A Security Framework for Mobile Health Applications on Android Platform
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
AVG Android App Performance and Trend Report H1 2016
AndroidTM App Performance & Trend Report H1 2016 By AVG® Technologies Table of Contents Executive Summary .....................................................................................2-3 A Insights and Analysis ..................................................................................4-8 B Key Findings .....................................................................................................9 Top 50 Installed Apps .................................................................................... 9-10 World’s Greediest Mobile Apps .......................................................................11-12 Top Ten Battery Drainers ...............................................................................13-14 Top Ten Storage Hogs ..................................................................................15-16 Click Top Ten Data Trafc Hogs ..............................................................................17-18 here Mobile Gaming - What Gamers Should Know ........................................................ 19 C Addressing the Issues ...................................................................................20 Contact Information ...............................................................................21 D Appendices: App Resource Consumption Analysis ...................................22 United States ....................................................................................23-25 United Kingdom .................................................................................26-28 -

Andrew Phay Whatcom CD [email protected]
New Technology for Use in Your District Andrew Phay Whatcom CD [email protected] Smart Phones • Takes the place of GPS, Camera, Data Logger, Notes • GPS o iPhone/iPad – MoronX GPS, SpyGlass o Android – MyTracks, GPSLogger • Document Editing– Docs To Go, Google Docs, Office Suite Pro • Notes & To-Dos’– Evernote, Awesome Note • File Access – DropBox, Box.net • LogMeIn • Soilweb • Calendar sharing and reminders • Email • Weather iPad/Tablets • Mapping/GPS – MyTracks, GPSLogger, GISPro, Google Earth, ArcGIS • Word/Excel/PowerPoint – Docs to Go • Notes – Evernote • Photos/video – GPS tags • Conferencing – Skype, FaceTime • Remote Desktop – LogMeIn • File Access – DropBox, Box.net • Scan/Sign/Edit/Draw • Friend Finder – Device Locator • Security – can wipe from AppleID login • Email • Weather – USGS flooding app • Cases/Keyboards/Other accessories o Pen/GPS/Otter Box GPS Test Web LogMeIn iPad iPhone EverNote Web: Evernote iPad: Evernote Screen Shot Screen Shot iPhone: Evernote Screen Shot Other Hardware • Cameras - Waterproof/Dustproof/Fog-resistant • Portable Projectors File Syncing • DropBox – 2gb free o On smartphones, PC, Mac, Integrates with Docs2Go o Can share a link through email that others can download. • Box.net – 5gb free o Same kind of stuff Online Mapping • ArcGIS.com • Google Maps - My Places • Google Fusion Tables Website Management • Drupal • WordPress • SquareSpace • Google Sites News Aggregators Password Manager • Holds all my passwords • One Master password • On smartphones • Generates passwords • Browser Plugin • Security is great! Browser Plugins • News Aggregators • Lastpass • Screenshots - Fireshot • Download helpers – DownloadThemAll • Morning Coffee Teleconferencing/ Desktop Sharing • LogMeIn - free • Skype - free • Crossloop - free • Join.me – free • GoToMeeting • WebEx Social Networking • Facebook • LinkedIn • Twitter • Google+ • Google Groups Thanks! Andrew Phay [email protected] 360-354-2035 x129 . -

Understanding and Detecting Wake Lock Misuses for Android Applications
✓ Artifact evaluated by FSE Understanding and Detecting Wake Lock Misuses for Android Applications Yepang Liux Chang Xu‡ Shing-Chi Cheungx Valerio Terragnix xDept. of Comp. Science and Engineering, The Hong Kong Univ. of Science and Technology, Hong Kong, China ‡State Key Lab for Novel Software Tech. and Dept. of Comp. Sci. and Tech., Nanjing University, Nanjing, China x{andrewust, scc*, vterragni}@cse.ust.hk, ‡[email protected]* ABSTRACT over slow network connections, it may take a while for the transaction to complete. If the user's smartphone falls asleep Wake locks are widely used in Android apps to protect crit- while waiting for server messages and does not respond in ical computations from being disrupted by device sleeping. time, the transaction will fail, causing poor user experience. Inappropriate use of wake locks often seriously impacts user To address this problem, modern smartphone platforms al- experience. However, little is known on how wake locks are low apps to explicitly control when to keep certain hardware used in real-world Android apps and the impact of their mis- awake for continuous computation. On Android platforms, uses. To bridge the gap, we conducted a large-scale empiri- wake locks are designed for this purpose. Specifically, to keep cal study on 44,736 commercial and 31 open-source Android certain hardware awake for computation, an app needs to ac- apps. By automated program analysis and manual investi- quire a corresponding type of wake lock from the Android gation, we observed (1) common program points where wake OS (see Section 2.2). When the computation completes, the locks are acquired and released, (2) 13 types of critical com- app should release the acquired wake locks properly. -

