Meta-Blackmail Russell Christopher [email protected]
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Charging Language
1. TABLE OF CONTENTS Abduction ................................................................................................73 By Relative.........................................................................................415-420 See Kidnapping Abuse, Animal ...............................................................................................358-362,365-368 Abuse, Child ................................................................................................74-77 Abuse, Vulnerable Adult ...............................................................................78,79 Accessory After The Fact ..............................................................................38 Adultery ................................................................................................357 Aircraft Explosive............................................................................................455 Alcohol AWOL Machine.................................................................................19,20 Retail/Retail Dealer ............................................................................14-18 Tax ................................................................................................20-21 Intoxicated – Endanger ......................................................................19 Disturbance .......................................................................................19 Drinking – Prohibited Places .............................................................17-20 Minors – Citation Only -

Common Law Fraud Liability to Account for It to the Owner
FRAUD FACTS Issue 17 March 2014 (3rd edition) INFORMATION FOR ORGANISATIONS Fraud in Scotland Fraud does not respect boundaries. Fraudsters use the same tactics and deceptions, and cause the same harm throughout the UK. However, the way in which the crimes are defined, investigated and prosecuted can depend on whether the fraud took place in Scotland or England and Wales. Therefore it is important for Scottish and UK-wide businesses to understand the differences that exist. What is a ‘Scottish fraud’? Embezzlement Overview of enforcement Embezzlement is the felonious appropriation This factsheet focuses on criminal fraud. There are many interested parties involved in of property without the consent of the owner In Scotland criminal fraud is mainly dealt the detection, investigation and prosecution with under the common law and a number where the appropriation is by a person who of statutory offences. The main fraud offences has received a limited ownership of the of fraud in Scotland, including: in Scotland are: property, subject to restoration at a future • Police Service of Scotland time, or possession of property subject to • common law fraud liability to account for it to the owner. • Financial Conduct Authority • uttering There is an element of breach of trust in • Trading Standards • embezzlement embezzlement making it more serious than • Department for Work and Pensions • statutory frauds. simple theft. In most cases embezzlement involves the appropriation of money. • Crown Office and Procurator Fiscal Service. It is important to note that the Fraud Act 2006 does not apply in Scotland (apart from Statutory frauds s10(1) which increases the maximum In addition there are a wide range of statutory Investigating fraud custodial sentence for fraudulent trading to offences which are closely related to the 10 years). -

CRIMINAL ATTEMPTS at COMMON LAW Edwin R
[Vol. 102 CRIMINAL ATTEMPTS AT COMMON LAW Edwin R. Keedy t GENERAL PRINCIPLES Much has been written on the law of attempts to commit crimes 1 and much more will be written for this is one of the most interesting and difficult problems of the criminal law.2 In many discussions of criminal attempts decisions dealing with common law attempts, stat- utory attempts and aggravated assaults, such as assaults with intent to murder or to rob, are grouped indiscriminately. Since the defini- tions of statutory attempts frequently differ from the common law concepts,8 and since the meanings of assault differ widely,4 it is be- "Professor of Law Emeritus, University of Pennsylvania. 1. See Beale, Criminal Attempts, 16 HARv. L. REv. 491 (1903); Hoyles, The Essentials of Crime, 46 CAN. L.J. 393, 404 (1910) ; Cook, Act, Intention and Motive in the Criminal Law, 26 YALE L.J. 645 (1917) ; Sayre, Criminal Attempts, 41 HARv. L. REv. 821 (1928) ; Tulin, The Role of Penalties in the Criminal Law, 37 YALE L.J. 1048 (1928) ; Arnold, Criminal Attempts-The Rise and Fall of an Abstraction, 40 YALE L.J. 53 (1930); Curran, Criminal and Non-Criminal Attempts, 19 GEo. L.J. 185, 316 (1931); Strahorn, The Effect of Impossibility on Criminal Attempts, 78 U. OF PA. L. Rtv. 962 (1930); Derby, Criminal Attempt-A Discussion of Some New York Cases, 9 N.Y.U.L.Q. REv. 464 (1932); Turner, Attempts to Commit Crimes, 5 CA=. L.J. 230 (1934) ; Skilton, The Mental Element in a Criminal Attempt, 3 U. -

