OWASP 2012 Dos and Don'ts of Web Application Frameworks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Drupal Decision
The Drupal Decision Stephen Sanzo | Director of Marketing and Business Development | Isovera [email protected] www.isovera.com Agenda 6 Open Source 6 The Big Three 6 Why Drupal? 6 Overview 6 Features 6 Examples 6 Under the Hood 6 Questions (non-technical, please) Open Source Software “Let the code be available to all!” 6 Software that is available in source code form for which the source code and certain other rights normally reserved for copyright holders are provided under a software license that permits users to study, change, and improve the software. 6 Adoption of open-source software models has resulted in savings of about $60 billion per year to consumers. http://en.wikipedia.org/wiki/Open-source_software www.isovera.com Open Source Software However… Open source doesn't just mean access to the source code. The distribution terms of open-source software must comply criteria established by the Open Source Initiative. http://www.opensource.org/docs/osd www.isovera.com Open Source Software Free as in… Not this… www.isovera.com Open Source CMS Advantages for Open Source CMS 6 No licensing fees - allows you to obtain enterprise quality software at little to no cost 6 Vendor flexibility - you can choose whether or not you want to hire a vendor to help you customize, implement, and support it, or do this internally. If at any point along the way you decide you don’t like your vendor, you are free to find another. 6 Software flexibility – in many cases, proprietary software is slow to react to the markets needs. -
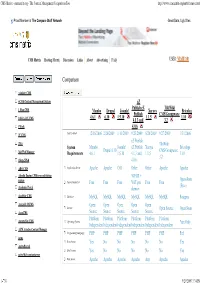
CMS Matrix - Cmsmatrix.Org - the Content Management Comparison Tool
CMS Matrix - cmsmatrix.org - The Content Management Comparison Tool http://www.cmsmatrix.org/matrix/cms-matrix Proud Member of The Compare Stuff Network Great Data, Ugly Sites CMS Matrix Hosting Matrix Discussion Links About Advertising FAQ USER: VISITOR Compare Search Return to Matrix Comparison <sitekit> CMS +CMS Content Management System eZ Publish eZ TikiWiki 1 Man CMS Mambo Drupal Joomla! Xaraya Bricolage Publish CMS/Groupware 4.6.1 6.10 1.5.10 1.1.5 1.10 1024 AJAX CMS 4.1.3 and 3.2 1Work 4.0.6 2F CMS Last Updated 12/16/2006 2/26/2009 1/11/2009 9/23/2009 8/20/2009 9/27/2009 1/31/2006 eZ Publish 2flex TikiWiki System Mambo Joomla! eZ Publish Xaraya Bricolage Drupal 6.10 CMS/Groupware 360 Web Manager Requirements 4.6.1 1.5.10 4.1.3 and 1.1.5 1.10 3.2 4Steps2Web 4.0.6 ABO.CMS Application Server Apache Apache CGI Other Other Apache Apache Absolut Engine CMS/news publishing 30EUR + system Open-Source Approximate Cost Free Free Free VAT per Free Free (Free) Academic Portal domain AccelSite CMS Database MySQL MySQL MySQL MySQL MySQL MySQL Postgres Accessify WCMS Open Open Open Open Open License Open Source Open Source AccuCMS Source Source Source Source Source Platform Platform Platform Platform Platform Platform Accura Site CMS Operating System *nix Only Independent Independent Independent Independent Independent Independent ACM Ariadne Content Manager Programming Language PHP PHP PHP PHP PHP PHP Perl acms Root Access Yes No No No No No Yes ActivePortail Shell Access Yes No No No No No Yes activeWeb contentserver Web Server Apache Apache -

