Google Pixel Phones on Android 11.0 (MDFPP31/WLANCEP10) Security Target
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Nokia Lumia 521 User Manual
www.nokia.com Product and safety information Copyright © 2013 Nokia. All rights reserved. Nokia and Nokia Connecting People are trademarks or registered trademarks of Nokia Corporation. Other product and company names mentioned herein may be trademarks or trade names of their respective owners. The phone supplied in the sales package may differ from that shown. Specifications subject to change without notice. Printed in China. 9260765 Ver. 1.0 03/13 Quick Guide Psst... Nokia Lumia 521 This guide isn't all there is... For the online user guide, even more info, user Contents guides in another language, and Safety 3 troubleshooting help, go to www.nokia.com/ support. Keys and parts 4 Check out the videos at www.youtube.com/ Get started 5 NokiaSupportVideos. Get the basics 9 For info on Nokia Service terms and Privacy policy, go to www.nokia.com/privacy. Try out the touch screen 10 First start-up Take your friends with you 15 Your new phone comes with great features that will be installed when you start your phone Messages 17 for the first time. Allow some minutes for your Mail 21 phone to be ready. Take photos and share 25 HERE Maps 27 Browse the web 29 Feature-specific instructions 36 Product and safety information 38 2 Stop using the device until the glass is replaced by Safety qualified service personnel. Read these simple guidelines. Not following them may be dangerous or illegal. For further info, read the PROTECT YOUR HEARING complete user guide. To prevent possible hearing damage, do not listen at high volume levels for long periods. -

RADA Sense Mobile Application End-User Licence Agreement
RADA Sense Mobile Application End-User Licence Agreement PLEASE READ THESE LICENCE TERMS CAREFULLY BY CONTINUING TO USE THIS APP YOU AGREE TO THESE TERMS WHICH WILL BIND YOU. IF YOU DO NOT AGREE TO THESE TERMS, PLEASE IMMEDIATELY DISCONTINUE USING THIS APP. WHO WE ARE AND WHAT THIS AGREEMENT DOES We Kohler Mira Limited of Cromwell Road, Cheltenham, GL52 5EP license you to use: • Rada Sense mobile application software, the data supplied with the software, (App) and any updates or supplements to it. • The service you connect to via the App and the content we provide to you through it (Service). as permitted in these terms. YOUR PRIVACY Under data protection legislation, we are required to provide you with certain information about who we are, how we process your personal data and for what purposes and your rights in relation to your personal data and how to exercise them. This information is provided in https://www.radacontrols.com/en/privacy/ and it is important that you read that information. Please be aware that internet transmissions are never completely private or secure and that any message or information you send using the App or any Service may be read or intercepted by others, even if there is a special notice that a particular transmission is encrypted. APPLE APP STORE’S TERMS ALSO APPLY The ways in which you can use the App and Documentation may also be controlled by the Apple App Store’s rules and policies https://www.apple.com/uk/legal/internet-services/itunes/uk/terms.html and Apple App Store’s rules and policies will apply instead of these terms where there are differences between the two. -

HEATING/COOLING BEVERAGE BASE with WIRELESS CHARGING Item No
