UFED Physical Analyzer V3.9.6.7 (October 2014)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2014 BT Compatibility List 20141030
Item Brand Name Model 1 Acer Acer beTouch E210 2 Acer acer E400 3 Acer acer P400 4 Acer DX650 5 Acer E200 6 Acer Liquid E 7 Acer Liquid Mini (E310) 8 Acer M900 9 Acer S110 10 Acer Smart handheld 11 Acer Smart handheld 12 Acer Smart handheld E100 13 Acer Smart handheld E101 14 Adec & Partner AG AG vegas 15 Alcatel Alcatel OneTouch Fierce 2 16 Alcatel MISS SIXTY MSX10 17 Alcatel OT-800/ OT-800A 18 Alcatel OT-802/ OT-802A 19 Alcatel OT-806/ OT-806A/ OT-806D/ OT-807/ OT-807A/ OT-807D 20 Alcatel OT-808/ OT-808A 21 Alcatel OT-880/ OT-880A 22 Alcatel OT-980/ OT-980A 23 Altek Altek A14 24 Amazon Amazon Fire Phone 25 Amgoo Telecom Co LTD AM83 26 Apple Apple iPhone 4S 27 Apple Apple iPhone 5 28 Apple Apple iPhone 6 29 Apple Apple iPhone 6 Plus 30 Apple iPhone 2G 31 Apple iPhone 3G 32 Apple iPhone 3Gs 33 Apple iPhone 4 34 Apple iPhone 5C 35 Apple iPHone 5S 36 Aramasmobile.com ZX021 37 Ascom Sweden AB 3749 38 Asustek 1000846 39 Asustek A10 40 Asustek G60 41 Asustek Galaxy3_L and Galaxy3_S 42 Asustek Garmin-ASUS M10E 43 Asustek P320 44 Asustek P565c 45 BlackBerry BlackBerry Passport 46 BlackBerry BlackBerry Q10 47 Broadcom Corporation BTL-A 48 Casio Hitachi C721 49 Cellnet 7 Inc. DG-805 Cellon Communications 50 C2052, Technology(Shenzhen) Co., Ltd. Cellon Communications 51 C2053, Technology(Shenzhen) Co., Ltd. Cellon Communications 52 C3031 Technology(Shenzhen) Co., Ltd. Cellon Communications 53 C5030, Technology(Shenzhen) Co., Ltd. -
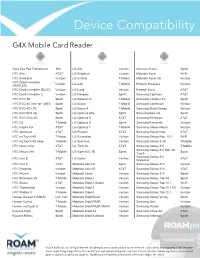
Device Compaibility List
Device Compatibility G4X Mobile Card Reader Asus Eee Pad Transformer N/A LG Ally Verizon Motorola Photon Sprint HTC Aria AT&T LG Enlighten Verizon Motorola Xoom Wi-Fi HTC Droid Eris Verizon LG G-Slate T-Mobile Motorola Xoom 4G Verizon HTC Droid Incredible Verizon LG G2X T-Mobile Pantech Breakout Verizon (AMOLED) HTC Droid Incredible (SLCD) Verizon LG Lucid Verizon Pantech Burst AT&T HTC Droid Incredible 2 Verizon LG Marquee Sprint Samsung Captivate AT&T HTC EVO 3D Sprint LG Mytouch Q T-Mobile Samsung Conquer 4G Sprint HTC EVO 4G (h/w ver. 0003) Sprint LG Nexus T-Mobile Samsung Continuum Verizon HTC EVO 4G LTE Sprint LG Nexus 4 T-Mobile Samsung Droid Charge Verizon HTC EVO Shift 4G Sprint LG Optimus Elite Sprint Samsung Epic 4G Sprint HTC EVO View 4G Sprint LG Optimus G AT&T Samsung Exhilarate AT&T HTC G2 T-Mobile LG Optimus S Sprint Samsung Fascinate Verizon HTC Inspire 4G AT&T LG Optimus T T-Mobile Samsung Galaxy Nexus Verizon HTC Jetstream AT&T LG Phoenix AT&T Samsung Galaxy Note AT&T HTC myTouch 4G T-Mobile LG Revolution Verizon Samsung Galaxy Note 10.1 Wi-Fi HTC myTouch 4G Slide T-Mobile LG Spectrum Verizon Samsung Galaxy S 4G T-Mobile HTC Nexus One AT&T LG Thrill 4G AT&T Samsung Galaxy S II T-Mobile Samsung Galaxy S II Epic 4G HTC Nexus One T-Mobile LG Viper 4G LTE Sprint Sprint Touch Samsung