Yiying Zhang Before We Start
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Effective Virtual CPU Configuration with QEMU and Libvirt
Effective Virtual CPU Configuration with QEMU and libvirt Kashyap Chamarthy <[email protected]> Open Source Summit Edinburgh, 2018 1 / 38 Timeline of recent CPU flaws, 2018 (a) Jan 03 • Spectre v1: Bounds Check Bypass Jan 03 • Spectre v2: Branch Target Injection Jan 03 • Meltdown: Rogue Data Cache Load May 21 • Spectre-NG: Speculative Store Bypass Jun 21 • TLBleed: Side-channel attack over shared TLBs 2 / 38 Timeline of recent CPU flaws, 2018 (b) Jun 29 • NetSpectre: Side-channel attack over local network Jul 10 • Spectre-NG: Bounds Check Bypass Store Aug 14 • L1TF: "L1 Terminal Fault" ... • ? 3 / 38 Related talks in the ‘References’ section Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications What this talk is not about 4 / 38 Related talks in the ‘References’ section What this talk is not about Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications 4 / 38 What this talk is not about Out of scope: Internals of various side-channel attacks How to exploit Meltdown & Spectre variants Details of performance implications Related talks in the ‘References’ section 4 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) libvirtd QMP QMP QEMU QEMU VM1 VM2 Custom Disk1 Disk2 Appliance ioctl() KVM-based virtualization components Linux with KVM 5 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) libvirtd QMP QMP Custom Appliance KVM-based virtualization components QEMU QEMU VM1 VM2 Disk1 Disk2 ioctl() Linux with KVM 5 / 38 OpenStack, et al. libguestfs Virt Driver (guestfish) Custom Appliance KVM-based virtualization components libvirtd QMP QMP QEMU QEMU VM1 VM2 Disk1 Disk2 ioctl() Linux with KVM 5 / 38 libguestfs (guestfish) Custom Appliance KVM-based virtualization components OpenStack, et al. -

Understanding Full Virtualization, Paravirtualization, and Hardware Assist
VMware Understanding Full Virtualization, Paravirtualization, and Hardware Assist Contents Introduction .................................................................................................................1 Overview of x86 Virtualization..................................................................................2 CPU Virtualization .......................................................................................................3 The Challenges of x86 Hardware Virtualization ...........................................................................................................3 Technique 1 - Full Virtualization using Binary Translation......................................................................................4 Technique 2 - OS Assisted Virtualization or Paravirtualization.............................................................................5 Technique 3 - Hardware Assisted Virtualization ..........................................................................................................6 Memory Virtualization................................................................................................6 Device and I/O Virtualization.....................................................................................7 Summarizing the Current State of x86 Virtualization Techniques......................8 Full Virtualization with Binary Translation is the Most Established Technology Today..........................8 Hardware Assist is the Future of Virtualization, but the Real Gains Have -

Introduction to Virtualization
z Systems Introduction to Virtualization SHARE Orlando Linux and VM Program Romney White, IBM [email protected] z Systems Architecture and Technology © 2015 IBM Corporation Agenda ° Introduction to Virtualization – Concept – Server Virtualization Approaches – Hypervisor Implementation Methods – Why Virtualization Matters ° Virtualization on z Systems – Logical Partitions – Virtual Machines 2 z Systems Virtualization Technology © 2015 IBM Corporation Virtualization Concept Virtual Resources Proxies for real resources: same interfaces/functions, different attributes May be part of a physical resource or multiple physical resources Virtualization Creates virtual resources and "maps" them to real resources Primarily accomplished with software or firmware Resources Components with architecturally-defined interfaces/functions May be centralized or distributed - usually physical Examples: memory, disk drives, networks, servers Separates presentation of resources to users from actual resources Aggregates pools of resources for allocation to users as virtual resources 3 z Systems Virtualization Technology © 2015 IBM Corporation Server Virtualization Approaches Hardware Partitioning Bare-metal Hypervisor Hosted Hypervisor Apps ... Apps Apps ... Apps Apps ... Apps OS OS OS OS OS OS Adjustable partitions Hypervisor Hypervisor Partition Controller Host OS SMP Server SMP Server SMP Server Server is subdivided into fractions Hypervisor provides fine-grained Hypervisor uses OS services to each of which can run an OS timesharing of all resources -

