Monitor and Manage System and Application Configuration Files at Kernel Level in GNU/Linux
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The GNOME Census: Who Writes GNOME?
The GNOME Census: Who writes GNOME? Dave Neary & Vanessa David, Neary Consulting © Neary Consulting 2010: Some rights reserved Table of Contents Introduction.........................................................................................3 What is GNOME?.............................................................................3 Project governance...........................................................................3 Why survey GNOME?.......................................................................4 Scope and methodology...................................................................5 Tools and Observations on Data Quality..........................................7 Results and analysis...........................................................................10 GNOME Project size.......................................................................10 The Long Tail..................................................................................11 Effects of commercialisation..........................................................14 Who does the work?.......................................................................15 Who maintains GNOME?................................................................17 Conclusions........................................................................................22 References.........................................................................................24 Appendix 1: Modules included in survey...........................................25 2 Introduction What -

Ivoyeur: Inotify
COLUMNS iVoyeur inotify DAVE JOSEPHSEN Dave Josephsen is the he last time I changed jobs, the magnitude of the change didn’t really author of Building a sink in until the morning of my first day, when I took a different com- Monitoring Infrastructure bination of freeways to work. The difference was accentuated by the with Nagios (Prentice Hall T PTR, 2007) and is Senior fact that the new commute began the same as the old one, but on this morn- Systems Engineer at DBG, Inc., where he ing, at a particular interchange, I would zig where before I zagged. maintains a gaggle of geographically dispersed It was an unexpectedly emotional and profound metaphor for the change. My old place was server farms. He won LISA ‘04’s Best Paper off to the side, and down below, while my future was straight ahead, and literally under award for his co-authored work on spam construction. mitigation, and he donates his spare time to the SourceMage GNU Linux Project. The fact that it was under construction was poetic but not surprising. Most of the roads I [email protected] travel in the Dallas/Fort Worth area are under construction and have been for as long as anyone can remember. And I don’t mean a lane closed here or there. Our roads drift and wan- der like leaves in the water—here today and tomorrow over there. The exits and entrances, neither a part of this road or that, seem unable to anticipate the movements of their brethren, and are constantly forced to react. -

Misc Thesisdb Bythesissuperv
Honors Theses 2006 to August 2020 These records are for reference only and should not be used for an official record or count by major or thesis advisor. Contact the Honors office for official records. Honors Year of Student Student's Honors Major Thesis Title (with link to Digital Commons where available) Thesis Supervisor Thesis Supervisor's Department Graduation Accounting for Intangible Assets: Analysis of Policy Changes and Current Matthew Cesca 2010 Accounting Biggs,Stanley Accounting Reporting Breaking the Barrier- An Examination into the Current State of Professional Rebecca Curtis 2014 Accounting Biggs,Stanley Accounting Skepticism Implementation of IFRS Worldwide: Lessons Learned and Strategies for Helen Gunn 2011 Accounting Biggs,Stanley Accounting Success Jonathan Lukianuk 2012 Accounting The Impact of Disallowing the LIFO Inventory Method Biggs,Stanley Accounting Charles Price 2019 Accounting The Impact of Blockchain Technology on the Audit Process Brown,Stephen Accounting Rebecca Harms 2013 Accounting An Examination of Rollforward Differences in Tax Reserves Dunbar,Amy Accounting An Examination of Microsoft and Hewlett Packard Tax Avoidance Strategies Anne Jensen 2013 Accounting Dunbar,Amy Accounting and Related Financial Statement Disclosures Measuring Tax Aggressiveness after FIN 48: The Effect of Multinational Status, Audrey Manning 2012 Accounting Dunbar,Amy Accounting Multinational Size, and Disclosures Chelsey Nalaboff 2015 Accounting Tax Inversions: Comparing Corporate Characteristics of Inverted Firms Dunbar,Amy Accounting Jeffrey Peterson 2018 Accounting The Tax Implications of Owning a Professional Sports Franchise Dunbar,Amy Accounting Brittany Rogan 2015 Accounting A Creative Fix: The Persistent Inversion Problem Dunbar,Amy Accounting Foreign Account Tax Compliance Act: The Most Revolutionary Piece of Tax Szwakob Alexander 2015D Accounting Dunbar,Amy Accounting Legislation Since the Introduction of the Income Tax Prasant Venimadhavan 2011 Accounting A Proposal Against Book-Tax Conformity in the U.S. -

