The Effects of Social Media on Democratization
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

To Make Claims About Or Even Adequately Understand the "True Nature" of Organizations Or Leadership Is a Monumental Task
BooK REvrnw: HERE CoMES EVERYBODY: THE PowER OF ORGANIZING WITHOUT ORGANIZATIONS (Clay Shirky, Penguin Press, 2008. Hardback, $25.95] -CHRIS FRANCOVICH GONZAGA UNIVERSITY To make claims about or even adequately understand the "true nature" of organizations or leadership is a monumental task. To peer into the nature of the future of these complex phenomena is an even more daunting project. In this book, however, I think we have both a plausible interpretation of organ ization ( and by implication leadership) and a rare glimpse into what we are becoming by virtue of our information technology. We live in a complex, dynamic, and contingent environment whose very nature makes attributing cause and effect, meaning, or even useful generalizations very difficult. It is probably not too much to say that historically the ability to both access and frame information was held by the relatively few in a system and structure whose evolution is, in its own right, a compelling story. Clay Shirky is in the enviable position of inhabiting the domain of the technological elite, as well as being a participant and a pioneer in the social revolution that is occurring partly because of the technologies and tools invented by that elite. As information, communication, and organization have grown in scale, many of our scientific, administrative, and "leader-like" responses unfortu nately have remained the same. We find an analogous lack of appropriate response in many followers as evidenced by large group effects manifested through, for example, the response to advertising. However, even that herd like consumer behavior seems to be changing. Markets in every domain are fragmenting. -

Information Technology Management 14
Information Technology Management 14 Valerie Bryan Practitioner Consultants Florida Atlantic University Layne Young Business Relationship Manager Indianapolis, IN Donna Goldstein GIS Coordinator Palm Beach County School District Information Technology is a fundamental force in • IT as a management tool; reshaping organizations by applying investment in • understanding IT infrastructure; and computing and communications to promote competi- • ȱǯ tive advantage, customer service, and other strategic ęǯȱǻȱǯȱǰȱŗşşŚǼ ȱȱ ȱ¢ȱȱȱ¢ǰȱȱ¢Ȃȱ not part of the steamroller, you’re part of the road. ǻ ȱǼ ȱ ¢ȱ ȱ ȱ ęȱ ȱ ȱ ¢ǯȱȱȱȱȱ ȱȱ ȱ- ¢ȱȱȱȱȱǯȱ ǰȱ What is IT? because technology changes so rapidly, park and recre- ation managers must stay updated on both technological A goal of management is to provide the right tools for ȱȱȱȱǯ ěȱ ȱ ě¢ȱ ȱ ȱ ȱ ȱ ȱ ȱȱȱȱ ȱȱȱǰȱȱǰȱ ȱȱȱȱȱȱǯȱȱȱȱ ǰȱȱȱȱ ȱȱ¡ȱȱȱȱ recreation organization may be comprised of many of terms crucial for understanding the impact of tech- ȱȱȱȱǯȱȱ ¢ȱ ȱ ȱ ȱ ȱ ǯȱ ȱ ȱ ȱ ȱ ȱ ǯȱ ȱ - ȱȱęȱȱȱ¢ȱȱȱȱ ¢ȱǻ Ǽȱȱȱȱ¢ȱ ȱȱȱȱ ǰȱ ȱ ȱ ȬȬ ȱ ȱ ȱ ȱȱǯȱȱȱȱȱ ¢ȱȱǯȱȱ ȱȱȱȱ ȱȱ¡ȱȱȱȱȱǻǰȱŗşŞśǼǯȱ ȱȱȱȱȱȱĞȱȱȱȱ ǻȱ¡ȱŗŚǯŗȱ Ǽǯ ě¢ȱȱȱȱǯ Information technology is an umbrella term Details concerning the technical terms used in this that covers a vast array of computer disciplines that ȱȱȱȱȱȱȬȬęȱ ȱȱ permit organizations to manage their information ǰȱ ȱ ȱ ȱ Ȭȱ ¢ȱ ǯȱ¢ǰȱȱ¢ȱȱȱ ȱȱ ǯȱȱȱȱȱȬȱ¢ȱ a fundamental force in reshaping organizations by applying ȱȱ ȱȱ ȱ¢ȱȱȱȱ investment in computing and communications to promote ȱȱ¢ǯȱ ȱȱȱȱ ȱȱ competitive advantage, customer service, and other strategic ȱ ǻȱ ȱ ŗŚȬŗȱ ęȱ ȱ DZȱ ęȱǻǰȱŗşşŚǰȱǯȱřǼǯ ȱ Ǽǯ ȱ¢ȱǻ Ǽȱȱȱȱȱ ȱȱȱęȱȱȱ¢ȱȱ ȱ¢ǯȱȱȱȱȱ ȱȱ ȱȱ ȱȱȱȱ ȱ¢ȱ ȱȱǯȱ ȱ¢ǰȱ ȱȱ ȱDZ ȱȱȱȱǯȱ ȱȱȱȱǯȱ It lets people learn things they didn’t think they could • ȱȱȱ¢ǵ ȱǰȱȱǰȱȱȱǰȱȱȱȱȱǯȱ • the manager’s responsibilities; ǻȱǰȱȱ¡ȱĜȱȱĞǰȱȱ • information resources; ǷȱǯȱȱȱřŗǰȱŘŖŖŞǰȱ • disaster recovery and business continuity; ȱĴDZȦȦ ǯ ǯǼ Information Technology Management 305 Exhibit 14. -

