officially ended support for Windows 95, Windows 98, Windows 98SE, and Windows ME (Millennium Edition). What does this mean for you? Microsoft©s end-of-support announcement means that users of Windows 95, 98, and ME will no longer receive security updates, bug fixes, and other patches for their computer©s operating system. It also means that future releases of Microsoft software (such as Media Player, Internet Explorer, and Outlook Express) will no longer support these operating systems. Users of these versions of Windows will not benefit from enhanced features and security in these new versions. Why should I be concerned? Windows 95, 98, and ME are based around the DOS operating system, an inherently insecure operating system. Users of DOS-based Windows will become increasingly at risk for viruses, spyware, malware, and system intrusions as new holes and exploits are discovered in these operating systems and the older software that runs on them. In addition, software vendors (including makers of anti-virus and other security products) will be phasing out support for these operating systems now that Microsoft has ended its support. If you are connecting your DOS-based Windows operating system to the Internet, you need to take action to secure your computer. What are my options? If you would like to continue to operate on your current hardware, you have a few options available to you: 1. Upgrade Windows Microsoft©s only currently-available Windows workstation operating system is Windows XP (Home or Professional). -

CS 151: Introduction to Computers
Information Technology: Introduction to Computers Handout One Computer Hardware 1. Components a. System board, Main board, Motherboard b. Central Processing Unit (CPU) c. RAM (Random Access Memory) SDRAM. DDR-RAM, RAMBUS d. Expansion cards i. ISA - Industry Standard Architecture ii. PCI - Peripheral Component Interconnect iii. PCMCIA - Personal Computer Memory Card International Association iv. AGP – Accelerated Graphics Port e. Sound f. Network Interface Card (NIC) g. Modem h. Graphics Card (AGP – accelerated graphics port) i. Disk drives (A:\ floppy diskette; B:\ obsolete 5.25” floppy diskette; C:\Internal Hard Disk; D:\CD-ROM, CD-R/RW, DVD-ROM/R/RW (Compact Disk-Read Only Memory) 2. Peripherals a. Monitor b. Printer c. Keyboard d. Mouse e. Joystick f. Scanner g. Web cam Operating system – a collection of files and small programs that enables input and output. The operating system transforms the computer into a productive entity for human use. BIOS (Basic Input Output System) date, time, language, DOS – Disk Operating System Windows (Dual, parallel development for home and industry) Windows 3.1 Windows 3.11 (Windows for Workgroups) Windows 95 Windows N. T. (Network Technology) Windows 98 Windows N. T. 4.0 Windows Me Windows 2000 Windows XP Home Windows XP Professional The Evolution of Windows Early 80's IBM introduced the Personal PC using the Intel 8088 processor and Microsoft's Disk Operating System (DOS). This was a scaled down computer aimed at business which allowed a single user to execute a single program. Many changes have been introduced over the last 20 years to bring us to where we are now. -

Password Attacks and Generation Strategies
PASSWORD ATTACKS AND GENERATION STRATEGIES Predrag Tasevski Tartu University, Faculty of Mathematics and Computer Sciences, major: Master of Science in Cyber Security May 21, 2011 Table of contents Introduction Methods Ad-hoc models Brute force Rainbow tables Examples and tools Comparison of input dictionary list Test Conclusion INTRODUCTION Password is a secret word or string of characters that is used for authentication in order to prove identity or gain access to a resource[Gill(1997)]. I Usage of password cracking tools I Methods and approaches guessing the passwords I Examples of leaks and generating password dictionaries I Comparison of already cracked passwords from available password dictionaries and I Test METHODS Password cracking is a method of guessing the attack. Types of password cracking methods[Vines(2007)]: I Dictionary I Hybrid I Brute force Ad-hoc models Dictionary attacks - colander rules Example Capitalization the rst letter, adding three digits to the end, changing the letter `a' to `@' etc. Hybrid it adds simple numbers or symbols to the password attempt. Brute force Brute force are fraction of the total words that are made by users creating their passwords. Brute force attacks methods: I Pure brute force [Group(2010)] I Letter frequency analysis attack [Stitson(2003)] I Markov models [Shmatikov Arvind(2005)] I Targeted brute force attacks [WEIR(2010b)] Rainbow tables (1) Rainbow tables are using the reduction functions to create multiple parallel chains within a single "rainbow" table. I Increases the probability of a correct crack for a given table size, the use of multiple reduction functions also greatly increases the speed of look-ups [JeXChen(2011)]. -