Compile Ta Primtux-Lubuntu-18.04
COMPILE TA PRIMTUX-LUBUNTU-18.04 PRÉREQUIS : • rouge : à taper dans le terminal du système chrooté (le système qu’on crée) • vert : à taper dans le terminal du système hôte • Remplacer USER par votre nom d’utilisateur et « Répertoire_de_l’iso_décompressée_de_Lubuntu-18.04 » par le vôtre. • Toutes les modifications exécutées à partir de l’explorateur de fichier hôte se font en root. • Testé sous Ubuntu 18.04 et 18.10 PRÉVOIR UNE DEMI-JOURNÉE : 1. Mise en place de l’environnement : • Dans l’environnement hôte : sudo apt-get install squashfs-tools schroot genisoimage • Télécharger puis extraire l'iso de la Lubuntu 18.04 • Créer un répertoire squashfs dans le /home/USER • Monter le filesystem.squashfs: sudo mount -t squashfs -o loop filesystem.squashfs /media/USER • Copier le filesystem.squashfs monté dans /squashfs: sudo cp -av /media/USER/. squashfs • Copier /run/systemd/resolve/stub-resolv.conf dans le /run/systemd/resolve/ du répertoire /home/USER/squashfs 2. Ajout des dépôts source : sudo chroot /home/USER/squashfs apt-get update add-apt-repository ppa:jclic/master add-apt-repository ppa:webupd8team/java wget -O – https://depot.primtux.fr/repo/debs/key/PrimTux.gpg.key | apt-key add – wget -q – https://depot.primtux.fr/repo/debs/key/PrimTux.gpg.key | apt-key add – • Supprimer PrimTux.gpg.key et -- de la racine du répertoire /home/USER/squashfs depuis l’explorateur de fichiers • Créer le document vide primtux.list dans /etc/apt/sources.list.d et y inscrire: deb https://depot.primtux.fr/repo/debs PrimTux2-Stretch64 main deb https://depot.primtux.fr/repo/debs PrimTux4-amd64 main apt-get update 3. -

Monitoring File Events
MONITORING FILE EVENTS Some applications need to be able to monitor files or directories in order to deter- mine whether events have occurred for the monitored objects. For example, a graphical file manager needs to be able to determine when files are added or removed from the directory that is currently being displayed, or a daemon may want to monitor its configuration file in order to know if the file has been changed. Starting with kernel 2.6.13, Linux provides the inotify mechanism, which allows an application to monitor file events. This chapter describes the use of inotify. The inotify mechanism replaces an older mechanism, dnotify, which provided a subset of the functionality of inotify. We describe dnotify briefly at the end of this chapter, focusing on why inotify is better. The inotify and dnotify mechanisms are Linux-specific. (A few other systems provide similar mechanisms. For example, the BSDs provide the kqueue API.) A few libraries provide an API that is more abstract and portable than inotify and dnotify. The use of these libraries may be preferable for some applications. Some of these libraries employ inotify or dnotify, on systems where they are available. Two such libraries are FAM (File Alteration Monitor, http:// oss.sgi.com/projects/fam/) and Gamin (http://www.gnome.org/~veillard/gamin/). 19.1 Overview The key steps in the use of the inotify API are as follows: 1. The application uses inotify_init() to create an inotify instance. This system call returns a file descriptor that is used to refer to the inotify instance in later operations. -

