Javaxpcom: Mozilla Firefox Scripting
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Servoy Stuff Browser Suite FAQ
Servoy Stuff Browser Suite FAQ Servoy Stuff Browser Suite FAQ Please read carefully: the following contains important information about the use of the Browser Suite in its current version. What is it? It is a suite of native bean components and plugins all Servoy-Aware and tightly integrated with the Servoy platform: - a browser bean - a flash player bean - a html editor bean - a client plugin to rule them all - a server plugin to setup a few admin flags - an installer to help deployment What version of Servoy is supported? - Servoy 5+ Servoy 4.1.8+ will be supported, starting with version 0.9.40+, except for Mac OS X developer (client will work though) What OS/platforms are currently supported? In Developer: - Windows all platform - Mac OS X 10.5+ - Linux GTK based In Smart client: - Windows all platform - Mac OS X 10.5+ - Linux GTK based The web client is not currently supported, although a limited support might come in the future if there is enough demand for it… What Java versions are currently supported? - Windows: java 5 or java 6 (except updates 10 to 14) – 32 and 64-bit - Mac OS X: java 5 or java 6 – 32 and 64-bit - Linux: java 6 (except updates 10 to 14) – 32 and 64-bit Where can I get it? http://www.servoyforge.net/projects/browsersuite What is it made of? It is build on the powerful DJ-NativeSwing project ( http://djproject.sourceforge.net/ns ) v0.9.9 This library is using the Eclipse SWT project ( http://www.eclipse.org/swt ) v3.6.1 And various other projects like the JNA project ( https://jna.dev.java.net/ ) v3.2.4 The XULRunner -
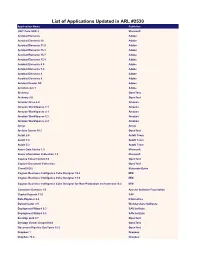
List of Applications Updated in ARL #2530
List of Applications Updated in ARL #2530 Application Name Publisher .NET Core SDK 2 Microsoft Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Application Name Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Alchemy OpenText Alchemy 9.0 OpenText Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Ansys Ansys Archive Server 10.1 OpenText AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team Azure Data Studio 1.9 Microsoft Azure Information Protection 1.0 Microsoft Captiva Cloud Toolkit 3.0 OpenText Capture Document Extraction OpenText CloneDVD 2 Elaborate Bytes Cognos Business Intelligence Cube Designer 10.2 IBM Cognos Business Intelligence Cube Designer 11.0 IBM Cognos Business Intelligence Cube Designer for Non-Production environment 10.2 IBM Commons Daemon 1.0 Apache Software Foundation Crystal Reports 11.0 SAP Data Explorer 8.6 Informatica DemoCreator 3.5 Wondershare Software Deployment Wizard 9.3 SAS Institute Deployment Wizard 9.4 SAS Institute Desktop Link 9.7 OpenText Desktop Viewer Unspecified OpenText Document Pipeline DocTools 10.5 OpenText Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox Dropbox 78.4 Dropbox Dropbox 79.4 Dropbox Dropbox 81.4 -
Open Source Software Notice
Open Source Software Notice This document describes open source software contained in LG Smart TV SDK. Introduction This chapter describes open source software contained in LG Smart TV SDK. Terms and Conditions of the Applicable Open Source Licenses Please be informed that the open source software is subject to the terms and conditions of the applicable open source licenses, which are described in this chapter. | 1 Contents Introduction............................................................................................................................................................................................. 4 Open Source Software Contained in LG Smart TV SDK ........................................................... 4 Revision History ........................................................................................................................ 5 Terms and Conditions of the Applicable Open Source Licenses..................................................................................... 6 GNU Lesser General Public License ......................................................................................... 6 GNU Lesser General Public License ....................................................................................... 11 Mozilla Public License 1.1 (MPL 1.1) ....................................................................................... 13 Common Public License Version v 1.0 .................................................................................... 18 Eclipse Public License Version -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Peer Participation and Software
Peer Participation and Software This report was made possible by the grants from the John D. and Cath- erine T. MacArthur Foundation in connection with its grant-making initiative on Digital Media and Learning. For more information on the initiative visit www.macfound.org. The John D. and Catherine T. MacArthur Foundation Reports on Digital Media and Learning Peer Participation and Software: What Mozilla Has to Teach Government by David R. Booth The Future of Learning Institutions in a Digital Age by Cathy N. Davidson and David Theo Goldberg with the assistance of Zoë Marie Jones The Future of Thinking: Learning Institutions in a Digital Age by Cathy N. Davidson and David Theo Goldberg with the assistance of Zoë Marie Jones New Digital Media and Learning as an Emerging Area and “Worked Examples” as One Way Forward by James Paul Gee Living and Learning with New Media: Summary of Findings from the Digital Youth Project by Mizuko Ito, Heather Horst, Matteo Bittanti, danah boyd, Becky Herr-Stephenson, Patricia G. Lange, C. J. Pascoe, and Laura Robinson with Sonja Baumer, Rachel Cody, Dilan Mahendran, Katynka Z. Martínez, Dan Perkel, Christo Sims, and Lisa Tripp Young People, Ethics, and the New Digital Media: A Synthesis from the GoodPlay Project by Carrie James with Katie Davis, Andrea Flores, John M. Francis, Lindsay Pettingill, Margaret Rundle, and Howard Gardner Confronting the Challenges of Participatory Culture: Media Education for the 21st Century by Henry Jenkins (P.I.) with Ravi Purushotma, Margaret Weigel, Katie Clinton, and Alice J. Robison The Civic Potential of Video Games by Joseph Kahne, Ellen Middaugh, and Chris Evans Peer Production and Software What Mozilla Has to Teach Government David R. -