KVM Based Virtualization and Remote Management Srinath Reddy Pasunuru St
St. Cloud State University theRepository at St. Cloud State Culminating Projects in Information Assurance Department of Information Systems 5-2018 KVM Based Virtualization and Remote Management Srinath Reddy Pasunuru St. Cloud State University, [email protected] Follow this and additional works at: https://repository.stcloudstate.edu/msia_etds Recommended Citation Pasunuru, Srinath Reddy, "KVM Based Virtualization and Remote Management" (2018). Culminating Projects in Information Assurance. 53. https://repository.stcloudstate.edu/msia_etds/53 This Starred Paper is brought to you for free and open access by the Department of Information Systems at theRepository at St. Cloud State. It has been accepted for inclusion in Culminating Projects in Information Assurance by an authorized administrator of theRepository at St. Cloud State. For more information, please contact [email protected]. 1 KVM Based Virtualization and Remote Management by Srinath Reddy Pasunuru A Starred Paper Submitted to the Graduate Faculty of St. Cloud State University in Partial Fulfillment of the Requirements for the Degree Master of Science in Information Assurance May, 2018 Starred Paper Committee Susantha Herath, Chairperson Ezzat Kirmani Sneh Kalia 2 Abstract In the recent past, cloud computing is the most significant shifts and Kernel Virtual Machine (KVM) is the most commonly deployed hypervisor which are used in the IaaS layer of the cloud computing systems. The Hypervisor is the one which provides the complete virtualization environment which will intend to virtualize as much as hardware and systems which will include the CPUs, Memory, network interfaces and so on. Because of the virtualization technologies such as the KVM and others such as ESXi, there has been a significant decrease in the usage if the resources and decrease in the costs involved. -

Hypervisors Vs. Lightweight Virtualization: a Performance Comparison
2015 IEEE International Conference on Cloud Engineering Hypervisors vs. Lightweight Virtualization: a Performance Comparison Roberto Morabito, Jimmy Kjällman, and Miika Komu Ericsson Research, NomadicLab Jorvas, Finland [email protected], [email protected], [email protected] Abstract — Virtualization of operating systems provides a container and alternative solutions. The idea is to quantify the common way to run different services in the cloud. Recently, the level of overhead introduced by these platforms and the lightweight virtualization technologies claim to offer superior existing gap compared to a non-virtualized environment. performance. In this paper, we present a detailed performance The remainder of this paper is structured as follows: in comparison of traditional hypervisor based virtualization and Section II, literature review and a brief description of all the new lightweight solutions. In our measurements, we use several technologies and platforms evaluated is provided. The benchmarks tools in order to understand the strengths, methodology used to realize our performance comparison is weaknesses, and anomalies introduced by these different platforms in terms of processing, storage, memory and network. introduced in Section III. The benchmark results are presented Our results show that containers achieve generally better in Section IV. Finally, some concluding remarks and future performance when compared with traditional virtual machines work are provided in Section V. and other recent solutions. Albeit containers offer clearly more dense deployment of virtual machines, the performance II. BACKGROUND AND RELATED WORK difference with other technologies is in many cases relatively small. In this section, we provide an overview of the different technologies included in the performance comparison. -

