A Probability Programming Language: Development and Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -

LATEX for Beginners
LATEX for Beginners Workbook Edition 5, March 2014 Document Reference: 3722-2014 Preface This is an absolute beginners guide to writing documents in LATEX using TeXworks. It assumes no prior knowledge of LATEX, or any other computing language. This workbook is designed to be used at the `LATEX for Beginners' student iSkills seminar, and also for self-paced study. Its aim is to introduce an absolute beginner to LATEX and teach the basic commands, so that they can create a simple document and find out whether LATEX will be useful to them. If you require this document in an alternative format, such as large print, please email [email protected]. Copyright c IS 2014 Permission is granted to any individual or institution to use, copy or redis- tribute this document whole or in part, so long as it is not sold for profit and provided that the above copyright notice and this permission notice appear in all copies. Where any part of this document is included in another document, due ac- knowledgement is required. i ii Contents 1 Introduction 1 1.1 What is LATEX?..........................1 1.2 Before You Start . .2 2 Document Structure 3 2.1 Essentials . .3 2.2 Troubleshooting . .5 2.3 Creating a Title . .5 2.4 Sections . .6 2.5 Labelling . .7 2.6 Table of Contents . .8 3 Typesetting Text 11 3.1 Font Effects . 11 3.2 Coloured Text . 11 3.3 Font Sizes . 12 3.4 Lists . 13 3.5 Comments & Spacing . 14 3.6 Special Characters . 15 4 Tables 17 4.1 Practical . -
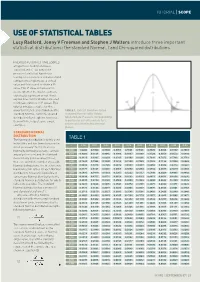
Use of Statistical Tables
TUTORIAL | SCOPE USE OF STATISTICAL TABLES Lucy Radford, Jenny V Freeman and Stephen J Walters introduce three important statistical distributions: the standard Normal, t and Chi-squared distributions PREVIOUS TUTORIALS HAVE LOOKED at hypothesis testing1 and basic statistical tests.2–4 As part of the process of statistical hypothesis testing, a test statistic is calculated and compared to a hypothesised critical value and this is used to obtain a P- value. This P-value is then used to decide whether the study results are statistically significant or not. It will explain how statistical tables are used to link test statistics to P-values. This tutorial introduces tables for three important statistical distributions (the TABLE 1. Extract from two-tailed standard Normal, t and Chi-squared standard Normal table. Values distributions) and explains how to use tabulated are P-values corresponding them with the help of some simple to particular cut-offs and are for z examples. values calculated to two decimal places. STANDARD NORMAL DISTRIBUTION TABLE 1 The Normal distribution is widely used in statistics and has been discussed in z 0.00 0.01 0.02 0.03 0.050.04 0.05 0.06 0.07 0.08 0.09 detail previously.5 As the mean of a Normally distributed variable can take 0.00 1.0000 0.9920 0.9840 0.9761 0.9681 0.9601 0.9522 0.9442 0.9362 0.9283 any value (−∞ to ∞) and the standard 0.10 0.9203 0.9124 0.9045 0.8966 0.8887 0.8808 0.8729 0.8650 0.8572 0.8493 deviation any positive value (0 to ∞), 0.20 0.8415 0.8337 0.8259 0.8181 0.8103 0.8206 0.7949 0.7872 0.7795 0.7718 there are an infinite number of possible 0.30 0.7642 0.7566 0.7490 0.7414 0.7339 0.7263 0.7188 0.7114 0.7039 0.6965 Normal distributions. -

Software Developement Tools Introduction to Software Building
Software Developement Tools Introduction to software building SED & friends Outline 1. an example 2. what is software building? 3. tools 4. about CMake SED & friends – Introduction to software building 2 1 an example SED & friends – Introduction to software building 3 - non-portability: works only on a Unix systems, with mpicc shortcut and MPI libraries and headers installed in standard directories - every build, we compile all files - 0 level: hit the following line: mpicc -Wall -o heat par heat par.c heat.c mat utils.c -lm - 0.1 level: write a script (bash, csh, Zsh, ...) • drawbacks: Example • we want to build the parallel program solving heat equation: SED & friends – Introduction to software building 4 - non-portability: works only on a Unix systems, with mpicc shortcut and MPI libraries and headers installed in standard directories - every build, we compile all files - 0.1 level: write a script (bash, csh, Zsh, ...) • drawbacks: Example • we want to build the parallel program solving heat equation: - 0 level: hit the following line: mpicc -Wall -o heat par heat par.c heat.c mat utils.c -lm SED & friends – Introduction to software building 4 - non-portability: works only on a Unix systems, with mpicc shortcut and MPI libraries and headers installed in standard directories - every build, we compile all files • drawbacks: Example • we want to build the parallel program solving heat equation: - 0 level: hit the following line: mpicc -Wall -o heat par heat par.c heat.c mat utils.c -lm - 0.1 level: write a script (bash, csh, Zsh, ...) SED -

