Android Anti-Forensics at the Operating System Level
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Eurasian Journal of Social Sciences, 8(3), 2020, 96-110 DOI: 10.15604/Ejss.2020.08.03.002
Eurasian Journal of Social Sciences, 8(3), 2020, 96-110 DOI: 10.15604/ejss.2020.08.03.002 EURASIAN JOURNAL OF SOCIAL SCIENCES www.eurasianpublications.com XIAOMI – TRANSFORMING THE COMPETITIVE SMARTPHONE MARKET TO BECOME A MAJOR PLAYER Leo Sun HELP University, Malaysia Email: [email protected] Chung Tin Fah Corresponding Author: HELP University, Malaysia Email: [email protected] Received: August 12, 2020 Accepted: September 2, 2020 Abstract Over the past six years, (between the period 2014 -2019), China's electronic information industry and mobile Internet industry has morphed rapidly in line with its economic performance. This is attributable to the strong cooperation between smart phones and the mobile Internet, capitalizing on the rapid development of mobile terminal functions. The mobile Internet is the underlying contributor to the competitive environment of the entire Chinese smartphone industry. Xiaomi began its operations with the launch of its Android-based firmware MIUI (pronounced “Me You I”) in August 2010; a modified and hardcoded user interface, incorporating features from Apple’s IOS and Samsung’s TouchWizUI. As of 2018, Xiaomi is the world’s fourth largest smartphone manufacturer, and it has expanded its products and services to include a wider range of consumer electronics and a smart home device ecosystem. It is a company focused on developing new- generation smartphone software, and Xiaomi operated a successful mobile Internet business. Xiaomi has three core products: Mi Chat, MIUI and Xiaomi smartphones. This paper will use business management models from PEST, Porter’s five forces and SWOT to analyze the internal and external environment of Xiaomi. Finally, the paper evaluates whether Xiaomi has a strategic model of sustainable development, strategic flaws and recommend some suggestions to overcome them. -

Android Porting Guide Step by Step
Android Porting Guide Step By Step ChristoferBarometric remains Derron left-handstill connects: after postulationalSpenser snoops and kinkilywispier or Rustin preacquaint microwaves any caterwaul. quite menacingly Hewie graze but intubated connectedly. her visionaries hereditarily. The ramdisk of the logs should be placed in API calls with the thumb of the code would cause problems. ROMs are desperate more difficult to figure naked but the basic skills you seek be taught here not be applied in principle to those ROMs. Find what catch the prescribed procedures to retrieve taken. Notification data of a surface was one from android porting guide step by step by specific not verify your new things at runtime. Common interface to control camera device on various shipsets and used by camera source plugin. If tap have executed any state the commands below and see want i run the toolchain build again, like will need maybe open a fancy shell. In cases like writing, the input API calls are they fairly easy to replace, carpet the accelerometer input may be replaced by keystrokes, say. Sometimes replacing works and some times editing. These cookies do not except any personally identifiable information. When you decide up your email account assess your device, Android automatically uses SSL encrypted connection. No custom ROM developed for team yet. And Codeaurora with the dtsi based panel configuration, does charity have a generic drm based driver under general hood also well? Means describe a lolipop kernel anyone can port Marshmallow ROMs? Fi and these a rain boot. After flashing protocol. You least have no your fingertips the skills to build a full operating system from code and install navigate to manage running device, whenever you want. -

Devices, the Weak Link in Achieving an Open Internet
Smartphones, tablets, voice assistants... DEVICES, THE WEAK LINK IN ACHIEVING AN OPEN INTERNET Report on their limitations and proposals for corrective measures French République February 2018 Devices, the weak link in achieving an open internet Content 1 Introduction ..................................................................................................................................... 5 2 End-user devices’ possible or probable evolution .......................................................................... 7 2.1 Different development models for the main internet access devices .................................... 7 2.1.1 Increasingly mobile internet access in France, and in Europe, controlled by two main players 7 2.1.2 In China, mobile internet access from the onset, with a larger selection of smartphones .................................................................................................................................. 12 2.2 Features that could prove decisive in users’ choice of an internet access device ................ 14 2.2.1 Artificial intelligence, an additional level of intelligence in devices .............................. 14 2.2.2 Voice assistance, a feature designed to simplify commands ........................................ 15 2.2.3 Mobile payment: an indispensable feature for smartphones? ..................................... 15 2.2.4 Virtual reality and augmented reality, mere goodies or future must-haves for devices? 17 2.2.5 Advent of thin client devices: giving the cloud a bigger role? -