Foot Prints Feel the Freedom of Fedora!
The Fedora Project: Foot Prints Feel The Freedom of Fedora! RRaahhuull SSuunnddaarraamm SSuunnddaarraamm@@ffeeddoorraapprroojjeecctt..oorrgg FFrreeee ((aass iinn ssppeeeecchh aanndd bbeeeerr)) AAddvviiccee 101011:: KKeeeepp iitt iinntteerraaccttiivvee!! Credit: Based on previous Fedora presentations from Red Hat and various community members. Using the age old wisdom and Indian, Free software tradition of standing on the shoulders of giants. Who the heck is Rahul? ( my favorite part of this presentation) ✔ Self elected Fedora project monkey and noisemaker ✔ Fedora Project Board Member ✔ Fedora Ambassadors steering committee member. ✔ Fedora Ambassador for India.. ✔ Editor for Fedora weekly reports. ✔ Fedora Websites, Documentation and Bug Triaging projects volunteer and miscellaneous few grunt work. Agenda ● Red Hat Linux to Fedora & RHEL - Why? ● What is Fedora ? ● What is the Fedora Project ? ● Who is behind the Fedora Project ? ● Primary Principles. ● What are the Fedora projects? ● Features, Future – Fedora Core 5 ... The beginning: Red Hat Linux 1994-2003 ● Released about every 6 months ● More stable “ .2” releases about every 18 months ● Rapid innovation ● Problems with retail channel sales model ● Impossible to support long-term ● Community Participation: ● Upstream Projects ● Beta Team / Bug Reporting The big split: Fedora and RHEL Red Hat had two separate, irreconcilable goals: ● To innovate rapidly. To provide stability for the long-term ● Red Hat Enterprise Linux (RHEL) ● Stable and supported for 7 years plus. A platform for 3rd party standardization ● Free as in speech ● Fedora Project / Fedora Core ● Rapid releases of Fedora Core, every 6 months ● Space to innovate. Fedora Core in the tradition of Red Hat Linux (“ FC1 == RHL10” ) Free as in speech, free as in beer, free as in community support ● Built and sponsored by Red Hat ● ...with increased community contributions. -

Fsmonitor: Scalable File System Monitoring for Arbitrary Storage Systems
FSMonitor: Scalable File System Monitoring for Arbitrary Storage Systems Arnab K. Paul∗, Ryan Chardy, Kyle Chardz, Steven Tueckez, Ali R. Butt∗, Ian Fostery;z ∗Virginia Tech, yArgonne National Laboratory, zUniversity of Chicago fakpaul, [email protected], frchard, [email protected], fchard, [email protected] Abstract—Data automation, monitoring, and management enable programmatic management, and even autonomously tools are reliant on being able to detect, report, and respond manage the health of the system. Enabling scalable, reliable, to file system events. Various data event reporting tools exist for and standardized event detection and reporting will also be of specific operating systems and storage devices, such as inotify for Linux, kqueue for BSD, and FSEvents for macOS. How- value to a range of infrastructures and tools, such as Software ever, these tools are not designed to monitor distributed file Defined CyberInfrastructure (SDCI) [14], auditing [9], and systems. Indeed, many cannot scale to monitor many thousands automating analytical pipelines [11]. Such systems enable of directories, or simply cannot be applied to distributed file automation by allowing programs to respond to file events systems. Moreover, each tool implements a custom API and and initiate tasks. event representation, making the development of generalized and portable event-based applications challenging. As file systems Most storage systems provide mechanisms to detect and grow in size and become increasingly diverse, there is a need report data events, such as file creation, modification, and for scalable monitoring solutions that can be applied to a wide deletion. Tools such as inotify [20], kqueue [18], and FileSys- range of both distributed and local systems. -