Police Perjury: a Factorial Survey
The author(s) shown below used Federal funds provided by the U.S. Department of Justice and prepared the following final report: Document Title: Police Perjury: A Factorial Survey Author(s): Michael Oliver Foley Document No.: 181241 Date Received: 04/14/2000 Award Number: 98-IJ-CX-0032 This report has not been published by the U.S. Department of Justice. To provide better customer service, NCJRS has made this Federally- funded grant final report available electronically in addition to traditional paper copies. Opinions or points of view expressed are those of the author(s) and do not necessarily reflect the official position or policies of the U.S. Department of Justice. FINAL-FINAL TO NCJRS Police Perjury: A Factorial Survey h4ichael Oliver Foley A dissertation submitted to the Graduate Faculty in Criminal Justice in partial fulfillment of the requirements for the degree of Doctor of Philosophy. The City University of New York. 2000 This document is a research report submitted to the U.S. Department of Justice. This report has not been published by the Department. Opinions or points of view expressed are those of the author(s) and do not necessarily reflect the official position or policies of the U.S. Department of Justice. I... I... , ii 02000 Michael Oliver Foley All Rights Reserved This document is a research report submitted to the U.S. Department of Justice. This report has not been published by the Department. Opinions or points of view expressed are those of the author(s) and do not necessarily reflect the official position or policies of the U.S. -

False Statements and Perjury: an Overview of Federal Criminal Law
False Statements and Perjury: An Overview of Federal Criminal Law Charles Doyle Senior Specialist in American Public Law May 11, 2018 Congressional Research Service 7-5700 www.crs.gov 98-808 False Statements and Perjury: An Overview of Federal Criminal Law Summary Federal courts, Congress, and federal agencies rely upon truthful information in order to make informed decisions. Federal law therefore proscribes providing the federal courts, Congress, or federal agencies with false information. The prohibition takes four forms: false statements; perjury in judicial proceedings; perjury in other contexts; and subornation of perjury. Section 1001 of Title 18 of the United States Code, the general false statement statute, outlaws material false statements in matters within the jurisdiction of a federal agency or department. It reaches false statements in federal court and grand jury sessions as well as congressional hearings and administrative matters but not the statements of advocates or parties in court proceedings. Under Section 1001, a statement is a crime if it is false, regardless of whether it is made under oath. In contrast, an oath is the hallmark of the three perjury statutes in Title 18. The oldest, Section 1621, condemns presenting material false statements under oath in federal official proceedings. Section 1623 of the same title prohibits presenting material false statements under oath in federal court proceedings, although it lacks some of Section 1621’s traditional procedural features, such as a two-witness requirement. Subornation of perjury, barred in Section 1622, consists of inducing another to commit perjury. All four sections carry a penalty of imprisonment for not more than five years, although Section 1001 is punishable by imprisonment for not more than eight years when the offense involves terrorism or one of the various federal sex offenses. -

CRIME How to Respond to Unlawful Behaviour Crime Is an Undeniable Part of Our Lives; Unfortunately We May Find Ourselves Victims
CRIME How to respond to unlawful behaviour Crime is an undeniable part of our lives; unfortunately we may find ourselves victims, perpetrators or witnesses of illegal actions varying in severity. To better understand the legality of certain actions (and inactions) is to be able to make ethical decisions to improve the safety in our communities. Are all crimes the same? NO. There are two categories of offences in the Criminal Code: indictable and summary. The category determines the jurisdiction of trial courts (provincial or superior), the possibility of having a jury trial or a preliminary inquiry, the application of limitation periods and the default maximum penalties. Summary offences are commonly known as the lesser offences. They carry a default maximum penalty (i.e. if not specified in the provision) of 6 months imprisonment and/or 5 000$ fine. They are subject to a limitation period of 6 months to start the prosecution. Indictable offences are commonly known as the most serious offences. They carry a default maximum penalty of 5 years imprisonment. Subject to certain exceptions, there is no statute of limitations. What do I do if I witness a crime? Contact the police as early as possible. Write down any information you can remember to give a complete account to the police or in case you are called to testify at court. If you have any concerns, you should consult a lawyer. What if I committed a crime but didn’t know that it was illegal at the time? As stated by s. 19 of the Criminal Code, “ignorance of the law by a person who commits an offence is not an excuse for committing that offence.” What if I just helped someone commit a crime? (i.e. -

