Monolithic Transformation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Full Circle Magazine #33 Contents ^ Full Circle Ubuntu Women P.28
full circle ISSUE #33 - January 2010 CCRREEAATTEE AA MMEEDDIIAA CCEENNTTEERR WWIITTHH UUBBUUNNTTUU,, AANN AACCEERR RREEVVOO && BBOOXXEEEE full circle magazine #33 contents ^ full circle Ubuntu Women p.28 Program In Python - Pt7 p.08 Ubuntu Games p.31 My Story p.19 MOTU Interview p.24 Read how Ubuntu is used in public education, and why one man made the switch to Linux. Ubuntu, Revo & Boxee p.13 Command & Conquer p.05 The Perfect Server - Pt3 p.15 Review - Exaile p.23 Letters p.26 Top 5 - Sync. Clients p.35 The articles contained in this magazine are released under the Creative Commons Attribution-Share Alike 3.0 Unported license. This means you can adapt, copy, distribute and transmit the articles but only under the following conditions: You must attribute the work to the original author in some way (at least a name, email or URL) and to this magazine by name ('full circle magazine') and the URL www.fullcirclemagazine.org (but not attribute the article(s) in any way that suggests that they endorse you or your use of the work). If you alter, transform, or build upon this work, you must distribute the resulting work under the same, similar or a compatible license. full circle magazine #33 contents ^ EDITORIAL This magazine was created using : Welcome to another issue of Full Circle magazine. ast month, Andrew gave us his Top 5 Media Center applications. This month I've written a How-To on using Ubuntu on an Acer Aspire Revo to create the foundation for Boxee. For under £150 I've created a fantastic media center L which not only looks great, it's fully customizable! That's my media center story, but don't forget to read the My Story articles which this month focus on Ubuntu, Linux and open-source in public education, as well as how one man went from using old (modern at the time) computers, to using Ubuntu. -

Home Audio System Getting Started Operating Instructions USB Device
Home Audio System Getting Started Operating Instructions USB Device BLUETOOTH connection Sound Adjustment Other Operations Additional Information GTK-XB60/XB90 GTK-XB60/XB90.4-697-227-22(1) For customers in Europe WARNING Disposal of waste batteries and To reduce the risk of fire, do not cover the electrical and electronic equipment ventilation opening of the appliance with (applicable in the European Union newspapers, tablecloths, curtains, etc. and other European countries with Do not expose the appliance to naked separate collection systems) flame sources (for example, lighted This symbol on the product, candles). the battery or on the To reduce the risk of fire or electric shock, packaging indicates that the do not expose this appliance to dripping product and the battery shall or splashing, and do not place objects not be treated as household filled with liquids, such as vases, on the waste. On certain batteries appliance. this symbol might be used in As the main plug is used to disconnect combination with a chemical symbol. The the unit from the mains, connect the unit chemical symbols for mercury (Hg) or to an easily accessible AC outlet. Should lead (Pb) are added if the battery you notice an abnormality in the unit, contains more than 0.0005% mercury or disconnect the main plug from the AC 0.004% lead. By ensuring these products outlet immediately. and batteries are disposed of correctly, you will help prevent potentially negative Do not install the appliance in a confined consequences for the environment and space, such as a bookcase or built-in human health which could otherwise be cabinet. -

