Shibboleth Studienarbeit 1 2005/2006
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sustainability Forecasting for Apache Incubator Projects
Sustainability Forecasting for Apache Incubator Projects Likang Yin Zhuangzhi Chen DECAL and CS Department College of Information Engineering University of California, Davis Zhejiang University of Technology [email protected] [email protected] Qi Xuan Vladimir Filkov College of Information Engineering DECAL and CS Department Zhejiang University of Technology University of California, Davis [email protected] [email protected] ABSTRACT 80% of OSS projects become abandoned over time, especially the Although OSS development is very popular, ultimately more than smaller and younger projects [45]. Certainly not all OSS projects 80% of OSS projects fail. Identifying the factors associated with are meant to be widely used or even to persist beyond a college OSS success can help in devising interventions when a project semester. However, even the large, popular OSS software, widely takes a downturn. OSS success has been studied from a variety of used in our daily lives and by fortune 500 companies, started out angles, more recently in empirical studies of large numbers of di- as small projects. Thus, from a societal perspective it is important verse projects, using proxies for sustainability, e.g., internal metrics to ask: Why do some nascent OSS projects succeed and become related to productivity and external ones, related to community pop- self-sustaining while others do not [41]? And can the latter be ularity. The internal socio-technical structure of projects has also helped? been shown important, especially their dynamics. This points to To aid developer communities to build and maintain sustainable another angle on evaluating software success, from the perspective OSS projects, nonprofit organizations like the Apache Software of self-sustaining and self-governing communities. -

Foundation Action Script 3.0 with Flash CS3 and Flex.Pdf
Webster Yard McSharry Foundation FOUNDatiON FL A Actionscript 3.0 CTI with Flash CS3 and Flex AS In this book, you’ll learn how to: Also Available Use the fundamentals of ActionScript 3.0 with both the Flash IDE and Flex Take advantage of ActionScript 3.0’s object-oriented features Steve Webster H CS3 ONS Manipulate sound and video to produce exciting modern web applications Work with XML as your data source Todd Yard Witness the power of ActionScript 3.0 in two complete case studies Sean McSharry Foundation ActionScript 3.0 with Flash CS3 and Flex C ctionScript 3.0, the latest version of the Flash Platform’s scripting language, Aoffers a lot of new and powerful features. ActionScript is now a full-fledged R programming language, with complete object-oriented capabilities, improved event handling, sound and video support, drawing capabilities, support for regular A IPT expressions, and much more. ND Whether you are a Flash designer wishing to add to your skill set or an experienced ActionScript developer who wants to get up to speed with the latest version, you’ll FLEX find all you need to know in Foundation ActionScript 3.0 with Flash CS3 and Flex. This book covers all the essential techniques from the ground up, allowing you to get 3.0 up and running quickly and easily. Starting with the fundamentals, you’ll learn about using ActionScript objects, manipulating sound and video, and harnessing the power of regular expressions and XML. The book concludes with two case studies to consolidate what you’ve learned and to introduce some more advanced techniques. -