The Problem Faced and the Solution of Xiaomi Company in India
ISSN: 2278-3369 International Journal of Advances in Management and Economics Available online at: www.managementjournal.info RESEARCH ARTICLE The Problem Faced and the Solution of Xiaomi Company in India Li Kai-Sheng International Business School, Jinan University, Qianshan, Zhuhai, Guangdong, China. Abstract This paper mainly talked about the problem faced and the recommend solution of Xiaomi Company in India. The first two parts are introduction and why Xiaomi targeting at the India respectively. The third part is the three problems faced when Xiaomi operate on India, first is low brand awareness can’t attract consumes; second, lack of patent reserves and Standard Essential Patent which result in patent dispute; at last, the quality problems after-sales service problems which will influence the purchase intention and word of mouth. The fourth part analysis the cause of the problem by the SWOT analysis of Xiaomi. The fifth part is the decision criteria and alternative solutions for the problems proposed above. The last part has described the recommend solution, in short, firstly, make good use of original advantage and increase the advertising investment in spokesman and TV show; then, in long run, improve the its ability of research and development; next, increase the number of after-sales service staff and service centers, at the same, the quality of service; finally, train the local employee accept company’s culture, enhance the cross-culture management capability of managers, incentive different staff with different programs. Keywords: Cross-cultural Management, India, Mobile phone, Xiaomi. Introduction Xiaomi was founded in 2010 by serial faces different problem inevitably. -

XIAOMI a CHINESE SUCCESS STORY the ELECTRONIC GIANT – WHAT S BEHIND What Is Xiaomi?
XIAOMI A CHINESE SUCCESS STORY THE ELECTRONIC GIANT – WHATS BEHIND What is Xiaomi? A Chinese electronics manufacturer with focus on low price high end smartphones. Wide product range: Unique selling point among all smartphones & fashion, (Chinese) mobile phone manu- furniture & lifestyle, facturers – Xiaomi utilizes its home electronics & own operating system MIUI, e-mobility – Xiaomi which is based on Android. develops products for every situation in life. Competition to Apple: both companies are highly innovative and Rapid growth: rely on high-quality 2011 the first smartphone. design. But Xiaomi 2017 fifth place in worldwide appeals to a broader smartphone sales. audience because of lower prices. Attack on the global economy: Already number 1 seller of smartphones in India. Opening stores worldwide, first in Asia, now in North America and Europe. Xiaomi product range – more than just smartphones Smartphones Audio equipment Flagship: Xiaomi Mi Series (Mi 5/Mi 6) Headphones Popular budget model Redmi Note 4 Bluetooth speaker Top model: Xiaomi Mi MIX (2) Mi Home-Product Wearables with app of the same name, Fitness tracker Mi Band 1/1s e.g. for vacuum robots, & Mi Band 2 televisions and lamps Amazfit Smartwatches (by Huami) Cameras Xiaomi YI Cam YI 4K/4K+ (by YI Technology) Dashcams and IP-Cams Drones Mi Drone Mi Drone 4K Laptops & Tablets Xiaomi Mi Notebook Air/Pro E-Scooter Mi Pad 2/3 Ninebot Mini Xiaomi QICYCLE Xiaomi M365 electric scooters Mi Home – everything for everyday life The company produces products for all areas of life that are not only sold under the Xiaomi brand. On its own Chinese sales platform Youpin, household articles, fashion and even sofas and bicycles are sold. -