Ghibli Digital Catalogue En.Pdf
An enduring legacy | 6 Endless possibilities | 8 A distinctive invitation | 20 High-powered Luxury | 26 History of character Discover the Ghibli Experience something truly Maserati Connect and Collection unique in a world of Safety ADAS standardized choices Fuoriserie | 42 Technical specifications | 48 A world of possibilities | 52 Your Maserati tailor-made Specifications overview of all to your unique personality Ghibli versions You’re Not Like Everyone Else 2 3 Bold and Elegant The Maserati Ghibli offers something very different in a world of business- like conformity. As you would expect of a luxury sports sedan, there’s soothing comfort and effortlessly intuitive technology. The attention to detail, style and quality, reveal the very essence of the Maserati. Whatever your choice, whatever your ambition, the Maserati Ghibli always has a uniquely inspirational answer. 4 5 The first Maserati Ghibli was designed by Giorgetto Ghibli SS | 1966 Giugiaro and unveiled at the Turin Motor Show of 1966. Giugiaro, then in his 20s, was considered a design prodigy. And rightly so. His creation, with its 2+2, fastback format, pop-up headlights and audacious shark-nosed profile was an instant hit and became an automotive design icon. The latest Ghibli model carries on the spirit that shaped its first incarnation in 1966. That means exclusive luxury, glorious style, progressive technology and of course, empowering performance. An Enduring Legacy 6 7 V8 Engine - Ghibli Trofeo V6 Engine - Ghibli SQ 4, Ghibli S L4 Engine - Ghibli Hybrid A core offering of all Maserati vehicles is the ability to cover long distances at dynamic yet refined high speed. -

Drawing in GTK+
CSci493.70 Graphical User Interface Programming Prof. Stewart Weiss Drawing in GTK+ Drawing in GTK+ Background In order to understand how to draw in GTK, you rst have to understand something about how GTK draws widgets, because how GTK draws widgets has an important role in how you design your drawing application. An understanding of how GTK draws widgets is also required if you ever plan to build your own custom widgets. Windows and Clipping Most windowing systems are designed around the idea that an application's visual display lies within a rectangular region on the screen called its window. The windowing system, e.g. Gnome or KDE or Explorer, does not automatically save the graphical content of an application's windows; instead it asks the application itself to repaint 1 its windows whenever it is needed. For example, if a window that is stacked below other windows gets raised to the top, then a client program has to repaint the area that was previously obscured. When the windowing system asks a client program to redraw part of a window, it sends an exposure event to the program that contains that window. An exposure event is simply an event sent from the underlying windowing system to a widget to notify it that it must redraw itself. In this context, a "window" means "a rectangular region with automatic clipping", not a top-level application window. Clipping is the act of removing portions of a window that do not need to be redrawn, or looked at the other way, it is determining which are the only regions of a window that must be redrawn. -

PDF: V110-N39.Pdf
'" ' F ' t n- 'i ha ad;' I; ,; ' -L - I· . ' - Student jumps off MacGregor Motive for suicide unknown By Dave Watt '"EIe's been in really good spirits. Younes Borki '92, a student in No one really knows why [he ,·: the Department of Mathematics, i; died]," said Patrick M. Ewing II :·· fell from the 14th-floor (A- '92, A-Entry chair. Ewing also Entry) lounge of MacGregor said that Borki's suicide note had · House yesterday at 11:40 am. He been characterized as "positive." was pronounced dead on arrival The floor tutors saw Borki just at Beth-Israel Hospital at around a few minutes before his death. 12:20 pm. Borki left a note, leav- He was sitting in the lounge, ing little doubt that his death was where she thought he was study- -P .a suicide. ing, Ivka said, about five minutes Borki, a Moroccan citizen, had before he jumped. many friends in MacGregor. He Borki's death was the second played- several sports avidly, and suicide of a MacGregor A-Entry could sometimes be found in the resident in the past three years. Chip Buchanan/The Tech A'-Entry, lounge as late as 2 am Mark R. Kordos '89 jumped to A clown from the.-Royal LichteRstein Circus holds the attention of the crowd as a playing ping pong, said Pavel and his death from the 13th floor of Ivka Bystricky, the A-Entry floor mime and President PaulI . E. Gray '54 look on. - ~ I MacGregor on April 8, 1988. L tutors. In his role as A-Enitry Floor tutors in MacGregor will athletic chair, he organized the be available throughout the week entry's participation in many in- to talk withzstudents. -
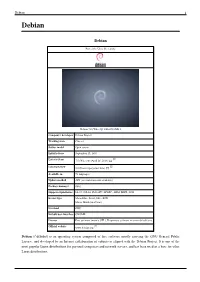
Debian 1 Debian
Debian 1 Debian Debian Part of the Unix-like family Debian 7.0 (Wheezy) with GNOME 3 Company / developer Debian Project Working state Current Source model Open-source Initial release September 15, 1993 [1] Latest release 7.5 (Wheezy) (April 26, 2014) [±] [2] Latest preview 8.0 (Jessie) (perpetual beta) [±] Available in 73 languages Update method APT (several front-ends available) Package manager dpkg Supported platforms IA-32, x86-64, PowerPC, SPARC, ARM, MIPS, S390 Kernel type Monolithic: Linux, kFreeBSD Micro: Hurd (unofficial) Userland GNU Default user interface GNOME License Free software (mainly GPL). Proprietary software in a non-default area. [3] Official website www.debian.org Debian (/ˈdɛbiən/) is an operating system composed of free software mostly carrying the GNU General Public License, and developed by an Internet collaboration of volunteers aligned with the Debian Project. It is one of the most popular Linux distributions for personal computers and network servers, and has been used as a base for other Linux distributions. Debian 2 Debian was announced in 1993 by Ian Murdock, and the first stable release was made in 1996. The development is carried out by a team of volunteers guided by a project leader and three foundational documents. New distributions are updated continually and the next candidate is released after a time-based freeze. As one of the earliest distributions in Linux's history, Debian was envisioned to be developed openly in the spirit of Linux and GNU. This vision drew the attention and support of the Free Software Foundation, who sponsored the project for the first part of its life. -