A Timely History of Cheating and Fraud Following Ivey V Genting Casinos (UK)
The honest cheat: a timely history of cheating and fraud following Ivey v Genting Casinos (UK) Ltd t/a Crockfords [2017] UKSC 67 Cerian Griffiths Lecturer in Criminal Law and Criminal Justice, Lancaster University Law School1 Author email: [email protected] Abstract: The UK Supreme Court took the opportunity in Ivey v Genting Casinos (UK) Ltd t/a Crockfords [2017] UKSC 67 to reverse the long-standing, but unpopular, test for dishonesty in R v Ghosh. It reduced the relevance of subjectivity in the test of dishonesty, and brought the civil and the criminal law approaches to dishonesty into line by adopting the test as laid down in Royal Brunei Airlines Sdn Bhd v Tan. This article employs extensive legal historical research to demonstrate that the Supreme Court in Ivey was too quick to dismiss the significance of the historical roots of dishonesty. Through an innovative and comprehensive historical framework of fraud, this article demonstrates that dishonesty has long been a central pillar of the actus reus of deceptive offences. The recognition of such significance permits us to situate the role of dishonesty in contemporary criminal property offences. This historical analysis further demonstrates that the Justices erroneously overlooked centuries of jurisprudence in their haste to unite civil and criminal law tests for dishonesty. 1 I would like to thank Lindsay Farmer, Dave Campbell, and Dave Ellis for giving very helpful feedback on earlier drafts of this article. I would also like to thank Angus MacCulloch, Phil Lawton, and the Lancaster Law School Peer Review College for their guidance in developing this paper. -

Res Judicata and Conspiracy John R
Journal of Criminal Law and Criminology Volume 39 | Issue 1 Article 7 1948 Res Judicata and Conspiracy John R. Gehlbach Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc Part of the Criminal Law Commons, Criminology Commons, and the Criminology and Criminal Justice Commons Recommended Citation John R. Gehlbach, Res Judicata and Conspiracy, 39 J. Crim. L. & Criminology 58 (1948-1949) This Criminal Law is brought to you for free and open access by Northwestern University School of Law Scholarly Commons. It has been accepted for inclusion in Journal of Criminal Law and Criminology by an authorized editor of Northwestern University School of Law Scholarly Commons. CRIMINAL LAW COMMENTS [Vol. 39 has been a tendency to carry its application to extremes. The minority approach of Texas and Maryland seems the more desirable; in other words, a waiver of the right of confrontation should be permitted only when personally requested by the accused, and when he has a full under- standing of the consequences.13 Three problems are raised in each case involving waiver: was the waiver actually made; if so, was it done know- ingly; and even if made with full knowledge, should it be permitted? The rule should not be permitted to operate automatically upon the re- quest of the defendant or his attorney. Some examination into the causes and circumstances which have resulted in the request should be made by the court, and discretion should be used in the granting or denial of such a request. KENN-r H. HANSON Res Judicata and Conspiracy The United States Supreme Court in Sealfon v. -

Criminal Assault Includes Both a Specific Intent to Commit a Battery, and a Battery That Is Otherwise Unprivileged Committed with Only General Intent
QUESTION 5 Don has owned Don's Market in the central city for twelve years. He has been robbed and burglarized ten times in the past ten months. The police have never arrested anyone. At a neighborhood crime prevention meeting, apolice officer told Don of the state's new "shoot the burglar" law. That law reads: Any citizen may defend his or her place of residence against intrusion by a burglar, or other felon, by the use of deadly force. Don moved a cot and a hot plate into the back of the Market and began sleeping there, with a shotgun at the ready. After several weeks of waiting, one night Don heard noises. When he went to the door, he saw several young men running away. It then dawned on him that, even with the shotgun, he might be in a precarious position. He would likely only get one shot and any burglars would get the next ones. With this in mind, he loaded the shotgun and fastened it to the counter, facing the front door. He attached a string to the trigger so that the gun would fire when the door was opened. Next, thinking that when burglars enter it would be better if they damaged as little as possible, he unlocked the front door. He then went out the back window and down the block to sleep at his girlfriend's, where he had been staying for most of the past year. That same night a police officer, making his rounds, tried the door of the Market, found it open, poked his head in, and was severely wounded by the blast. -
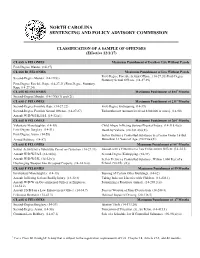
Classification of a Sample of Felony Offenses
NORTH CAROLINA SENTENCING AND POLICY ADVISORY COMMISSION CLASSIFICATION OF A SAMPLE OF OFFENSES (Effective 12/1/17) CLASS A FELONIES Maximum Punishment of Death or Life Without Parole First-Degree Murder. (14-17) CLASS B1 FELONIES Maximum Punishment of Life Without Parole First-Degree Forcible Sexual Offense. (14-27.26)/First-Degree Second-Degree Murder. (14-17(b)) Statutory Sexual Offense. (14-27.29) First-Degree Forcible Rape. (14-27.21)/First-Degree Statutory Rape (14-27.24) CLASS B2 FELONIES Maximum Punishment of 484* Months Second-Degree Murder. (14-17(b)(1) and (2)) CLASS C FELONIES Maximum Punishment of 231* Months Second-Degree Forcible Rape. (14-27.22) First-Degree Kidnapping. (14-39) Second-Degree Forcible Sexual Offense. (14-27.27) Embezzlement (amount involved $100,000 or more). (14-90) Assault W/D/W/I/K/I/S/I. (14-32(a)) CLASS D FELONIES Maximum Punishment of 204* Months Voluntary Manslaughter. (14-18) Child Abuse Inflicting Serious Physical Injury. (14-318.4(a)) First-Degree Burglary. (14-51) Death by Vehicle. (20-141.4(a)(1)) First-Degree Arson. (14-58) Sell or Deliver a Controlled Substance to a Person Under 16 But Armed Robbery. (14-87) More than 13 Years of Age. (90-95(e)(5)) CLASS E FELONIES Maximum Punishment of 88* Months Sexual Activity by a Substitute Parent or Custodian. (14-27.31) Assault with a Firearm on a Law Enforcement Officer. (14-34.5) Assault W/D/W/I/S/I. (14-32(b)) Second-Degree Kidnapping. (14-39) Assault W/D/W/I/K. -