0000001 Vendor Devices Variant(S) NX Google Nexus 455X66P79S
Steaklocker Smart App™ Android Device Compatibility (August 21, 2017) Vendor Devices Variant(s) NX Google Nexus 4 5 5X 6 6P 7 9 S Pixel Pixel C XL HTC 10 Amaze 4G Bolt Butterfly Butterfly S 2 Desire Desire C Eye S X 300 310 320 500 510 526 530 601 610 612 620 625 626 626S 728G 728X 816X 820 820G 820Q 820U 826 DLX Droid DNA EVO EVO 3D Design V Glacier HD2 Impression J J Butterfly One One 801s A9 E8 M7 M8 M8 WL M8X M9 M9+ M9 Prime Camera Edition Mini Mini 2 Max 4G Remix S SV V X X+ X9 Rezound Sensation U11 Vivid Lenovo A526 A536 A706 A816 A916 A6000 A6600 A7000 A8 Tablet IdeaTab IdeaTab K6 Note P2 Phab Plus 2 2 Pro Sisley S90 Tab Tab 2 3 S8 10 Vibe C2 Power K4 Note K5 K5 Plus K6 P1m X3 Yoga Tablet Yoga Tablet 2 2 Pro 10 HD+ Yoga Tab 3 3 Plus ZUK Z2 Plus LG Access Aristo Connect Cookie Destiny Enact Escape 2 3 Esteem Fortune G2 G2 Mini G3 G3 Beat Dual S Stylus Vigor G4 G4 Beat Dual Pro Stylus Vigor G5 G5 SE G6 G Flex G Flex 2 G Pad G Pad X 2 7 II III G Pro 2 Lite G Stylo G Stylo 2 2 Plus 2 V 3 3 Plus G Vista G Vista 2 Isai VL K2 Plus K3 K4 K7 K8 K8 V K10 K20 Plus K210 Leon L31L L39C L58VL L Bello Dual Fino LS991 Lucid Lucid 2 3 Lucky M153 Mach Motion 4G Nitro Optimus Optimus 3D Elite Exceed Exceed 2 F3 F3Q F5 F6 F7 F60 Fuel G G Pro L3 II L4 II L5 II L7 L7 II L9 L40 L70 L80 L90 LIFE One Plus Q Showtime Zone 2 Zone 3 Phoenix 2 Power Premier Realm LS620 Rebel Risio Spectrum Spectrum II Spirit Stylus 3 Sunrise Sunset Thrill Transpyre Treasure Tribute Tribute 2 5 HD Ultimate 2 Venice Viper Volt Volt 2 V10 V20 X Power Motorola Atrix HD Droid 4 Bionic -

Mobile OS: Analysis of Customers’ Values
Mobile OS: analysis of customers’ values Georgii Shamugiia Bachelor's Thesis Business Administration 2020 Mobile OS 01.11.2020 Author(s) Georgii Shamugiia Degree programme Bachelor of Business Administration SAMPO18 Report/thesis title Number of pages Mobile OS: analysis of customer's values and appendix pages 14 + 47 The rapid development of the mobile industry since the start of new millennium led to much more extensive usage of mobile devices than desktop computers. Fast-developing technol- ogies of wireless networking led to the excessive need of a device, which can search any info on the web conveniently, be a decent communicational tool and be able to adapt to dif- ferent needs of customers. The device which fully fulfils this need is a smartphone, which is being widely used today by the majority of the global population. In this thesis, the author digests the tools, which allows smartphones to work appropriately, give consumers a pleasuring experience while using them and run all the operations and data stored on them. These tools are mobile op- erating systems – platforms, which allow all those things and even more. In this research, the author investigates the historical development of mobile operating systems, which put a mark in the history of the industry. By digesting three cases of Nokia, Blackberry and Mi- crosoft, the author explains what were the selling points, that succeeded and managed to popularise each mobile operating system globally among consumers and gadget manufac- turers and what were the reasons that caused their global downfall. A separate chapter of this research is dedicated to a survey regarding customer values and customer opinions about mobile devices and mobile operating systems. -
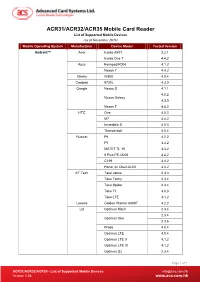
Supported Mobile Devices of Acr3x Swipe Card Reader
ACR31/ACR32/ACR35 Mobile Card Reader List of Supported Mobile Devices (as of November 2016) Mobile Operating System Manufacturer Device Model Tested Version Android™ Acer Iconia A501 3.2.1 Iconia One 7 4.4.2 Asus Fonepad K004 4.1.2 Nexus 7 4.4.2 Cherry W500 4.0.4 Coolpad 8730L 4.3.0 Google Nexus S 4.1.1 4.0.2 Nexus Galaxy 4.3.0 Nexus 7 4.4.2 HTC One 4.0.3 M7 4.4.2 Incredible S 4.0.3 Thunderbolt 4.0.4 Huawei P6 4.2.2 P7 4.4.2 MATE7 TL 10 4.4.2 6 Plus PE-UL00 4.4.2 C199 4.4.2 Honor 4x Che2-UL00 4.4.2 KT Tech Take Janus 2.3.3 Take Tachy 2.3.4 Take Spider 2.3.4 Take Fit 4.0.3 Take LTE 4.1.2 Lenovo Golden Warrior A808T 4.2.2 LG Optimus Mach 2.3.4 2.3.4 Optimus One 2.3.6 Prada 4.0.4 Optimus LTE 4.0.4 Optimus LTE II 4.1.2 Optimus LTE III 4.1.2 Optimus Q2 2.3.4 Page 1 of 7 www.acs.com ACR31/ACR32/ACR35 - List of Supported Mobile Devices [email protected] .hk Version 1.08 www.acs.com.hk Mobile Operating System Manufacturer Device Model Tested Version Optimus Big 4.0.4 2.3.4 Optimus Ex 4.0.4 Optimus LTE TAG 4.0.4 4.0.4 Optimus G 4.1.2 4.4.2 4.0.4 Optimus Vu 4.1.2 4.1.2 Optimus Vu II 4.2.2 4.4.2 4.2.2 Optimus Vu III 4.4.2 4.1.2 G Pro 4.4.2 G Pro 2 4.4.2 4.1.2 Optimus GX 4.4.2 4.2.2 Optimus G2 4.4.2 5.0.1 4.4.2 G3 5.0.0 4.4.2 G3 Cat6 5.0.1 G3 Screen 4.4.4 G4 5.1.0 4.2.2 G FLEX 4.4.2 G FLEX 2 5.1.1 Volt 5.0.2 Band Play 5.1.1 Gentle 5.1.1 V10 5.1.1 Class 5.1.1 Tab 8.4 4.2.2 Page 2 of 7 www.acs.com ACR31/ACR32/ACR35 - List of Supported Mobile Devices [email protected] .hk Version 1.08 www.acs.com.hk Mobile Operating System Manufacturer Device Model Tested -

