Remote Control Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

File Management
File management Information about file management How to use the SFTP Wrapper Advanced: WinSCP SFTP Guide Advanced: CyberDuck SFTP Guide Restoring Backups Installation Locations File Manager How to use the SFTP Wrapper To quickly load up WinSCP, you can use our wrapper to automatically launch WinSCP and log you in without messing around with usernames/passwords/ports/protocols etc. It's super easy!* Our wrapper is currently Windows only; if you would like information on how to access your files using one of our other sFTP guides. Our wrapper is currently Windows only; if you would like information on how to access your files please see one of our other sFTP guides. 1. Make sure you have .NET Framework 4.0 (or higher) installed from Microsoft's website. This is needed for the wrapper to work properly. If your computer is on Windows 8 or later, you already have it! 2. Download and run it by clicking here: here NOTE: CLOSE THE PROGRAM AFTER INSTALLATION. 1. Head on over back to the "Service" > "Access" page and click the "Download" button and then confirm you have read the very serious warning, and click "Download" again. This will download your chPPK file, a tiny little file crammed with information on how to connect to your system. Note: If clicking the sFTP wrapper install URL shows a page full of text. You will need to go back and Right Click > Save As, and run the wrapper application from your download folder. Some browsers/browser versions will not automatically download this .application file. 2. -

Data File Manager
Data File Manager Welcome to Data File Manager! Thank you for using the data file manager. Highlights of the data file manager are as follows: Intuitive operability Buttons on the tool menu, drag & drop, and context menu with a right click are supported to use each function. Tree view for data in SD memory card Files and folders in SD memory card are shown in a tree structure and target files can easily be found. Operations for files and folders Files and folders can be added, renamed or deleted. PLC maintenance Viewing the PLC status, such as Run/Stop state or error status, downloading/uploading user programs, or upgrading the system software of the PLC are supported. MICRO/I maintenance Viewing the target information, such as system software version or external memory device information, or downloading/uploading project is supported. Notes - Data File Manager There are the following notes when you use Data File Manager: Supported hardware Data File Manager supports the following hardware: FC4A series MICROSmart FC5A series MICROSmart Pentra FC6A series MICROSmart FT1A series SmartAXIS expect FT1A Touch HG3G/4G series MICRO/I HG2G-5F series MICRO/I HG2G-5T series MICRO/I HG1G series MICRO/I SD card access (SmartAXIS Pro & Lite) SD card inserted on SmartAXIS series can be accessed while the PLC is stopped only. Downloading or uploading the user program (PLC) You can download or upload the user programs using ZLD files, which can be created or read with WindLDR. Downloading or uploading the project (MICRO/I) You can download or upload the project using ZNV files, which can be created or read with WindO/I-NV4. -
Open Windows File from Download Open Files from the File Menu
open windows file from download Open files from the File menu. The Open tab on the File menu shows a list of files you’ve recently opened, and it includes links to places where you commonly store files. The Recent list shows the files that you opened recently from any of your devices. If this list gets unwieldy, you can remove files from it. Just right- click the file name and then pick Remove from list . You can make other changes to the Recent list. To learn more, see Customize the list of recently used files. If you don’t use the list of Recent files, and you’d rather jump straight into browsing folders, use Ctrl+F12 to open the Open dialog box directly. To access files from your Microsoft 365 Groups or SharePoint Online document libraries click the Sites - Your Company link. You'll get a list of your frequently Groups and Sites to select from. Pick the one you want and browse to the file you want to open. Double-click Computer to get to local files, including removable flash drives. You can also select one of the locations your accounts let you get to, sign in if necessary, and then open the file you want. To add a new location, click Add a Place . Tip: If you want to bypass File > Open and always use the Open dialog box, do this: Select File > Options > Save , and then select the Don’t show the Backstage when opening or saving files check box. Then, close and reopen any open Office applications. -

ATM Adaptation Layer for Computer Data
29762 99 389-410 r1jk.ps 6/18/03 1:38 PM Page 389 Index 3GIO, 273 Associated IRP, 40 8B/10B encoding scheme, 108 Asymmetric cryptography, 85–86 1394 architecture, 43–44 Asynchronous I/O, 12–14 1394 driver, 29 Asynchronous replication, 321, 324 ATA (AT attached), 48 AAL5 (ATM Adaptation Layer for computer data), 119 ATA devices, 49 Access Controls, 129, 133 ATA drives and SMART, 49 ACK (positive acknowledgment) frame, 114 ATA specifications, 48–49 ACLs (access control lists), 8, 205, 211, 338–339 ATAPI (AT Attachment Packet Interface), 49 Active Directory, 334, 336 $AttrDef file, 198 adapter/HBA class, 55 Attribute list defragmentation, 217 Address Resolution Protocol, 105 Authentication, 75–76 Address spoofing, 102 Automated System Recovery, 365 ADIC (Advanced Digital Information Corporation), AutoPath, 315–316 129, 236, 237 AndX, 76–77 B+ tree, 204 ANSI (American National Standards Institute), 107 Back-end networks, 274 ANSI (American National Standards Institute) Web BackOffice, 88 site, 43 Backup applications, 141–144, 156, 165 APCs (asynchronous procedure calls), 7, 24–25, 41 Backup classifications, 143 APIs architecture-based, 144–146 backup/restore applications, 163 functionality-based, 146–147 backups and restores, 139–140 network infrastructure-based, 148–156 volume management applications, 333–334 Backup Exec program, 156 Windows 2000 RSM (Removable Storage Manage- Backup ISVs (independent software vendors), 155 ment), 266–268 Backup server and server-free backups, 154–155 Application images, 227–230 Backup utility, 156–157 Application -

