Paper 3262-2015
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -

The Gnu Binary Utilities
The gnu Binary Utilities Version cygnus-2.7.1-96q4 May 1993 Roland H. Pesch Jeffrey M. Osier Cygnus Support Cygnus Support TEXinfo 2.122 (Cygnus+WRS) Copyright c 1991, 92, 93, 94, 95, 1996 Free Software Foundation, Inc. Permission is granted to make and distribute verbatim copies of this manual provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modi®ed versions of this manual under the conditions for verbatim copying, provided also that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this manual into another language, under the above conditions for modi®ed versions. The GNU Binary Utilities Introduction ..................................... 467 1ar.............................................. 469 1.1 Controlling ar on the command line ................... 470 1.2 Controlling ar with a script ............................ 472 2ld.............................................. 477 3nm............................................ 479 4 objcopy ....................................... 483 5 objdump ...................................... 489 6 ranlib ......................................... 493 7 size............................................ 495 8 strings ........................................ 497 9 strip........................................... 499 Utilities 10 c++®lt ........................................ 501 11 nlmconv .................................... -
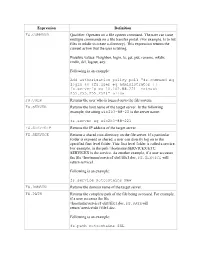
Expression Definition FS.COMMAND Qualifier. Operates on a File System Command
Expression Definition FS.COMMAND Qualifier. Operates on a file system command. The user can issue multiple commands on a file transfer portal. (For example, ls to list files or mkdir to create a directory). This expression returns the current action that the user is taking. Possible values: Neighbor, login, ls, get, put, rename, mkdir, rmdir, del, logout, any. Following is an example: Add authorization policy pol1 “fs.command eq login && (fs.user eq administrator || fs.serverip eq 10.102.88.221 –netmask 255.255.255.252)” allow FS.USER Returns the user who is logged on to the file system. FS.SERVER Returns the host name of the target server. In the following example, the string win2k3-88-22 is the server name: fs.server eq win2k3-88-221 FS.SERVERIP Returns the IP address of the target server. FS.SERVICE Returns a shared root directory on the file server. If a particular folder is exposed as shared, a user can directly log on to the specified first level folder. This first level folder is called a service. For example, in the path \\hostname\SERVICEX\ETC, SERVICEX is the service. As another example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.SERVICE will return service1. Following is an example: fs.service notcontains New FS.DOMAIN Returns the domain name of the target server. FS.PATH Returns the complete path of the file being accessed. For example, if a user accesses the file \\hostname\service1\dir1\file1.doc, FS.PATHwill return \service\dir1\file1.doc. Following is an example: fs.path notcontains SSL Expression Definition FS.FILE Returns the name of the file being accessed. -

Also Includes Slides and Contents From
The Compilation Toolchain Cross-Compilation for Embedded Systems Prof. Andrea Marongiu ([email protected]) Toolchain The toolchain is a set of development tools used in association with source code or binaries generated from the source code • Enables development in a programming language (e.g., C/C++) • It is used for a lot of operations such as a) Compilation b) Preparing Libraries Most common toolchain is the c) Reading a binary file (or part of it) GNU toolchain which is part of d) Debugging the GNU project • Normally it contains a) Compiler : Generate object files from source code files b) Linker: Link object files together to build a binary file c) Library Archiver: To group a set of object files into a library file d) Debugger: To debug the binary file while running e) And other tools The GNU Toolchain GNU (GNU’s Not Unix) The GNU toolchain has played a vital role in the development of the Linux kernel, BSD, and software for embedded systems. The GNU project produced a set of programming tools. Parts of the toolchain we will use are: -gcc: (GNU Compiler Collection): suite of compilers for many programming languages -binutils: Suite of tools including linker (ld), assembler (gas) -gdb: Code debugging tool -libc: Subset of standard C library (assuming a C compiler). -bash: free Unix shell (Bourne-again shell). Default shell on GNU/Linux systems and Mac OSX. Also ported to Microsoft Windows. -make: automation tool for compilation and build Program development tools The process of converting source code to an executable binary image requires several steps, each with its own tool. -