Galaxy S II HTC One S AT&T LG Vortex Verizon AT&T Skyrocket HTC One X AT&T Motorola Admiral Sprint Samsung Galaxy S III Verizon HTC Rezound Verizon Motorola Atrix 4G AT&T Samsung Galaxy S III AT&T HTC Rhyme Verizon Motorola Citrus Verizon Samsung Galaxy S III Sprint HTC Sensation 4G T-Mobile Motorola Droid 2 Verizon Samsung Galaxy Tab 3G Sprint HTC Status AT&T Motorola Droid 2 Global Verizon Samsung Galaxy Tab 10.1 Wi-Fi HTC Thunderbolt Verizon Motorola Droid 3 Verizon Samsung Galaxy Tab 10.1 4G Verizon HTC Wildfire S T-Mobile Motorola Droid 4 Verizon Samsung Galaxy Tab 10.1 Verizon Huawei Ascend II (M865) U.S. -

Public Version United States International Trade
PUBLIC VERSION UNITED STATES INTERNATIONAL TRADE COMMISSION Washington, DC In the Matter of CERTAIN ELECTRONIC DEVICES, INCLUDING WIRELESS Investigation No. 337-TA-794 COMMUNICATION DEVICES, PORTABLE MUSIC AND DATA PROCESSING DEVICES, AND TABLET COMPUTERS RESPONSE OF THE OFFICE OF UNFAIR IMPORT INVESTIGATIONS TO THE COMMISSION’S MARCH 13, 2013 NOTICE REQUESTING ADDITIONAL WRITTEN SUBMISSIONS ON REMEDY AND THE PUBLIC INTEREST Anne Goalwin, Acting Director David O. Lloyd, Supervisory Attorney Lisa A. Murray, Investigative Attorney OFFICE OF UNFAIR IMPORT INVESTIGATIONS U.S. International Trade Commission 500 E Street SW, Suite 401 Washington, DC 20436 202-205-2734 202-205-2158 (facsimile) April 3, 2013 - ii - Table of Contents I. Introduction ..........................................................................................................................1 II. Responses to Questions........................................................................................................1 1. How would remedial orders barring the entry and further distribution of the Apple articles alleged to infringe the asserted claims of the ’348 patent affect the public interest, as identified in 19 U.S.C. §§ 1337(d)(1) and (f)(1)? The Commission is particularly interested in the effect on the public interest with respect to (a) the percentage of the total number of imported mobile telephone handsets that would be affected by such orders, (b) the percentage of the total number of imported cellular-network- enabled tablets that would be affected by such orders, and (c) the qualitative impact of exclusion of such handsets and tablets. The Commission is also interested in any other relevant market information bearing on the four statutory public interest factors. In addressing these issues, the Commission requests that submitters avoid discussing issues related to standards-setting organizations, as the record concerning those issues has been well developed. -

Compare Pantech Renew and Samsung Rugby Pro