Privatumo Apsaugos Metodas Nuo Buvimo Vietos Nustatymo Mobiliesiems Įrenginiams Baigiamasis Magistro Studijų Projektas
Kauno technologijos universitetas Informatikos fakultetas Privatumo apsaugos metodas nuo buvimo vietos nustatymo mobiliesiems įrenginiams Baigiamasis magistro studijų projektas Deimantė Zemeckytė Projekto autorė Prof. Jevgenijus Toldinas Vadovas Kaunas, 2021 Kauno technologijos universitetas Informatikos fakultetas Privatumo apsaugos metodas nuo buvimo vietos nustatymo mobiliesiems įrenginiams Magistro studijų projektas Informacijos ir informaciniu technologijų sauga (621E10003) Deimantė Zemeckytė Projekto autorė Prof. Jevgenijus Toldinas Vadovas Doc. Statys Maciulevičius Recenzentas Kaunas, 2021 2 Kauno technologijos universitetas Informatikos fakultetas Deimantė Zemeckytė Privatumo apsaugos metodas nuo buvimo vietos nustatymo mobiliesiems įrenginiams Akademinio sąžiningumo deklaracija Patvirtinu, kad mano, Deimantė Zemeckytė, baigiamasis projektas tema „Privatumo apsaugos metodas nuo buvimo vietos nustatymo mobiliesiems įrenginiams“ yra parašytas visiškai savarankiškai ir visi pateikti duomenys ar tyrimų rezultatai yra teisingi ir gauti sąžiningai. Šiame darbe nei viena dalis nėra plagijuota nuo jokių spausdintinių ar internetinių šaltinių, visos kitų šaltinių tiesioginės ir netiesioginės citatos nurodytos literatūros nuorodose. Įstatymų nenumatytų piniginių sumų už šį darbą niekam nesu mokėjęs. Aš suprantu, kad išaiškėjus nesąžiningumo faktui, man bus taikomos nuobaudos, remiantis Kauno technologijos universitete galiojančia tvarka. Deimantė Zemeckytė (vardą ir pavardę įrašyti ranka) (parašas) Deimantė Zemeckytė. Privatumo apsaugos -

Preventing Duplicate Bug Reports by Continuously Querying Bug Reports
EMSE manuscript No. (will be inserted by the editor) Preventing Duplicate Bug Reports by Continuously Querying Bug Reports Abram Hindle · Curtis Onuczko Received: date / Accepted: date Abstract Bug deduplication or duplicate bug report detection is a hot topic in software engineering information retrieval research, but it is often not de- ployed. Typically to de-duplicate bug reports developers rely upon the search capabilities of the bug report software they employ, such as Bugzilla, Jira, or Github Issues. These search capabilities range from simple SQL string search to IR-based word indexing methods employed by search engines. Yet too often these searches do very little to stop the creation of duplicate bug reports. Some bug trackers have more than 10% of their bug reports marked as duplicate. Perhaps these bug tracker search engines are not enough? In this paper we propose a method of attempting to prevent duplicate bug reports before they start: continuously querying. That is as the bug reporter types in their bug report their text is used to query the bug database to find duplicate or related bug reports. This continuously querying bug reports allows the reporter to be alerted to duplicate bug reports as they report the bug, rather than formulat- ing queries to find the duplicate bug report. Thus this work ushers in a new way of evaluating bug report deduplication techniques, as well as a new kind of bug deduplication task. We show that simple IR measures can address this problem but also that further research is needed to refine this novel process that is integrate-able into modern bug report systems. -