HEATING/COOLING BEVERAGE BASE WITH WIRELESS CHARGING Item No. 207196 User Guide Thank you for purchasing the Sharper Image Heating/Cooling Beverage Base with Wireless Charging. Please take a moment to read this guide and store it for future reference. FEATURES • Keeps coffee mug hot or soda can cold • Charges your Qi-enabled phone without cables or wires • Quick charge capable (10W and 7.5W) • Standard charge 5W • Auto sensor supplies the correct power for your device • Automatic safety shut-off after 4 hours (charging) CONTENTS OF BOX • 1X Mug • 1X Base Unit • 1 Power Adapter OPERATION 1. Connect the power adapter to the device. 2. Plug the power adapter into an AC outlet. 3. Place the included mug or your beverage can on top of the heating/cooling element, properly aligning it with the bottom of the container. 4. Press the power button ONCE to activate COOLING. Press a SECOND TIME to activate HEATING. 5. Place your wireless charging device on the charging surface. The Qi wireless charging pad will begin charging automatically. NOTE: There is no On/Off Switch for the wireless charger. Your phone will charge automatically if it is compatible with wireless charging. See the Compatibility list below or consult your device’s owner’s manual to check if your device is Qi enabled for wireless charging. For safety purposes, the Qi wireless charging pad will shut off automatically after 4 hours. - 1 - COMPATIBILITY Qi wireless charging is compatible with most newer phones, including: • Apple iPhone 8, 8 Plus, X, XS, XS Max, XR, 11, 11 Pro, 11 -

February 2009
February 2009 By Eric Berkowitz In most associations, conscientious Board members answers the phone. How great is that? This is nationwide ordinarily jump on any opportunity to save money. In and it is absolutely free! the Regency Tower, the Board members are all afflicted with an unrelenting compulsion to aggressively hunt Following this intriguing anecdote, the storyteller down these opportunities. For eight years, President recommends clicking on a link to Dott Nicholson-Brown applied tactics she learned while “http://www.google.com/goog411/” and watching a researching inventories for the U.S. Army to save the brief demo of the free service. The message closes with association $millions. After spending 14 hours in the the admonition to “Put 800-GOOG-411 in your phone to office emotionally lambasting vendors into trimming get telephone numbers of people anywhere free.” prices, she walks the premises turning off lights in unoccupied areas. Assistant Treasurer Bill Tannenbaum Although seemingly scripted by a third rate PR successfully tortured the workers comp insurance wannabe, the point is well taken. A quick trip to carrier into issuing overcharge credits by plastering the web site revealed the engineering behind this them with enough evidentiary documentation to cause new service. In a nutshell, GOOG-411 is Google’s permanent brain damage. Dee Lanzillo doubled the new 411 service. With GOOG-411, you can find size of the gym using in-house labor and home cook- local business information completely free, directly ing. When Iris Anastasi found the following little tidbit from your phone by calling 1-800-466-4411 (1- and sent it to the President, Dott labeled it “Good Info” 800-GOOG-411) anytime. -

English-P360-Deductible-Tool.Pdf
T-Mobile® Deductible and Fee Schedule Alcatel Tier BlackBerry Tier Huawei Tier 9810, 9900 3T 8 Comet Q10 665 3 Prism, Prism II Z10 768 Sonic 4G A30 Priv 4 Summit 1 Aspire Tap Evolve webConnect Fierce XL Coolpad Tier Fierce, Fierce 2, Fierce 4 1 Catalyst GO FLIP myTouch 2 LINKZONE Defiant Pixi 7 Rogue 1 S7 PRO 3 POP 7 Snap POP Astro Surf REVVL REVVL Plus 2 Kyocera Tier Soul Hydro WAVE 1 IDOL 4S 3 Dell Tier Rally Streak 7 2 DuraForce PRO, DuraForceXD 3 Apple Tier Ericsson Tier iPad iPad Air 2 World 1 LG Tier iPad Mini, iPad Mini 2, iPad Mini 4 450 iPhone 4, iPhone 4s 3 GARMIN Tier Aristo iPhone 5, iPhone 5c, iPhone 5s Aristo 2 PLUS iPhone 6s Garminfone 3 dLite iPhone SE GS170 Watch Series 3 1 GEOTAB Tier K7, K10 K20 Plus iPad Air SyncUP FLEET 1 Leon iPad Mini 3 Optimus L90 iPad Pro 9.7 Sentio iPhone 6 4 GOOGLE Tier iPhone 6s Plus Pixel 3a DoublePlay iPhone 7, iPhone 7 Plus Pixel 3a XL 3 Watch Series 4 G Pad F 8.0 G Pad X2 8.0, G Pad X2 8.0 Plus Pixel 3 4 G Pad X 8.0 iPad Pro 10.5-inch Pixel 3 XL G Stylo iPad Pro 11-inch G2 iPad Pro 12.9-inch G2x iPhone 6 Plus HTC Tier1 5 K30 2 iPhone 8, iPhone 8 Plus Desire iPhone X Lion iPhone XR myTouch iPhone XS, iPhone XS MAX Amaze 4G Optimus F3, F3Q, F6, L9, T Dash 3G Stylo 2 PLUS, Stylo 3 PLUS G2 Stylo 4 ASUS Tier HD2, HD7 V20 life Google Nexus 7 2 myTouch 3G 1.2, myTouch 3G slide 2 G3, G5, G6 myTouch 4G G-Slate One M9 Nexus 4, Nexus 5 3 BlackBerry Tier One S P Plus Radar 4G Q7+ 7100T, 7105T Shadow 7230, 7290 Wildfire S G Flex 8120, 8520 G7 9780 Bold 2 4 10 G8 Classic Flyer V30 Curve myTouch V10 myTouch 4G Slide 3 5 9700 Bold 3 One V30+ Sensation 4G Windows Phone 8X Please note: If you switch your device to one that is classified in another tier, the monthly charge for your new tier will be reflected on your T-Mobile bill. -

