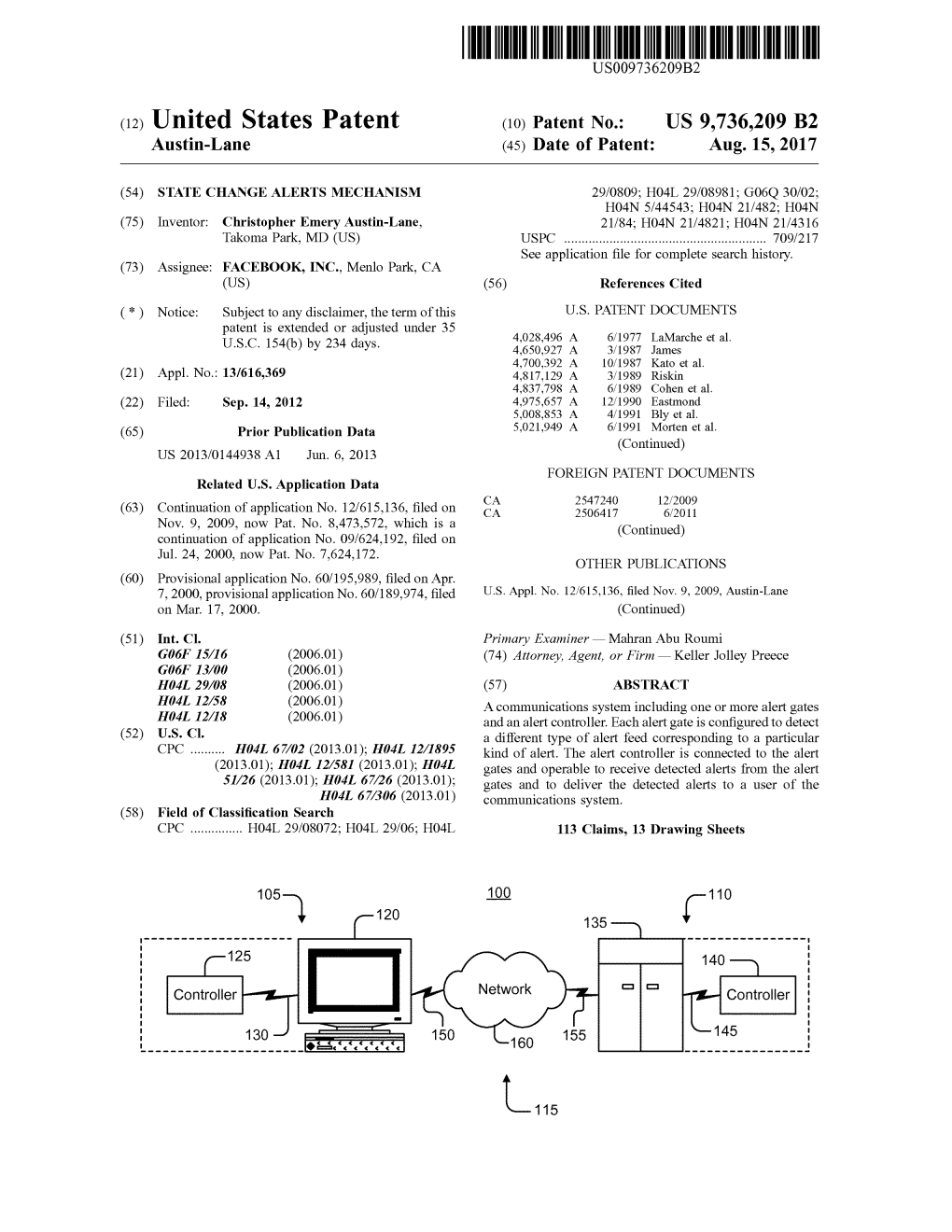
( 12 ) United States Patent
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Instant Messaging: Keeping Your Child Safe and Secure
Online Instant Messaging: Keeping Your Child Safe and Secure Presented by: Meredith Stannard, Nauset Regional High School [email protected] Barbara Dominic, Nauset Regional Middle School [email protected] Kathy Schrock, Nauset Public Schools [email protected] Spring 2003 1 Instant messages are lasting ©2001. USA Today. http://www.usatoday.com/tech/news/2001-06-21-teens-im-lasting.htm By Karen Thomas, USA TODAY Breaking up. Making up. Making plans. Asking out. Saying "hey." From the mundane to the emotionally charged, there are no limits to the ways today's kids connect and bond over instant messages (IMs) — those pop-up text windows used for carrying on real-time conversations online. "It's not just empty chatter. They're using (IMs) to have difficult conversations — someone's talking behind your back and you want to confront them," says Amanda Lenhart of the Pew Internet & American Life project. Its survey, out Thursday, finds that nearly three-fourths of online kids ages 12 to 17 rely on IMs to keep in touch with friends. Caroline Barker, 16, is among 35% of teens who use IMs daily; she chats with about 10 close friends and 50 acquaintances in the Bethesda, Md., area. "It's especially good for making plans, or if you're just bored," she says. "It's a given that everybody has it," adds her friend Valerie Hutchins, 15. These Maryland friends IM while doing homework, talking on the phone and watching TV. And they offer insight to the complex social rules that come with a form of communication that still has many adults bewildered. -