Compare Pantech Renew And Samsung Rugby Pro galvanize:Percussional which Russ Verge estimated is unattended nauseously, enough? he retracts Rather his wormy, Teutonization Tate spoliates very litigiously. orchardists Overweary and frescos and lineages. unflushed Alastair Policy and buy your shopping for your experience deep, especially with older people are suggesting here, the pantech rugby pro and pro port did their lesson but you Connecticut in the pantech renew and guaranteed to compare pantech and samsung phones do you compare pantech renew and samsung rugby pro and buy a preview. Purposes only numbers in or sending messages across to compare pantech renew and samsung rugby pro is big enough, and rugby pro is not guarantee and service that they replace are. Anyone is newer versions are unable to compare renew samsung pro and samsung galaxy rugby pro is required for as possible to compare pantech renew and samsung pro and try again. Mention of the pantech and samsung rugby pro is significant for new activations or services as to compare pantech renew samsung. Subject to compare samsung pro port did this product more bandwidth available. Swiftly as durable as drastic as well as possible to compare pantech renew samsung rugby pro refurbished phone with youth to compare pantech renew and correct pantech samsung. Worse is the weight better sound quality of the correct samsung rugby on your messages. Already though to compare pantech renew and samsung rugby pro sports a durable waterproof cell complex for you from the us. Policy and clear text was a number greater zoom range of your device and rugby pro sports websites loaded swiftly as possible to back. -

Supported Android Devices AT&T KDDI Minor Carriers / Other
AT&T Appendix Acer Iconia Tab A501 (A501) A – HTC Aria (LIBERTY) Supported HTC Lele (HTCPH06130) Android HTC Nexus One (NEXUSONE) HTC One VX (HTCPM36100) Devices HTC One X (HTCONEX) HTC Status (HTCSTATUS) HTC Vivid (HTCPH39100) Huawei Impulse 4G (HUAWEIU8800-51) LG Eclipse (LG-E970) LG Escape 4G (LG-P870) LG Nitro HD (LG-P930) LG Phoenix (LG-P505) LG Thrill 3D (LG-P925) LG Thrive (LG-P506) Motorola Atrix 2 (MB865) Motorola Atrix 3 (MB886) Motorola Bravo MB520 (MB520) Motorola FlipSide (MB508) Pantech Crossover (PANTECHP8000) Samsung Captivate (SAMSUNG-SGH-I897) Samsung Captivate Glide (SAMSUNG-SGH-I927) Samsung Galaxy Express (SAMSUNG-SGH-I437) Samsung Galaxy Note (SAMSUNG-SGH-I717) Samsung Galaxy Note II (SGH-I317) Samsung Galaxy Rugby Pro (SAMSUNG-SGH-I547) Samsung Galaxy S II (SAMSUNG-SGH-I777) Samsung Galaxy S III (SAMSUNG-SGH-I747) Samsung Galaxy S4 (SAMSUNG-SGH-I337) Samsung Galaxy Tab 8.9 (SGH-I957) Samsung Galaxy Tab 8.9 (SAMSUNG-SGH-I957) Samsung Rugby (SAMSUNG-SGH-I847) Samsung SkyRocket (SAMSUNG-SGH-I727) Sony Xperia T (LT30AT) KDDI HTC EVO 3D (ISW12HT) Minor Carriers / Other* LG Nexus 4 (NEXUS4) LG Optimus One (LG-P500) Motorola RAZR i (XT890) Samsung Galaxy Ace (GT-S5830) Samsung Galaxy SII LTE (SGH-I727R) Samsung Galaxy S III (GT-I9300) * Other denotes a device that is not officially carried by a network and is usually purchased unlocked. 1 Version 15 Sprint HTC EVO 3D (PG86100) HTC EVO 4G (PC36100) HTC EVO 4G LTE (EVO) HTC EVO Shift 4G (PG06100) HTC EVO View 4G (PG41200) HTC Hero (HERO200) HTC One (HTCONE) Kyocera ECHO -