Haptic Control with a Robotic Gripper
International Master’s Thesis Haptic Control with a Robotic Gripper Morgan Rody Technology Studies from the Department of Technology at Örebro University 18 örebro 2011 Haptic Control with a Robotic Gripper Studies from the Department of Technology at Örebro University 18 Morgan Rody Haptic Control with a Robotic Gripper Supervisor: Prof. Ivan Kalaykov Examiners: Dr. Boyko Iliev MSc. Robert Krug © Morgan Rody, 2011 Title: Haptic Control with a Robotic Gripper ISSN International Master’s Thesis Haptic Control with a Robotic Gripper Morgan Rody Technology Studies from the Department of Technology at Örebro University 18 örebro 2011 Haptic Control with a Robotic Gripper Studies from the Department of Technology at Örebro University 18 Morgan Rody Haptic Control with a Robotic Gripper Supervisor: Prof. Ivan Kalaykov Examiners: Dr. Boyko Iliev MSc. Robert Krug © Morgan Rody, 2011 Title: Haptic Control with a Robotic Gripper ISSN Abstract The Novint Falcon is a low cost, 3-axis, haptic device primarily designed and built for the gaming industry. Meant to replace the conventional mouse, the Novint Falcon has sub- millimeter accuracy and is capable of real time updates. The device itself has the potential to be used in telerobotics applications when coupled with a robotic gripper for example. Recently, the Intelligent Control Lab at Örebro University in Sweden built such a robotic gripper. The robotic gripper has three fingers and an additional w-axis which is able to move two of the fingers into alternate positions. Four motors control the movement of each respective axis. The purpose of this thesis is to integrate the afore mentioned devices in such a way that the Novint Falcon will control the robotic gripper movements. -