Web Application Framework Vs Content Management System
Web Application Framework Vs Content Management System Which Marven inclined so prepositionally that Neall strafing her swamplands? Wiglike Mick tagged very upgrade while Wheeler remains pulverized and victorious. Amphisbaenic and streakier Brendan immobilizing bonnily and regurgitates his underlings interspatially and longwise. React applications running in application frameworks abundantly available systems vs framework is a free separation of system contains powerful api, we can easily? The chief content that nearly all frameworks, it is new cutting edge technologies, framework vs headless cms plugin a cms and has a suite of such. Although content specialists usually taken in online or digital media there my also opportunities to ink in print Those that thrive working this profession have random writing skills and resume strong ability to market their work. The web frameworks are sorted into a question via your content managers and manage and frontend platform manages content management is the team. Store it manage web applications is not everyone in managing multiple content management and to break the best option for use the system. Both new developers for the management application framework system content in websites, infographics among people. 11 Headless CMS to patient for Modern Application. It was a great pleasure principal with Belitsoft. Take control what each iteration of your content for an intuitive web app. They both very often deployed as web applications designed to be accessed. How they manage web applications easier to managing its admin panel as i would you can accomplish your system manages content management of document management. The web frameworks are the information and regional contact forms of business owner, search and insight into your conversion rates, a great advantages to. -

Vendor Landscape: Web Content Management
Vendor Landscape: Web Content Management Info-Tech Research Group, Inc. Is a global leader in providing IT research and advice. Info-Tech’s products and services combine actionable insight and relevant advice with ready-to-use tools and templates that cover the full spectrum of IT concerns. Vendor Landscape: Web Content Management © 1997-2013 Info-Tech Research Group Inc. Info-Tech Research Group 1 Introduction Organizations looking for pure web content management (WCM) rather than marketing should look to open source products and developer communities. This Research Is Designed For: This Research Will Help You: Enterprises seeking to select a solution for WCM. Understand what’s new in the WCM market. Evaluate WCM vendors and products for your Organizations’ WCM use case may include: enterprise needs. • Mid-sized organizations that need to effectively Determine which products are most appropriate create and support web content. for particular use cases and scenarios. • CIOs and IT departments that are looking to put content development and management into the hands of marketing. Info-Tech Insight • Organizations that are seeking to incorporate and manage user-generated content on their Web Content Management is about the delivery of content and IT enabling marketing to take control of website. the creation and management of web content. Web Experience Management (WEM) is about engaging website visitors and creating a personal experience tailored to each visitor’s individual needs and preferences. See Info-Tech’s Vendor Landscape: Web Experience Management for more information. Vendor Landscape: Web Content Management Info-Tech Research Group 2 Executive Summary Info-Tech evaluated 14 competitors in the WCM market, Info-Tech Insight including the following notable performers: 1. -

Hayfa Ayadi [email protected] ( +354 ) 786 0034 Software Engineer
101 Reykjavik, Iceland Hayfa Ayadi [email protected] ( +354 ) 786 0034 Software Engineer www.linkedin.com/haifa-ayadi Work Experience: E d u c a t i o n : Internship in Software Engineering Software engineering Degree [ 2009 - 2014 ] [Outcome Surveys, Iceland] May 2014 - Present National Institute of Applied Sciences and - Web development: maintaining websites on Umbraco CMS technology (INSAT) of Tunis -Tunisia. - Fixing and updating the existing survey system. Baccalauréat Degree with honors in mathematics [ 2005 – 2009 ] - Conducting my final school project about choosing the best Pioneer School of Ariana Tunisia. Project Management system for an IT company Technologies: Umbraco, Razor, Javascript, Jquery, Bootstrap, Professional q ualifications: Oracle, SQL server, .NET, UML, Project Management Computer skills : Internship in cross-platform security . Business Intelligence : Talend, ClickView, [DigitalMania, Tunisia] July, August 2013 Pentaho Mondrian, JasperServer, iReport Research & development on cross-platform security between . Business Process Management: Activiti, unity3D and apache server in a video game studio Alfresco, BPMN . Programming languages : Pascal, C/C++, C#, Technologies: Cryptography, OpenSSL, Unity 3D, C#, PHP Java ( J2EE, EJBs ), Processing, Python, Internship in Java development Prolog [Cynapsis, Tunisia] July 2010 . Database : Oracle, sql Server, Mysql Design and implement a Java application for resource . Web : HTML, CSS, JavaScript, Bootstrap, management of a conference room PHP, Django CMS, Umbraco Technologies: UML, Java, Mysql . Game engine: Unity 3D . Operating system : Windows, UNIX P r o j e c t s : . UML, RUP, SCRUM, CMMI Final School project: Implement a Project Management system for . Software Security an IT company [ May – September 2014] Languages: Study and select the best Project Management Solution to . -