Step 1(To Be Performed on Your Google Pixel 2 XL)
For a connection between your mobile phone and your Mercedes-Benz hands-free system to be successful, Bluetooth® must be turned on in your mobile phone. Please make sure to also read the operating and pairing instructions of the mobile phone. Please follow the steps below to connect your mobile phone Google Pixel 2 XL with the mobile phone application of your Mercedes-Benz hands-free system using Bluetooth®. Step 1(to be performed on your Google Pixel 2 XL) Step 2 To get to the telephone screen of your Mercedes-Benz hands-free system press the Phone icon on the homescreen. Step 3 Select the Phone icon in the lower right corner. Step 4 Select the “Connect a New Device” application. Page 1 of 3 Step 5 Select the “Start Search Function” Step 6 The system will now search for any Bluetooth compatible phones. This may take some time depending on how many devices are found by the system. Step 7 Once the system completes searching select your mobile phone (example "My phone") from the list. Step 8 The pairing process will generate a 6-digit passcode and display it on the screen. Verify that the same 6 digits are shown on the display of your phone. Step 9 (to be performed on your Google Pixel 2 XL) There will be a pop-up "Bluetooth Request: 'MB Bluetooth' would like to pair with your phone. Confirm that the code '### ###' is shown on 'MB Bluetooth'. " Select "Pair" on your phone if the codes match. Page 2 of 3 Step 10 After the passcode is verified on both the mobile and the COMAND, the phone will begin to be authorized. -

IRAC Test Report
1 L NASA Technical Memorandum 878 13 IRAC Test Report . Gallium Doped Silicon Band I1 READ NOISE AND DARK CURRENT Gerald Lamb, Peter Shu, John Mather, Audrey Ewin, and Jeffrey Bowser JANUARY 1987 NASA Technical Memorandum 878 13 IRAC Test Report Gallium Doped Silicon Band I1 READ NOISE AND DARK CURRENT Gerald Lamb, Peter Shu, John Mather, Audrey Ewin NASA Go&rd Space Flight Center Greenbelt, Maryland Jeffrey Bowser Science Applications Research Corp. a National Aeronautics and Space Ad ministration Goddard Space Flight Center Greenbelt, Maryland 20771 1987 TABLE OF CONTENTS Page Introduction .................................................... 1 Background ..................................................... Array ........................................................ 5 Unit Cell Performance ........................................... 8 Dewar ......................................................... 17 Electronic .................................................... 23 Timing Generator .............................................. 23 Warm Preamplifier .............................................. 23 Analog Signal Processor ........................................... 25 Signal Response ............................................... 26 Noise Response ............................................... 28 Digital Electronics ................................................. 31 Software ...................................................... 32 Experimental Procedure .............................................. 33 Read Noise ................................................... -
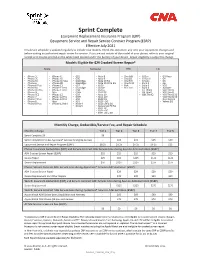
Sprint Complete