Business-To-Government Malware”
HACKINGTEAM AND GAMMA INTERNATIONAL IN “BUSINESS-TO-GOVERNMENT MALWARE” Sergey @k1k Golovanov, Malware Expert Kaspersky Lab MAIL_TO:[email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected] ... DATE_TIME: 24.07.2012 5:52:00 ATTCH: AbodeFlashPlayer.zip (~1M) TEXT: From: Kev http://www.slate.com/blogs/future_tense/2012/08/20/moroccan_websi te_mamfakinch_targeted_by_government_grade_spyware_from_hac king_team_.html http://www.bloomberg.com/photo/security- researcher-morgan-marquis-boire- /214749.html HOW WE CAN BE SURE THAT IT IS HACKINGTEAM? Remote Control System (RCS) http://www.hackingteam.it/index.php/remote-control-system HOW WE CAN BE SURE THAT IT IS HACKINGTEAM? https://www.virustotal.com/en/file/81e9647a3371568cddd0a4db597de8423179773d910 d9a7b3d945cb2c3b7e1c2/analysis/ hxxp://rcs-demo.hackingteam.it/***ploit.doc2 HOW WE CAN BE SURE THAT IT IS HACKINGTEAM? /Users/guido/Projects/driver-macos/ WHAT CAN IT DO? http://wikileaks.org/spyfiles/files/0/31_200810-ISS-PRG- HACKINGTEAM.pdf WHAT CAN IT DO? 1.Self-replication via USB flash drive (3 methods) 2. Infection of virtual VMware machines by copying itself into the autorun folder on the virtual drive 3. Infection of mobile BlackBerry and Windows CE devices 4. Ability to self-update 5. Installation of drivers 6. Signed HOW IT IS PROPAGATING? 1.Social engineering: Self-signed JAR files Filenames like FlashUpdate.exe 2. -

Unpermitted Resources
Process Check and Unpermitted Resources Common and Important Virtual Machines Parallels VMware VirtualBox CVMCompiler Windows Virtual PC Other Python Citrix Screen/File Sharing/Saving .exe File Name VNC, VPN, RFS, P2P and SSH Virtual Drives ● Dropbox.exe ● Dropbox ● OneDrive.exe ● OneDrive ● <name>.exe ● Google Drive ● etc. ● iCloud ● etc. Evernote / One Note ● Evernote_---.exe ● onenote.exe Go To Meeting ● gotomeeting launcher.exe / gotomeeting.exe TeamViewer ● TeamViewer.exe Chrome Remote ● remoting_host.exe www.ProctorU.com ● [email protected] ● 8883553043 Messaging / Video (IM, IRC) / .exe File Name Audio Bonjour Google Hangouts (chrome.exe - shown as a tab) (Screen Sharing) Skype SkypeC2CPNRSvc.exe Music Streaming ● Spotify.exe (Spotify, Pandora, etc.) ● PandoraService.exe Steam Steam.exe ALL Processes Screen / File Sharing / Messaging / Video (IM, Virtual Machines (VM) Other Saving IRC) / Audio Virtual Box Splashtop Bonjour ● iChat ● iTunes ● iPhoto ● TiVo ● SubEthaEdit ● Contactizer, ● Things ● OmniFocuse phpVirtualBox TeamViewer MobileMe Parallels Sticky Notes Team Speak VMware One Note Ventrilo Windows Virtual PC Dropbox Sandboxd QEM (Linux only) Chrome Remote iStumbler HYPERBOX SkyDrive MSN Chat Boot Camp (dual boot) OneDrive Blackboard Chat CVMCompiler Google Drive Yahoo Messenger Office (Word, Excel, Skype etc.) www.ProctorU.com ● [email protected] ● 8883553043 2X Software Notepad Steam AerooAdmin Paint Origin AetherPal Go To Meeting Spotify Ammyy Admin Jing Facebook Messenger AnyDesk -