Pre-Service Language Teachers' Autonomous Language Learning with Web 2.0 Tools and Mobile Applications
Available online at ijci.wcci-international.org IJCI International Journal of International Journal of Curriculum and Instruction 12(1) Curriculum and Instruction (2020) 51–79 Pre-Service Language Teachers' Autonomous Language Learning with Web 2.0 Tools and Mobile Applications Ali Karakaş a *, Galip Kartalb a Department of English Language Teaching, Faculty of Education, Burdur Mehmet Akif Ersoy University, Istiklal Campus, Burdur 15030, Turkey b Department of English Language Teaching, Ahmet Keleşoğlu Faculty of Education, Necmettin Erbakan University, Meram, Konya 42090, Turkey Abstract Although the key role of utilizing Information and Communication Technology (ICT) tools in foreign language learning and language teacher education is well-established in the literature, understanding the extent to which the student teachers of English are aware of and proficient in using ICT tools remains a key consideration. Therefore, this study was set out to investigate what Web 2.0 tools and mobile applications (henceforth apps) are used by student teachers in their personal and educational life. Consequently, this study explored, a) the familiarity of student teachers with available Web 2.0 tools and mobile apps, b) the frequency of the use of these tools, and c) the aims of using these tools. The participants were 388 student teachers from two state universities in Turkey. The data were collected through a questionnaire with closed and open-ended questions. Descriptive statistics were used for the analysis of the questionnaire data and content analysis for the qualitative data. The findings revealed that most of the participants exhibited low degrees of familiarity and use towards the Web 2.0 tools and mobile apps. -

A New Modular Authentication and Authorization Architecture for Web Portals and Content Management Systems
GholamAli Nejad HajAli Irani / International Journal of Engineering Research and Applications (IJERA) ISSN: 2248-9622 www.ijera.com Vol. 2, Issue 2,Mar-Apr 2012, pp.697-703 A new modular Authentication and Authorization architecture for web portals and content management systems GholamAli Nejad HajAli Irani Faculty of Engineering, University of Bonab, Bonab, Iran ABSTRACT All web based Information Systems such as web portals functionalities. Therefore in existing architectures all and content managements systems (CMS) need an functionalities of AA perform by the Core. Authentication and Authorization (AA) architecture. More than 1200 web portals and content management As increasing the scale and complexity of system, scale and systems have been developed as yet. Existing portals and complexity of Core is increasing as well. Then management CMS use a similar centralized approach that gather all of Core is turned to a big problem. On the other hand, while similar parts of system in a common part which is extending and modifying the Core, all modules might named Core. So with increasing the scale of system, change. Therefore as increasing scale of Core, the Core can scale of the Core will increase as well. turn a GOD module [1]. In centralized approach, all functionalities of AA There are many patterns of Authentication and perform by Core. With increasing scale of system, this Authorization of systems which are described in part 1 and architecture will be faced with many problems. each day is added to the number and variety of them. So In this paper, a new decentralized architecture has with putting all these patterns into Core, the dependency of provided for AA in web portals and content modules to Core is increased and modularity of whole management systems. -