Riscv-Software-Stack-Tutorial-Hpca2015
Software Tools Bootcamp RISC-V ISA Tutorial — HPCA-21 08 February 2015 Albert Ou UC Berkeley [email protected] Preliminaries To follow along, download these slides at http://riscv.org/tutorial-hpca2015.html 2 Preliminaries . Shell commands are prefixed by a “$” prompt. Due to time constraints, we will not be building everything from source in real-time. - Binaries have been prepared for you in the VM image. - Detailed build steps are documented here for completeness but are not necessary if using the VM. Interactive portions of this tutorial are denoted with: $ echo 'Hello world' . Also as a reminder, these slides are marked with an icon in the upper-right corner: 3 Software Stack . Many possible combinations (and growing) . But here we will focus on the most common workflows for RISC-V software development 4 Agenda 1. riscv-tools infrastructure 2. First Steps 3. Spike + Proxy Kernel 4. QEMU + Linux 5. Advanced Cross-Compiling 6. Yocto/OpenEmbedded 5 riscv-tools — Overview “Meta-repository” with Git submodules for every stable component of the RISC-V software toolchain Submodule Contents riscv-fesvr RISC-V Frontend Server riscv-isa-sim Functional ISA simulator (“Spike”) riscv-qemu Higher-performance ISA simulator riscv-gnu-toolchain binutils, gcc, newlib, glibc, Linux UAPI headers riscv-llvm LLVM, riscv-clang submodule riscv-pk RISC-V Proxy Kernel (riscv-linux) Linux/RISC-V kernel port riscv-tests ISA assembly tests, benchmark suite All listed submodules are hosted under the riscv GitHub organization: https://github.com/riscv 6 riscv-tools — Installation . Build riscv-gnu-toolchain (riscv*-*-elf / newlib target), riscv-fesvr, riscv-isa-sim, and riscv-pk: (pre-installed in VM) $ git clone https://github.com/riscv/riscv-tools $ cd riscv-tools $ git submodule update --init --recursive $ export RISCV=<installation path> $ export PATH=${PATH}:${RISCV}/bin $ ./build.sh . -

The Frege Programming Language ( Draft)
The Frege Programming Language (Draft) by Ingo Wechsung last changed May 14, 2014 3.21.285 Abstract This document describes the functional programming language Frege and its implemen- tation for the Java virtual machine. Commonplace features of Frege are type inference, lazy evaluation, modularization and separate compile-ability, algebraic data types and type classes, pattern matching and list comprehension. Distinctive features are, first, that the type system supports higher ranked polymorphic types, and, second, that Frege code is compiled to Java. This allows for maximal interoperability with existing Java software. Any Java class may be used as an abstract data type, Java functions and methods may be called from Frege functions and vice versa. Despite this interoperability feature Frege is a pure functional language as long as impure Java functions are declared accordingly. What is or who was Frege? Friedrich Ludwig Gottlob Frege was a German mathematician, who, in the second half of the 19th century tried to establish the foundation of mathematics in pure logic. Al- though this attempt failed in the very moment when he was about to publish his book Grundgesetze der Arithmetik, he is nevertheless recognized as the father of modern logic among philosophers and mathematicians. In his essay Funktion und Begriff [1] Frege introduces a function that takes another function as argument and remarks: Eine solche Funktion ist offenbar grundverschieden von den bisher betrachteten; denn als ihr Argument kann nur eine Funktion auftreten. Wie nun Funktionen von Gegenst¨andengrundverschieden sind, so sind auch Funktionen, deren Argu- mente Funktionen sind und sein m¨ussen,grundverschieden von Funktionen, deren Argumente Gegenst¨andesind und nichts anderes sein k¨onnen. -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

Data Transformation Language (DTL)
DTL Data Transformation Language Phillip H. Sherrod Copyright © 2005-2006 All rights reserved www.dtreg.com DTL is a full programming language built into the DTREG program. DTL makes it easy to generate new variables, transform and combine input variables and select records to be used in the analysis. Contents Contents...................................................................................................................................................3 Introduction .............................................................................................................................................6 Introduction to the DTL Language......................................................................................................6 Using DTL For Data Transformations ....................................................................................................7 The main() function.............................................................................................................................7 Global Variables..................................................................................................................................8 Implicit Global Variables ................................................................................................................8 Explicit Global Variables ................................................................................................................9 Static Global Variables..................................................................................................................11 -