Dell EMC Openmanage Installation and Management Release Notes Version 9.3.1 Notes, Cautions, and Warnings
Dell EMC OpenManage Installation and Management Release Notes Version 9.3.1 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2019 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. 2019 - 10 Rev. A01 Contents 1 Release summary..........................................................................................................................4 2 New and enhanced features.......................................................................................................... 5 3 Compatibility............................................................................................................................... 6 Supported network cards.....................................................................................................................................................6 Supported operating systems..............................................................................................................................................6 Supported web browsers.................................................................................................................................................... -

Operating Systems Lecture #5: File Management
Operating Systems Lecture #5: File Management Written by David Goodwin based on the lecture series of Dr. Dayou Li and the book Understanding Operating Systems 4thed. by I.M.Flynn and A.McIver McHoes (2006) Department of Computer Science and Technology, University of Bedfordshire. Operating Systems, 2013 25th February 2013 Outline Lecture #5 File Management David Goodwin 1 Introduction University of Bedfordshire 2 Interaction with the file manager Introduction Interaction with the file manager 3 Files Files Physical storage 4 Physical storage allocation allocation Directories 5 Directories File system Access 6 File system Data compression summary 7 Access 8 Data compression 9 summary Operating Systems 46 Lecture #5 File Management David Goodwin University of Bedfordshire Introduction 3 Interaction with the file manager Introduction Files Physical storage allocation Directories File system Access Data compression summary Operating Systems 46 Introduction Lecture #5 File Management David Goodwin University of Bedfordshire Introduction 4 Responsibilities of the file manager Interaction with the file manager 1 Keep track of where each file is stored Files 2 Use a policy that will determine where and how the files will Physical storage be stored, making sure to efficiently use the available storage allocation space and provide efficient access to the files. Directories 3 Allocate each file when a user has been cleared for access to File system it, and then record its use. Access 4 Deallocate the file when the file is to be returned to storage, Data compression and communicate its availability to others who may be summary waiting for it. Operating Systems 46 Definitions Lecture #5 File Management field is a group of related bytes that can be identified by David Goodwin University of the user with a name, type, and size. -

Clintegrity File Manager User Guide Table of Contents
Nuance® Clintegrity™ File Manager File Manager User Guide 18.1 Release Client Support Phone: 800.892.5049 Fax: 877.238.2776 Web Portal: http://www.nuance.com/support/index.htm Government Programs Support Phone: 800.257.0512 Self-Service Support: https://www.nuance.com/gov/support Proprietary Statement This material constitutes proprietary and trade secret information and shall not be disclosed to any third party, nor used by the recipient except under the terms and conditions prescribed by Nuance Communications, Inc. Copyright Statement © 2018 Nuance Communications, Inc. All rights reserved. Nuance, the Nuance logo, and Clintegrity are trademarks and/or registered trademarks of Nuance Communications, Inc., and/or its subsidiaries in the United States and/or other countries. All other trademarks are properties of their respective owners. Table of Contents Clintegrity File Manager User Guide Table of Contents 18.1 Release What’s New . xi About This Guide . xiii Chapter 1 About Clintegrity File Manager What is File Manager? . .1 File Manager Filing Cabinet. .1 About Setting Up File Manager . .2 Chapter 2 Getting Started Enable Clintegrity Keystrokes in Flat Panel Monitors . .3 Configuring Your Browser. .4 How to … Set Standard Browser Settings . 4 Configure Security Settings . 5 Set Print Page Options . 10 Set Recommended Options . 10 Set Custom Links . 11 Signing In . .12 How to … Start the Clintegrity Application . 12 Standard Sign In. 13 First Time Sign In . 13 Rules for Creating Passwords . 14 Reset Password . 14 Changing Password from the Home Page . 15 Password Settings . 16 Get Help Signing In . 16 i Clintegrity File Manager User Guide Configuring Users. -