Factor — Factor Analysis
Title stata.com factor — Factor analysis Description Quick start Menu Syntax Options for factor and factormat Options unique to factormat Remarks and examples Stored results Methods and formulas References Also see Description factor and factormat perform a factor analysis of a correlation matrix. The commands produce principal factor, iterated principal factor, principal-component factor, and maximum-likelihood factor analyses. factor and factormat display the eigenvalues of the correlation matrix, the factor loadings, and the uniqueness of the variables. factor expects data in the form of variables, allows weights, and can be run for subgroups. factormat is for use with a correlation or covariance matrix. Quick start Principal-factor analysis using variables v1 to v5 factor v1 v2 v3 v4 v5 As above, but retain at most 3 factors factor v1-v5, factors(3) Principal-component factor analysis using variables v1 to v5 factor v1-v5, pcf Maximum-likelihood factor analysis factor v1-v5, ml As above, but perform 50 maximizations with different starting values factor v1-v5, ml protect(50) As above, but set the seed for reproducibility factor v1-v5, ml protect(50) seed(349285) Principal-factor analysis based on a correlation matrix cmat with a sample size of 800 factormat cmat, n(800) As above, retain only factors with eigenvalues greater than or equal to 1 factormat cmat, n(800) mineigen(1) Menu factor Statistics > Multivariate analysis > Factor and principal component analysis > Factor analysis factormat Statistics > Multivariate analysis > Factor and principal component analysis > Factor analysis of a correlation matrix 1 2 factor — Factor analysis Syntax Factor analysis of data factor varlist if in weight , method options Factor analysis of a correlation matrix factormat matname, n(#) method options factormat options matname is a square Stata matrix or a vector containing the rowwise upper or lower triangle of the correlation or covariance matrix. -

Unix Tools 2
Unix Tools 2 Jeff Freymueller Outline § Variables as a collec9on of words § Making basic output and input § A sampler of unix tools: remote login, text processing, slicing and dicing § ssh (secure shell – use a remote computer!) § grep (“get regular expression”) § awk (a text processing language) § sed (“stream editor”) § tr (translator) § A smorgasbord of examples Variables as a collec9on of words § The shell treats variables as a collec9on of words § set files = ( file1 file2 file3 ) § This sets the variable files to have 3 “words” § If you want the whole variable, access it with $files § If you want just the second word, use $files[2] § The shell doesn’t count characters, only words Basic output: echo and cat § echo string § Writes a line to standard output containing the text string. This can be one or more words, and can include references to variables. § echo “Opening files” § echo “working on week $week” § echo –n “no carriage return at the end of this” § cat file § Sends the contents of a file to standard output Input, Output, Pipes § Output to file, vs. append to file. § > filename creates or overwrites the file filename § >> filename appends output to file filename § Take input from file, or from “inline input” § < filename take all input from file filename § <<STRING take input from the current file, using all lines un9l you get to the label STRING (see next slide for example) § Use a pipe § date | awk '{print $1}' Example of “inline input” gpsdisp << END • Many programs, especially Okmok2002-2010.disp Okmok2002-2010.vec older ones, interac9vely y prompt you to enter input Okmok2002-2010.gmtvec • You can automate (or self- y Okmok2002-2010.newdisp document) this by using << Okmok2002_mod.stacov • Standard input is set to the 5 contents of this file 5 Okmok2010.stacov between << END and END 5 • You can use any label, not 5 just “END”. -

