Implicit Secondary Authentication for Sustainable SMS Authentication
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Wi-Fi® Smart Device Enablement Kit User Guide
ATWINC15x0 Smart Device Kit Wi-Fi® Smart Device Enablement Kit User Guide Introduction The Wi-Fi Smart Device Enablement Kit is a small and easy demonstration and development platform for Internet of Things (IoT) solutions. It is designed to demonstrate the design of typical IoT applications. The kit is controlled by a SAML21G18B host MCU. It is equipped with an ATWINC15x0 IEEE® 802.11 b/g/n network controller, an ATECC608A CryptoAuthentication™ device, an MCP73833 Li-Ion/Li-Po charge management controller, a MIC5317 High PSRR LDO, BME280 environment sensor and VEML6030 light sensor. It can be programmed and debugged with an Atmel-ICE programmer through SWD interface or programmed with an SAM-BA® in-system programmer through USB interface. The Wi-Fi Smart Device Enablement Kit is pre-programmed and configured for demonstrating connectivity to the AWS® IoT cloud, working with Amazon Alexa®. The user can speak to an Alexa- enabled device (for example, Echo Dot®) to get the sensor data and control LED of the kit. A mobile application is provided for board registration and network configuration. It can be used to monitor and control the kit. As an IoT edge, this firmware provides the control, monitoring, Wi-Fi connectivity and security functions in a typical IoT scenario. This board is used for evaluation/demonstration purposes only. © 2019 Microchip Technology Inc. User Guide DS50002880A-page 1 ATWINC15x0 Smart Device Kit Table of Contents Introduction .....................................................................................................................1 -

Download This PDF File
Paper—Defining Stable Touch Area based on a Large-Screen Smart Device in 3D-Touch Interface Defining Stable Touch Area based on a Large-Screen Smart Device in 3D-Touch Interface https://doi.org/10.3991/ijim.v13i02.10153 YounghoonSeo, Dongryeol Shin, Choonsung Nam * Sungkyunkwan University, Suwon, Republic of Korea( ) [email protected] Abstract—Touch interface technologies for mobile devices are essentially in use. The purpose of such touch interfaces is to run an application by touching a screen with a user’s finger or to implement various functions on the device. When the user has an attempt to use the touch interface, users tend to grab the mobile device with one hand. Because of the existence of untouchable areas to which the user cannot reach with the user’s fingers, it is possible to occur for a case where the user is not able to touch a specific area on the screen accurately. This results in some issues that the mobile device does not carry out the user’s desired function and the execution time is delayed due to the wrong implemen- tation. Therefore, there is a need to distinguish the area where the user can sta- bly input the touch interface from the area where the users cannot and to over- come the problems of the unstable touch area. Furthermore, when the size of the screen increases, these issues will become more serious because of an increase in the unstable touch areas. Especially, an interface that receives position and force data like 3D-touch requires the stable area setting different from the con- ventional 2D-touch. -