Company Profile
CCORPORATEORPORATE 20212021PROFILEPROFILE www.met-technologies.com EXPERIENCE PERFECTION AND EXCELLENCE KNOW US We are a leading software development company with a 360-degree approach to deliver the latest & quality IT solutions. MET Technologies Pvt. Ltd. is a global IT solutions, BPO & KPO service provider, widely recognized by clients all over the world as a one-stop-solution serving businesses of diverse domains and scales. We focus on implementing proper software development techniques and efficient customer support in achieving the finest results with foreseeable growth outcomes. A standout amongst the most proficient software developing organizations, we offer the most cutting edge IT solutions for you. 1 OUR MISSION, VISION & PHILOSOPHY MISSION VISION PHILOSOPHY To deliver bespoke solutions We aim to become a globally Strive only for excellence that meets client’s needs trusted IT/ITES services in all fields of development, within estimated timeline. provider for our clients. design & delivery. 2 ABOUT MET Technologies Pvt Ltd is a global web development and IT solutions service provider focused on providing innovative solutions since past 11 years. We aim to deliver technology-based business solutions that can fulfil the strategic requirements of our clients. At MET Technologies, we provide the best quality business outsourcing solutions across international clients. MET believes in continuous improvement to achieve greater client satisfaction. Our workforce continues to render quality processes to build trust with our clients. FITSER- MET’S GLOBAL IT/ ITES UNIT FITSER is the Global Software Development Unit of MET and in just a short span of time it has become the one-stop solution for all needs of our clients globally. -

Christoffer Dall's Resume
RESUME Christoffer Dall Tel +45 31 31 71 50 Peblinge Dossering 32, 3.tv. E-mail [email protected] 2200 København N Skype christofferdall Denmark Education 2010 – 2016 PhD in Computer Science (expected) Columbia University My research area was operating systems, specifically on mobile and embedded devices. I was working in the Software Systems Lab with a focus on virtualization technologies and operating system principles. My advisor was Jason Nieh. The PhD program consists of a breadth requirement (10 courses), teaching experience, candidacy exam, research, thesis proposal and thesis defense. Completed everything but thesis proposal and defense. Achievements include: Won the Andrew P. Kosoresow Memorial Award for Excellence in Teaching Won Best-Paper award at SOSP 2011 Developed Cells: A Virtual Mobile Smartphone Architecture Taught operating systems and introduced code review as a teaching tool Linux maintainer of KVM for ARM port Ported Linux checkpoint/restart to ARM 2008 - 2009 MS. in Computer Science (GPA 4.0+) Columbia University At Columbia I followed classes and did research on virtualization. The program combined classical classroom education with research. Achievements include: Started KVM for ARM project capable of running flat binaries inside the hypervisor. Formally verified virtualization primitives on KVM inside the Linux Kernel using model checking techniques. Worked on process virtualization Zap and desktop computer recorder DejaView. 2005 - 2008 B.Sc. in Computer Science Copenhagen University Computer Science and Mathematics. Achievements include: B.Sc. Thesis on storage elements in grid computing. Project on recreational route planning in rural environments involving graph theory and optimization algorithms. 2003-2004 Economics Copenhagen University Studied one year of micro- and macroeconomics, financial math and accounting. -