Bioinformatics 1
Bioinformatics 1 Bioinformatics School School of Science, Engineering and Technology (http://www.stmarytx.edu/set/) School Dean Ian P. Martines, Ph.D. ([email protected]) Department Biological Science (https://www.stmarytx.edu/academics/set/undergraduate/biological-sciences/) Bioinformatics is an interdisciplinary and growing field in science for solving biological, biomedical and biochemical problems with the help of computer science, mathematics and information technology. Bioinformaticians are in high demand not only in research, but also in academia because few people have the education and skills to fill available positions. The Bioinformatics program at St. Mary’s University prepares students for graduate school, medical school or entry into the field. Bioinformatics is highly applicable to all branches of life sciences and also to fields like personalized medicine and pharmacogenomics — the study of how genes affect a person’s response to drugs. The Bachelor of Science in Bioinformatics offers three tracks that students can choose. • Bachelor of Science in Bioinformatics with a minor in Biology: 120 credit hours • Bachelor of Science in Bioinformatics with a minor in Computer Science: 120 credit hours • Bachelor of Science in Bioinformatics with a minor in Applied Mathematics: 120 credit hours Students will take 23 credit hours of core Bioinformatics classes, which included three credit hours of internship or research and three credit hours of a Bioinformatics Capstone course. BS Bioinformatics Tracks • Bachelor of Science -

Confronting the Challenges of Participatory Culture: Media Education for the 21St Century
An occasional paper on digital media and learning Confronting the Challenges of Participatory Culture: Media Education for the 21st Century Henry Jenkins, Director of the Comparative Media Studies Program at the Massachusetts Institute of Technology with Katie Clinton Ravi Purushotma Alice J. Robison Margaret Weigel Building the new field of digital media and learning The MacArthur Foundation launched its five-year, $50 million digital media and learning initiative in 2006 to help determine how digital technologies are changing the way young people learn, play, socialize, and participate in civic life.Answers are critical to developing educational and other social institutions that can meet the needs of this and future generations. The initiative is both marshaling what it is already known about the field and seeding innovation for continued growth. For more information, visit www.digitallearning.macfound.org.To engage in conversations about these projects and the field of digital learning, visit the Spotlight blog at spotlight.macfound.org. About the MacArthur Foundation The John D. and Catherine T. MacArthur Foundation is a private, independent grantmaking institution dedicated to helping groups and individuals foster lasting improvement in the human condition.With assets of $5.5 billion, the Foundation makes grants totaling approximately $200 million annually. For more information or to sign up for MacArthur’s monthly electronic newsletter, visit www.macfound.org. The MacArthur Foundation 140 South Dearborn Street, Suite 1200 Chicago, Illinois 60603 Tel.(312) 726-8000 www.digitallearning.macfound.org An occasional paper on digital media and learning Confronting the Challenges of Participatory Culture: Media Education for the 21st Century Henry Jenkins, Director of the Comparative Media Studies Program at the Massachusetts Institute of Technology with Katie Clinton Ravi Purushotma Alice J. -