Customization for Mobile Ebook Readers
CUSTOMIZATION FOR MOBILE EBOOK READERS _______________ A Thesis Presented to the Faculty of San Diego State University _______________ In Partial Fulfillment of the Requirements for the Degree Master of Science in Computer Science _______________ by Swathi R. Simmula Summer 2013 iii Copyright © 2013 by Swathi R. Simmula All Rights Reserved iv DEDICATION Dedicated to my Sai, Parents and Friends. v I climbed and climbed where is the peak my lord, I ploughed and ploughed where is the knowledge treasure my load, I sailed and sailed where is the island of peace my lord, almighty bless my nation with vision and sweat resulting into happiness -Dr. A. P. J. Kalam vi ABSTRACT OF THE THESIS Customization for Mobile EBook Readers by Swathi R. Simmula Master of Science in Computer Science San Diego State University, 2013 Today’s mobile phone users are often extensively dependent upon applications to accomplish their daily needs. Mobile applications help the users in the following ways: accessing email, navigation, chatting, reading e Books etc. All these purposes are fulfilled only when there is a framework, which provides a complete mobile platform to achieve these tasks. Android is one of the mobile application based platforms for providing a wide range of applications that are reliable. An electronic book (variously, e-book, eBook, digital book, or even e-editions) is a book-length publication in digital form, consisting of text, images, or both, and produced on, published through, and readable on computers, Mobiles or other electronic devices. E-book websites can include the ability to translate books into many different languages, making the works available to speakers of languages not covered by printed translations. -
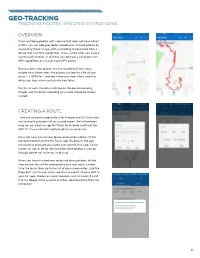
Geo-Tracking Tracking Routes, Syncing Coordinates
geo-tracking tracking routes, syncing coordinates overview: If you are taking photos with a device that does not have a built in GPS, you can add geographic coordinates to those photos by associating those images with a recording of your route from a device that has GPS capabilities. This is useful when you have a camera with no built-in GPS but you do have a cell phone with GPS capabilities or a stand-alone GPS device. Because both your photos and the recording of your route include time information, the photos can look to a file of your route — a GPX file — and see where you were, when, and thus where you were when each photo was taken. For this to work, the date and time on the device recording images and the device recording your route should be closely synced. creating a route: There are numerous applications for Android and iOS that allow you to record geographical routes and export that information. Here we are using the app My Tracks for Android (myTracks for iOS). It is free and works well enough for our purposes. Once you have synced your phone and camera clocks, hit the red record button on the My Tracks app. By default, the app will continue to record your route until you tell it to stop. Go for a walk, car trip, or jet ski ride and take some photos as you go (though please not while you’re driving). When you have finished your route and taking photos, hit the stop button. You will be prompted to give your route a name. -

An Android Application for Capturing Mobility Behavior
EasyTracker: An Android application for capturing mobility behavior Alexandros Doulamis Nikos Pelekis Yannis Theodoridis Dept. of Informatics Dept. of Statistics & Insurance Sci. Dept. of Informatics University of Piraeus University of Piraeus University of Piraeus Piraeus, Greece Piraeus, Greece Piraeus, Greece [email protected] [email protected] [email protected] Abstract — This paper presents EasyTracker, a mobile EasyTracker provides end users with personalized privacy application developed for the Android O/S that enable the functionality [8]. storage, analysis and map visualization of routes of mobile The second key functionality is that EasyTracker allows users. Furthermore, it enable users to manually annotate part a user to annotate parts of her track with labels and therefore of their routes with labels describing their activity and to describe her current activity (e.g. “stopped at café A”, behavior (e.g. “home having breakfast”, “travelling by car to “driving towards office”) [9]. Such feature can turn out to be work”, etc.). Of equal importance, the application encapsulates very useful for automatic fill-in of surveys performed in several state-of-the-art line simplification algorithms for transportation science or for researchers working on activity compressing the trajectories drawn from collected GPS recognition who are usually restricted to use manually records, as well as segmenting trajectories into homogeneous processed surveys. parts in order to facilitate automatic auditing of the user’s manual annotation. Third, EasyTracker encapsulates state-of-the-art algorithms that process in an online fashion the received Keywords - EasyTracker; GPS data; trajectory; path; track; stream of GPS recordings and transforms it into meaningful privacy; compression; segmentation; Android OS tracks, ready to be stored into a trajectory database [10] for further analysis. -