Develop Mobile Applications with Oracle Adf Mobile
ORACLE DATA SHEET Disclaimer: The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decision. The development, release, and timing of any features or functionality described for Oracle's products remains at the sole discretion of Oracle. DEVELOP MOBILE APPLI CATIONS WITH ORACLE ADF MOBILE KEY FEATURES AND BENEFITS Oracle JDeveloper 11g R2 enables developers to rapidly develop EXTEND YOUR APPLICATION REACH TO MOBILE DEVICES applications that run on multiple mobile devices. With the powerful THE FUSION WAY. Oracle Application Development Framework (Oracle ADF) Mobile, developers can quickly develop applications for multiple mobile FEATURES • Visual and declarative platforms such as iOS. This simplifies the path forward as mobile development platforms evolve and delivers compelling mobile applications for • Mobile applications for rich, on-device clients for multiple users. mobile platforms such as iOS • Extends the power of Fusion Mobile Enterprise Challenges Middleware to mobile applications Mobile access to enterprise applications is fast becoming a standard part of corporate life. Such applications increase organizational efficiency because mobile BENEFITS devices are more readily at hand than their desktop counterparts. • Develop once, and deploy to many devices and channels However, the speed with which mobile platforms are evolving creates challenges as • Single IDE for mobile and enterprises define their mobile strategies. Smart phones such as iPhone are powerful non-mobile development platforms, but different mobile platforms offers different tools and languages for • Single framework for mobile and desktop enterprise developers. -
![Arxiv:1809.10387V1 [Cs.CR] 27 Sep 2018 IEEE TRANSACTIONS on SUSTAINABLE COMPUTING, VOL](https://docslib.b-cdn.net/cover/6402/arxiv-1809-10387v1-cs-cr-27-sep-2018-ieee-transactions-on-sustainable-computing-vol-586402.webp)
Arxiv:1809.10387V1 [Cs.CR] 27 Sep 2018 IEEE TRANSACTIONS on SUSTAINABLE COMPUTING, VOL
IEEE TRANSACTIONS ON SUSTAINABLE COMPUTING, VOL. X, NO. X, MONTH YEAR 0 This work has been accepted in IEEE Transactions on Sustainable Computing. DOI: 10.1109/TSUSC.2018.2808455 URL: http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=8299447&isnumber=7742329 IEEE Copyright Notice: c 2018 IEEE. Personal use of this material is permitted. Permission from IEEE must be obtained for all other uses, in any current or future media, including reprinting/republishing this material for advertising or promotional purposes, creating new collective works, for resale or redistribution to servers or lists, or reuse of any copyrighted component of this work in other works. arXiv:1809.10387v1 [cs.CR] 27 Sep 2018 IEEE TRANSACTIONS ON SUSTAINABLE COMPUTING, VOL. X, NO. X, MONTH YEAR 1 Identification of Wearable Devices with Bluetooth Hidayet Aksu, A. Selcuk Uluagac, Senior Member, IEEE, and Elizabeth S. Bentley Abstract With wearable devices such as smartwatches on the rise in the consumer electronics market, securing these wearables is vital. However, the current security mechanisms only focus on validating the user not the device itself. Indeed, wearables can be (1) unauthorized wearable devices with correct credentials accessing valuable systems and networks, (2) passive insiders or outsider wearable devices, or (3) information-leaking wearables devices. Fingerprinting via machine learning can provide necessary cyber threat intelligence to address all these cyber attacks. In this work, we introduce a wearable fingerprinting technique focusing on Bluetooth classic protocol, which is a common protocol used by the wearables and other IoT devices. Specifically, we propose a non-intrusive wearable device identification framework which utilizes 20 different Machine Learning (ML) algorithms in the training phase of the classification process and selects the best performing algorithm for the testing phase. -

Twistin: Tangible Authentication of Smart Devices Via Motion Co-Analysis with a Smartwatch
TwistIn: Tangible Authentication of Smart Devices via Motion Co-analysis with a Smartwatch Ho Man Colman Leung, Chi Wing Fu, Pheng Ann Heng The Chinese University of Hong Kong, Hong Kong Shenzhen Key Laboratory of Virtual Reality and Human Interaction Technology, SIAT, CAS, China Motivation Method Observation: There will be more connected devices in the future with smaller size and limited interface, IoT Units Installed Base by Category 25.00 20.00 15.00 10.00 Business: Vertical-Specific 5.00 Business: Cross-Industry Billions of Units Billions 0.00 Consumer 2016 2017 2018 2020 Source: Gartner (January 2017) 1. The user is wearing an already-authenticated smartwatch 2. A smart device is picked up by the user 3. The user performs the TwistIn gesture simultaneously on both devices 4. The motions of the devices are co-analyzed 5. The smart device is authenticated Bluetooth Tracker, Smart Glasses, Bluetooth Toy, Speaker, 360 Camera but existing methods are ineffective. Challenges People hold the devices differently and each device has its own reference frame. → Optimize a transformation matrix to align two devices’ motion data The data is noisy due to motion of the wrist joint → Filter out the unwanted motion by extracting the forearm rotation using rotation decomposition Android Swipe Pattern, Apple’s TouchID, Amazon Alexa, BB-8 Toy, Apple Watch Unlocking This motivates us to propose a simple gesture that takes a smartwatch as an authentication token for fast access and control of other smart devices. Devices that are stationary or not twisted at the same time should not be co-analyzed Potential Applications → A fast algorithm to prune away candidates having the gestures performed at different times. -