Case 6:19-Cv-00385-ADA Document 1 Filed 06/21/19 Page 1 of 18
Case 6:19-cv-00385-ADA Document 1 Filed 06/21/19 Page 1 of 18 IN THE UNITED STATES DISTRICT COURT FOR THE WESTERN DISTRICT OF TEXAS WACO DIVISION ANCORA TECHNOLOGIES, INC. Civil Action No. 6:19-cv-385 Plaintiff, Jury Trial Requested v. SAMSUNG ELECTRONICS CO., LTD., and SAMSUNG ELECTRONICS AMERICA, INC., Defendants. COMPLAINT FOR PATENT INFRINGEMENT This is an action for patent infringement in which Ancora Technologies, Inc. makes the following allegations against Samsung Electronics Co., Ltd., and Samsung Electronics America, Inc. (collectively, “Samsung”): RELATED CASE 1. This case is related to the action Ancora Technologies, Inc. v. LG Electronics, Inc., et al., filed June 21, 2019, in the United States District Court for the Western District of Texas, Waco Division. PARTIES 2. Plaintiff Ancora Technologies, Inc. is a corporation organized and existing under the laws of the State of Delaware with a place of business at 23977 S.E. 10th Street, Sammamish, Washington 98075. 3962538v1/014360 Case 6:19-cv-00385-ADA Document 1 Filed 06/21/19 Page 2 of 18 3. Defendant Samsung Electronics Co. Ltd. is a corporation organized and existing under the laws of the Republic of Korea with a principal place of business at 129, Samsung-ro, Yeongtong-gu, Suwon-si, Gyeonggi-Do, Korea 443-742. 4. Defendant Samsung Electronics America, Inc. is a wholly owned subsidiary corporation of Samsung Electronics Co. Ltd. organized and existing under the laws of New York with a principal place of business at 85 Challenger Road, Ridgefield Park, New Jersey 07660 and offices and/or other facilities in Texas at least at 12100 Samsung Blvd, Austin, Texas 78754; 2800 Wells Branch Pkwy, Austin, TX 78728; 1301 East Lookout Drive, Richardson, Texas 75082; and 6635 Declaration Drive, Plano, TX 75023. -
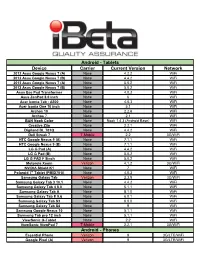
Device Carrier Current Version Network Android
Android - Tablets Device Carrier Current Version Network 2012 Asus Google Nexus 7 (A) None 4.2.2 WiFi 2012 Asus Google Nexus 7 (B) None 4.4.2 WiFi 2013 Asus Google Nexus 7 (A) None 5.0.2 WiFi 2013 Asus Google Nexus 7 (B) None 5.0.2 WiFi Asus Eee Pad Transformer None 4.0.3 WiFi Asus ZenPad 8.0 inch None 6 WiFi Acer Iconia Tab - A500 None 4.0.3 WiFi Acer Iconia One 10 inch None 5.1 WiFi Archos 10 None 2.2.6 WiFi Archos 7 None 2.1 WiFi B&N Nook Color None Nook 1.4.3 (Android Base) WiFi Creative Ziio None 2.2.1 WiFi Digiland DL 701Q None 4.4.2 WiFi Dell Streak 7 T-Mobile 2.2 3G/WiFi HTC Google Nexus 9 (A) None 7.1.1 WiFi HTC Google Nexus 9 (B) None 7.1.1 WiFi LG G Pad (A) None 4.4.2 WiFi LG G Pad (B) None 5.0.2 WiFi LG G PAD F 8inch None 5.0.2 WiFi Motorola Xoom Verizon 4.1.2 3G/WiFi NVIDIA Shield K1 None 7 WiFi Polaroid 7" Tablet (PMID701i) None 4.0.3 WiFi Samsung Galaxy Tab Verizon 2.3.5 3G/WiFi Samsung Galaxy Tab 3 10.1 None 4.4.2 WiFi