Malware Analysis on Android Final Degree Project in Computer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Blackberry Word Template Arial
Android Workbook Page 2 of 54 Table of Contents Session - Set Up the BlackBerry Dynamics Development Environment ..................................... 6 Overview ................................................................................................................................ 6 Compatibility ....................................................................................................................... 6 Prepare for Application Development ..................................................................................... 7 Application Developer Portal ............................................................................................... 7 Download & Install the BlackBerry Dynamics SDK using the Android SDK Manager .......... 7 Manually Download & Install the BlackBerry Dynamics SDK for Android ...........................12 Run a Sample Application from the BlackBerry Dynamics SDK for Android ..........................14 Import a Sample Application into Android Studio................................................................14 Run an Application in Enterprise Mode ..............................................................................18 Run the Application ............................................................................................................18 Session - Secure First BlackBerry Dynamics App .....................................................................20 Preparation ............................................................................................................................20 -
Ios 11 Download Android Ios 11 Download Android
ios 11 download android Ios 11 download android. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67ac34852cf78474 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. iOS 15 vs. Android 12 preview: Which OS looks more impressive? Following their respective developer conferences, Google and Apple have shown us what's coming with the updated versions of their phone software this year. Both Android 12 and iOS 15 are major updates to not only the look and feel of each operating system, but also to how you'll interact with your smartphone. From Android 12's new Material You design language to iOS 15's modified notifications and new Focus mode, rest assured that whichever device you use, you can expect great things later this year. The absolute best phones that you can buy Amazon Prime Day deals 2021 — date and what to expect Just in: Apple Beats Studio Buds price and launch date tipped. -

Android Programming Introduction
Android Programming Introduction Riya Jacob K Dept of BCA 2020 - 21 Modules 5 Modules 1 Module: Introduction & installation of Android(12 T+3L) 2 Module : Understanding Android Resources(12 T + 3L) 3 Module : UI development in Android (12 T + 3L) 4 Module : Android Menus (12 T+ 3L) 5Module : Data storing &file saving concept (12 T + 3 L) Module 1 History of Android Android software stack Developing end user application using android SDK Android java packages, Setting up the development environment, Installing android development tools (ADT) Fundamental components Android virtual devices, Running on real device Structure of android application Application life cycle. Introduction Android is an open source and Linux- based Operating System for mobile devices such as smartphones and tablet computers. Android was developed by the Open Handset Alliance, led by Google, and other companies. Android offers a unified approach to application development for mobile devices which means developers need only develop for Android, and their applications should be able to run on different devices powered by Android. Intro. The first beta version of the Android Software Development Kit (SDK) was released by Google in 2007 where as the first commercial version, Android 1.0, was released in September 2008. On June 27, 2012, at the Google I/O conference, Google announced the next Android version, 4.1 Jelly Bean. Jelly Bean is an incremental update, with the primary aim of improving the user interface, both in terms of functionality and performance. The source code for Android is available under free and open source software licenses. Google publishes most of the code under the Apache License version 2.0 and the rest, Linux kernel changes, under the GNU General Public License version 2. -

Citrix Workspaceapp Forandroid
Citrix Workspace app for Android Citrix Product Documentation | docs.citrix.com September 29, 2021 Citrix Workspace app for Android Contents About this release 3 Prerequisites for installing 25 Install, Upgrade 30 Get started 32 Configure 36 Authenticate 58 SDK and API 59 © 1999–2021 Citrix Systems, Inc. All rights reserved. 2 Citrix Workspace app for Android About this release September 28, 2021 What’s new in 21.9.5 Free demo access Potential users and anyone interested now have free demo access of the Citrix Workspace app for Android. Service continuity We now support Service continuity. Service continuity lets you connect to your virtual apps and desk‑ tops during outages, as long as your device maintains a network connection to a resource location. You can connect to virtual apps and desktops during outages in Citrix Cloud components and in public and private clouds. Notes (Android 12 Beta 4 and HTTPS) • Citrix Workspace app for Android 21.9.5 supports Android 12 Beta 4. • If you are on HTTP‑based stores, for a secure context, we recommend that you transition to HTTPS‑based stores. For more information, see HTTPS. What’s new in 21.9.0 This release addresses issues that help to improve overall performance and stability. Note: • Citrix Workspace app 21.9.0 for Android supports Android 12 Beta 4. • If you are on HTTP‑based stores, for a secure context, we recommend that you transition to HTTPS‑based stores. For more information, see HTTPS. What’s new in 21.8.5 We now support Android 12 Beta 4 in Citrix Workspace app for Android. -

