Dropdmg 2.6 Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
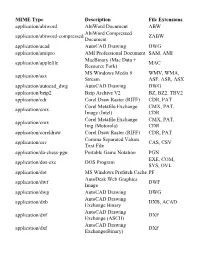
MIME Type Description File Extensions Application/Abiword
MIME Type Description File Extensions application/abiword AbiWord Document ABW AbiWord Compressed application/abiword-compressed ZABW Document application/acad AutoCAD Drawing DWG application/amipro AMI Professional Document SAM, AMI MacBinary (Mac Data + application/applefile MAC Resource Fork) MS Windows Media 9 WMV, WMA, application/asx Stream ASF, ASR, ASX application/autocad_dwg AutoCAD Drawing DWG application/bzip2 Bzip Archive V2 BZ, BZ2, TBV2 application/cdr Corel Draw Raster (RIFF) CDR, PAT Corel Metafile Exchange CMX, PAT, application/cmx Image (Intel) CDR Corel Metafile Exchange CMX, PAT, application/cmx Img (Motorola) CDR application/coreldraw Corel Draw Raster (RIFF) CDR, PAT Comma Separated Values application/csv CAS, CSV Text File application/da-chess-pgn Portable Game Notation PGN EXE, COM, application/dos-exe DOS Program SYS, OVL application/dot MS Windows Prefetch Cache PF AutoDesk Web Graphics application/dwf DWF Image application/dwg AutoCAD Drawing DWG AutoCAD Drawing application/dxb DXB, ACAD Exchange Binary AutoCAD Drawing application/dxf DXF Exchange (ASCII) AutoCAD Drawing application/dxf DXF Exchange(Binary) EMF, TMP, EMF, TMP, application/emf Windows Enhanced Metafile WMF application/envoy Envoy Document EVY, ENV Comma Separated Values application/excel CAS, CSV Text File MS Excel XLS, XLA, application/excel Worksheet/Add-In/Template XLT, XLB EXE, COM, application/exe DOS Program SYS, OVL EXE, VXD, application/exe MS Windows Driver (16 bit) SYS, DRV, 386 MS Windows Program (16 application/exe EXE, MOD, BIN bit) -

ACS – the Archival Cytometry Standard
http://flowcyt.sf.net/acs/latest.pdf ACS – the Archival Cytometry Standard Archival Cytometry Standard ACS International Society for Advancement of Cytometry Candidate Recommendation DRAFT Document Status The Archival Cytometry Standard (ACS) has undergone several revisions since its initial development in June 2007. The current proposal is an ISAC Candidate Recommendation Draft. It is assumed, however not guaranteed, that significant features and design aspects will remain unchanged for the final version of the Recommendation. This specification has been formally tested to comply with the W3C XML schema version 1.0 specification but no position is taken with respect to whether a particular software implementing this specification performs according to medical or other valid regulations. The work may be used under the terms of the Creative Commons Attribution-ShareAlike 3.0 Unported license. You are free to share (copy, distribute and transmit), and adapt the work under the conditions specified at http://creativecommons.org/licenses/by-sa/3.0/legalcode. Disclaimer of Liability The International Society for Advancement of Cytometry (ISAC) disclaims liability for any injury, harm, or other damage of any nature whatsoever, to persons or property, whether direct, indirect, consequential or compensatory, directly or indirectly resulting from publication, use of, or reliance on this Specification, and users of this Specification, as a condition of use, forever release ISAC from such liability and waive all claims against ISAC that may in any manner arise out of such liability. ISAC further disclaims all warranties, whether express, implied or statutory, and makes no assurances as to the accuracy or completeness of any information published in the Specification. -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -
![User Commands GZIP ( 1 ) Gzip, Gunzip, Gzcat – Compress Or Expand Files Gzip [ –Acdfhllnnrtvv19 ] [–S Suffix] [ Name ... ]](https://docslib.b-cdn.net/cover/1609/user-commands-gzip-1-gzip-gunzip-gzcat-compress-or-expand-files-gzip-acdfhllnnrtvv19-s-suffix-name-561609.webp)
User Commands GZIP ( 1 ) Gzip, Gunzip, Gzcat – Compress Or Expand Files Gzip [ –Acdfhllnnrtvv19 ] [–S Suffix] [ Name ... ]
User Commands GZIP ( 1 ) NAME gzip, gunzip, gzcat – compress or expand files SYNOPSIS gzip [–acdfhlLnNrtvV19 ] [– S suffix] [ name ... ] gunzip [–acfhlLnNrtvV ] [– S suffix] [ name ... ] gzcat [–fhLV ] [ name ... ] DESCRIPTION Gzip reduces the size of the named files using Lempel-Ziv coding (LZ77). Whenever possible, each file is replaced by one with the extension .gz, while keeping the same ownership modes, access and modification times. (The default extension is – gz for VMS, z for MSDOS, OS/2 FAT, Windows NT FAT and Atari.) If no files are specified, or if a file name is "-", the standard input is compressed to the standard output. Gzip will only attempt to compress regular files. In particular, it will ignore symbolic links. If the compressed file name is too long for its file system, gzip truncates it. Gzip attempts to truncate only the parts of the file name longer than 3 characters. (A part is delimited by dots.) If the name con- sists of small parts only, the longest parts are truncated. For example, if file names are limited to 14 characters, gzip.msdos.exe is compressed to gzi.msd.exe.gz. Names are not truncated on systems which do not have a limit on file name length. By default, gzip keeps the original file name and timestamp in the compressed file. These are used when decompressing the file with the – N option. This is useful when the compressed file name was truncated or when the time stamp was not preserved after a file transfer. Compressed files can be restored to their original form using gzip -d or gunzip or gzcat. -