Digital Blackmail As an Emerging Tactic 2016
September 9 DIGITAL BLACKMAIL AS AN EMERGING TACTIC 2016 Digital Blackmail (DB) represents a severe and growing threat to individuals, small businesses, corporations, and government Examining entities. The rapid increase in the use of DB such as Strategies ransomware; the proliferation of variants and growth in their ease of use and acquisition by cybercriminals; weak defenses; Public and and the anonymous nature of the money trail will only increase Private Entities the scale of future attacks. Private sector, non-governmental organization (NGO), and government cybersecurity experts Can Pursue to were brought together by the Office of the Director of National Contain Such Intelligence and the Department of Homeland Security to determine emerging tactics and countermeasures associated Attacks with the threat of DB. In this paper, DB is defined as illicitly acquiring or denying access to sensitive data for the purpose of affecting victims’ behaviors. Threats may be made of lost revenue, the release of intellectual property or sensitive personnel/client information, the destruction of critical data, or reputational damage. For clarity, this paper maps DB activities to traditional blackmail behaviors and explores methods and tools, exploits, protection measures, whether to pay or not pay the ransom, and law enforcement (LE) and government points of contact for incident response. The paper also examines the future of the DB threat. Digital Blackmail as an Emerging Tactic Team Members Name Organization Caitlin Bataillon FBI Lynn Choi-Brewer -

~. Provocation As a Defence to Murder
If you have issues viewing or accessing this file contact us at NCJRS.gov. LAW REFORM COMMISSIONER VICTORIA , r Working Paper No.6 : - I ~. PROVOCATION AS A DEFENCE "~I TO MURDER MELBOURNE 1979 '. NCJf:'~~S SEP 261979 ACQUISITIONS, LAW REFORM COMMISSIONER I VICTORIA . " ! . , ". ~. I :'! .~, . ' .. " \ .. ' , Working Paper No.6 _} " ",!, I .. 1:. : . : ~ , PROVOCATION AS A DEFENCE TO MUR'D'ER MELBOURNE 1979 / Views expressed in this Working Paper are provisional only and such suggestions as are made are tentative. Comment and criticism are invited and it would be greatly appreciated if these could be forwarded before 1st October, 1979. Law Reform Commissioner 155 Queen Street, Melbourne, Vic. 3000. I CONTENTS Paragraph Page Introduction 1 5 What is Provocation? 4 S 19th Century Views 5 6 The Emergence of "The Reasonable Man" and "The Ordinary Man" 9 7 "The Ordinary Man" in Legislation 13 9 "The Reasonable Man" and the Common Law 18 11 The Case of Holmes 20 11 More of "The Reasonable Person" 28 13 Legislative Change 32 15 The New Zealand Crimes Act 1961 37 16 The New Zealand Case 38 16 Victoria Today 41 18 Ever the Problem of "The Ordinary Man" 59 23 A Climate of Reform 64 24 (a) Eire 64 24 (b) England 65 24 (c) U.S.A.- The Model Penal Code . 68 25 (d) South Australia 72 26 Reform for Victoria 76 27 References 31 3 WORKING PAPER No.6 PROVOCATION AS A DEFENCE TO MURDER. Introduction 1. By letter dated the 13th day of March, 1979 The Honourable the Attorney-General acting pursuant to section 8 (b) of the Law Reform Act 1973 referred to the Law Reform Commissioner the following reference:- "To investigate and report upon the necessity for reform of the law relating to provocation as a defence to a charge of murder." 2.