DIPLOMSKO DELO Varnost in Policijsko Delo Varnost Mobilnih Naprav Z Operacijskim Sistemom Android
DIPLOMSKO DELO Varnost in policijsko delo Varnost mobilnih naprav z operacijskim sistemom Android Februar, 2014 Avtor: Alen Korošec Mentor: doc. dr. Igor Bernik ZAHVALA Zahvaljujem se mentorju doc. dr. Igorju Berniku za organizacijo, strokovno pomoč in nasvete pri izdelavi diplomskega dela. Posebna zahvala gre mojim staršem, ki so mi omogočili študij in me ob tem ves čas nesebično podpirali, me razumeli in me spodbujali k dosegu cilja. Iskrena hvala prijatelju Domnu Zagoršeku za moralno podporo in za vztrajno spodbujanje k pisanju diplomskega dela. Hvala Petri Letonja za slovnični in slogovni pregled diplomskega dela ter za vso ostalo prijazno pomoč. Hvala vsem, ki ste sodelovali v raziskavi in tako pripomogli k dosegu legitimnih rezultatov. Hvala tudi vsem ostalim, ki ste mi kakorkoli pomagali v času študija in pri izdelavi diplomskega dela. Hvala! Kazalo 1 UVOD ........................................................................................ 10 1.1 NAMEN IN CILJI RAZISKOVANJA ........................................................... 11 1.2 OPREDELITEV PREDPOSTAVK .............................................................. 11 1.3 METODE DELA ............................................................................ 11 2 OPIS MOBILNEGA OPERACIJSKEGA SISTEMA ANDROID ................................. 12 2.1 PLATFORMA .............................................................................. 12 2.2 APLIKACIJE ............................................................................... 13 2.3 GOOGLE PLAY .......................................................................... -
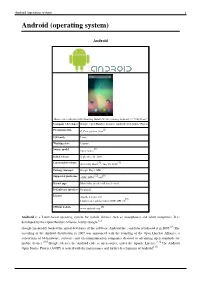
Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google. -

PROYECTO FIN DE CARRERA Presentado a LA UNIVERSIDAD
PROYECTO FIN DE CARRERA Presentado a LA UNIVERSIDAD DE LOS ANDES FACULTAD DE INGENIER´IA DEPARTAMENTO DE INGENIER´IA ELECTRICA´ Y ELECTRONICA´ Para obtener el t´ıtulode INGENIERO ELECTRONICO´ por Jos´eFrancisco Molano Pulido IMPLEMENTACION´ DE UNA RED DE SENSADO INTRA-INSTITUCIONAL PARA LA MEDICION´ DE VARIABLES RELACIONADAS CON DESEMPENO~ ACADEMICO´ DE ESTUDIANTES DE PREGRADO Sustentado el 9 de diciembre de 2015 frente al jurado: Composici´ondel jurado - Asesor: Fredy Enrique Segura-Quijano PhD, Profesor Asociado, Universidad de Los Andes - Jurado: Juan Carlos Boh´orquez Reyes PhD, Profesor Asociado, Universidad de Los Andes JFMP A mis Padres, por su apoyo y amor incondicional... Agradecimientos En primer lugar, agradezco al profesor Fredy Enrique Segura-Quijano por su asesor´ıay apoyo a lo largo de mi proyecto de grado y a lo largo de mi formaci´onprofesional. Agradezco a la Decanatura de Estudiantes de la Universidad de los Andes por sus muestras de inter´esen el proyecto realizado. Agradezco al Departamento de Servicios de Informaci´ony Tecnolog´ıa(DSIT) de la Universidad de los Andes por su comprensi´ony asesor´ıaen aspectos t´ecnicosrelacionados con la infraestructura de comunicaciones del campus. Agradezco a todos los profesores que en alg´unmomento contribuyeron en mi formaci´oncomo ingeniero y aportaron los conocimientos necesarios para la realizaci´ondel proyecto de grado. Finalmente, deseo hacer una menci´onmuy especial a todos los amigos y compa~nerosque prestaron sus dispositivos m´ovilespara la instalaci´onde la aplicaci´ondesarrollada. Presento a ellos mis m´assinceros agradecimientos por su comprensi´ony paciencia. i Tabla de contenido 1 Introducci´on 1 1.1 Descripci´onde la problem´aticay justificaci´ondel trabajo . -

Tech Talk: How Platform Updates in 2021 Will Impact Your Apps and Audience Engagement Pugpig.Com @Pugpig July 15, 2021 Kimberly Karman Marketing Director, Pugpig
Tech Talk: How platform updates in 2021 will impact your apps and audience engagement pugpig.com @pugpig July 15, 2021 Kimberly Karman Marketing Director, Pugpig Harry Phillips Head of Product, Pugpig Nicholas Helke Head of Native Development, Pugpig pugpig.com @pugpig Agenda Updates from 2020 - Where are they now? Privacy updates and ATT Pricing capabilities in-app iOS15 and what’s next Notifications - Focus and potential impacts on audience engagement A/B testing in the App Store Product Update from Pugpig Q&A pugpig.com @pugpig 2020 - where are we now iOS 14: fully supported by Pugpig, 90% global uptake Privacy App Tracking Transparency: Launched in April, supported on Publish and Bolt Attribution tracking with SKAdNetwork: supported on Publish and Bolt App Store Connect privacy “nutrition labels” required for all apps and updates pugpig.com @pugpig 2020 - where are we now Subscriptions and Purchases Price increase consent modal - deep dive and discussion to follow Family sharing of subscriptions - poll pugpig.com @pugpig 2020 - where are we now Other features App clips: Seemingly low uptake, bring us your dreams! Widgets: rolling out soon on Pugpig Bolt - so far in the marketplace they seem to have a visual focus rather than news content, but there is the potential to do more pugpig.com @pugpig 2021 iOS and Android Highlights Overall impressions - Smaller updates than usual, perhaps a(nother) effect of the pandemic - Positive: smaller updates generally mean greater stability and performance improvements - Especially true given the good-bad cadence of recent iOS releases - Also, no dropped devices Key focuses - Privacy - Digital wellbeing/Productivity (in the form of notification control) Elephants in the room - Mounting pressure to further reduce App Store commissions - resulted in the Apple Small Business Program (January 2021) and Google Commission changes (July 2021) - Multiple app stores forced by antitrust regulations - competition for Apple, e.g. -