File Handling
Today Comp 104: Operating Systems Concepts • Files – Introduction – Filestore allocation policies • Contiguous allocation • Linked allocation Files and Filestore Allocation • File allocation table • Indexed allocation – Links – File deletion 1 2 Operating System – An Abstract View Files & I/O User Command Interface • Most filesystems are tree-structured (e.g. Unix) Processor Manager / (root) etc bin usr users Memory Manager bin staff students Device Manager u0abc u0def File Manager file1 file2 file3 3 4 1 Directories Unix Inodes • Non-leaf nodes are directories • An inode contains info such as – contain list of filenames plus further info about – file owner each file – permissions • Example: Unix – modify and access times – directory entry consists of filename and inode – size number – type (regular, special, etc.) – inode number references an inode - a file – location on disk descriptor 5 6 UNIX Permissions File Types • Permissions are read, write and execute • Some systems (e.g. Windows) use file (rwx) for user, group, others (ugo) extension to indicate application – e.g. .doc, .ps, .ppt, .html – e.g. rwxr--r-- (rwx for owner, r for everyone • Other systems more basic else) • On UNIX, can try to execute any file – Exec will look for ‘magic number’ at head of valid executable binary file • Permissions can be altered with chmod – If number not present, exec looks for “#!” followed by name of program to execute – e.g. chmod go-r prog1 • e.g. #!/bin/ksh – Otherwise, assumes file is shell script and creates instance of user’s preferred shell to process it 7 8 2 Filestore Allocation The Free List • Filestore divided into fixed-size blocks • Can be a simple bit vector – e.g. -

File Manager
File Manager 2016.12 Rev. 1.0 Contents 1.Introduction....................................................................................1 1-1.Overview .........................................................................................................1 1-2. System Requirements and Restrictions .......................................................1 2.Installation on Windows PC ...........................................................2 2-1.Installation......................................................................................................2 2-2.Uninstallation.................................................................................................4 3.How to use RSD-FDFM ..................................................................5 3-1.How to proceed with format CF media..........................................................6 3-2.How to proceed with writing data to CF media ............................................8 3-3.How to create files/folders at CF media.......................................................11 3-4.How to delete files/folders at CF media.......................................................14 3-5.How to save files/folders at CF media .........................................................15 3-6.A list of error messages of RSD-FDFM .......................................................16 *All trademarks and logos are the properties of their respective holders. *The specifications and pictures are subject to change without notice. 1.Introduction Thank you for purchasing file -

Installing Agile PLM for OAS V9.2.2.7
Agile Product Lifecycle Management Installing Agile PLM for OAS v9.2.2.7 Part No. E15405-01 September 2009 Installing Agile PLM for OAS Copyright and Trademarks Copyright © 1995, 2009, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this software or related documentation is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -

User Guide – Colligo Contributor V4.2 File Manager
User Guide – Colligo Contributor v4.2 File Manager USER GUIDE Introduction This User Guide is designed to serve as a brief overview to help you get started. There is also information available under the Help option in the various Contributor interface toolbar. If necessary you can access the Help by launching the Contributor interface from the System Tray and selecting Help->Help and Support. If you would like further instructions, please consult the Features list at http://support.colligo.com/Lists/Features/AllItems.aspx - where you will find a complete list of features by product along with instructions for use. You will also find a number of screencasts on the support site that walk you through the main product features. The SharePoint support site can be synchronized with Colligo Contributor for anytime access, online or offline. Please follow the instructions on the home page at http://support.colligo.com/. We hope you enjoy using the product, and please don’t hesitate to send us questions or provide feedback at [email protected]. Thank You. June 23, 2010 Copyright 2010 Colligo Networks, Inc. All rights reserved. Page 1 of 13 Not to be reproduced without permission. Learn more here www.colligo.com. User Guide – Colligo Contributor v4.2 File Manager Quick Start Contents INTRODUCTION ............................................................................................................................................................................... 1 INSTALLING COLLIGO CONTRIBUTOR .............................................................................................................................................. -
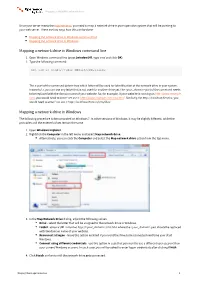
Mapping a Network Drive in Windows Command Line Mapping a Network
Mapping a WebDAV network drive Once your server meets the requirements, you need to map a network drive in your operation system that will be pointing to your web server. There are two ways how this can be done: Mapping the network drive in Windows command line Mapping the network drive in Windows Mapping a network drive in Windows command line 1. Open Windows command line (press [window]+R, type cmd and click OK). 2. Type the following command: net use x: http://<your_domain>/cms/files The x: part of the command determines which letter will be used for identification of the network drive in your system. Instead of x, you can use any letter that is not used for another drive yet.The <your_domain> part of the command needs to be replaced with the domain name of your website. So, for example, if your website is running on http://www.example. com, you would need to enter 'net use x: http://www.example.com/cms/files'. Similarly, for http://localhost/Kentico, you would need to enter 'net use x: http://localhost/Kentico/cms/files'. Mapping a network drive in Windows The following procedure is demonstrated on Windows 7. In other versions of Windows, it may be slightly different, while the principles and the entered values remain the same. 1. Open Windows Explorer. 2. Rightclick the Computer in the left menu and select Map network drive. Alternatively, you can click the Computer and select the Map network drive action from the top menu. 3. In the Map Network Drive dialog, adjust the following values: Drive - select the letter that will be assigned to the network drive in Windows.