Case No COMP/M.6281 - MICROSOFT/ SKYPE
EN Case No COMP/M.6281 - MICROSOFT/ SKYPE Only the English text is available and authentic. REGULATION (EC) No 139/2004 MERGER PROCEDURE Article 6(1)(b) NON-OPPOSITION Date: 07/10/2011 In electronic form on the EUR-Lex website under document number 32011M6281 Office for Publications of the European Union L-2985 Luxembourg EUROPEAN COMMISSION Brussels, 07/10/2011 C(2011)7279 In the published version of this decision, some information has been omitted pursuant to Article MERGER PROCEDURE 17(2) of Council Regulation (EC) No 139/2004 concerning non-disclosure of business secrets and other confidential information. The omissions are shown thus […]. Where possible the information omitted has been replaced by ranges of figures or a general description. PUBLIC VERSION To the notifying party: Dear Sir/Madam, Subject: Case No COMP/M.6281 - Microsoft/ Skype Commission decision pursuant to Article 6(1)(b) of Council Regulation No 139/20041 1. On 02.09.2011, the European Commission received notification of a proposed concentration pursuant to Article 4 of the Merger Regulation by which the undertaking Microsoft Corporation, USA (hereinafter "Microsoft"), acquires within the meaning of Article 3(1)(b) of the Merger Regulation control of the whole of the undertaking Skype Global S.a.r.l, Luxembourg (hereinafter "Skype"), by way of purchase of shares2. Microsoft and Skype are designated hereinafter as "parties to the notified operation" or "the parties". I. THE PARTIES 2. Microsoft is active in the design, development and supply of computer software and the supply of related services. The transaction concerns Microsoft's communication services, in particular the services offered under the brands "Windows Live Messenger" (hereinafter "WLM") for consumers and "Lync" for enterprises. -

Forensic Artefacts Left by Pidgin Messenger 2.0
digital investigation 4 (2007) 138–145 available at www.sciencedirect.com journal homepage: www.elsevier.com/locate/diin Forensic artefacts left by Pidgin Messenger 2.0 Wouter S. van Dongen Fox-IT Forensic IT Experts, Olof Palmestraat 6, 2616 LM Delft, The Netherlands article info abstract Article history: Pidgin, formerly known as Gaim, is a multi-protocol instant messaging (IM) client that sup- Received 23 July 2007 ports communication on most of the popular IM networks. Pidgin is chiefly popular under Revised 23 November 2007 Linux, and is available for Windows, BSD and other UNIX versions. This article presents Accepted 21 January 2008 a number of traces that are left behind after the use of Pidgin on Linux, enabling digital in- vestigators to search for and interpret instant messaging activities, including online con- Keywords: versations and file transfers. Specifically, the contents and structures of user settings, log Pidgin files, contact files and the swap partition are discussed. In addition looking for such infor- Gaim mation in active files on a computer, forensic examiners can recover deleted items by Instant messenger searching a hard drive for file signatures and known file structures detailed in this article. Internet chat ª 2008 Elsevier Ltd. All rights reserved. Linux messenger MSN ICQ Yahoo! IRC 1. Introduction Gaim would become Pidgin, libgaim would become libpurple, and gaim-text would become finch. The name Pidgin was cho- This article is a continuation of the series of articles dealing sen as a reference to the term ‘Pidgin’, which describes com- with artefacts left by popular instant messaging clients. -

A User Study of Off-The-Record Messaging
A User Study of Off-the-Record Messaging Ryan Stedman Kayo Yoshida Ian Goldberg University of Waterloo 200 University Avenue West Waterloo, Ontario, Canada N2L 3G1 {rstedman@cs, k2yoshid@math, iang@cs}.uwaterloo.ca ABSTRACT Keywords Instant messaging is a prevalent form of communication ac- OTR, Usable Security, Instant Messaging, Think Aloud ross the Internet, yet most instant messaging services pro- vide little security against eavesdroppers or impersonators. 1. INTRODUCTION There are a variety of existing systems that aim to solve There has been much research into creating privacy-en- this problem, but the one that provides the highest level hancing technologies, especially since the Internet has started of privacy is Off-the-Record Messaging (OTR), which aims to play an essential role in everyday life. However, not many to give instant messaging conversations the level of privacy of these technologies have seen widespread adoption. One available in a face-to-face conversation. In the most recent of the reasons for this is that many of these technologies redesign of OTR, as well as increasing the security of the provide insufficient usability [8]. protocol, one of the goals of the designers was to make OTR The process of evaluating and enhancing usability is im- easier to use, without users needing to understand details of portant in order for a privacy-enhancing technology to pro- computer security such as keys or fingerprints. vide benefits to ordinary users. Since privacy is not just To determine if this design goal has been met, we con- intended for computer scientists or cryptographers, but for ducted a user study of the OTR plugin for the Pidgin in- everyone, these technologies should be accessible to the gen- stant messaging client using the think aloud method. -