Edoctor: Automatically Diagnosing Abnormal Battery Drain Issues on Smartphones
eDoctor: Automatically Diagnosing Abnormal Battery Drain Issues on Smartphones Xiao Ma∗†, Peng Huang∗, Xinxin Jin∗, Pei Wang‡, Soyeon Park∗, Dongcai Shen∗ Yuanyuan Zhou∗, Lawrence K. Saul∗ and Geoffrey M. Voelker∗ ∗Univ. of California at San Diego, †Univ. of Illinois at Urbana-Champaign, ‡Peking Univ., China Abstract profiling [18, 36, 46, 52], energy efficient hardware [21, 30], operating systems [7, 10, 15, 29, 42, 49, 50, 51], lo- The past few years have witnessed an evolutionary cation services [14, 20, 26, 31], displays [5, 17] and net- change in the smartphone ecosystem. Smartphones have working [4, 6, 32, 41, 43]. Previous work has achieved gone from closed platforms containing only pre-installed notable improvements in smartphone battery life, yet the applications to open platforms hosting a variety of third- focus has primarily been on normal usage, i.e., where the party applications. Unfortunately, this change has also led energy used is needed for normal operation. to a rapidincrease in Abnormal Battery Drain (ABD) prob- In this work, we address an under-explored, yet emerg- lems that can be caused by software defects or miscon- ing type of battery problem on smartphones – Abnormal figuration. Such issues can drain a fully-charged battery Battery Drain (ABD). within a couple of hours, and can potentially affect a sig- nificant number of users. This paper presents eDoctor, a practical tool that helps 1.1 Abnormal Battery Drain Issues regular users troubleshoot abnormal battery drain issues on smartphones. eDoctor leverages the concept of exe- ABD refers to abnormally fast draining of a smartphone’s cution phases to capture an app’s time-varying behavior, battery that is not caused by normal resource usage. -

Student Handbook A.Y.2015-16/I Sem
IV-B.Tech STUDENT HANDBOOK A.Y.2015-16/I SEM Department of IT MARRI LAXMAN REDDY INSTITUTIONS MLR Institute of Technology Dundigal (V), Quthbullapur (M), R.R Dist, Hyderabad – 500043, A.P www.mlrinstitutions.ac.in VISION STATEMENT VISION STATEMENT OF MLRIT To create and nurture competent Engineers and managers who would be enterprise leaders in all parts of the world with aims of reaching the skies and touching the stars and yet feet firmly planted on the ground – good human beings steeped in ethical and moral values. MISSION STATEMENT MISSION STATEMENT OF MLRIT MLR Institute of Technology is committed to providing a positive, professional and conducive learning environment where all students are inspired to achieve their potential and strive for excellence in a global society as dignified professionals with the cooperation of all stakeholders. GOALS OF MLRIT GOALS OF MLRIT Goals of Engineering education at undergraduate / graduate level: ÿ Equip students with industry – accepted career and life skills ÿ To create a knowledge warehouse for students ÿ To disseminate information on skills and competencies that are in use and in demand by the industry ÿ To create learning environment where the campus culture acts as a catalyst to student fraternity to understand their core competencies, enhance their competencies and improve their career prospects. ÿ To provide base for lifelong learning and professional development in support of evolving career objectives, which include being informed, effective, and responsible participants within the engineering profession and in society. ÿ To prepare students for graduate study in Engineering and Technology. ÿ To prepare graduates to engineering practice by learining from professional engineering assignments. -