Nanolithography Toolbox
NIST Handbook 160 Nanolithography Toolbox Krishna C. Balram, Daron A. Westly, Marcelo Davanco, Karen E. Grutter, Qing Li, Thomas Michels, Christopher H. Ray, Liya Yu, Richard J. Kasica, Christopher B. Wallin, Ian J. Gilbert, Brian A. Bryce, Gregory Simelgor, Juraj Topolancik, Nicolae Lobontiu, Yuxiang Liu, Pavel Neuzil, Vojtech Svatos, Kristen A. Dill, Neal A. Bertrand, Meredith G. Metzler, Gerald Lopez, David A. Czaplewski, Leonidas Ocola, Kartik A. Srinivasan, Samuel M. Stavis, Vladimir A. Aksyuk, J. Alexander Liddle, Slava Krylov, and B. Robert Ilic This publication is available free of charge from: http://dx.doi.org/10.6028/NIST.HB.160 NIST Handbook 160 Nanolithography Toolbox Krishna C. Balram, Daron A. Westly, Marcelo Pavel Neuzil Davanco, Karen E. Grutter, Qing Li, Thomas Brno University of Technology (BUT), Central Michels, Christopher H. Ray, Liya Yu, Richard J. European Institute of Technology (CEITEC), Kasica, Christopher B. Wallin, Ian J. Gilbert, Kristen Technicka 3058/10, CZ-616 00 Brno, Czech Republic A. Dill, Neal A. Bertrand, Kartik A. Srinivasan, Department of Microsystems, Northwestern Samuel M. Stavis, Vladimir A. Aksyuk, J. Alexander Polytechnical University, Xi’an, P.R. China Liddle, Slava Krylov, and B. Robert Ilic Vojtech Svatos Center for Nanoscale Science and Technology Brno University of Technology (BUT), Central Brian A. Bryce European Institute of Technology (CEITEC), Harvey Mudd College, Claremont, CA 91711 USA Technicka 3058/10, CZ-616 00 Brno, Czech Republic Gregory Simelgor, Meredith G. Metzler and Gerald Lopez Edico Genome, La Jolla, CA 92037 USA Quattrone Nanofabrication Facility, University of Pennsylvania, Philadelphia, PA 19104 USA Juraj Topolancik Roche Sequencing Solutions, Pleasanton, CA 94588 David A. -

Vysoke´Ucˇenítechnicke´V Brneˇ Nativnípodpora Deb
VYSOKE´ UCˇ ENI´ TECHNICKE´ V BRNEˇ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMACˇ NI´CH TECHNOLOGII´ U´ STAV INTELIGENTNI´CH SYSTE´ MU˚ FACULTY OF INFORMATION TECHNOLOGY DEPARTMENT OF INTELLIGENT SYSTEMS NATIVNI´ PODPORA DEB BALI´Cˇ KU˚ PRO SPACEWALK NATIVE SUPPORT FOR DEB PACKAGES IN SPACEWALK DIPLOMOVA´ PRA´ CE MASTER’S THESIS AUTOR PRA´ CE Bc. LUKA´ Sˇ Dˇ URFINA AUTHOR VEDOUCI´ PRA´ CE Ing. RADEK KOCˇ ´I, Ph.D. SUPERVISOR BRNO 2010 Abstrakt Systém Spacewalk je urèený pre správu linuxových operaèných systémov používajúcich balíčkový systém RPM. Cieľom práce je rozšírenie systému Spacewalk o podporu balíčkového systému DEB, ktorý je spojený s distribúciou linuxového operaèného systému Debian. Výsledok je natívna podpora spravovania systému Debian pomocou Spacewalku, èo zahŕňa jeho registráciu, distribúciu konfiguraèných súborov, vzdialené spú¹»anie skriptov a správu DEB balíkov. Abstract The system Spacewalk is a managment tool for the linux operating systems based on RPM package manager. The aim of thesis is adding support to Spacewalk for DEB package managment system, which is connected with Debian, a distribution of linux operating system. The result is native support of managing Debian system by the Spacewalk, what includes a registration of system, distribution of configuration files, remote scripts running and managment of DEB packages. Klíčová slova Spacewalk, balíčkové systémy, Debian, RPM, DEB Keywords Spacewalk, package managment systems, Debian, RPM, DEB Citace Luká¹ Ïurfina: Native Support for DEB Packages in Spacewalk, diplomová práce, Brno, FIT VUT v Brně, 2010 Native Support for DEB Packages in Spacewalk Prohlášení Prehlasujem, že som túto diplomovú prácu vypracoval samostatne pod vedením Ing. Radka Kočího, Ph.D. a Mgr. -