Kernel Korner
Kernel Korner http://0-delivery.acm.org.innopac.lib.ryerson.ca/10.1145/1110000/11030... Kernel Korner Intro to inotify Robert Love Abstract Applications that watch thousands of files for changes, or that need to know when a storage device gets disconnected, need a clean, fast solution to the file change notification problem. Here it is. John McCutchan and I had been working on inotify for about a year when it was finally merged into Linus' kernel tree and released with kernel version 2.6.13. Although a long struggle, the effort culminated in success and was ultimately worth every rewrite, bug and debate. What Is inotify? inotify is a file change notification system—a kernel feature that allows applications to request the monitoring of a set of files against a list of events. When the event occurs, the application is notified. To be useful, such a feature must be simple to use, lightweight with little overhead and flexible. It should be easy to add new watches and painless to receive notification of events. To be sure, inotify is not the first of its kind. Every modern operating system provides some sort of file notification system; many network and desktop applications require such functionality—Linux too. For years, Linux has offered dnotify. The problem was, dnotify was not very good. In fact, it stank. dnotify, which ostensibly stands for directory notify, was never considered easy to use. Sporting a cumbersome interface and several painful features that made life arduous, dnotify failed to meet the demands of the modern desktop, where asynchronous notification of events and a free flow of information rapidly are becoming the norm. -
Hitachi Cloud Accelerator Platform Product Manager HCAP V 1
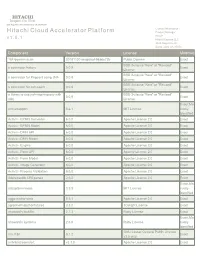
HITACHI Inspire the Next 2535 Augustine Drive Santa Clara, CA 95054 USA Contact Information : Hitachi Cloud Accelerator Platform Product Manager HCAP v 1 . 5 . 1 Hitachi Vantara LLC 2535 Augustine Dr. Santa Clara CA 95054 Component Version License Modified 18F/domain-scan 20181130-snapshot-988de72b Public Domain Exact BSD 3-clause "New" or "Revised" a connector factory 0.0.9 Exact License BSD 3-clause "New" or "Revised" a connector for Pageant using JNA 0.0.9 Exact License BSD 3-clause "New" or "Revised" a connector for ssh-agent 0.0.9 Exact License a library to use jsch-agent-proxy with BSD 3-clause "New" or "Revised" 0.0.9 Exact sshj License Exact,Ma activesupport 5.2.1 MIT License nually Identified Activiti - BPMN Converter 6.0.0 Apache License 2.0 Exact Activiti - BPMN Model 6.0.0 Apache License 2.0 Exact Activiti - DMN API 6.0.0 Apache License 2.0 Exact Activiti - DMN Model 6.0.0 Apache License 2.0 Exact Activiti - Engine 6.0.0 Apache License 2.0 Exact Activiti - Form API 6.0.0 Apache License 2.0 Exact Activiti - Form Model 6.0.0 Apache License 2.0 Exact Activiti - Image Generator 6.0.0 Apache License 2.0 Exact Activiti - Process Validation 6.0.0 Apache License 2.0 Exact Addressable URI parser 2.5.2 Apache License 2.0 Exact Exact,Ma adzap/timeliness 0.3.8 MIT License nually Identified aggs-matrix-stats 5.5.1 Apache License 2.0 Exact agronholm/pythonfutures 3.3.0 3Delight License Exact ahoward's lockfile 2.1.3 Ruby License Exact Exact,Ma ahoward's systemu 2.6.5 Ruby License nually Identified GNU Lesser General Public License ai's -

Displaying and Watching Directories Using Lazarus
Displaying and Watching directories using Lazarus Michaël Van Canneyt October 31, 2011 Abstract Using Lazarus, getting the contents of a directory can be done in 2 ways: a portable, and a unix-specific way. This article shows how to get the contents of a directory and show it in a window. Additionally, it shows how to get notifications of the Linux kernel if the contents of the directory changes. 1 Introduction Examining the contents of a directory is a common operation, both using command-line tools or a GUI file manager. Naturally, Free/Pascal and Lazarus offer an API to do this. In fact, there are 2 API’s to get the contents of a directory: one which is portable and will work on all platforms supported by Lazarus. The other is not portable, but resembles closely the POSIX API for dealing with files and directories. Each API has its advantages and disadvantages. Often, it is desirable to be notified if the contents of a directory changes: in a file manager, this can be used to update the display - showing new items or removing items as needed. This can also be done by scanning the contents of the directory at regular intervals, but it should be obvious that this is not as efficient. There are other scenarios when a notification of a change in a directory is interesting: for instance, in a FTP server, one may want to move incoming files to a location outside the FTP tree, or to a new location based on some rules (e.g. images to one directory, sound files to another). -