Software to Extract Cab Files
Software to extract cab files click here to download You can use WinZip to extract CAB files by following the steps listed below. file extension associated with WinZip program, just double-click on the file. PeaZip offers read-only support (open and extract cab files) for Microsoft Cabinet file format, providing a free alternative utility to open (list content) and www.doorway.ru packages, or disassemble single files from the container, under Windows and Linux operating systems. Moreover, the OS can create, extract, or rebuild cab files. This means you do not require any additional third-party software for this task. All CAB. For a number of years, Microsoft has www.doorway.ru files to compress software that was distributed on disks. Originally, these files were used to minimize the number . The InstallShield installer program makes files with the CAB However, you can also open or extract CAB files with a file decompression tool. Open, browse, extract, or view Microsoft CAB files with Altap Salamander File Manager. High quality software with emphasis on error states. Affordable cost: . Microsoft uses cab files to package software programs. You can view the contents of a cab file by unzipping it and extracting its contents to a. Hi, I need some help www.doorway.ru files. I have to extract a patch for one game, so i used universal extractor for to extract www.doorway.ru Now I have to. cab Extension - List of programs that can www.doorway.ru files. www.doorway.ru, Inventoria Stock Manager, NCH Software, Extract with Express Zip, Low. -

The Ark Handbook
The Ark Handbook Matt Johnston Henrique Pinto Ragnar Thomsen The Ark Handbook 2 Contents 1 Introduction 5 2 Using Ark 6 2.1 Opening Archives . .6 2.1.1 Archive Operations . .6 2.1.2 Archive Comments . .6 2.2 Working with Files . .7 2.2.1 Editing Files . .7 2.3 Extracting Files . .7 2.3.1 The Extract dialog . .8 2.4 Creating Archives and Adding Files . .8 2.4.1 Compression . .9 2.4.2 Password Protection . .9 2.4.3 Multi-volume Archive . 10 3 Using Ark in the Filemanager 11 4 Advanced Batch Mode 12 5 Credits and License 13 Abstract Ark is an archive manager by KDE. The Ark Handbook Chapter 1 Introduction Ark is a program for viewing, extracting, creating and modifying archives. Ark can handle vari- ous archive formats such as tar, gzip, bzip2, zip, rar, 7zip, xz, rpm, cab, deb, xar and AppImage (support for certain archive formats depends on the appropriate command-line programs being installed). In order to successfully use Ark, you need KDE Frameworks 5. The library libarchive version 3.1 or above is needed to handle most archive types, including tar, compressed tar, rpm, deb and cab archives. To handle other file formats, you need the appropriate command line programs, such as zipinfo, zip, unzip, rar, unrar, 7z, lsar, unar and lrzip. 5 The Ark Handbook Chapter 2 Using Ark 2.1 Opening Archives To open an archive in Ark, choose Open... (Ctrl+O) from the Archive menu. You can also open archive files by dragging and dropping from Dolphin. -