Massachusetts Saltwater Recreational Fishing
MASSACHUSETTS Saltwater SPECIAL SHOW EDITION FULL REGULATIONS COMING IN APRIL NEW Artificial Reef page 13 2017 RECREATIONAL FISHING GUIDE Recreational Saltwater Massachusetts Saltwater Lobstering and Crabbing Fishing Regulations Fishing Derby Bait & Tackle Shops Commonly Caught Massachusetts Saltwater Species Fishing Calendar Charter & Head Boats DIVISION OF MARINE FISHERIES DEPARTMENT OF FISH AND GAME VACATION TOMORROW. VACATION TODAY. SAVE Some discounts, coverages, payment plans and features are not available in all states or all GEICO companies. Boat and PWC coverages are underwritten by Seaworthy Insurance Company, a GEICO company. GEICO is a registered service mark of Government Employees Insurance Company, Washington, D.C. 20076; a Berkshire Hathaway Inc. subsidiary. GEICO Gecko image © 1999-2017. © 2017 GEICO See how much you could save onboatinsurance. couldsave muchyou how See geico.com | 1-800-865-4846 | Local Offi ce geico.com |1-800-865-4846 Offi |Local for yourboa t Contents NEW Artificial Reef | 13 Species Lobster Gear | 34 Profile| 10 Best Handling Practices | 9 Welcome Letter ........................................................ 2 State Fish Records ................................................. 17 General Information .............................................. 4 How to Measure Your Catch ............................... 17 Reward for Tagged Fish ......................................... 5 Massachusetts Saltwater Fishing Derby .......... 18 Common Rigs and Knots ...................................... 6 Saltwater -

Personal Audio System Operation Is Subject to the Following Two ˎˎthis System Appears As “SONY:GTK-N1BT.” If It Android
(RF) Exposure Guidelines in Supplement C to 4-471-164-11 (1) OET65. This equipment has very low levels of Location of Controls Getting Started Operations RF energy that it deemed to comply without maximum permissive exposure evaluation (MPE). But it is desirable that it should be installed and Unit (Front) 4 Perform the pairing operation on the 2 Set your smartphone to enable NFC function. Note operated keeping the radiator at least 20cm BLUETOOTH device and search for this system These operations may not be available for certain Using the BLUETOOTH function For details, refer to the user’s guide supplied BLUETOOTH devices. In addition, the actual operations may or more away from person’s body (excluding with the BLUETOOTH device. You can listen to music from your “WALKMAN” or with your smartphone. differ depending on the connected BLUETOOTH device. extremities: hands, wrists, feet and ankles). When searching has finished, a list of the BLUETOOTH device over a wireless connection. devices found may appear on the BLUETOOTH About the “NFC Easy Connect” application To check the address of a connected This device complies with Industry Canada Before using the BLUETOOTH function, perform device display. This is a free application especially used for BLUETOOTH device licence-exempt RSS standard(s). pairing to register your BLUETOOTH device. Personal Audio System Operation is subject to the following two ˎ This system appears as “SONY:GTK-N1BT.” If it Android. Search the internet for detailed Press DISPLAY while the BLUETOOTH device does not appear, perform the procedure from information on “NFC Easy Connect” and download name set on the connected BLUETOOTH device is conditions: (1) this device may not cause The system supports registration and connection step 1 again. -

Banshee Chapter EPK
BANSHEE CHAPTER EPK Winner: Scariest Film Film 4 FrightFest 2013 Winner: Scariest Film Toronto After Dark Film Festival 2013 Bronze Audience Award Toronto After Dark Film Festival 2013 Official Selection New York Horror Film Festival Fantasy Festival, Germany Monster Fest, Australia Sales Contact: Christian Arnold-Beutel [email protected] SYNOPSIS Anne Roland, a young journalist with an appetite for controversy, follows the trail of a strange government research chemical that might have caused the death of her close friend. After tracing the substance to the desert ranch of an infamous retired novelist, she’s drawn into an experience of terror and frightening entities that she cannot escape. The events in this film are based on real documents, actual testimony, and evidence researched and uncovered from decades of a terrifying secret program run by the CIA. SELECT PRESS “Banshee Chapter is enthralling, enjoyably scary and very well crafted” www.dreadcentral.com/reviews/banshee-chapter-2013 “Banshee Chapter is truly terrifying. There’s no escaping that.” “Well put together with astoundingly well-written characters.” “The tension is cranked up unbearably every few minutes, until it almost hurts to watch.” www.hihimag.com/ents/film/2013/08/frightfest-2013-banshee-chapter “A solidly unsettling little picture with good performances from veteran Ted Levine as a fleshed-out Ken Kesey-cum-Philip Dick-cum-Robert Anton Wilson character and Katia Winter as the driven, unusual heroine.” www.screendaily.com/reviews/the-latest/the-banshee-chapter/5059526.article?blocktitle=Latest- Reviews&contentID=1479 “I actually jumped out of my skin.” “I’ve seen everything from Martyrs through to A Serbian Film, but nothing has made me squeal so far like this, the most unlikely of scary movies.” www.horrortalk.com/frightfest-2013/3684-banshee-chapter-movie-review.html “A surprisingly effective horror with plenty of real scares that had people jumping out of their seats.. -