Sprint Complete Equipment Replacement Insurance Program (ERP) Equipment Service and Repair Service Contract Program (ESRP) Effective July 2021 This device schedule is updated regularly to include new models. Check this document any time your equipment changes and before visiting an authorized repair center for service. If you are not certain of the model of your phone, refer to your original receipt or it may be printed on the white label located under the battery of your device. Repair eligibility is subject to change. Models Eligible for $29 Cracked Screen Repair* Apple Samsung HTC LG • iPhone 5 • iPhone X • GS5 • Note 8 • One M8 • G Flex • G3 Vigor • iPhone 5C • iPhone XS • GS6 • Note 9 • One E8 • G Flex II • G4 • iPhone 5S • iPhone XS Max • GS6 Edge • Note 20 5G • One M9 • G Stylo • G5 • iPhone 6 • iPhone XR • GS6 Edge+ • Note 20 Ultra 5G • One M10 • Stylo 2 • G6 • iPhone 6 Plus • iPhone 11 • GS7 • GS10 • Bolt • Stylo 3 • V20 • iPhone 6S • iPhone 11 Pro • GS7 Edge • GS10e • HTC U11 • Stylo 6 • X power • iPhone 6S Plus • iPhone 11 Pro • GS8 • GS10+ • G7 ThinQ • V40 ThinQ • iPhone SE Max • GS8+ • GS10 5G • G8 ThinQ • V50 ThinQ • iPhone SE2 • iPhone 12 • GS9 • Note 10 • G8X ThinQ • V60 ThinQ 5G • iPhone 7 • iPhone 12 Pro • GS9+ • Note 10+ • V60 ThinQ 5G • iPhone 7 Plus • iPhone 12 Pro • A50 • GS20 5G Dual Screen • iPhone 8 Max • A51 • GS20+ 5G • Velvet 5G • iPhone 8 Plus • iPhone 12 Mini • Note 4 • GS20 Ultra 5G • Note 5 • Galaxy S20 FE 5G • GS21 5G • GS21+ 5G • GS21 Ultra 5G Monthly Charge, Deductible/Service Fee, and Repair Schedule -

Google Search by Voice: a Case Study
Google Search by Voice: A case study Johan Schalkwyk, Doug Beeferman, Fran¸coiseBeaufays, Bill Byrne, Ciprian Chelba, Mike Cohen, Maryam Garret, Brian Strope Google, Inc. 1600 Amphiteatre Pkwy Mountain View, CA 94043, USA 1 Introduction Using our voice to access information has been part of science fiction ever since the days of Captain Kirk talking to the Star Trek computer. Today, with powerful smartphones and cloud based computing, science fiction is becoming reality. In this chapter we give an overview of Google Search by Voice and our efforts to make speech input on mobile devices truly ubiqui- tous. The explosion in recent years of mobile devices, especially web-enabled smartphones, has resulted in new user expectations and needs. Some of these new expectations are about the nature of the services - e.g., new types of up-to-the-minute information ("where's the closest parking spot?") or communications (e.g., "update my facebook status to 'seeking chocolate'"). There is also the growing expectation of ubiquitous availability. Users in- creasingly expect to have constant access to the information and services of the web. Given the nature of delivery devices (e.g., fit in your pocket or in your ear) and the increased range of usage scenarios (while driving, biking, walking down the street), speech technology has taken on new importance in accommodating user needs for ubiquitous mobile access - any time, any place, any usage scenario, as part of any type of activity. A goal at Google is to make spoken access ubiquitously available. We would like to let the user choose - they should be able to take it for granted that spoken interaction is always an option. -

LG Nexus 4 Is Now Available Slightly Cheaper on the UK Play Store
LG Nexus 4 Is Now Available Slightly Cheaper On The UK Play Store LG Nexus 4 Is Now Available Slightly Cheaper On The UK Play Store 1 / 3 Buy LG Nexus 5 UK Smartphone - Black (16GB) at Amazon UK. ... or enable your printer by downloading an app from the Google Play™ Store. ... Then‚ swipe to check Google Now™ cards and find the latest information personalized for you. ... As soon as I powered on, the new Android Lollipop was available to install which .... Google Nexus 5 best price is Rs. 12000 as on 17th July 2020. ... 4.Last but not the least,Best value for money phone available in the market in this range. ... But for now, there is no compelling reason for people to buy a Pixel yet, so until then the ... I lost my Samsung galaxy S4 and decided to look for a cheaper alternative.. It's true: we're a bit late reviewing Google's latest Nexus-branded Android smartphone, which went on sale in the UK in November 2012. ... march into the mainstream - not just as a cheaper alternative to Apple's iPhone, but ... digital magazines and films all now available through the Google Play store app.. Do Google and LG Have a Nexus 4 Sequel On the Way Already? ... Now that CES is all done and dusted, MWC is next on the global tech roadshow. ... designing a phone that's slightly cheaper to produce and easier to manufacture. ... release of Key Lime Pie, as usually there's a reference device available.. The Nexus 4 just got a lot cheaper. -