File Management Tools
File Management Tools ● gzip and gunzip ● tar ● find ● df and du ● od ● nm and strip ● sftp and scp Gzip and Gunzip ● The gzip utility compresses a specified list of files. After compressing each specified file, it renames it to have a “.gz” extension. ● General form. gzip [filename]* ● The gunzip utility uncompresses a specified list of files that had been previously compressed with gzip. ● General form. gunzip [filename]* Tar (38.2) ● Tar is a utility for creating and extracting archives. It was originally setup for archives on tape, but it now is mostly used for archives on disk. It is very useful for sending a set of files to someone over the network. Tar is also useful for making backups. ● General form. tar options filenames Commonly Used Tar Options c # insert files into a tar file f # use the name of the tar file that is specified v # output the name of each file as it is inserted into or # extracted from a tar file x # extract the files from a tar file Creating an Archive with Tar ● Below is the typical tar command used to create an archive from a set of files. Note that each specified filename can also be a directory. Tar will insert all files in that directory and any subdirectories. tar cvf tarfilename filenames ● Examples: tar cvf proj.tar proj # insert proj directory # files into proj.tar tar cvf code.tar *.c *.h # insert *.c and *.h files # into code.tar Extracting Files from a Tar Archive ● Below is the typical tar command used to extract the files from a tar archive. -

K.2 Firmware Updater Technical Note
K.2 Series Active Loudspeakers Technical Notes K.2 Firmware Updater—Mac OS Installation Purpose: This Technical Note is for users who get an error message from the Mac Operating System (Mac OS) when attempting to install the K2Updater-2.0.1-osx-installer app. The error message recommends deletion of the app. If the K2Updater-2.0.1-osx-installer app was successfully downloaded, extracted, and installed, this document is unnecessary. If the error message appears when you double-click on the K2Updater-2.0.1-osx-installer app, use the following procedure to work around it and successfully install the K.2 Firmware updater. Software required: • Internet browser (Safari, Firefox, Chrome, etc.) • K2Updater-2.0.1-osx-installer.tar.gz MacOS utilities required: • Archive Utility • Terminal Utility Using Terminal to enable the K.2 Update Installer NOTE: If you have not done so already, download and extract the fileK2Updater-2.0.1-osx-installer.tar.gz from the K.2 firmware update page at www.qsc.com. The Terminal app in the Mac OS is similar to the Command Prompt (CMD) app in Windows. By accessing the OS shell, it allows changes at the root level that allow the K2Updater-2.0.1-osx-installer.app to run. Revision A—8 April 2020 1 K.2 Series Active Loudspeakers Technical Notes K.2 Firmware Updater—Mac OS Installation 1. Open the folder Applcations/Go/Utilities/Terminal. Double-click Terminal to launch. 2. In the Terminal window at the prompt, type xattr<space>-cr<space> but do not press Return yet. -

UNIX (Solaris/Linux) Quick Reference Card Logging in Directory Commands at the Login: Prompt, Enter Your Username
UNIX (Solaris/Linux) QUICK REFERENCE CARD Logging In Directory Commands At the Login: prompt, enter your username. At the Password: prompt, enter ls Lists files in current directory your system password. Linux is case-sensitive, so enter upper and lower case ls -l Long listing of files letters as required for your username, password and commands. ls -a List all files, including hidden files ls -lat Long listing of all files sorted by last Exiting or Logging Out modification time. ls wcp List all files matching the wildcard Enter logout and press <Enter> or type <Ctrl>-D. pattern Changing your Password ls dn List files in the directory dn tree List files in tree format Type passwd at the command prompt. Type in your old password, then your new cd dn Change current directory to dn password, then re-enter your new password for verification. If the new password cd pub Changes to subdirectory “pub” is verified, your password will be changed. Many systems age passwords; this cd .. Changes to next higher level directory forces users to change their passwords at predetermined intervals. (previous directory) cd / Changes to the root directory Changing your MS Network Password cd Changes to the users home directory cd /usr/xx Changes to the subdirectory “xx” in the Some servers maintain a second password exclusively for use with Microsoft windows directory “usr” networking, allowing you to mount your home directory as a Network Drive. mkdir dn Makes a new directory named dn Type smbpasswd at the command prompt. Type in your old SMB passwword, rmdir dn Removes the directory dn (the then your new password, then re-enter your new password for verification. -