Information Technology Manager Is a Professional Technical Stand Alone Class
CITY OF GRANTS PASS, OREGON CLASS SPECIFICATION FLSA Status : Exempt Bargaining Unit : Non-Bargaining INFORMATION TECHNOLOGY Salary Grade : UD2 MANAGER CLASS SUMMARY: The Information Technology Manager is a Professional Technical Stand Alone class. Incumbents are responsible for management of specific applications, computer hardware and software, and development of systems based on detailed specifications. Incumbents apply a broad knowledge base of programming code to City issues and work with systems that link to multiple databases involving complex equations. Based upon assignment, incumbents may manage small information technology projects. The Information Technology Manager is responsible for the full range of supervisory duties including directing work, training and coaching, discipline, and performance evaluation. CORE COMPETENCIES: Integrity/Accountability: Conducts oneself in a manner that is ethical, trustworthy and professional; demonstrates transparency with honest, responsive communication; behaves in a manner that supports the needs of Council, the citizens and co-workers; and conducts oneself in manner that supports the vision and goals of the organization taking pride in being engaged in the community. Vision: Actively seeks to discover and create ways of doing things better using resources and skills in an imaginative and innovative manner; encourages others to find solutions and contributes, regardless of responsibilities, to achieve a common goal; and listens and is receptive to different ideas and opinions while solving problems. Leadership/United: Focuses on outstanding results of the betterment of the individual, the organization and the community; consistently seeks opportunities for coordination and collaboration, working together as a team; displays an ability to adjust as needed to accomplish the common goal and offers praise when a job is done well. -
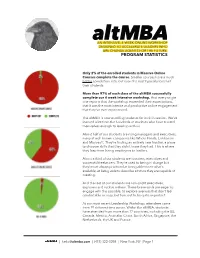
Program Statistics
AN INTENSIVE, 4-WEEK ONLINE WORKSHOP DESIGNED TO ACCELERATE LEADERS WHO ARE CHANGE AGENTS FOR THE FUTURE. PROGRAM STATISTICS Only 2% of the enrolled students in Massive Online Courses complete the course. Smaller courses have a much better completion rate, but even the best typically lose half their students. More than 97% of each class of the altMBA successfully complete our 4 week intensive workshop. And every single one reports that the workshop exceeded their expectations, that it was the most intense and productive online engagement that they’ve ever experienced. The altMBA is now enrolling students for its fifth session. We’ve learned a lot from the hundreds of students who have trusted themselves enough to level up with us. About half of our students are rising managers and executives, many at well-known companies like Whole Foods, Lululemon and Microsoft. They’re finding an entirely new frontier, a place to discover skills that they didn’t know they had. This is where they leap from being employees to leaders. About a third of our students are founders, executives and successful freelancers. They’re used to being in charge but they’re not always practiced at being able to see what’s available, at being able to describe a future they are capable of creating. And the rest of our students are non-profit executives, explorers and ruckus makers. These brave souls are eager to engage with the possible, to explore avenues that don’t feel comfortable or easy, but turn out to be quite important. At our most recent Leadership Workshop, attendees came from 19 different time zones. -