How to Handle Rainbow Tables with External Memory
How to Handle Rainbow Tables with External Memory Gildas Avoine1;2;5, Xavier Carpent3, Barbara Kordy1;5, and Florent Tardif4;5 1 INSA Rennes, France 2 Institut Universitaire de France, France 3 University of California, Irvine, USA 4 University of Rennes 1, France 5 IRISA, UMR 6074, France [email protected] Abstract. A cryptanalytic time-memory trade-off is a technique that aims to reduce the time needed to perform an exhaustive search. Such a technique requires large-scale precomputation that is performed once for all and whose result is stored in a fast-access internal memory. When the considered cryptographic problem is overwhelmingly-sized, using an ex- ternal memory is eventually needed, though. In this paper, we consider the rainbow tables { the most widely spread version of time-memory trade-offs. The objective of our work is to analyze the relevance of storing the precomputed data on an external memory (SSD and HDD) possibly mingled with an internal one (RAM). We provide an analytical evalua- tion of the performance, followed by an experimental validation, and we state that using SSD or HDD is fully suited to practical cases, which are identified. Keywords: time memory trade-off, rainbow tables, external memory 1 Introduction A cryptanalytic time-memory trade-off (TMTO) is a technique introduced by Martin Hellman in 1980 [14] to reduce the time needed to perform an exhaustive search. The key-point of the technique resides in the precomputation of tables that are then used to speed up the attack itself. Given that the precomputation phase is much more expensive than an exhaustive search, a TMTO makes sense in a few scenarios, e.g., when the adversary has plenty of time for preparing the attack while she has a very little time to perform it, the adversary must repeat the attack many times, or the adversary is not powerful enough to carry out an exhaustive search but she can download precomputed tables. -

Unit 5 Windows 2000/XP History, and Data Management
Unit 5 Windows 2000/XP History, and Data Management Copyright © 2002 Heathkit Company, Inc. All rights reserved. Microsoft Windows98 Microsoft WindowsMe Microsoft Windows 2000 Professional Microsoft WindowsXP 2 Windows 2000/XP or Windows 9x (95/98/Me)? Windows 9x Windows 2000/XP Runs on today’s Runs on “nearly any hardware, doesn’t run old hardware” well or at all on marginal hardware Secure, more difficult to Open, easy to configure configure Supports lots of Device support somewhat devices limited, so far 3 Windows XP or Windows 9x? If you need: Choose: Reliable, solid security Windows 2000/XP “Crash-proof” system Windows 2000/XP Support for older/slower Windows 9x machines Easy setup and configuration Windows 9x Support for that older scanner, Windows 9x CD Writer, NIC, Video, etc. 4 The Windows Business Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 5 The Windows Business Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 6 The TheWindows Windows Business Universe Consumer Universe 1990 Windows 3.1 Windows NT 3.51 Windows for Workgroups Windows NT 4 Windows 95 Windows 98 Windows 2000 Windows Me Today Windows XP Pro/Home 7 Windows XP Flavors • Windows XP Professional • Windows XP Home • Windows 2003 Server • Windows 2003 Enterprise Server • Windows 2003 Datacenter Server 8 Windows Package Types • Upgrade • Full Version -

Operating System and Device Driver Support for 2004 HP Compaq Business Desktop Computers with the Intel 915 Chipset
Operating System and Device Driver Support for 2004 HP Compaq Business Desktop Computers with the Intel 915 Chipset HP PSG Business PC Group June 2004 (revised 1/25/05) Abstract ............................................................................................................................................ 1 Introduction......................................................................................................................................... 2 Acronyms used .................................................................................................................................... 3 Preinstalled operating system availability by model.................................................................................. 4 Device driver availability by device class................................................................................................ 6 Audio ............................................................................................................................................. 6 Graphics......................................................................................................................................... 6 Networking ..................................................................................................................................... 7 Wireless LAN .................................................................................................................................. 7 Modems......................................................................................................................................... -
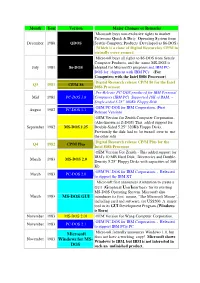
Microsoft Windows for MS
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

L38 Ñ Windows XP
History History (cont.) (Timeline from www.cgonline.com) 10/81 — IBM PC (“Personal Computer”) 10/88 — OS/2 1.1 (Windows-like GUI, end and PC-DOS 1.0 of collaboration when IBM gets upset with Microsoft for improving Windows) 3/83 — Microsoft MS-DOS 2.0 (hard disk, file system) 5/90 — Windows 3.0 (big success!) 11/83 — Windows announced (vaporware!) 4/92 — Windows 3.1 (bug fixes etc.) 11/84 — MS-DOS 3.1 10/92 — Windows for Workgroups 3.1 (adds networking, but fails in market) 11/85 — Windows 1.0 (tiled windows, doesn’t do well in market) 5/93 — Windows NT 3.1 (visually like Windows 3.1, but stable 32-bit platform) 4/87 — IBM & Microsoft OS/2 1.0 (next generation, DOS-like command lines) 11/93 — Windows for Workgroups 3.11 (precursor to Windows 95) 12/87 — Windows/386 (uses 80386’s virtual memory to allow safe “preemptive” 5/94 — MS-DOS 6.22 (DOS final version) multitasking) 9/94 — Windows NT 3.5 6/95 — Windows NT 3.51 (faster) 1 Fall 2002, Lecture 38 2 Fall 2002, Lecture 38 History (cont.) What is Windows XP? 8/95 — Windows 95 (originally Windows I 32/64 -bit preemptive multitasking 4.0) (long file names, plug and play operating system for AMD K6/7, Intel hardware, taskbar and Start menu, IA32/64 and later microprocessors HUGE success in market!) ● Replaces Windows 95/98/Me as well as Windows NT/200 7/96 — Windows NT 4.0 (Windows 95 GUI, first successful version of NT) I Key goals 6/98 — Windows 98 (Windows 95 + ● security, reliability, ease of use Internet Explorer 4.0, success in market) ● Windows and POSIX compliance ● high performance, extensibility 2/00 — Windows 2000 (Windows NT 4.0 + plug and play, DirectX, USB, etc.) ● portability, international support 9/00 — Windows Me (Millennium Edition) I Various versions: XP Personal, XP (Windows 98 + IE 5.0, media support, Professional, XP Server last version in Windows 9x line) I Uses a micro-kernel architecture 9/01 — Windows XP (combines Windows ● Subsystems to provide OS personalities 2000 and ME, but based on NT/2000) for Win32, POSIX, etc. -