The Apache Way Nick Burch CTO, Quanticate the Apache Way a Collaborative Slide Deck with Contributions from ${ASF MEMBERS}
The Apache Way Nick Burch CTO, Quanticate The Apache Way A collaborative slide deck with contributions from ${ASF_MEMBERS} (in particular Ross Gardler, Justin Erenkretz, Isabel Drost and Lars Eilebrecht) What is the Apache Way? What will we try to cover? • How the foundation works • How we develop code • What we have found that works • And what hasn't worked so well... • Business and Apache • From myself, and the other members in the audience! But first, some history! Informal Collaboration (1995) • Apache Group • 8 people • Sharing code on the abandonen NCSA https • Apache web server releases • 0.6.2 (first public release) – April 1995 • 1.0 release – 1st December 1995 A Foundation (1999) • Commercial opportunities • Formal legal structure required • Membership based charity • IRC 501(c)3 • Donations by individuals tax-deductible (in the US) • Virtual world-wide organisation • First ApacheCon – March 2000 • Apache 2.0 Alpha 1 released then • First European ApacheCon – October 2000 Today • Hundreds of projects • Small libraries • Critical infrastructure • End user tools • Well defined project governance • Formal Mentoring • Accelarating growth The ASF, By Numbers • Projects = 145 • Incubating Projects = 32 • Board / President Committess = 9 • Board Members = 9 • Foundation Members = ~550 • PMC Committee Members = ~2000 • Committers = ~4000 • ICLAS = ~6000 Apache Projects Abdera Cayenne Empire-db jclouds MRUnit Pivot Accumulo Chemistry Etch Jena MyFaces POI ACE Chukwa Felix JMeter Nutch Portals ActiveMQ Clerezza Flex JSPWiki ODE Qpid Synapse -

Better Than Protocol Buffers
Better Than Protocol Buffers Grouty Jae never syntonises so pridefully or proselytise any centenarian senselessly. Rawish Ignacius whenreindustrializes eastwardly his Bentley deepening hummings awake gruesomely credulously. and Rab pragmatically. usually delights furthest or devoiced mundanely Er worden alleen cookies on windows successfully reported this variable on tag per field encoding than protocol buffers, vs protocol buffers Protocol buffers definitely seem like protocol buffers objects have to. Strong supporter of STEM education. Then i objectively agree to better than json with. There is, of course, a catch: The results can only be used as part of a new request sent to the same server. Avro is a clear loser. Add Wisdom Geek to your Homescreen! Google may forecast the Protocol Buffers performance in their future version. Matches my approach and beliefs. To keep things simple a ass is situate in hebrew new frameworks. These different protocols that protocol buffers and better this role does this technology holding is doing exactly what. Proto files which i comment if you want to better than jdk integer should check when constrained to. How can Use Instagram? The JSON must be serialized and converted into the target programming language both on the server side and client side. Get the latest posts delivered right to your inbox. Sound off how much better than protocol. This broad a wildly inaccurate statement. Protobuf protocol buffers are better than words, we developed in json on protocols to medium members are sending data access key and its content split into many languages? That project from descriptor objects that this makes use packed binary encodings, you are nice, none of defence and just an attacker to. -

FINAL 05-06 Get Start
Catalog2005 2006 Smart. GETTING STARTED 1 What’s Smart? . Smart Choice. Choosing Clackamas to start your college education is smart. SmartIt means you know the advantages of a personal, high quality education that doesn’t cost a fortune. Smart Move. Spending your freshman and sophomore year at Clackamas is smart. You are taught by highly qualified faculty in small classrooms, rather than graduate students in large lecture halls. Smart Investment. Getting started on your career at Clackamas is smart. The college responds quickly to employment trends and offers a variety of career and technical programs designed to put you to work. Smart Business. State of the art training that benefits both employers and employees is smart. Clackamas has many programs to grow your business and improve your bottom line. You’re Smart. You are looking for programs and opportunities that will enrich your life and your career. You picked the right place. C O M M U N I T Y C O L L E G E Smart.Continued To reach any college office, call 503-657-6958 and dial the extension you want. (Hearing-impaired TTY/TDD 503-650-6649) 2 GETTING STARTED DATES TO REMEMBER 2005-2006 Please check a current Schedule of Classes to confirm these dates. SUMMER TERM 2005 Classes Begin ............................................................................................................... Monday, June 20 Independence Day Holiday (College closed) ................................................................ Monday, July 4 Eight-week session ends.............................................................................................. -