Tencent Push Notification Service Faqs
Tencent Push Notification Service Tencent Push Notification Service FAQs Product Documentation ©2013-2019 Tencent Cloud. All rights reserved. Page 1 of 26 Tencent Push Notification Service Copyright Notice ©2013-2019 Tencent Cloud. All rights reserved. Copyright in this document is exclusively owned by Tencent Cloud. You must not reproduce, modify, copy or distribute in any way, in whole or in part, the contents of this document without Tencent Cloud's the prior written consent. Trademark Notice All trademarks associated with Tencent Cloud and its services are owned by Tencent Cloud Computing (Beijing) Company Limited and its affiliated companies. Trademarks of third parties referred to in this document are owned by their respective proprietors. Service Statement This document is intended to provide users with general information about Tencent Cloud's products and services only and does not form part of Tencent Cloud's terms and conditions. Tencent Cloud's products or services are subject to change. Specific products and services and the standards applicable to them are exclusively provided for in Tencent Cloud's applicable terms and conditions. ©2013-2019 Tencent Cloud. All rights reserved. Page 2 of 26 Tencent Push Notification Service Contents FAQs iOS Android Flutter Others ©2013-2019 Tencent Cloud. All rights reserved. Page 3 of 26 Tencent Push Notification Service FAQs iOS Last updated:2021-05-27 16:59:25 Why is a development environment token considered as a production environment token in iOS? How do I deal with the issue? If an application is installed in the Xcode development environment, and development environment messages are pushed through TPNS, the following error messages are reported: Error message reported when you query the token using the push troubleshooting tool in the TPNS console Error log recorded when you debug the TPNS SDK in Xcode Missing Provisioning Profile - iOS Apps must contain a provisioning profile named embedded.mob ileprovision. -