Battle-Hardened Upstart Linux Plumbers 2013
Battle-Hardened Upstart Linux Plumbers 2013 James Hunt <[email protected]> and Dmitrijs Ledkovs <[email protected]> September, 2013 Table of Contents Utilities 1. Overview 3. Enablements 2. Design and Architecture cloud-init Event-based Design friendly-recovery Example Job gpg-key-compose SystemV Support Summary SystemV Runlevels 4. Quality Checks Bridges 5. Areas of Friction More Events 6. Links . 2 / 31 Overview of Upstart Revolutionary event-based /sbin/init system. Written by Scott James Remnant (Canonical, Google). Maintained by Canonical. Developed by Canonical and the community. PID 1 on every Ubuntu system since 2006 (introduced in Ubuntu 6.10 "Edgy Eft"). Systems booted using native Upstart jobs (not SysVinit compat) since Ubuntu 9.10 ("Karmic Koala") in 2009. Handles system boot and shutdown and supervises services. Provides legacy support for SystemV services. Upstart is a first-class citizen in Debian ([Debian Policy]). 3 / 31 Availability and Usage Runs on any modern Linux system. Used by... 6.10 ! 11.3/11.4 RHEL6 ChromeOS Now available in... 4 / 31 Platform Presence Upstart runs on all types of systems: Desktop systems Servers Embedded devices Thin clients (such as ChromeBooks, Edubuntu) Cloud instances Tablets Phones (Ubuntu Touch) . 5 / 31 Cloud Upstart is the #1 init system used in the cloud (through Ubuntu). Ubuntu, and thus Upstart, is used by lots of large well-known companies such as: HP AT&T Wikipedia Ericsson Rackspace Instagram twitpic … Companies moving to Ubuntu... Netflix . Hulu eBay 6 / 31 Versatility Upstart is simple and versatile The /sbin/init daemon only knows about events and processes: it doesn't dictate runlevel policy. -

Indicators for Missing Maintainership in Collaborative Open Source Projects
TECHNISCHE UNIVERSITÄT CAROLO-WILHELMINA ZU BRAUNSCHWEIG Studienarbeit Indicators for Missing Maintainership in Collaborative Open Source Projects Andre Klapper February 04, 2013 Institute of Software Engineering and Automotive Informatics Prof. Dr.-Ing. Ina Schaefer Supervisor: Michael Dukaczewski Affidavit Hereby I, Andre Klapper, declare that I wrote the present thesis without any assis- tance from third parties and without any sources than those indicated in the thesis itself. Braunschweig / Prague, February 04, 2013 Abstract The thesis provides an attempt to use freely accessible metadata in order to identify missing maintainership in free and open source software projects by querying various data sources and rating the gathered information. GNOME and Apache are used as case studies. License This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported (CC BY-SA 3.0) license. Keywords Maintenance, Activity, Open Source, Free Software, Metrics, Metadata, DOAP Contents List of Tablesx 1 Introduction1 1.1 Problem and Motivation.........................1 1.2 Objective.................................2 1.3 Outline...................................3 2 Theoretical Background4 2.1 Reasons for Inactivity..........................4 2.2 Problems Caused by Inactivity......................4 2.3 Ways to Pass Maintainership.......................5 3 Data Sources in Projects7 3.1 Identification and Accessibility......................7 3.2 Potential Sources and their Exploitability................7 3.2.1 Code Repositories.........................8 3.2.2 Mailing Lists...........................9 3.2.3 IRC Chat.............................9 3.2.4 Wikis............................... 10 3.2.5 Issue Tracking Systems...................... 11 3.2.6 Forums............................... 12 3.2.7 Releases.............................. 12 3.2.8 Patch Review........................... 13 3.2.9 Social Media............................ 13 3.2.10 Other Sources..........................