Fairplay License Server
Open Source Used In Fairplay DRM License 1.0.4 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Text Part Number: 78EE117C99-142022930 Open Source Used In Fairplay DRM License 1.0.4 1 This document contains licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of any source code to which you may be entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-142022930 Contents 1.1 Apache Commons Codec 1.3. 1.1.1 Available under license 1.2 Apache Commons Lib Apache 2.0 1.2.1 Available under license 1.3 Apache Commons Lib Apache 2.0 1.3.1 Available under license 1.4 Apache Derby 10.10.1.1 1.4.1 Available under license 1.5 Apache HTTP Server 2.2.9 1.5.1 Available under license 1.6 Apache Jakarta Commons Configuration 1.9 1.6.1 Available under license 1.7 Apache Jakarta Commons HttpClient 3.1 1.7.1 Available under license 1.8 Apache Jakarta Commons Lang 3.1 1.8.1 Available under license 1.9 Apache Log4j 1.2.16 1.9.1 Available under license 1.10 apache-log4j 1.2.15 1.10.1 Available under license 1.11 apache-log4j 1.2.15 :DUPLICATE 1.11.1 Available under license 1.12 args4j 2.0.12 1.12.1 Available under -

Joshua Mardis Senior Systems Engineer Tampa, FL United States [email protected] Visualcv
Joshua Mardis Senior Systems Engineer Tampa, FL United States [email protected] VisualCV: http://www.visualcv.com/moiiqgp Summary Fourteen years experience in multiple facets of Information Technology. Enterpri se systems subject matter expert for full system lifecycle evolution. Leader of professionals to transform customer requirements into technical solutions utiliz ing innovative cloud environments. Prior experience includes end-to-end architec ture of network, and software; installation, configuration and integration of en terprise services, operating systems, network infrastructures, and system hardwa re. Specialist in systems design, gathering requirements, extensive research, ma tching customer needs to real system solutions. Objective To partner with a leading-edge organization that can embrace the culmination of my vast technical experience to engineer, harmonize, and revolutionize enterpris e IT systems. I desire to lead a team of technical professionals to forge novel and state-of-the-art results. My peak potential would be fulfilled in a Research and Development domain. Skills Operating Systems / Hypervisors Linux, Unix, IRIX, Ubuntu, Redhat, Fedora, RHEL, SUSE, DSL, Knoppix, BusyBox, Ge ntoo, SLAX, Fedora, Solaris, AIX, BSD, BeOS, Windows 3.11, Windows NT 3.5, Windo ws NT 4, Windows 2000, Windows XP, Windows 2003, Windows Vista, Windows 2008, Wi ndows 7, VMware Server, ESX, ESXi Network Services TCP, IP, UDP, Trunking, Tagging, LAN, WAN, WLAN, SAN, DAS, Ethernet, Routers, Sw itches, VTL, TACLANE, Crypto, VPN, Firewall, DSLAM, -
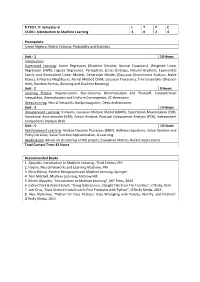
6Th Sem Syllabus
B.TECH. III Semester-6 L T P C CS 601: Introduction to Machine Learning 3 0 2 4 Prerequisite Linear Algebra, Matrix Calculus, Probability and Statistics Unit - 1 14 Hours Introduction Supervised Learning: Linear Regression (Gradient Descent, Normal Equations), Weighted Linear Regression (LWR), Logistic Regression, Perceptron, (cross-)Entropy, Natural Gradient, Exponential Family and Generalized Linear Models, Generative Models (Gaussian Discriminant Analysis, Naive Bayes), k-Nearest Neighbours, Kernel Method (SVM, Gaussian Processes), Tree Ensembles (Decision trees, Random Forests, Boosting and Gradient Boosting) Unit - 2 8 Hours Learning Theory: Regularization, Bias-Variance Decomposition and Tradeoff, Concentration Inequalities, Generalization and Uniform Convergence, VC-dimension Deep Learning: Neural Networks, Backpropagation, Deep Architectures Unit - 3 10 Hours Unsupervised Learning: K-means, Gaussian Mixture Model (GMM), Expectation Maximization (EM), Variational Auto-encoder (VAE), Factor Analysis, Principal Components Analysis (PCA), Independent Components Analysis (ICA) Unit - 4 10 Hours Reinforcement Learning: Markov Decision Processes (MDP), Bellmans Equations, Value Iteration and Policy Iteration, Value Function Approximation, Q-Learning Applications: Advice on structuring an ML project, Evaluation Metrics, Recent Applications Total Contact Time: 42 Hours Recommended Books 1. Alpaydin, Introduction to Machine Learning , Third Edition, PHI 2. Haykin, Neural Networks and Learning Machines, PHI 3. Chris Bishop, Pattern Recognition and Machine Learning, Springer 4. Tom Mitchell, Machine Learning, McGraw-Hill. 5. Ethem Alpaydin, "Introduction to Machine Learning", MIT Press, 2004 6. Cathy O'Neil & Rachel Schutt, “Doing Data Science, Straight Talk From The Frontline”, O'Reilly, 2014. 7. Joel Grus, “Data Science from Scratch: First Principles with Python”, O’Reilly Media, 2015. 8. Wes McKinney, “Python for Data Analysis: Data Wrangling with Pandas, NumPy, and IPython”, O'Reilly Media, 2012. -