Computer Routines for Probability Distributions, Random Numbers, and Related Functions
COMPUTER ROUTINES FOR PROBABILITY DISTRIBUTIONS, RANDOM NUMBERS, AND RELATED FUNCTIONS By W.H. Kirby Water-Resources Investigations Report 83 4257 (Revision of Open-File Report 80 448) 1983 UNITED STATES DEPARTMENT OF THE INTERIOR WILLIAM P. CLARK, Secretary GEOLOGICAL SURVEY Dallas L. Peck, Director For additional information Copies of this report can write to: be purchased from: Chief, Surface Water Branch Open-File Services Section U.S. Geological Survey, WRD Western Distribution Branch 415 National Center Box 25425, Federal Center Reston, Virginia 22092 Denver, Colorado 80225 (Telephone: (303) 234-5888) CONTENTS Introduction............................................................ 1 Source code availability................................................ 2 Linkage information..................................................... 2 Calling instructions.................................................... 3 BESFIO - Bessel function IQ......................................... 3 BETA? - Beta probabilities......................................... 3 CHISQP - Chi-square probabilities................................... 4 CHISQX - Chi-square quantiles....................................... 4 DATME - Date and time for printing................................. 4 DGAMMA - Gamma function, double precision........................... 4 DLGAMA - Log-gamma function, double precision....................... 4 ERF - Error function............................................. 4 EXPIF - Exponential integral....................................... 4 GAMMA -

(LS-Factor) for Modeling Soil Erosion by Water
Geosciences 2015, 5, 117-126; doi:10.3390/geosciences5020117 OPEN ACCESS geosciences ISSN 2076-3263 www.mdpi.com/journal/geosciences Short Communication A New European Slope Length and Steepness Factor (LS-Factor) for Modeling Soil Erosion by Water Panos Panagos 1,*, Pasquale Borrelli 1,† and Katrin Meusburger 2,† 1 European Commission, Joint Research Centre, Institute for Environment and Sustainability, Via Enrico Fermi 2749, I-21027 Ispra (VA), Italy; E-Mail: [email protected] 2 Environmental Geosciences, University of Basel, Bernoullistrasse 30, 4056 Basel, Switzerland; E-Mail: [email protected] † These authors contributed equally to this work. * Author to whom correspondence should be addressed; E-Mail: [email protected]; Tel.: +39-0332-785574; Fax: +39-0332-786394. Academic Editor: Jesus Martinez-Frias Received: 24 December 2014 / Accepted: 23 March 2015 / Published: 3 April 2015 Abstract: The Universal Soil Loss Equation (USLE) model is the most frequently used model for soil erosion risk estimation. Among the six input layers, the combined slope length and slope angle (LS-factor) has the greatest influence on soil loss at the European scale. The S-factor measures the effect of slope steepness, and the L-factor defines the impact of slope length. The combined LS-factor describes the effect of topography on soil erosion. The European Soil Data Centre (ESDAC) developed a new pan-European high-resolution soil erosion assessment to achieve a better understanding of the spatial and temporal patterns of soil erosion in Europe. The LS-calculation was performed using the original equation proposed by Desmet and Govers (1996) and implemented using the System for Automated Geoscientific Analyses (SAGA), which incorporates a multiple flow algorithm and contributes to a precise estimation of flow accumulation. -

Useful Commands in Linux and Other Tools for Quality Control
Useful commands in Linux and other tools for quality control Ignacio Aguilar INIA Uruguay 05-2018 Unix Basic Commands pwd show working directory ls list files in working directory ll as before but with more information mkdir d make a directory d cd d change to directory d Copy and moving commands To copy file cp /home/user/is . To copy file directory cp –r /home/folder . to move file aa into bb in folder test mv aa ./test/bb To delete rm yy delete the file yy rm –r xx delete the folder xx Redirections & pipe Redirection useful to read/write from file !! aa < bb program aa reads from file bb blupf90 < in aa > bb program aa write in file bb blupf90 < in > log Redirections & pipe “|” similar to redirection but instead to write to a file, passes content as input to other command tee copy standard input to standard output and save in a file echo copy stream to standard output Example: program blupf90 reads name of parameter file and writes output in terminal and in file log echo par.b90 | blupf90 | tee blup.log Other popular commands head file print first 10 lines list file page-by-page tail file print last 10 lines less file list file line-by-line or page-by-page wc –l file count lines grep text file find lines that contains text cat file1 fiel2 concatenate files sort sort file cut cuts specific columns join join lines of two files on specific columns paste paste lines of two file expand replace TAB with spaces uniq retain unique lines on a sorted file head / tail $ head pedigree.txt 1 0 0 2 0 0 3 0 0 4 0 0 5 0 0 6 0 0 7 0 0 8 0 0 9 0 0 10 -