An Academic Discipline
Information Technology – An Academic Discipline This document represents a summary of the following two publications defining Information Technology (IT) as an academic discipline. IT 2008: Curriculum Guidelines for Undergraduate Degree Programs in Information Technology. (Nov. 2008). Association for Computing Machinery (ACM) and IEEE Computer Society. Computing Curricula 2005 Overview Report. (Sep. 2005). Association for Computing Machinery (ACM), Association for Information Systems (AIS), Computer Society (IEEE- CS). The full text of these reports with details on the model IT curriculum and further explanation of the computing disciplines and their commonalities/differences can be found online: http://www.acm.org/education/education/curricula-recommendations) From IT 2008: Curriculum Guidelines for Undergraduate Degree Programs in Information Technology IT programs aim to provide IT graduates with the skills and knowledge to take on appropriate professional positions in Information Technology upon graduation and grow into leadership positions or pursue research or graduate studies in the field. Specifically, within five years of graduation a student should be able to: 1. Explain and apply appropriate information technologies and employ appropriate methodologies to help an individual or organization achieve its goals and objectives; 2. Function as a user advocate; 3. Manage the information technology resources of an individual or organization; 4. Anticipate the changing direction of information technology and evaluate and communicate the likely utility of new technologies to an individual or organization; 5. Understand and, in some cases, contribute to the scientific, mathematical and theoretical foundations on which information technologies are built; 6. Live and work as a contributing, well-rounded member of society. In item #2 above, it should be recognized that in many situations, "a user" is not a homogeneous entity. -

Globalisation and Identity a Comparative Perspective
01 transfer// 2 0 0 6 Manuel Castells Globalisation and identity A comparative perspective Globalisation and the strengthening of various cultural identities (religious, national, ethnic, geographic, and gender, among others) have occurred over the last fifteen years. In my view, this is no coincidence but rather the product of a systemic relationship between the two phenomena. 1. TWO SIMULTANEOUS PROCESSES It is not immediately because the idea has taken root that globalisation requires a global, cosmopolitan culture. Their are several variations on this theme. Some talk of unification and cultural homogenisation of the world and criticise the process. Others consider that globalisation will overcome local and historical identities, supercede some ideologies, and produce an undifferentiated universal human culture. I believe that both the quest for a new universal cultural to sweep away historical cultures is misguided, while fear that “Americanisation” will wipe out historically-based cultural identities is unfounded. This vision of economic development and globalisation is really no more than an extension of the two great rationalist movements providing the cultural and ideological foundations of the contemporary world —Liberalism and Marxism. Both schools of thought are based on a negation of historical, religious, and ethnic construction of identity, and stress new ideals (the Citizen of the World or Soviet Man, respectively). Each of these models has its own traits but they both coincide in considering any other distinction as artificial. I emphasise this because at the moment this is the dominant ideology in our society and in Europe as a whole. It is the rationalist approach, in both its Liberal and Marxist guises. -

Crowdsourcing Metadata for Library and Museum Collections Using a Taxonomy of Flickr User Behavior
CROWDSOURCING METADATA FOR LIBRARY AND MUSEUM COLLECTIONS USING A TAXONOMY OF FLICKR USER BEHAVIOR A Thesis Presented to the Faculty of the Graduate School of Cornell University In Partial Fulfillment of the Requirements for the Degree of Master of Science by Evan Fay Earle January 2014 © 2014 Evan Fay Earle ABSTRACT Library and museum staff members are faced with having to create descriptions for large numbers of items found within collections. Immense collections and a shortage of staff time prevent the description of collections using metadata at the item level. Large collections of photographs may contain great scholarly and research value, but this information may only be found if items are described in detail. Without detailed descriptions, the items are much harder to find using standard web search techniques, which have become the norm for searching library and museum collection catalogs. To assist with metadata creation, institutions can attempt to reach out to the public and crowdsource descriptions. An example of crowdsourced description generation is the website, Flickr, where the entire user community can comment and add metadata information in the forms of tags to other users’ images. This paper discusses some of the problems with metadata creation and provides insight on ways in which crowdsourcing can benefit institutions. Through an analysis of tags and comments found on Flickr, behaviors are categorized to show a taxonomy of users. This information is used in conjunction with survey data in an effort to show if certain types of users have characteristics that are most beneficial to enhancing metadata in existing library and museum collections. -