Cross Site Scripting Attacks Xss Exploits and Defense.Pdf
436_XSS_FM.qxd 4/20/07 1:18 PM Page ii 436_XSS_FM.qxd 4/20/07 1:18 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and deliv- ering those books in media and formats that fit the demands of our customers. We are also committed to extending the utility of the book you purchase via additional mate- rials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value- added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of expertise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in downloadable Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -

Visual Validation of SSL Certificates in the Mozilla Browser Using Hash Images
CS Senior Honors Thesis: Visual Validation of SSL Certificates in the Mozilla Browser using Hash Images Hongxian Evelyn Tay [email protected] School of Computer Science Carnegie Mellon University Advisor: Professor Adrian Perrig Electrical & Computer Engineering Engineering & Public Policy School of Computer Science Carnegie Mellon University Monday, May 03, 2004 Abstract Many internet transactions nowadays require some form of authentication from the server for security purposes. Most browsers are presented with a certificate coming from the other end of the connection, which is then validated against root certificates installed in the browser, thus establishing the server identity in a secure connection. However, an adversary can install his own root certificate in the browser and fool the client into thinking that he is connected to the correct server. Unless the client checks the certificate public key or fingerprint, he would never know if he is connected to a malicious server. These alphanumeric strings are hard to read and verify against, so most people do not take extra precautions to check. My thesis is to implement an additional process in server authentication on a browser, using human recognizable images. The process, Hash Visualization, produces unique images that are easily distinguishable and validated. Using a hash algorithm, a unique image is generated using the fingerprint of the certificate. Images are easily recognizable and the user can identify the unique image normally seen during a secure AND accurate connection. By making a visual comparison, the origin of the root certificate is known. 1. Introduction: The Problem 1.1 SSL Security The SSL (Secure Sockets Layer) Protocol has improved the state of web security in many Internet transactions, but its complexity and neglect of human factors has exposed several loopholes in security systems that use it. -

IT Acronyms.Docx
List of computing and IT abbreviations /.—Slashdot 1GL—First-Generation Programming Language 1NF—First Normal Form 10B2—10BASE-2 10B5—10BASE-5 10B-F—10BASE-F 10B-FB—10BASE-FB 10B-FL—10BASE-FL 10B-FP—10BASE-FP 10B-T—10BASE-T 100B-FX—100BASE-FX 100B-T—100BASE-T 100B-TX—100BASE-TX 100BVG—100BASE-VG 286—Intel 80286 processor 2B1Q—2 Binary 1 Quaternary 2GL—Second-Generation Programming Language 2NF—Second Normal Form 3GL—Third-Generation Programming Language 3NF—Third Normal Form 386—Intel 80386 processor 1 486—Intel 80486 processor 4B5BLF—4 Byte 5 Byte Local Fiber 4GL—Fourth-Generation Programming Language 4NF—Fourth Normal Form 5GL—Fifth-Generation Programming Language 5NF—Fifth Normal Form 6NF—Sixth Normal Form 8B10BLF—8 Byte 10 Byte Local Fiber A AAT—Average Access Time AA—Anti-Aliasing AAA—Authentication Authorization, Accounting AABB—Axis Aligned Bounding Box AAC—Advanced Audio Coding AAL—ATM Adaptation Layer AALC—ATM Adaptation Layer Connection AARP—AppleTalk Address Resolution Protocol ABCL—Actor-Based Concurrent Language ABI—Application Binary Interface ABM—Asynchronous Balanced Mode ABR—Area Border Router ABR—Auto Baud-Rate detection ABR—Available Bitrate 2 ABR—Average Bitrate AC—Acoustic Coupler AC—Alternating Current ACD—Automatic Call Distributor ACE—Advanced Computing Environment ACF NCP—Advanced Communications Function—Network Control Program ACID—Atomicity Consistency Isolation Durability ACK—ACKnowledgement ACK—Amsterdam Compiler Kit ACL—Access Control List ACL—Active Current -