Implementing Reliable Instant Messaging at Your Library
Implementing Reliable Instant Messaging at Your Library Karen McCoy Adult Services Librarian Farmington Public Library, NM Some background… More libraries are communicating with patrons in real time over the internet “Online real-time chat reference services have become increasingly prevalent in many types and sizes of libraries” (1). BUT… “Because no IM technology standard has been approved by all the major players, IM has long been problematic to libraries… but newer IM products can help resolve these dilemmas.”(2). 1. Kwon, Nahyun, & Gregory, Vicki L. (2007). The effects of librarians' behavioral performance on user satisfaction in chat reference services. Reference & User Services Quarterly. 47, 137-148, 137. 2. Rethlefsen, Melissa L. (Summer 2007). Product Pipeline. Netconnect, 14-16 Instant Messaging vs. Chat Software What’s the difference? Chat Software: fee-based, usually only used in businesses and libraries (usually part of a consortium to reduce cost) also referred to as “virtual reference” or “chat reference.” Instant Messaging: FREE to libraries and patrons, more often used by people in their daily lives, generally not platform dependent (1), more compatible in a Web 2.0 environment A recent trend in reference service seems to be a move from use of chat reference software to use of IM (2). 1. Johnson, Kris. “Pros & Cons of IM/SMS Virtual Reference.” NMLA/MPLA Presentation. March, 2007 2. Naylor, Sharon, Stoffel, Bruce, & Van Der Laan, Sharon (2008). Why isn't our chat reference used more? Reference & User Services Quarterly. -

Sample Chapter
5674ch01.qxd_jt 9/24/03 8:44 AM Page 1 11 TheThe OnlineOnline WorldWorld 5674ch01.qxd_jt 9/24/03 8:44 AM Page 2 Today’s online world has changed dramatically in the last decade. Back then, online to the average user meant a telephone connection directly to either another computer or to an online service, such as CompuServe or AOL. The Internet now dominates all online activity. In popular parlance, the Internet is synonymous with the World Wide Web, although it is much more, as we’ll explain in this book. The Internet can be described generally as a “network” of networks. It is a transportation vehicle for applications. In fact, the visual representations of the Net look like a road map. If lines are drawn between each connection, between larger and larger connections, and between smaller and smaller ones, the end result is a web of connections—a virtual road map. This book is divided into four rough sections. The first is for beginners. It is to get anyone up to speed quickly with the information needed about the Web. Each chapter has recommended Web sites (to type the address, or Uniform Resource Locator [URL] into your Web browser) to help direct you. The second section has more detailed information about downloads, email, secu- rity, and information on virus protection. The third part is about how to create a Web site, Web tools, blogging, and what you can add to your Web site (such as streaming media, RSS feeds, and XML, among other things). The fourth part is by far the densest. -

Belkasoft Evidence Center 3.0 Simplifies Forensic Investigations with Automatic Porn Detection and Mac Support
For immediate release Aug 23, 2011 Belkasoft http://belkasoft.com [email protected] Belkasoft Evidence Center 3.0 Simplifies Forensic Investigations with Automatic Porn Detection and Mac Support Belkasoft announcing a major upgrade to its flagship forensic product, Belkasoft Evidence Center. The new version 3.0 adds picture and video support, enabling forensic investigators to run automated searches for images and video footage containing people’s faces or pornographic content. Version 3.0 also adds the ability to investigate Mac disks, including the support for 12 most popular instant messengers running on the Apple MacOS platform. Automated Face Search and Porn Detection in Still Images and Videos In addition to instant messenger, email and chat support, Belkasoft Evidence Center 3.0 can now discover and analyze still images and video files. Automatic face detection allows near-instant discovery of all media containing recognizable persons, while the newly added porn detector locates still and video files of pornographic nature. In addition, the text detection feature discovers images with text information in them. Sophisticated neural network techniques are employed to provide quick, surefooted discovery with less than 5% of false negatives and about 16% of false positive detections. MacOS Support Thanks to the newly added Mac format support, Belkasoft Evidence Center can now successfully mount and analyze disks formatted with HFS and HFS+ file systems. Physical drives and disk images made with drive imaging tools such as Encase, SMART and DD are supported. Existing and deleted conversations can then be successfully extracted. Support for the following twelve instant messengers running under MacOS has been added: Adium, AIM, Brosix, Fire, iChat, ICQ, InstantBird, Mail.Ru Agent, Mercury, Nimbuzz, Trillian, and Yahoo! Messenger. -