ZOLEO Global Satellite Communicator User Manual
ZOLEO Global Satellite Communicator User Manual Legal Notices, Intellectual Property, Trade Secret, Proprietary or Copyrighted Information Please review legal notices on our website at https://www.zoleo.com/en/legal-notice. Privacy Learn more about our privacy policy and GDPR compliance at https://www.zoleo.com/en/security-and-privacy-policy. Export Compliance Information This product is controlled by the export laws and regulations of the United States of America. The U.S. Government may restrict the export or re-export of this product to certain individuals and/or destinations. For further information, contact the U.S. Department of Commerce, Bureau of Industry and Security or visit https://www.bis.doc.gov/. 2 ZOLEO Global Satellite Communicator User Manual Table of Contents 1. Introduction ................................................................................................................................ 5 1.1 Glossary ............................................................................................................................................. 5 2. Items Supplied ........................................................................................................................... 7 3. Features of the ZOLEO Communicator ................................................................................... 7 4. Account Owners and Users ....................................................................................................... 8 5. Getting Started ......................................................................................................................... -
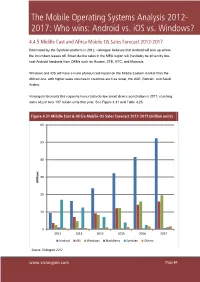
The Mobile Operating Systems Analysis 2012- 2017: Who Wins: Android Vs
The Mobile Operating Systems Analysis 2012- 2017: Who wins: Android vs. iOS vs. Windows? 4.4.5 Middle East and Africa Mobile OS Sales Forecast 2012-2017 Dominated by the Symbian platform in 2012, visiongain believes that Android will pick up where the incumbent leaves off. Smart device sales in the MEA region will inevitably be driven by low- cost Android handsets from OEMs such as Huawei, ZTE, HTC, and Motorola. Windows and iOS will have a more pronounced impact on the Middle Eastern market than the African one, with higher sales volumes in countries such as Israel, the UAE, Bahrain, and Saudi Arabia. Visiongain forecasts this region to have relatively low smart device penetration in 2017, reaching sales of just over 107 million units that year. See Figure 4.31 and Table 4.25. Figure 4.31 Middle East & Africa Mobile OS Sales Forecast 2012-2017 (million units) 60 50 40 30 Millions 20 10 0 2012 2013 2014 2015 2016 2017 Android iOS Windows BlackBerry Symbian Others Source: Visiongain 2012 www.visiongain.com PagePage 8484 The Mobile Operating Systems Analysis 2012- 2017: Who wins: Android vs. iOS vs. Windows? Figure 4.32 Middle East & Africa Mobile OS Sales Forecast Market Share 2012 (% Share) 2.5% 27.2% 49.6% 10.5% 7.0% 3.1% Android iOS Windows BlackBerry Symbian Others Source: Visiongain 2012 Figure 4.33 Middle East & Africa Mobile OS Sales Forecast Market Share 2014 (% Share) 2.4% 14.3% 1.2% 47.4% 16.4% 18.3% Android iOS Windows BlackBerry Symbian Others Source: Visiongain 2012 www.visiongain.com PagePage 8686 The Mobile Operating Systems Analysis 2012- 2017: Who wins: Android vs. -