The Operating System Process in Virtualization for Cloud Computing 1J
INFOKARA RESEARCH ISSN NO: 1021-9056 THE OPERATING SYSTEM PROCESS IN VIRTUALIZATION FOR CLOUD COMPUTING 1J. Saravanan, 2Saravanan .P 1M.Phil. Research Scholar, D.B.Jain College (Autonomous), Thoraipakkam, Chennai, India. E-mail: [email protected] 2Assistant Professor, D.B.Jain College (Autonomous), Thoraipakkam, Chennai, India. E-mail: [email protected] ABSTRACT: OS-level virtualization is an era that walls the working system to create a couple of remoted Virtual Machines (VM). An OS-level VM is a digital execution environment that may be forked right away from the baserunning environment. OS-level virtualization has been extensively used to improve safety, manageability, and availability of today’s complicated software program surroundings, with small runtime and resource overhead, and with minimal modifications to the existing computing infrastructure. Keywords: Operating System Virtualization, Virtual Machines, Virtual Environment Cloud Computing, Virtual Private System. 1. INTRODUCTION: Operating System Virtualization (OS Virtualization) is the last form of Virtualization in Cloud Computing. Operating system virtualization is a part of virtualization technology and is a form of server virtualization. In this OS Virtualization tutorial, we are going to cowl makes use of, working, types, kinds of disks, blessings of Operating System Virtualization. Operating System virtualizations consists of a modified shape than a normal operating system so that exceptional customers can perform its give up-use unique applications. This entire process shall perform on a unmarried laptop at a time. In OS virtualizations, the virtual eyes surroundings accept the command from any of the users working it and performs the different duties on the identical gadget by using running specific packages. -

New Directors of the A.P. Moller Holding Board
Copenhagen March 12 2020 New Directors of the A.P. Moller Holding Board Diane Greene and Claus V. Hemmingsen are expected to be elected as new members of the A.P. Moller Holding Board of Directors at the annual general meeting April 20, 2020. Diane Greene is an American national and holds an M.S. in Computer Science from UC, Berkeley, an M.S. in Naval Architecture from MIT and a B.S. in Mechanical Engineering. Diane is a Director of SAP and Stripe, and a lifetime member of the MIT Corporation, as well as co- Chair of UC Berkeley School of Engineering Advisory Board. She is also an investor and advisor to tech start ups. Diane has served as Director of Google/Alphabet from 2012 to 2019, Intuit from 2006 to 2017, and VMware from 1998 to 2008. Diane was in 2015 employed by Google/Alphabet as CEO of Google Cloud. Prior to this, Diane co- founded and was CEO of three companies: VXtreme, which was sold to Microsoft in 1995, VMware, which she ran for 11 years and took public to a USD19bn valuation in 2007, and Bebop, sold to Google in 2015. Before that, Diane worked as a software engineer and as a Naval Architect. Diane was the U.S. national sailing champion in 1976 and remains an avid sailor. Claus V. Hemmingsen has since 1981 held various positions in the A.P. Moller Group, including Deputy CEO of A.P. Moller – Maersk, CEO of the Maersk Energy division, CEO of Maersk Drilling, SVP of the Maersk Shared Service Centres, CEO of APM Terminals, as well as various management positions in Singapore and Hong Kong. -

What's New in the Z/VM 6.3 Hypervisor Session 17515
What's New in the z/VM 6.3 Hypervisor Session 17515 John Franciscovich IBM: z/VM Development Endicott, NY Insert Custom Presented by Bill Bitner Session QR if [email protected] Desired Trademarks The following are trademarks of the International Business Machines Corporation in the United States and/or other countries. BladeCenter* FICON* OMEGAMON* RACF* System z9* zSecure DB2* GDPS* Performance Toolkit for VM Storwize* System z10* z/VM* DS6000* HiperSockets Power* System Storage* Tivoli* z Systems* DS8000* HyperSwap PowerVM System x* zEnterprise* ECKD IBM z13* PR/SM System z* z/OS* * Registered trademarks of IBM Corporation The following are trademarks or registered trademarks of other companies. Adobe, the Adobe logo, PostScript, and the PostScript logo are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States, and/or other countries. Cell Broadband Engine is a trademark of Sony Computer Entertainment, Inc. in the United States, other countries, or both and is used under license therefrom. Intel, Intel logo, Intel Inside, Intel Inside logo, Intel Centrino, Intel Centrino logo, Celeron, Intel Xeon, Intel SpeedStep, Itanium, and Pentium are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. IT Infrastructure Library is a registered trademark of the Central Computer and Telecommunications Agency which is now part of the Office of Government Commerce. ITIL is a registered trademark, and a registered community trademark of the Office of Government Commerce, and is registered in the U.S. Patent and Trademark Office. Java and all Java based trademarks and logos are trademarks or registered trademarks of Oracle and/or its affiliates. -