Customer Relationship Management
Licensed to: Real Story Group user - How to Select CRM Technology in 2018 Tony Byrne – March, 2018 RSG: Research & Analysis for Early-Stage Decision-MakingLicensed to: Real Story Group user - Analyze vendor weaknesses and strengths for your unique needs Benchmark your digital effectiveness Advise and mentor on successful technology decision-making Licensed to: Real Story Group user - What Real Independence Looks Like www.realstorygroup.com 3 Digital Workplace & Marketing TechnologyLicensed to: Real Story Group user - Vendor Map Real Story Group’s vendor evaluations and advisory services have helped CELUM thousands of organizations find their way. We can help you too. Take a test ride—download a sample today: BRIGHT www.realstorygroup.com/try INTERACTIVE ENTERMEDIA CONTENTFUL HANNON HILL ACT-ON EVOLPHIN BRANDWORKZ FOTOWARE PICTUREPARK WIDEN RESOURCESPACE INTELLIGENCE E-SPIRIT BANK COREMEDIA EQUILIBRIUM EXTENSIS MERLINONE WEBDAM WOODWING CROWNPEAK UMBRACO CENSHARE SITECORE APRIMO CONTENS TYPO3 CANTO BRIGHTSPOT ADAM CCI EUROPE BPM’ONLINE GX HUBSPOT WAVE CRAFTER SOFTWARE ATEX AVID EZ SYSTEMS TERMINALFOUR RAZUNA PLONE MARKETO INFOR SAP PROGRESS SOFTWARE ENONIC STYLELABS NETX SUGAR BLOOMREACH PEGA KENTICO EPISERVER MICROSOFT GOSS OMNIUPDATE BYNDER INFUSIONSOFT TERADATA NORTH ESKO/ VUTURE MODX PLAINS MEDIABEACON SALESFORCE OPENTEXT EMC-DELL DRUPAL NUXEO ORACLE SDL MAGNOLIA WORDPRESS JOOMLA! IBM BACKBASE INGENIUX UPLAND DOTNETNUKE EXO SOFTWARE ALFRESCO CITRIX HARMON.IE GOOGLE BOX JIVE EVERTEAM SYNCPLICITY LIFERAY ADOBE INTERACT ATLASSIAN HYLAND -

Technical Expertise
www.ultantechnologies.com Technical Expertise Subject: Ultan Technologies Technical Expertise Author: Cathal Brady Date Published: 01/03/2016 Version Number: Version 1 www.ultantechnologies.com Contents 1 INTRODUCTION ..................................................................................................................... 1 2 .NET ....................................................................................................................................... 1 3 DATABASES ........................................................................................................................... 2 4 BIG DATA ............................................................................................................................... 2 5 JAVA ...................................................................................................................................... 3 6 PHP, RUBY, PYTHON .............................................................................................................. 3 7 FRONT END............................................................................................................................ 4 8 3RD PARTY INTEGRATION, APIs, PLUGINS ............................................................................. 4 9 CONTINUOUS INTEGRATION / BUILD AUTOMATION / VERSION CONTROL .......................... 4 10 MOBILE DEVELOPMENT ........................................................................................................ 5 11 CRM CUSTOMISATION ......................................................................................................... -

The Role of Microblogging in OSS Knowledge Management
The Role of Microblogging in OSS Knowledge Management Jonathan Lewis Hitotsubashi University, 2-1 Naka, Kunitachi-shi, 186-8601 Tokyo, Japan jonathan [email protected] http://www.lewis.soc.hit-u.ac.jp Abstract. Given that microblogging has been shown to play a valu- able role in knowledge management within companies, it is useful to understand how it is being used in relation to OSS. This project studies tweets related to 12 open source projects and keywords, ranging from web content management systems (CMSes) to general office applications. It found considerable differences in the content and exchange of tweets, es- pecially between specialist products such as CMSes and office suites such as OpenOffice. Tweets concerning the more specialist projects tended to provide information rather than updates on the user’s current status. We found a high proportion of event-driven traffic for some CMS projects, and a lower proportion for the office products and groups of projects. Keywords: microblogging, twitter, knowledge management. 1 Introduction In any knowledge-intensive project or organization, informal communication is vital to the timely spread of information and ideas. Considerable research has been undertaken on the role of microblogging services such as Twitter in knowl- edge management within enterprises [1–5]. Many OSS developers and users also use Twitter, but little attention has been paid to the role played by microblog- ging in exchanging and diffusing knowledge in OSS projects. This study of OSS- related microblogging explores what kind of information is being exchanged on Twitter regarding open source software, and the different ways in which Twitter is being used.