5 Command Line Functions by Barbara C
ADAPS: Chapter 5. Command Line Functions 5 Command Line Functions by Barbara C. Hoopes and James F. Cornwall This chapter describes ADAPS command line functions. These are functions that are executed from the UNIX command line instead of from ADAPS menus, and that may be run manually or by automated means such as “cron” jobs. Most of these functions are NOT accessible from the ADAPS menus. These command line functions are described in detail below. 5.1 Hydra Although Hydra is available from ADAPS at the PR sub-menu, Edit Time Series Data using Hydra (TS_EDIT), it can also be started from the command line. However, to start Hydra outside of ADAPS, a DV or UV RDB file needs to be available to edit. The command is “hydra rdb_file_name.” For a complete description of using Hydra, refer to Section 4.5.2 Edit Time-Series Data using Hydra (TS_EDIT). 5.2 nwrt2rdb This command is used to output rating information in RDB format. It writes RDB files with a table containing the rating equation parameters or the rating point pairs, with all other information contained in the RDB comments. The following arguments can be used with this command: nwrt2rdb -ooutfile -zdbnum -aagency -nstation -dddid -trating_type -irating_id -e (indicates to output ratings in expanded form; it is ignored for equation ratings.) -l loctzcd (time zone code or local time code "LOC") -m (indicates multiple output files.) -r (rounding suppression) Rules • If -o is omitted, nwrt2rdb writes to stdout; AND arguments -n, -d, -t, and -i must be present. • If -o is present, no other arguments are required, and the program will use ADAPS routines to prompt for them. -

Basic Plotting Codes in R
The Basics of R for Windows We will use the data set timetrial.repeated.dat to learn some basic code in R for Windows. Commands will be shown in a different font, e.g., read.table, after the command line prompt, shown here as >. After you open R, type your commands after the prompt in what is called the Console window. Do not type the prompt, just the command. R stores the variables you create in a working directory. From the File menu, you need to first change the working directory to the directory where your data are stored. 1. Reading in data files Download the data file from www.biostat.umn.edu/~lynn/correlated.html to your local disk directory, go to File -> Change Directory to select that directory, and then read the data in: > contact = read.table(file="timetrial.repeated.dat", header=T) Note: if the first row of the data file had data instead of variable names, you would need to use header=F in the read.table command. Now you have named the data set contact, which you can then see in R just by typing its name: > contact or you can look at, for example, just the first 10 rows of the data set: > contact[1:10,] time sex age shape trial subj 1 2.68 M 31 Box 1 1 2 4.14 M 31 Box 2 1 3 7.22 M 31 Box 3 1 4 8.00 M 31 Box 4 1 5 7.09 M 30 Box 1 2 6 8.55 M 30 Box 2 2 7 8.79 M 30 Box 3 2 8 9.68 M 30 Box 4 2 9 6.05 M 30 Box 1 3 10 6.25 M 30 Box 2 3 This data set has 6 variables, one each in a column, where sex and shape are character valued. -

PS TEXT EDIT Reference Manual Is Designed to Give You a Complete Is About Overview of TEDIT
Information Management Technology Library PS TEXT EDIT™ Reference Manual Abstract This manual describes PS TEXT EDIT, a multi-screen block mode text editor. It provides a complete overview of the product and instructions for using each command. Part Number 058059 Tandem Computers Incorporated Document History Edition Part Number Product Version OS Version Date First Edition 82550 A00 TEDIT B20 GUARDIAN 90 B20 October 1985 (Preliminary) Second Edition 82550 B00 TEDIT B30 GUARDIAN 90 B30 April 1986 Update 1 82242 TEDIT C00 GUARDIAN 90 C00 November 1987 Third Edition 058059 TEDIT C00 GUARDIAN 90 C00 July 1991 Note The second edition of this manual was reformatted in July 1991; no changes were made to the manual’s content at that time. New editions incorporate any updates issued since the previous edition. Copyright All rights reserved. No part of this document may be reproduced in any form, including photocopying or translation to another language, without the prior written consent of Tandem Computers Incorporated. Copyright 1991 Tandem Computers Incorporated. Contents What This Book Is About xvii Who Should Use This Book xvii How to Use This Book xvii Where to Go for More Information xix What’s New in This Update xx Section 1 Introduction to TEDIT What Is PS TEXT EDIT? 1-1 TEDIT Features 1-1 TEDIT Commands 1-2 Using TEDIT Commands 1-3 Terminals and TEDIT 1-3 Starting TEDIT 1-4 Section 2 TEDIT Topics Overview 2-1 Understanding Syntax 2-2 Note About the Examples in This Book 2-3 BALANCED-EXPRESSION 2-5 CHARACTER 2-9 058059 Tandem Computers