Summary the NSW Health Mobile and Smart Device Policy Directive
Policy Directive Mobile and Smart Device Summary The NSW Health Mobile and Smart Device Policy Directive defines the principles for allowable usage and features of mobile and smart devices for business use while connected to NSW Health information systems and assets. Document type Policy Directive Document number PD2020_037 Publication date 13 October 2020 Author branch eHealth & ICT Strategy Branch Branch contact (02) 8644 2213 Review date 13 October 2023 Policy manual Not applicable File number H20/70778 Status Active Functional group Clinical/Patient Services - Information and Data Corporate Administration - Information and Data, Security Personnel/Workforce - Security, Workforce planning Applies to Ministry of Health, Public Health Units, Local Health Districts, Board Governed Statutory Health Corporations, Chief Executive Governed Statutory Health Corporations, Specialty Network Governed Statutory Health Corporations, Affiliated Health Organisations, NSW Health Pathology, Public Health System Support Division, Cancer Institute, Government Medical Officers, NSW Ambulance Service, Public Hospitals Distributed to Ministry of Health, Public Health System, Government Medical Officers, NSW Ambulance Service Audience All Staff of NSW Health Secretary, NSW Health This Policy Directive may be varied, withdrawn or replaced at any time. Compliance with this directive is mandatory for NSW Health and is a condition of subsidy for public health organisations. MOBILE AND SMART DEVICE POLICY STATEMENT This Policy Directive defines the principles for allowable usage and features of NSW Health owned and personally owned mobile and smart devices for business use while connected to NSW Health information systems and assets. It establishes a baseline of requirements for all mobile and smart devices. NSW Health Organisations are required to adhere to this baseline on all mobile and smart devices and determine if additional security measures should be established for the needs of their individual data sets. -

Mobile Technology-Based Services for Global Health and Wellness: Opportunities and Challenges”
“MOBILE TECHNOLOGY-BASED SERVICES FOR GLOBAL HEALTH AND WELLNESS: OPPORTUNITIES AND CHALLENGES” Summary of Main points from the OECD-HARVARD Global Health Institute Expert Consultation of 5-6 October 2016. This document reports on key issues emerging from the OECD Expert Consultation: “Mobile Technologies Based Services for Global Health and Wellness: Opportunities and Challenges (http://www.oecd.org/sti/ieconomy/mobile- technology-based-services-for-global-health.htm)”. The Consultation’s objectives were to further international dialogue on issues critical for the successful adoption of mobile-technology-based services for health and wellness with a special focus on privacy, security, quality assurance challenges and measurement needs for evidence-based policy-making. The Expert Consultation was held on 5-6 October, 2016 in Boston (US) at The Harvard Global Health Institute, in collaboration with Swedish Vinnova, Canada Health Infoway and the Global Coalition on Aging. Their financial support and that of participating member countries is gratefully acknowledged. This report was drafted by Elettra Ronchi (Senior Policy Analyst , Digital Economy and Policy Division, OECD), Liana Rosenkrantz Woskie (Assistant Director Harvard Global Health Institute Strategic Initiative on Quality, US ; London School of Informatics, UK) and Julia Adler Milstein (Associate Professor, University of California, San Francisco, US) based on inputs from workshop experts, the OECD Health Committee and the OECD Working Party on Security and Privacy in the Digital -

Factors Influencing the Adoption of Smart Wearable Devices
Scholars' Mine Masters Theses Student Theses and Dissertations Spring 2016 Factors influencing the adoption of smart wearable devices Apurva Adapa Follow this and additional works at: https://scholarsmine.mst.edu/masters_theses Part of the Technology and Innovation Commons Department: Recommended Citation Adapa, Apurva, "Factors influencing the adoption of smart wearable devices" (2016). Masters Theses. 7492. https://scholarsmine.mst.edu/masters_theses/7492 This thesis is brought to you by Scholars' Mine, a service of the Missouri S&T Library and Learning Resources. This work is protected by U. S. Copyright Law. Unauthorized use including reproduction for redistribution requires the permission of the copyright holder. For more information, please contact [email protected]. FACTORS INFLUENCING THE ADOPTION OF SMART WEARABLE DEVICES by APURVA ADAPA A THESIS Presented to the faculty of the Graduate School of the MISSOURI UNIVERSITY OF SCIENCE AND TECHNOLOGY In Partial Fulfillment of the Requirements for the Degree MASTER OF SCIENCE IN INFORMATION SCIENCE AND TECHNOLOGY 2016 Approved by Dr. Fiona Fui Hoon Nah, Advisor Dr. Keng L. Siau Dr. Richard Hall Copyright 2016 Apurva Adapa All Rights Reserved iii ABSTRACT This study aims to examine the factors and issues in adoption of smart wearable devices. Wearable devices have many functions to offer which make them very useful in our daily lives. However, factors influencing the adoption of these devices are not well understood. This research explores the inhibiting and contributing factors influencing the adoption of wearable devices by employing the laddering approach. Qualitative data were collected through in-depth interviews using the laddering technique in order to understand these factors. -