Enabling TLS 1.2 in Major Browsers
Enabling TLS 1.2 in Major Browsers Table of Contents Updating Microsoft Internet Explorer ...................................................................................................................................................... 2 Enabling or Disabling TLS Protocols in Internet Explorer .................................................................................................................... 2 Updating Mozilla Firefox ........................................................................................................................................................................... 3 Enabling or Disabling TLS Protocols in Firefox .................................................................................................................................... 4 Updating Google Chrome ......................................................................................................................................................................... 5 Enabling or Disabling TLS Protocols in Chrome .................................................................................................................................. 5 Updating Apple Safari ............................................................................................................................................................................... 7 Enabling or Disabling TLS Protocols in Apple Safari ............................................................................................................................ 7 Appendix -

Development Production Line the Short Story
Development Production Line The Short Story Jene Jasper Copyright © 2007-2018 freedumbytes.dev.net (Free Dumb Bytes) Published 3 July 2018 4.0-beta Edition While every precaution has been taken in the preparation of this installation manual, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License. To get an idea of the Development Production Line take a look at the following Application Integration overview and Maven vs SonarQube Quality Assurance reports comparison. 1. Operating System ......................................................................................................... 1 1.1. Windows ........................................................................................................... 1 1.1.1. Resources ................................................................................................ 1 1.1.2. Desktop .................................................................................................. 1 1.1.3. Explorer .................................................................................................. 1 1.1.4. Windows 7 Start Menu ................................................................................ 2 1.1.5. Task Manager replacement ........................................................................... 3 1.1.6. Resource Monitor ..................................................................................... -

A Declarative Approach Based on Xforms
Helsinki University of Technology Publications in Telecommunications Software and Multimedia Teknillisen korkeakoulun tietoliikenneohjelmistojen ja multimedian julkaisuja Espoo 2006 TML-A16 WEB USER INTERACTION - A DECLARATIVE APPROACH BASED ON XFORMS Mikko Honkala Dissertation for the degree of Doctor of Science in Technology to be presented with due permission of the Department of Computer Science and Engineering, for pub- lic examination and debate in Auditorium T2 at Helsinki University of Technology (Espoo, Finland) on the 12th of January, 2007, at 12 noon. Helsinki University of Technology Department of Computer Science and Engineering Telecommunications Software and Multimedia Laboratory Teknillinen korkeakoulu Tietotekniikan osasto Tietoliikenneohjelmistojen ja multimedian laboratorio Distribution: Helsinki University of Technology Telecommunications Software and Multimedia Laboratory P.O.Box 5400 FIN-02015 HUT Tel. +358-9-451 2870 Fax. +358-9-451 5014 c Mikko Honkala ISBN-13 978-951-22-8565-5 ISBN-10 951-22-8565-7 ISSN 1456-7911 ISBN-13 978-951-22-8566-2 (PDF) ISBN-10 951-22-8566-5 (PDF) ISSN 1455 9722 (PDF) URL: http://lib.tkk.fi/Diss/ Otamedia Oy Espoo 2006 ABSTRACT Author Mikko Honkala Title Web User Interaction - a Declarative Approach Based on XForms Published Doctoral thesis, Helsinki University of Technology, 2006 Keywords XML, User Interfaces, User Interaction, XForms, UIDL, XHTML This thesis studies next-generation web user interaction definition languages, as well as browser software architectures. The motivation comes from new end-user requirements for web applications: demand for higher interaction, adaptation for mobile and multimodal usage, and rich multimedia content. At the same time, there is a requirement for non- programmers to be able to author, customize, and maintain web user interfaces. -

Django and Mongodb
1. .bookmarks . 5 2. 1.1 Development Cycle . 5 3. Creating and Deleting Indexes . 5 4. Diagnostic Tools . 5 5. Django and MongoDB . 5 6. Getting Started . 5 7. International Documentation . 6 8. Monitoring . 6 9. Older Downloads . 6 10. PyMongo and mod_wsgi . 6 11. Python Tutorial . 6 12. Recommended Production Architectures . 6 13. Shard v0.7 . 7 14. v0.8 Details . 7 15. v0.9 Details . 7 16. v1.0 Details . 7 17. v1.5 Details . 7 18. v2.0 Details . 8 19. Building SpiderMonkey . 8 20. Documentation . 8 21. Dot Notation . 8 22. Dot Notation . 23. Getting the Software . 8 24. Language Support . 8 25. Mongo Administration Guide . 9 26. Working with Mongo Objects and Classes in Ruby . 9 27. MongoDB Language Support . 9 28. Community Info . 9 29. Internals . 9 30. TreeNavigation . 10 31. Old Pages . 10 31.1 Storing Data . 10 31.2 Indexes in Mongo . 10 31.3 HowTo . 10 31.4 Searching and Retrieving . 10 31.4.1 Locking . 10 31.5 Mongo Developers' Guide . 11 31.6 Locking in Mongo . 11 31.7 Mongo Database Administration . ..