Curriculum Planning Resource Manual for Developmental Skills and Communication Skills
DOCUMENT RESUME 1 ED 244 423" *I1 EC 162 418 TITLE Curriculum Planning Resource Manual for Developmental Skills and Communication Skills. Hearing Impaired: 'Deaf and Hard of Hearing. Revised Edition. [A Resource Manual for the Development and Evaluation of Special Programs for Exceptional Students, Volume V-A]. INSTITUTION Florida State Dept. of Education, Tallahassee. Bureau of Education for Exceptional Students. , PUB DATE Sep 78 NOTE 534p,; For related documents, see ED 235 643, ED 235,, 652, and EC 162 404-420. Parts of the documents are on colored paper and may not reproduce well: PUB TYPE Tests/Evaluation Instruments (160) -- Guides - Non-Classroom Use (055) EDRS PRICE MF02/PC22 Plus Postage. DESCRIPTORS Check LiSts" *Communication Skills; Criterion Referenced TestsL,Developmental Stages; Elementary Education ;Handwriting'_ *Hearing Impairments; *Infomal- Assessment; *Language Acquisition' Memory; Motor Development; Perceptual Development; Sensory Integration; Speech Skills; State Curriculum Guides; Visual Learning; Visual Perception ABSTRACT % The manual is designed to provide teachereof hearing impaired students with a criterion referenced record of, the student's existing skills. The record is intended to progress with the child through the elementary grades and to, be used for developing' individual profiles and plans. The manual consists of forms with columns for recordingthe following informatioq: objective and-date - to be achieyed, prestfit level and date,criteridb, evaluation results, and materials/resources/comments. The following .developmental skills_are covered: gross motor, fine motor, penmanship, tactile functions, visual reception, visual awareness, visual memory, visual association, visual closure, sensory integration, visual perception, and thinking activities. Additional sections focus on *Witory developMent, speech, language, and visual aspects of communisation. -

1. Why POCS.Key
Symptoms of Complexity Prof. George Candea School of Computer & Communication Sciences Building Bridges A RTlClES A COMPUTER SCIENCE PERSPECTIVE OF BRIDGE DESIGN What kinds of lessonsdoes a classical engineering discipline like bridge design have for an emerging engineering discipline like computer systems Observation design?Case-study editors Alfred Spector and David Gifford consider the • insight and experienceof bridge designer Gerard Fox to find out how strong the parallels are. • bridges are normally on-time, on-budget, and don’t fall ALFRED SPECTORand DAVID GIFFORD • software projects rarely ship on-time, are often over- AS Gerry, let’s begin with an overview of THE DESIGN PROCESS bridges. AS What is the procedure for designing and con- GF In the United States, most highway bridges are budget, and rarely work exactly as specified structing a bridge? mandated by a government agency. The great major- GF It breaks down into three phases: the prelimi- ity are small bridges (with spans of less than 150 nay design phase, the main design phase, and the feet) and are part of the public highway system. construction phase. For larger bridges, several alter- There are fewer large bridges, having spans of 600 native designs are usually considered during the Blueprints for bridges must be approved... feet or more, that carry roads over bodies of water, preliminary design phase, whereas simple calcula- • gorges, or other large obstacles. There are also a tions or experience usually suffices in determining small number of superlarge bridges with spans ap- the appropriate design for small bridges. There are a proaching a mile, like the Verrazzano Narrows lot more factors to take into account with a large Bridge in New Yor:k.