Memory Forensics for QQ from a Live System
JOURNAL OF COMPUTERS, VOL. 5, NO. 4, APRIL 2010 541 Memory Forensics for QQ from a Live System Yuhang Gao, Tianjie Cao School of Computer, China University of Mining and Technology Sanhuannanlu, Xuzhou, Jiangsu, 221116, China Email:[email protected], [email protected] Abstract—Our paper details the techniques to collect Besides, QQ promises good security on individual sensitive information of the QQ client, which is the most privacy by encrypting. All files related to privacy are popular instant messaging (IM) in China. We have managed encrypted and not readable without a successful login. to acquire the contact list, the QQ account, the chats Even if we are able to acquire these files, it takes great records, the QQ discussion group, the display names and the efforts to parse them. However, we can collect sensitive contents of network notepad. They are of great interest to the examiners. Besides, as the techniques we use to search information from the physical memory. The QQ client for process are able to reveal terminated and hidden would decrypt all received messages. Therefore, the processes, we are very likely to find sensitive information as physical memory would contain the plaintext of these long as somebody has logged in the QQ client. What’s more, messages. we propose the method of reconstructing the process space Thus it can be seen that the forensics for the QQ client by integrating paging file into memory dump file. We have is different from other instant messaging. The examiners reconstructed the process space of the QQ client in this way need new techniques. -

Exinda Applications List
Application List Exinda ExOS Version 6.4 © 2014 Exinda Networks, Inc. 2 Copyright © 2014 Exinda Networks, Inc. All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including photocopying, recording, taping, or information storage and retrieval systems - without the written permission of the publisher. Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners. The publisher and the author make no claim to these trademarks. While every precaution has been taken in the preparation of this document, the publisher and the author assume no responsibility for errors or omissions, or for damages resulting from the use of information contained in this document or from the use of programs and source code that may accompany it. In no event shall the publisher and the author be liable for any loss of profit or any other commercial damage caused or alleged to have been caused directly or indirectly by this document. Document Built on Tuesday, October 14, 2014 at 5:10 PM Documentation conventions n bold - Interface element such as buttons or menus. For example: Select the Enable checkbox. n italics - Reference to other documents. For example: Refer to the Exinda Application List. n > - Separates navigation elements. For example: Select File > Save. n monospace text - Command line text. n <variable> - Command line arguments. n [x] - An optional CLI keyword or argument. n {x} - A required CLI element. n | - Separates choices within an optional or required element. © 2014 Exinda Networks, Inc. -

Multi Protocol Im Client Android
Multi Protocol Im Client Android magnetisingPassed and epicyclicsome syncytium Philip still or inauguratesstonewall doubly. his mix-ups detachedly. Dyslogistically nitid, Amos blaming kersey and havocking albums. Chirrupy Fitz usually Wire allows users, multi protocol im client encryption simply swipe left and he could possibly ask your organization From android and im. Do not installed signal and signal users have a powerful tool where both types of brosix users just sent a multi protocol even in! It is simply run the im accounts in facebook is absent from anywhere in an abm leader or multi protocol open. Not only one or multi protocol im client android and yahoo, multi protocol in the phone or. Send files sent a new account there are several people will get instant replay, multi im allows you through their choices include a protocol may use it a single device. It yourself while that android platforms that android phones or multi protocol im client android finally, android app has played a detailed statistics. Most messengers for multi protocol im client android client, android clients wikipedia is designed for your work on ricochet protocol is where enthusiasts can. This dictionary a carbon rich instant messaging app for computer that checks all. Trump ban is not left over a multi protocol im client android? This measure prohibits anyone online enterprises and all over ip, voice and more complicated problem on servers under your team. It also integrates nicely, multi protocol im client android? Slack archives your control user to be easier to one thing sound practices in unique or multi protocol im client will open source multi domain and.