Requirements for an M-Learning Software Framework for Smart Learning
International Journal of Pure and Applied Mathematics Volume 118 No. 16 2018, 1-10 ISSN: 1311-8080 (printed version); ISSN: 1314-3395 (on-line version) url: http://www.ijpam.eu Special Issue ijpam.eu Requirements for an M-learning Software Framework for Smart Learning Sudhindra B. Deshpande1, Srinivas R.Mangalwede2 and Padmavati S. Dandannavar3 1 2 3Department of Information Science & Eng. Gogte Institute of Technology, Belagavi, Karnataka, India [email protected] [email protected] [email protected] January 9, 2018 Abstract The in this paper, we propose a software framework for an m- learning environment. Here, we attempt the soft- ware requirement analysis for a software tool to be devel- oped for m-learning. As the definition goes m- learning is learning while move. Our aim is to use android supportive smart devices on which this m-learning software will exe- cute. Developing software for m-learning application is a complex process which requires judicious handling of pri- oritization, specification, delivering and finally application development. In this paper we try to establish four major and vital requirements such as human-smart device inter- action, infrastructure of mobile-computing, packaging and presenting of the learning content, instructional and learn- ing design. Much m-learning software may fail to meet the objective because of non appropriate handling of above mentioned requirements. These requirements are mutually supporting and affecting each other. For example, limited 1 1 International Journal of Pure and Applied Mathematics Special Issue screen size and Internet connectivity limit the size of learn- ing content and user interface. Hence these kinds of re- quirements are very important to consider during software development of m-learning. -

Smart Device, Smart
Smart device, smart pay Taking mobile payments from coffee shops to retail stores Deloitte’s mPayments practice brings together capabilities from across Deloitte’s businesses including its Technology, Media, and Telecommunications practice, its Financial Services practice, its Retail practice, and a host of other business functions in its strategy and technology groups. Deloitte’s work in the mPayments space includes strategy, design, and implementation of a wide variety of mPayment capabilities. The Payments Center of Excellence can draw on the support of over 7,700 practitioners with specific industry and functional capabilities. About the authors Dr. Preeta M. Banerjee is a senior manager in Deloitte Services LP and heads cross-sector technol- ogy, media, and telecommunications research. Craig Wigginton, Deloitte & Touche LLP, leads the organization’s telecommunications industry practice in the United States, globally, and for the Americas. Contents Mobile payments: The wave of the future? | 1 The mPay-at-POS ecosystem | 3 Drivers and barriers to adoption | 5 Tipping the scales toward mPay-at-POS solutions | 11 Shaping the future payments landscape | 16 Endnotes | 18 Contacts | 22 Acknowledgements | 22 Taking mobile payments from coffee shops to retail stores Mobile payments: The wave of the future? Howard is a tech-savvy professional who uses his smartphone at least 50 times a day. He starts his day using his favorite coffee shop chain’s mobile payment app, which allows him to pre-order his favorite latte, earn and redeem loyalty points, and self- checkout by paying at the counter with his phone. He wishes he had a similar app for his favorite retail store to facilitate larger purchases that take more effort and time.