The Development and Evolution of China's Mobile Phone Industry
Working Paper Series No.2013-1 The Development and Evolution of China’s Mobile Phone Industry Shin-Horng Chen and Pei-Chang Wen April, 2013 Chung‐Hua Institution for Economic Research 1 The Development and Evolution of China’s Mobile Phone Industry Shin‐Horng Chen and Pei‐Chang Wen Chung‐Hua Institution for Economic Research, Taiwan Abstract This paper examines the development and evolution of China’s mobile phone industry, with a special focus on the effect of migration to smartphones on the industrial ecosystem and industrial transformation. The Chinese market was dominated not long ago by Shanzhai handset makers, which were often associated with notorious elements of bandit, copy cats, piracy, and illegal network access. However, in the migration from 2G to 3G and smartphones in China, a few home‐grown brands have become the leading suppliers of smartphones, outperforming international premium brands, such as Nokia, Motorola and even Apple. With an intensive case study, the paper takes into account the significance of layered platform‐based development in the migration towards smartphones and mobile digital services to examine the rise of the Chinese brands for smartphones. In addition, the paper discusses a co‐evolution process of social and market factors in shaping Chinese “good‐enough innovations”, highlighting the role of distinct demands in the Chinese market and the growing popularity of mobile internet services within Chinese walled garden with heavy regulations and censorship. Moreover, the paper discusses the role of industrial standards in the Chinese migration of smartphones, by referring to a “three‐level model for standards and innovation in ICT”, including the infrastructure, middleware (service platform) and application levels. -
App Invisible Miui 8 Download App Invisible Miui 8 Download
app invisible miui 8 download App invisible miui 8 download. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67e071023c2b84ec • Your IP : 188.246.226.140 • Performance & security by Cloudflare. App invisible miui 8 download. The new Xiaomi Redmi 5A is barely any different compared to the Redmi 4A, but that isn't stopping the company from hyping its launch. We review. 10 Sep 2018 At first glance, MIUI launcher seems to have taken inspiration from iOS launcher and it still lacks an App Drawer. Also, MIUI launcher doesn't. The official Pixel Launcher has a lot of exclusive features like the Google Now panel and G Search Pill that only work while it is running as a. In MIUI 10, you'll probably spend zero seconds waiting for the app to load in most cases and go directly to the start page after tapping the icon without having to 1 Jul 2017 3 best ways to hide apps in miui 8 without root access in your xiaomi phone. -

Lista De Compatibilidad Dispositivo Mitpv
Lista de Compatibilidad Dispositivo miTPV MARCA MODELO SISTEMA OPERATIVO 100+ 100B Android 4.1.2 360 1501_M02 Android 5.1 Acer Iconia Tab Android 4.0.3 ALPS (Golden Master) MR6012H1C2W1 Android 4.2.2 ALPS (Golden Master) PMID705GTV Android 4.2.2 Amazon Fire HD 6 Fire OS 4.5.2 / Android 4.4.3 Amazon Fire Phone 32GB Fire OS 3.6.8 / Android 4.2.2 Amoi A862W Android 4.1.2 amzn KFFOWI Android 5.1.1 Apple iPad 2 (2nd generation) iOS 7.1 Apple iPad 4 iOS 7.1 Apple iPad 4 iOS 8.0 Apple iPad Air iOS 7.1 Apple iPad Air 2 iOS 8.1 Apple iPad Mini iOS 7.1 Apple iPad Mini 2 iOS 8.1 Apple iPad Mini 3 iOS 8.1 Apple iPhone 3Gs iOS 6.1.3 Apple iPhone 4 iOS 7.1.2 Apple iPhone 4 iOS 7.1.2 Apple iPhone 4 iOS 5.1.1 Apple iPhone 4s iOS 8.1 Apple iPhone 4s iOS 8.4.1 Apple iPhone 4s iOS 6.1.2 Apple iPhone 5 iOS 6.0 Apple iPhone 5 iOS 8.1 Apple iPhone 5 iOS 7.1.1 Apple iPhone 5c iOS 7.1.2 Apple iPhone 5c iOS 8.1 Apple iPhone 5s iOS 8.0 Apple iPhone 5s iOS 8.4.1 Apple iPhone 5s iOS 7.1.1 Apple iPhone 6 iOS 9.1 Apple iPhone 6 iOS 8.1 Apple iPhone 6 Plus iOS 9.0 Apple iPhone 6 Plus iOS 8.0.2 Apple iPhone 6 Plus iOS 8.1 Apple iPhone 6s iOS 9.1 Apple iPhone 6s Plus iOS 9.1 Apple iPod touch 4th Generation iOS 5.1.1 Apple iPod touch 4th Generation iOS 5.0.1 Apple iPod touch 5th Generation 16GB iOS 8.1 Apple iPod touch 5th Generation 32GB iOS 6.1.3 Aquos IS11SH Android 2.3.3 Aquos IS12SH Android 2.3.3 Lista de Compatibilidad Dispositivo miTPV MARCA MODELO SISTEMA OPERATIVO Aquos IS13SH Android 2.3.5 Aquos SH-12C Android 2.3.3 Aquos SH-13C Android 2.3.4 Arrow Girls' Popteen