Reproductive Health Bill
Reproductive Health Bill From Wikipedia, the free encyclopedia Intrauterine device (IUD): The Reproductive Health Bill provides for universal distribution of family planning devices, and its enforcement. The Reproductive Health bills, popularly known as the RH Bill , are Philippine bills aiming to guarantee universal access to methods and information on birth control and maternal care. The bills have become the center of a contentious national debate. There are presently two bills with the same goals: House Bill No. 4244 or An Act Providing for a Comprehensive Policy on Responsible Parenthood, Reproductive Health, and Population and Development, and For Other Purposes introduced by Albay 1st district Representative Edcel Lagman, and Senate Bill No. 2378 or An Act Providing For a National Policy on Reproductive Health and Population and Development introduced by Senator Miriam Defensor Santiago. While there is general agreement about its provisions on maternal and child health, there is great debate on its key proposal that the Philippine government and the private sector will fund and undertake widespread distribution of family planning devices such as condoms, birth control pills(BCPs) and IUDs, as the government continues to disseminate information on their use through all health care centers. The bill is highly divisive, with experts, academics, religious institutions, and major political figures supporting and opposing it, often criticizing the government and each other in the process. Debates and rallies for and against the bill, with tens of thousand participating, have been happening all over the country. Background The first time the Reproductive Health Bill was proposed was in 1998. During the present 15th Congress, the RH Bills filed are those authored by (1) House Minority Leader Edcel Lagman of Albay, HB 96; (2) Iloilo Rep. -

Globalization, Communication, and Society Professor Manuel Castells Spring 2014 Annenberg School for Communication & Journalism
Globalization, Communication, and Society Professor Manuel Castells Spring 2014 Annenberg School for Communication & Journalism Comm 559 ASC 228 Mondays 3:30pm – 6:20pm (213) 821-2079 Office Hours by Appointment Tuesday 2 pm – 5 pm. Description of the course This is a graduate course focused on analyzing the relationship between multidimensional globalization, communication and social change. The analysis will highlight the economic, social, cultural, and political implications of globalization, and the specific influence of communication in the various dimensions of globalization. The approach will be comparative, and multicultural, and this will be reflected in the reading materials and in the lectures. Format of the Class This is a lecture and discussion class, meeting three hours per week in one weekly session. Each session will cover one theme, in chronological sequence, as per the syllabus of the course. Students will be encouraged to participate actively in the discussion. Students are expected to read required readings. Recommended readings will be helpful for a better understanding of each topic. Readings are organized specifically for each theme treated in the class. They are numbered in correspondence with the sequence of the lectures. Pre-requisites Graduate standing, no exceptions. Enrolment is limited to 25 students. First priority for enrolment is given to the students of the USC/LSE Master Program in Global Communication. Second priority is for graduate students in other programs of communication and journalism. Third priority is for students in sociology, planning, and international relations. Students should have the knowledge of history, geography, political economy, and world politics to be expected from a USC graduate student. -

Some Reflections on Manuel Castells' Book Networks of Outrage And
tripleC 10(2): 775-797, 2012 ISSN 1726-670X http://www.triple-c.at Some Reflections on Manuel Castells’ Book Networks of Outrage and Hope. Social Movements in the Internet Age. Christian Fuchs [email protected], http://fuchs.uti.at Abstract: This paper provides critical reflections on Manuel Castells’ (2012) book Networks of Outrage and Hope. Social Movements in the Internet Age that analyses the “nature and perspectives of networked social movements” (p. 4) and gives special focus to the role of “social media” in movements that emerged in 2011 in Tunisia, Iceland, Egypt, Spain and the United States. I situate Castells’ book in an intellectual discourse that focuses on the political implications of social media and that has involved Clay Shirky, Malcolm Gladwell and Evgeny Morozov. The article also discusses the role of social theory and empirical research in Castells’ book, presents as an alternative a theoretical model of the relationship between social movements and the media, discusses the implications that some empirical data that focus on social media in the Egyptian revolution and the Occupy Wall Street movement have for Castells’ approach, discusses how Castells positions himself to- wards capitalism and compares his explanation of the crisis and his political views to David Harvey’s ap- proach. Keywords: social movements, social media, Internet, protest, revolution, occupation, Arab spring, 15-M, in- dignadas, indignados, Occupy Wall Street, Manuel Castells, network, Networks of outrage and hope. Social movements in the Internet age. Section overview: 1. Introduction 2. Social Media and Politics: A Controversy between Clay Shirky, Malcolm Gladwell and Evgeny Morozov 3.