An Analysis of XML Compression Efficiency
An Analysis of XML Compression Efficiency Christopher J. Augeri1 Barry E. Mullins1 Leemon C. Baird III Dursun A. Bulutoglu2 Rusty O. Baldwin1 1Department of Electrical and Computer Engineering Department of Computer Science 2Department of Mathematics and Statistics United States Air Force Academy (USAFA) Air Force Institute of Technology (AFIT) USAFA, Colorado Springs, CO Wright Patterson Air Force Base, Dayton, OH {chris.augeri, barry.mullins}@afit.edu [email protected] {dursun.bulutoglu, rusty.baldwin}@afit.edu ABSTRACT We expand previous XML compression studies [9, 26, 34, 47] by XML simplifies data exchange among heterogeneous computers, proposing the XML file corpus and a combined efficiency metric. but it is notoriously verbose and has spawned the development of The corpus was assembled using guidelines given by developers many XML-specific compressors and binary formats. We present of the Canterbury corpus [3], files often used to assess compressor an XML test corpus and a combined efficiency metric integrating performance. The efficiency metric combines execution speed compression ratio and execution speed. We use this corpus and and compression ratio, enabling simultaneous assessment of these linear regression to assess 14 general-purpose and XML-specific metrics, versus prioritizing one metric over the other. We analyze compressors relative to the proposed metric. We also identify key collected metrics using linear regression models (ANOVA) versus factors when selecting a compressor. Our results show XMill or a simple comparison of means, e.g., X is 20% better than Y. WBXML may be useful in some instances, but a general-purpose compressor is often the best choice. 2. XML OVERVIEW XML has gained much acceptance since first proposed in 1998 by Categories and Subject Descriptors the World-Wide Web Consortium (W3C). -

Desktop Security
JPL Informat'1" I Desktop Security Alan Stepakoff lClS - Desktop Services January 14,2004 JPL lnformatio-” ill*--- Interoperable Computing Environment UWindows 2000, XP +=5500 UMac OS 9, 1O.x += 1800 ULinux Red Hat 8, 9 +=150 orrnatio Desktop Configuration Standard Interoperable Environment MS Word Norton Anti-Virus (F-Prof) PowerPoint Meeting Maker Excel QuickTime player Netscape Real Player Acrobat Reader Timbuktu (VNC) Eudora Stuffit (TAR) SMS or Netoctopus Systems are configured to a standard set of Protective Measures + JPL specific security requirements in-line with NASA regulations + Separate Protective Measure for each OS JPL lnforr_ ” - i_*- User Privileges II Authorization 4 Windows users authorize to Active Directory + Macintosh and Linux users authorize to local system, considering Kerberos Privileges 4 Users are given System Administrative privileges 4 Users are not given System Administrative responsibility 4 Support Contractor has SA privileges and respsonsibility JPL System Management Requirements II Monthly and ad-hoc reporting II New systems delivered secure II Security patches maintained monthly Anti-Virus signature files maintained as needed II Emergency patches within 7 days Quarterlv Service Packs or point releases JPL Information-__1_c System Tools H Periodic ISS scans ITSecure - Custom maintenance utility for Windows II SMS - Windows patch deployment H Netoctopus - Macintosh patch deployment H Norton Anti-Virus Liveupdate Issues ISS scans - may take many scans to capture information w ITSecure needs to be deployed q ua rter I y w SMS + Domain dependant + Too costly to prepare packages w Netoctopus Costly to prepare packages System Management-Future Tools Periodic ISS scans Norton Anti-Virus Liveupdate 4 sus 4 Easy to support 4 Responsibility is transferred to users PatchLink - NASA-wide tool 4 Unobtrusive data gathering and patch delivery + User can control reboot 4 Large patch repository 4 Cross platform 4 Upload data to IT Security Database to close SPL tickets and update configuration information . -
Creating a Showcase Portfolio CD
Creating a Showcase Portfolio C.D. At the end of student teaching it will be necessary for you to export your showcase portfolio, burn it onto a C.D., and turn it in to your university supervisor. This can be done in TaskStream by going to your “Resource Manager” within TaskStream. Once you have clicked on the Resource Manager, choose the tab across the top that says “Pack-It-Up”. You will be packing up a package of your work that is already in TaskStream. A showcase portfolio is a very large file and will have to be packed up by TaskStream in a compressed file format. This will also require you to uncompress the portfolio after downloading. This tutorial will assist with the steps to follow. The next step is to select the work you would like TaskStream to package. This is done by clicking on the tab for selecting work. You will then be asked what type of work you want to package. Your showcase portfolio is a presentation portfolio, so you will click there and click next step. The next step will be to choose the presentation portfolio you want packaged, check the box, and click next step. TaskStream will confirm your selection and then ask you to choose the type of file you need your work to be packaged into. If you are using a computer with a Windows operating system, you will choose a zip file. If you are using a computer with a Macintosh operating system, you will choose a sit file. You will also be asked how you would like TaskStream to notify you that they have completed the task of packing up your work.