File Management Tools
File Management Tools ● gzip and gunzip ● tar ● find ● df and du ● od ● nm and strip ● sftp and scp Gzip and Gunzip ● The gzip utility compresses a specified list of files. After compressing each specified file, it renames it to have a “.gz” extension. ● General form. gzip [filename]* ● The gunzip utility uncompresses a specified list of files that had been previously compressed with gzip. ● General form. gunzip [filename]* Tar (38.2) ● Tar is a utility for creating and extracting archives. It was originally setup for archives on tape, but it now is mostly used for archives on disk. It is very useful for sending a set of files to someone over the network. Tar is also useful for making backups. ● General form. tar options filenames Commonly Used Tar Options c # insert files into a tar file f # use the name of the tar file that is specified v # output the name of each file as it is inserted into or # extracted from a tar file x # extract the files from a tar file Creating an Archive with Tar ● Below is the typical tar command used to create an archive from a set of files. Note that each specified filename can also be a directory. Tar will insert all files in that directory and any subdirectories. tar cvf tarfilename filenames ● Examples: tar cvf proj.tar proj # insert proj directory # files into proj.tar tar cvf code.tar *.c *.h # insert *.c and *.h files # into code.tar Extracting Files from a Tar Archive ● Below is the typical tar command used to extract the files from a tar archive. -

Learning Objectives ECHO Commands. Command. 10. Explain
. SA Learning Objectives After completing this chapter you will be able to: 1. List commands used in batch files. 2. List and explain batch file rules. 3. Use a batch file with a shortcut. 3. Explore the function of the REM, 4. Use the SHIFT command to move param- ECHO commands. eters. 4. Explain the use of batch files with shortcuts. 5. Use the IF command with strings for condi- 5. Explain the purpose and function of the tional processing. GOTO command. 6. Test for null values in a batch file. 6. Explain the purpose and function of the 7. Use the IF EXIST /IF SHIFT command. test for the existence of a file or a 7. Explain the purpose and function of the IF subdirectory. command. 8. Use the SET command. 8. Explain the purpose and function of the IF 9. Use the environment and environmental EXIST /IF variables in batch files. 9. Explain the purpose and function of the IF 10. Use the IF ERRORLEVEL command ERRORLEVEL command. XCOpy to write a batch file for testing exit 10. Explain the purpose and function of writing codes. programs. 11. Use the FOR...IN...OO command for repeti- 11. Explain the purpose and function of the tive processing. environment and environmental variables. 12. Use the CALL command in a batch file. 12. Explain the use of the SET command. 13. Explain the purpose and function of the Chapter Overview FOR...IN...OO command. You learned in Chapter 10 how to write simple 14. Explain the purpose and function of the batch files and use replaceable parameters. -

Reference Manual for the Icon Programming Language Version 5 (( Implementation for Limx)*
Reference Manual for the Icon Programming Language Version 5 (( Implementation for liMX)* Can A. Contain. Ralph £ Grixwoltl, and Stephen B. Watnplcr "RSI-4a December 1981, Corrected July 1982 Department of Computer Science The University of Arizona Tucson, Arizona 85721 This work was supported by the National Science Foundation under Grant MCS79-03890. Copyright © 1981 by Ralph E. Griswold All rights reserved. No part of this work may be reproduced, transmitted, or stored in any form or by any means without the prior written consent of the copyright owner. CONTENTS Chapter i Introduction 1.1 Background I 1.2 Scope ol the Manual 2 1.3 An Overview of Icon 2 1.4 Syntax Notation 2 1.5 Organization ol the Manual 3 Chapter 2 Basic Concepts and Operations 2.1 Types 4 2.2 Expressions 4 2.2.1 Variables and Assignment 4 2.2.2 Keywords 5 2.2.3 Functions 5 2.2.4 Operators 6 2.3 Evaluation of Expressions 6 2.3.1 Results 6 2.3.2 Success and Failure 7 2.4 Basic Control Structures 7 2.5 Compound Expressions 9 2.6 Loop Control 9 2.7 Procedures 9 Chapter 3 Generators and Expression Evaluation 3.1 Generators 11 3.2 Goal-Directed Evaluation 12 }.?> Evaluation of Expres.sions 13 3.4 I he Extent ol Backtracking 14 3.5 I he Reversal ol Effects 14 Chapter 4 Numbers and Arithmetic Operations 4.1 Integers 15 4.1.1 literal Integers 15 4.1.2 Integer Arithmetic 15 4.1.3 Integer Comparison 16 4.2 Real Numbers 17 4.2.1 literal Real Numbers 17 4.2.2 Real Arithmetic 17 4.2.3 Comparison of Real Numbers IS 4.3 Mixed-Mode Arithmetic IX 4.4 Arithmetic Type Conversion 19