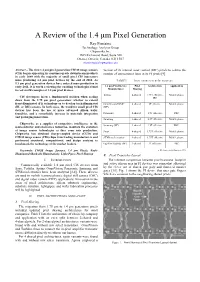
A Review of the 1.4 Μm Pixel Generation Ray Fontaine Technology Analysis Group Chipworks Inc
A Review of the 1.4 µm Pixel Generation Ray Fontaine Technology Analysis Group Chipworks Inc. 3685 Richmond Road, Suite 500 Ottawa, Ontario, Canada K2H 5B7 [email protected] Abstract – The first 1.4 µm pixel generation CMOS image sensors version of its internal reset control (IRC) pixels to reduce the (CIS) began appearing in consumer-grade downstream products number of interconnect lines in its FI pixels [9]. in early 2009 with the majority of small pixel CIS innovators mass producing 1.4 µm pixel devices by the end of 2010. As TABLE I. PIXEL ARCHITECTURE BY COMPANY 1.1 µm pixel generation devices have entered mass production in early 2011, it is worth reviewing the enabling technologies found 1.4 µm Pixel Device Pixel Architecture Application in real world examples of 1.4 µm pixel devices. Manufacturer Sharing Aptina 4-shared 1.75T effective, Mobile phone CIS developers faced a fundamental decision when scaling IRC down from the 1.75 µm pixel generation: whether to extend front-illuminated (FI) technology or to develop back-illuminated OmniVision/TSMC 2-shared 2T effective Mobile phone (BI, or BSI) sensors. In both cases, the trend for small pixel CIS (BIa) devices has been the use of more advanced silicon wafer foundries, and a remarkable increase in materials integration Panasonic 4-shared 1.5T effective DSC and packaging innovation. Samsung 2-shared 2.5T effective Mobile phone Chipworks, as a supplier of competitive intelligence to the Samsung (BIa) 2-shared 2.5T effective DVC semiconductor and electronics industries, monitors the evolution of image sensor technologies as they come into production. -
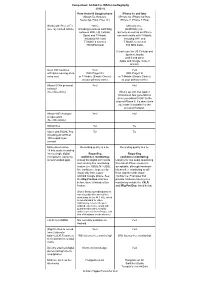
Comparison: Android Vs IOS for Mediography
Comparison: Android vs IOS for mediography 2016.12 Pure Android Google phone iPhone 6s and later (Nexus 5x, Nexus 6, (iPhone 6s, iPhone 6s Plus, Nexus 6p, Pixel, Pixel XL) iPhone 7, iPhone 7 Plus) Works with Project Fi? 100%, Officially, no... (see my related article) including seamless switching Unofficially yes... between WiFi, US Cellular, but only as well as an iPhone Sprint and T-Mobile, can work solely with T-Mobile, including WiFi and including WiFi and T-Mobile’s coveted T-Mobile’s coveted 700 MHz band 700 MHz band. (It can’t use the US Cellular and Sprint networks —until if and when— Apple and Google make it official.) Over 130 countries Yes! Yes! with data roaming at no With Project Fi With Project Fi extra cost or T-Mobile (Simple Choice) or T-Mobile (Simple Choice) as your primary carrier. as your primary carrier. Allows 5GHz personal Yes! No! hotspot? (See this article) What’s up with that Apple? It has been four generations since you added 5 GHz to the original iPhone 5. It’s about time you make it available for the personal hotspot. Allows WiFi Analyzer Yes! No! or equivalent (See this article) Still photos Tie Tie Video with FiLMiC Pro, Tie Tie including 4K UHD at 100 megabits per second Mono direct native Recording quality is a tie. Recording quality is a tie. 48 kHz audio recording from a single digital Regarding Regarding microphone, using my confidence monitoring: confidence monitoring: recommended apps Unless the digital mic has its Latency for live audio monitoring own latency-free monitoring from latest iPhone models is feature (i.e.