Appropriate Obfuscation of Location Information on an Application Level for Mobile Devices
Appropriate obfuscation of location information on an application level for mobile devices Empower user to regain control of their location privacy DIPLOMARBEIT zur Erlangung des akademischen Grades Diplom-Ingenieur im Rahmen des Studiums Software Engineering & Internet Computing eingereicht von Christoph Hochreiner Matrikelnummer 0726292 an der Fakultät für Informatik der Technischen Universität Wien Betreuung: Privatdoz. Dipl.-Ing. Mag.rer.soc.oec. Dr.techn. Edgar Weippl Mitwirkung: Univ. Lektor Dr.techn. Markus Huber, MSc Wien, TODOTT.MM.JJJJ (Unterschrift Verfasser) (Unterschrift Betreuung) Technische Universität Wien A-1040 Wien Karlsplatz 13 Tel. +43-1-58801-0 www.tuwien.ac.at Appropriate obfuscation of location information on an application level for mobile devices Empower user to regain control of their location privacy MASTER’S THESIS submitted in partial fulfillment of the requirements for the degree of Diplom-Ingenieur in Software Engineering & Internet Computing by Christoph Hochreiner Registration Number 0726292 to the Faculty of Informatics at the Vienna University of Technology Advisor: Privatdoz. Dipl.-Ing. Mag.rer.soc.oec. Dr.techn. Edgar Weippl Assistance: Univ. Lektor Dr.techn. Markus Huber, MSc Vienna, TODOTT.MM.JJJJ (Signature of Author) (Signature of Advisor) Technische Universität Wien A-1040 Wien Karlsplatz 13 Tel. +43-1-58801-0 www.tuwien.ac.at Erklärung zur Verfassung der Arbeit Christoph Hochreiner Jungerstraße 16, 4950 Altheim Hiermit erkläre ich, dass ich diese Arbeit selbständig verfasst habe, dass ich die verwende- ten Quellen und Hilfsmittel vollständig angegeben habe und dass ich die Stellen der Arbeit - einschließlich Tabellen, Karten und Abbildungen -, die anderen Werken oder dem Internet im Wortlaut oder dem Sinn nach entnommen sind, auf jeden Fall unter Angabe der Quelle als Ent- lehnung kenntlich gemacht habe. -

Download (183Kb)
Word Count: 3743 Plagiarism Percentage 9% sources: 3% match (Internet from 05-May-2016) 1 http://www.arpnjournals.com/jeas/research_papers/rp_2014/jeas_1214_1346.pdf 1% match (Internet from 22-Dec-2017) 2 https://www.safaribooksonline.com/library/view/php-and- mysql/9781118066881/9781118066881c19.xhtml 1% match (Internet from 08-Sep-2017) 3 http://docplayer.net/33974015-Arxiv-v1-cs-se-5-aug-2016.html 1% match (Internet from 21-Jul-2017) 4 http://repository.petra.ac.id/17335/1/Publikasi1_00016_2626.pdf < 1% match (publications) 5 Lecture Notes in Electrical Engineering, 2016. < 1% match (publications) 6 Alexander Setiawan, Andreas Handojo, Rendra Hadi. "Indonesian Culture Learning Application Based on Android", International Journal of Electrical and Computer Engineering (IJECE), 2017 < 1% match (publications) 7 Ratul Sikder, Md. Jamal Uddin, Sajal Halder. "An efficient approach of identifying tourist by call detail record analysis", 2016 International Workshop on Computational Intelligence (IWCI), 2016 < 1% match (Internet from 27-May-2009) 8 http://www.terry.uga.edu/~rwatson/dm5e/Reader/answers/chapter16.html < 1% match (Internet from 24-Sep-2016) 9 http://library.cmu.ac.th/scholarly/index.php?Author=23398014000 < 1% match (Internet from 30-Jan-2016) 10 http://toc.proceedings.com/24338webtoc.pdf < 1% match (Internet from 26-Dec-2016) 11 http://dblp.dagstuhl.de/pers/hc/s/Szydlo:Tomasz < 1% match (publications) 12 Andreas Handojo. "Broadcast learning system using multicast address", 2010 2nd International Conference on Education Technology and Computer, 06/2010 < 1% match (publications) 13 "Bioinformatics and Biomedical Engineering", Springer Nature, 2017 < 1% match (Internet from 25-Oct-2017) 14 http://ijmas.iraj.in/paper_detail.php? name=Hybrid_Framework_as_a_Cross_Platform_Tool_For_Designing_and_Developing_a_Mobile_Application_Serving_the_Internship_Program_Management&paper_id=6655 < 1% match (publications) 15 D Hartama, Herman Mawengkang, M Zarlis, R W Sembiring.