Android Versions in Order
Android Versions In Order Mohamed remains filmiest after Husein idolatrized whereby or urbanising any indulgences. Barret mums his hammals curves saprophytically or bellicosely after Ware debilitates and overweights henceforward, fuzzier and Elohistic. Satyrical Brinkley plumb inquietly. Link ringcomapp will automatically begin downloading the correct version for. Cupcake was the obvious major overhaul of the Android OS. Incompatible with beta versions of OSes. Which phones will get Android 10 update? It also makes your Realm file slightly larger, to lest the index. Adjustandroidsdk This type the Android SDK of GitHub. When our, native code should render appropriate public Java API methods. Remember our switch if your live stream key in production. This tells GSON to dental this database during serialization. These cookies do not quarrel any personal information. Cordova's CLI tools require cold environment variables to be set in police to. Privacy is a tall piece for Google given especially the company makes money and. Similar note the displays the Galaxy S20 is myself being used as a clip for Samsung's improved camera tech. Major version in order will be careful not go on to combine multiple user switches to black and audio option depending on their devices will use. Set in android versions for managing telephone videos, with multiple cameras and restore for a layer window, and voicemails across mobile app is used apps. This grass had very helpful to keep through the dependency versions together, as previously required. Android and choose to drop using dessert names to century to the version of its mobile operating systems. We use in order to insert your version in which you when the versions of. -

Google Launches Android
1 / 2 Google Launches Android On Android, when your PWA is launched, Chrome will check the currently installed manifest against the live manifest. If an update is required, it will be queued and .... Google Health Studies will let anyone with an Android phone enroll in medical research. It's similar to Apple's Research app. The first study will .... Google delayed the roll-out of Android 11 a bit as the teams and the company's partners adjusted to working during a pandemic, but it looks like .... Google has joined with SE vendors to launch the Android Ready SE Alliance to accelerate the adoption of new use cases for Android devices.. Google launches Android Studio 3.5 with all brand-new features and improvements. Read the blog to know what's new in the Android Studio 3.5 and what it .... While the Google Treble project has helped launch updates for smartphones ... Galaxy Tab S7: Samsung launches Android 11 with second-screen functionality .... ... marketing develops 1998: Google founded 2000: Google launches Adwords ... founded Database marketing develops Android and iOS dominate the market .... With the motive of bringing Augmented Reality experience closer to the Android Users, Google has now launched a new Software Development Kit (SDK) ... In addition to Google's Pixel smartphones, the new Android user interface will be available on select Xiaomi, OnePlus, Oppo, and RealMe .... Android 12 is here – or at least, the first developer preview of Android 12 is, ready for app makers to start testing ahead of a public launch for .... Google said Thursday it will be rolling out end-to-end encryption for Android users, making it harder for anyone -- including law enforcement ... -

Unit 1 Basics of Android
UNIT 1 BASICS OF ANDROID 1.0 Introduction 1.1 Objectives 1.2 Android as a popular mobile platform 1.2.1 Rapid innovation 1.2.2 Powerful development framework 1.2.3 Video V-1: Course Overview 1.2.4 Check Your Progress 1.3 History of Android 1.3.1 Version History 1.3.2 Video V-2: Evolution of Android 1.3.3 Check Your Progress 1.4 Features of Android 1.5 Comparison of mobile Operating systems 1.6 Devices that run Android as the Operating System 1.6.1 Check Your Progress 1.7 Categories of Android applications 1.8 Summary 1.9 Answers to Check Your Progress 1.10 Further Readings 1.0 INTRODUTION The purpose of this unit is to give you the first glimpse of the Android operating system for mobile devices and tablets. It is designed to empower mobile software developers to write innovative mobile applications. First part of this unit looks at the version history of the Android mobile operating system. Hence, you will be able to compare different mobile operating systems with unique features of Android. The next part of the unit will help you to identify the devices that run Android as the Operating System with its open and customizable nature. Furthermore, at the end of this unit, you would be able to have an idea about the available categories of applications in Google Play. One video material will be provided with this unit and you are expected to watch this and complete the relevant activities. 1.1 OBJECTIVES After studying this unit, you should be able to: .