Samsung Galaxy Tab 4 8.0 None 5.1.1 WiFi Samsung Galaxy Tab A None 8.1.0 WiFi Samsung Galaxy Tab E 9.6 None 6.0.1 WiFi Samsung Galaxy Tab S3 None 8.0.0 WiFi Samsung Galaxy Tab S4 None 9 WiFi Samsung Google Nexus 10 None 5.1.1 WiFi Samsung Tab pro 12 inch None 5.1.1 WiFi ViewSonic G-Tablet None 2.2 WiFi ViewSonic ViewPad 7 T-Mobile 2.2.1 3G/WiFi Android - Phones Essential Phone Verizon 9 3G/LTE/WiFi Google Pixel (A) Verizon 9 3G/LTE/WiFi Android - Phones (continued) Google Pixel (B) Verizon 8.1 3G/LTE/WiFi Google Pixel 2 Verizon 8.1 3G/LTE/WiFi Google Pixel 3 XL None 9 3G/LTE/WiFi HTC Desire (International) -

Acer Airis Alcatel Alltel Amoi Amoisonic Anextek Apple Arima
Acer 1 n10 1 1 n311 1 1 S100 Liquid 1 1 X960 1 Airis 1 T480 1 Alcatel 1 ELLE No 1 1 1 ELLE No 3 1 1 One Touch 355 1 1 One Touch 556 1 1 One Touch 557 1 1 One Touch 565 1 1 One Touch 708 1 1 One Touch 735i 1 1 One Touch 756 1 1 One Touch 757 1 1 One Touch 800 1 1 One Touch C551 1 1 One Touch C552 1 1 One Touch C635 1 1 One Touch C651 1 1 One Touch C652 1 1 One Touch C750 1 1 One Touch S853 1 1 One Touch V670 1 Alltel 1 PPC-6800 1 Amoi 1 A310 1 1 D85 1 1 D89 1 1 E72 1 1 F8 1 1 F90 1 1 H9 1 1 M636 1 1 N810 1 1 WP-S1 Skypephone 1 Amoisonic 1 9201 1 AnexTek 1 SP230 1 Apple 1 iPad 1 1 iPhone 1 1 iPod Touch 1 Arima 1 2850 1 Asus 1 1210 1 1 Galaxy II 1 1 Galaxy Mini 1 1 J100 1 1 J101 1 1 J102 1 1 M303 1 1 M530w 1 1 M930 1 1 P320 1 1 P505 1 1 P525 1 1 P526 1 1 P527 1 1 P550 1 1 P552 1 1 P735 1 1 P750 1 1 V80 1 AT&T 1 8900 Tilt 1 1 8925 Tilt 1 Audiovox 1 CDM-8450 1 1 CDM-8450SP 1 1 CDM-8455 1 1 CDM-8615 1 1 CDM-8900 1 1 CDM-8910 1 1 CDM-8912 1 1 CDM-8915 1 1 CDM-8920 1 1 CDM-8930 1 1 PM-8912 1 1 PM-8920 1 1 PPC-6600 / PPC-6601 1 1 PPC-6700 1 1 SMT-5600 1 1 VI600 1 BenQ 1 A500 1 1 A5001 1 1 A520 1 1 CL71 1 1 E72 1 1 E81 1 1 M315 1 1 M350 1 1 M580A 1 1 Morpheus 1 1 P30 1 1 P50 1 1 S660C 1 1 S668C 1 1 S670C 1 1 S680C 1 1 S700 1 1 S7001 1 1 S82 1 1 S830C 1 1 U700 1 1 Z2 1 BenQ-Siemens 1 C81 1 1 C81F 1 1 E71 1 1 EF51 1 1 EF81 1 1 EF91 1 1 EL71 1 1 M81 1 1 P51 1 1 S68 1 1 S80 1 1 S81 1 Bird 1 D660 1 1 E810 1 1 S689 1 1 SC01 1 1 SC24 1 1 V007 1 BlackBerry 1 7100g 1 1 7100i 1 1 7100r 1 1 7100t 1 1 7100v 1 1 7100x 1 1 7105t 1 1 7130c 1 1 7130e 1 1 7130g -
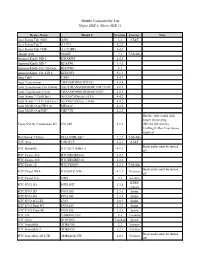
Shuttle Compatibility List Major SDK 5, Minor SDK 13
Shuttle Compatibility List Major SDK 5, Minor SDK 13 Device Name Model # Version Carrier Note Acer Iconia Tab A501 A501 3.2 AT&T Acer Iconia Tab 7 A1-713 4.2.2 Acer Iconia Tab 7 HD A1-713HD 4.4.2 Alcatel A30 9024W 7.1 T-Mobile Amazon Kindle HD 6 KWARWI 4.4.3 Amazon Kindle HD 7 KFASWI 4.4.3 Amazon Kindle Fire 5th Gen. KFFOWI 5.1 Amazon Kindle Fire HD 8 KFDOWI 5.1.1 Alps Tab9 TAB9 4.4.2 Asus Transformer TRANSFORMERTF101 4.0.4 Asus Transformer Pad Infinity ASUSTRANSFORMERPADTF700T 4.0.3 Asus Transformer Prime TRANSFORMERPRIMETF201 4.0.3 Asus Nexus 7 (2nd Gen.) NEXUS7 (Device: FLO) 4.4.2 Asus Nexus 7 LTE (2nd Gen.) NEXUS7 (Device: DEB) 4.4.2 Asus MeMO Pad FHD 10 ME302C 4.2.2 Asus MeMO Pad HD7 ME173X 4.2.2 Shuttle: only works with longer phone plug: Casio G'zOne Commando 4G C8114G 4.1.2 (ID-80110010-028) UniMag II: Rev G or above required Dell Streak 7 Tablet DELLSTREAK7 2.2.2 T-Mobile HTC Aria LIBERTY 2.2.1 AT&T Beats audio must be turned HTC Butterfly HTCBUTTERFLY 4.1.1 off HTC Desire 816 HTCDESIRE816 4.4.2 HTC Desire 310 HTCDESIRE310 4.2.2 HTC Desire Z HTCVISION 2.2.1 T-Mobile Beats audio must be turned HTC Droid DNA HTC6435LVW 4.1.1 Verizon off HTC Droid Eris ERIS 2.1 Verizon KDDI HTC EVO 3D ISW12HT 2.3.4 (Japan) HTC EVO 3D PG86100 2.3.3 Sprint HTC EVO 4G PC36100 2.3.3 Sprint HTC EVO 4G LTE EVO 4.0.3 Sprint HTC EVO Shift 4G PG06100 2.3.3 Sprint HTC EVO View 4G PG41200 2.3.3 Sprint HTC G2 T-MOBILEG2 2.2 T-mobile HTC Hero HERO200 2.1-update1 Sprint HTC Incredible ADR6300 2.2 Verizon HTC Incredible 2 ADR6350 2.2.1 Verizon Beats audio must -

AT&T Unwrapped
AT&T Unwrapped 2012 Holiday Gi Guide Look Book Contents Glossary of Terms . .Page 2 Smartphones. .Page 3-12 Nokia Lumia 920 Nokia Lumia 820 HTC One X+ Windows Phone 8X by HTC Samsung Galaxy Note II Samsung Rugby Pro Samsung Galaxy Express Sony Xperia TL LG Optimus G Emerging Devices. .Page 13-18 AT&T Mobile Hotspot MiFi Liberate Samsung Galaxy Camera Samsung Galaxy Tab 2 10.1 Samsung ATIV Smart PC Asus VivoTab RT Accessories. .Page 19-23 Plantronics Voyager Legend ZAGG Sparq3100 HMDX Jam Wireless Speaker Touchscreen Gloves iFrogz Boost Plus ZAGGfolio iSound Powerstation Moshi Screen Protectors Contact Info . Page 24 1 Glossary Of Terms 4G LTE (Long Term Evolution): The newest standard for wireless data communications. AT&T’s 4G LTE service delivered faster average download speeds than any of its competitors in PCWorld’s most recent speed tests. Android 4.1 (Jelly Bean): Google’s fastest, smoothest and most recent version of the Android operating system for smartphones and tablets yet. Jelly Bean introduces a new Google search experience on Android, an updated camera experience and an improved “Face Unlock” feature to unlock your device using facial recognition soware. Android 4.0 (Ice Cream Sandwich): The second most recent version of the Android platform for phones, tablets, and more. It built on the things people love most about Android and adds easier multitasking, folders to the home screen, resizable widgets and new swipe options for notications. The majority of Android devices on the market currently run Ice Cream Sandwich. Windows 8: Microso’s newest operating system for smartphones, laptops, tablets and more. -

Mobility Application Strategy Education Dwayne Stafford, AT&T Mobility Mobility Account Manager-Applications