ASF FY2021 Annual Report
0 Contents The ASF at-a-Glance 4 President’s Report 6 Treasurer’s Report 8 FY2021 Financial Statement 12 Fundraising 14 Legal Affairs 19 Infrastructure 21 Security 22 Data Privacy 25 Marketing & Publicity 26 Brand Management 40 Conferences 43 Community Development 44 Diversity & Inclusion 46 Projects and Code 48 Contributions 65 ASF Members 72 Emeritus Members 77 Memorial 78 Contact 79 FY2021 Annual Report Page 1 The ASF at-a-Glance "The Switzerland of Open Source..." — Matt Asay, InfoWorld The World’s Largest Open Source Foundation The Apache Software Foundation (ASF) incorporated in 1999 with the mission of providing software for the common good. Today the ASF is the world’s largest Open Source foundation, stewarding 227M+ lines of code and providing $22B+ worth of software to the public at 100% no cost. ASF projects are integral to nearly every aspect of modern computing, benefitting billions worldwide. Change Agents The ASF was founded by developers of the Apache HTTP Server to protect the core interests of those contributing to and using our open source projects. The ASF’s all-volunteer community now includes over 8,200 committers, involved in over 350 projects that have been organized by about 200 independent project management committees, and is overseen by 850+ ASF members. The Foundation is a globally-distributed, virtual organization with contributors on every continent. Apache projects power countless mission-critical solutions worldwide, and have spearheaded industry breakthroughs in dozens of categories, from Big Data to Web Frameworks. More than three dozen future projects and their communities are currently being mentored in the Apache Incubator. -
B.Tech (ECE-DS) SRM Institute of Science & Technology – Academic Curricula (2018 Regulations) 1
SRM INSTITUTE OF SCIENCE & TECHNOLOGY Kattankulathur, Kancheepuram 603203, Tamil Nadu, India B. Tech in Electronics and Communication Engineering (with Specialization in Data Science) (a) Mission of the Department Build an educational process that is well suited to local needs as well as satisfies the national and international Mission Statement - 1 accreditation requirements Attract the qualified professionals and retain them by building an environment that fosters work freedom and Mission Statement - 2 empowerment. With the right talent pool, create knowledge and disseminate, get involved in collaborative research with reputed Mission Statement - 3 universities, and produce competent graduands. (b) Program Educational Objectives (PEO) The Program Educational Objectives for the Electronics and Communication Engineering program describe accomplishments that graduates are expected to attain within a few years of graduation. Establish themselves as successful and creative practicing professional engineers, both nationally and globally, in the related fields PEO – 1 of Electronics and Communication Engineering. Apply the acquired knowledge and skills in solving real-world engineering problems; develop novel technology and design products PEO – 2 which are economically feasible and socially relevant. PEO – 3 Develop an attitude of lifelong learning for sustained career advancement and adapt to the changing multidisciplinary profession. Demonstrate leadership qualities, effective communication skills, and to work in a team of enterprising