MICROSOFT WINDOWS Early Versions Main Articles: Windows 1.0
MICROSOFT WINDOWS Early versions Main articles: Windows 1.0, Windows 2.0, and Windows 2.1x Windows 1.0, the first version, released in 1985 The history of Windows dates back to September 1981, when Chase Bishop, a computer scientist, designed the first model of an electronic device and project "Interface Manager" was started. It was announced in November 1983 (after the Apple Lisa, but before the Macintosh) under the name "Windows", but Windows 1.0 was not released until November 1985.[5] Windows 1.0 achieved little popularity and was to compete with Apple's own operating system. Windows 1.0 is not a complete operating system; rather, it extends MS-DOS. The shell of Windows 1.0 is a program known as the MS- DOS Executive. Components included Calculator, Calendar, Cardfile, Clipboard viewer, Clock, Control Panel, Notepad, Paint, Reversi, Terminal and Write. Windows 1.0 does not allow overlapping windows. Instead all windows are tiled. Only modal dialog boxes may appear over other windows. Windows 2.0 was released in December 1987 and was more popular than its predecessor. It features several improvements to the user interface and memory management.[citation needed] Windows 2.03 changed the OS from tiled windows to overlapping windows. The result of this change led to Apple Computer filing a suit against Microsoft alleging infringement on Apple's copyrights.[6][7] Windows 2.0 also introduced more sophisticated keyboard shortcuts and could make use of expanded memory. Windows 2.1 was released in two different versions: Windows/286 and Windows/386. Windows/386 uses the virtual 8086 mode of Intel 80386 to multitask several DOS programs and the paged memory model to emulate expanded memory using available extended memory. -

IAARAAA-AAYCQHDJ-EYWHPWL Serial Id : 6MKGY7-V7H2UBDZ
Style Xp MMy HHaardrdwwarare Id :: IIAAAARARAAAA-A-AAAAYYCQCQHHDJDJ--EEYWYWHPHPWWLL SSeerriiaal idd :: 66MMKKGGYY77--VV77HH22UUBBDDZZ--77KKCCUU33YYLLSS--AAWW55LL66TTNN88--NNZZTTPPMMEEWWYY--33 NERO 6.6 CD KEYS: 1. 1A21-0009-3030-2203-0668-4234 2. 1A23-0009-9030-2278-0306-3602 nEnERO eXeXPRPRESESS 66 : 1A1A2020-0-010100-0-00000000-1-170706-6-45458989-4-4949488 IF THERE IS A PROBLEM REFER TO FILES WITH EXTENSION : README.TXT, INSTALL.TXT, COMMENTS.TXT, diz, nfo, txt & no FOR INSTALLATION AND SERIAL NO ================================================================================== =============== WWIINNDDOOWWS XXPP : FFCCKKGGWW--RRHHQQQQ22--YYXXRRKKTT--88TTGG66WW--22BB77QQ88 WWIINNDDOOWWS MMEE : JJFFWWPP33--NNGGIIOO44--DD66882211--KK5577JJYY--JJGGRRMMGG WWIINNDDOOWWSS--22000000 : RRBBDDCC99--VVTTRRCC88--DD77997722--JJ9977JJYY--PPRRVVMMGG WINDOWS-2K SERVER : RBDC9-VTRC8-D7972-J97JY-CJ97JY-PRVMG WWIINNDDOOWWSS''9988 : KK44HHVVDD--QQ99TTJJ99--66CCRRXX99--CC99GG6688--RRQQ22DD33 : R4MVV-PQV8M-8WBG6-8VXC7-DCW48 WWIINNDDOOWWSS''998 SSEE : HHQQ66KK22--QQPPCC4422--33HHWWDDMM--BBFF44KKJJ--WW44XXWWJJ : PYDMY-DVJ9J-996VH-JX66P-9TWKW WWIINNDDOOWWSS''9977 : 011000000--OOEEMM--00112233445566--0011110000 : 19195-OEM-0002397-21994 WWIINNDDOOWWSS''9955 : 155669955--OOEEMM--00000011334466--0000888811 ================================================================================== =============== NT 4.0 WKS : 09496-OEM-0009552-77303 : 21599-OEM-0043491-94713 NT 4.0 SERV : 313-0224805 ==================================================================================