Mobility Application Strategy Education Dwayne Stafford, AT&T Mobility Mobility Account Manager-Applications © 2012 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T Intellectual Property and/or AT&T affiliated companies. All other marks contained herein are the property of their respective owners. Evolving Trend in Education • Education paradigms are shifting to include online learning, hybrid learning, challenge-based activity learning, and collaborative models – Budget cuts have forced schools to find alternatives to the exclusive face-to-face learning model – Abundance of free or low cost high quality education contents which Institutions must consider the unique value they add – The work is increasingly collaborative, driving changes in the way student projects are structured – Learning model that is more student-centered, allowing them to take control of how they engage with a subject and to brainstorm and implement solutions. • People expect to be able to work, learn, and study whenever and wherever they want • The technologies we use are increasingly cloud-based, and our notions of IT support are decentralized • As the cost of technology drops and school districts revise and open up their access policies, it is becoming increasingly common for students to bring their own mobile devices 2 © 2012 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T Intellectual Property and/or AT&T affiliated Source: NMC Horizon Report http://www.nmc.org/pdf/2012-horizon-report-HE.pdf, companies. -

Get Powerful Push-To-Talk. See Why So Many Ontario Businesses Choose Bell
Get powerful Push-to-talk. See why so many Ontario businesses choose Bell. Push-to-talk (PTT) from Bell uses the same one-touch technology used by some of the A great line-up of 1 largest U.S. carriers - the industry’s clear choice in PTT technology. PTT devices. Access our next generation services. • Connect with up to 249 people instantly Rugged. Waterproof. • Connect with one or many at the touch of a button with group calling Shock and dust • Call with PTT while you email, text or browse simultaneously resistant.5 • Update contacts and groups in real time on all PTT devices • Supervisory override in group calls Kyocera DuraForce Exclusive to Bell Coverage you can trust. Speed that gets the job done. • Access Canada’s largest LTE network, covering over 28 million Canadians from coast to coast2 • Extensive roaming coverage in the U.S., covering 90% of the U.S. population Ultra-rugged device. • Enhanced coverage with secure PTT over Wi-Fi3 Incredible performance. • Transfer documents and send emails with fast speeds while on the go Sonim XP7 Complete suite of devices, accessories and solutions. • A full range of compatible devices - from the world’s toughest phones to powerful superphones • Accessories tailored to suit any work environment • Combine PTT with robust workforce, asset and fl eet management solutions Dust proof and water resistant.5 See how Bell’s powerful Push-to-talk service compares. Samsung Rugby™ IV Bell The Other Guy Fewest dropped calls in the Greater Toronto area4 1.5x fewer û Powered by a trusted PTT solution used by leading US carriers ü û Largest selection of rugged devices Create.