Virtualizationoverview
VMWAREW H WHITEI T E PPAPERA P E R Virtualization Overview 1 VMWARE WHITE PAPER Table of Contents Introduction .............................................................................................................................................. 3 Virtualization in a Nutshell ................................................................................................................... 3 Virtualization Approaches .................................................................................................................... 4 Virtualization for Server Consolidation and Containment ........................................................... 7 How Virtualization Complements New-Generation Hardware .................................................. 8 Para-virtualization ................................................................................................................................... 8 VMware’s Virtualization Portfolio ........................................................................................................ 9 Glossary ..................................................................................................................................................... 10 2 VMWARE WHITE PAPER Virtualization Overview Introduction Virtualization in a Nutshell Among the leading business challenges confronting CIOs and Simply put, virtualization is an idea whose time has come. IT managers today are: cost-effective utilization of IT infrastruc- The term virtualization broadly describes the separation -

Paravirtualization (PV)
Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. Fidelity National Financial Distinguished Professor of CIS School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels of privilege known as Ring 0, 1, 2 and 3 to operating systems and applications to manage access to the computer hardware. While user level applications typically run in Ring 3, the operating system needs to have direct access to the memory and hardware and must execute its privileged instructions in Ring 0. x86 privilege level architecture without virtualization Technique 1: Full Virtualization using Binary Translation This approach relies on binary translation to trap (into the VMM) and to virtualize certain sensitive and non-virtualizable instructions with new sequences of instructions that have the intended effect on the virtual hardware. Meanwhile, user level code is directly executed on the processor for high performance virtualization. Binary translation approach to x86 virtualization Full Virtualization using Binary Translation This combination of binary translation and direct execution provides Full Virtualization as the guest OS is completely decoupled from the underlying hardware by the virtualization layer. The guest OS is not aware it is being virtualized and requires no modification. The hypervisor translates all operating system instructions at run-time on the fly and caches the results for future use, while user level instructions run unmodified at native speed. VMware’s virtualization products such as VMWare ESXi and Microsoft Virtual Server are examples of full virtualization. Full Virtualization using Binary Translation The performance of full virtualization may not be ideal because it involves binary translation at run-time which is time consuming and can incur a large performance overhead. -

IIP (System Z9 Integrated Information Processor) Computer CEC (Central Electronics Complex) Server
IBM System z z/VM Basics Arwed Tschoeke Systems Architect [email protected] © 2009 IBM Corporation © 2008 IBM Corporation Introduction We'll explain basic concepts of System z: – Terminology – Processors – Memory – I/O – Networking We'll see that z/VM virtualizes a System z machine: – Virtual processors – Virtual memory – … and so on Where appropriate, we'll compare or contrast: – PR/SM or LPAR – z/OS – Linux 2 z/VM: The Very Basics z/VM: The Very Basics 1 IBM System z © 2008 IBM Corporation System z Parts Nomenclature x86, UNIX, etc. System z Memory Storage (though we are moving toward "memory") Disk, Storage DASD – Direct Access Storage Device Processor Processor, Engine, PU (processing unit) IOP (I/O processor) CPU (central processing unit) CP (central processor) SAP (system assist processor) Specialty engines –IFL (Integrated Facility for Linux) –zAAP (System z Application Assist Processor) –zIIP (System z9 Integrated Information Processor) Computer CEC (central electronics complex) Server 3 z/VM: The Very Basics © 2008 IBM Corporation IBM System z Virtualization Genetics Over 40 years of continuous innovation in virtualization – Refined to support modern business requirements System z10 . – Exploit hardware technology for economical growth , .. ity System z9 z/VM V5 bil – LPAR, Integrated Facility for Linux, HiperSockets xi 64-Bit Fle – System z Application Assist Processors s, zSeries es VM/ESA Virtual Switch – System z Information Integration stn 9672 bu ESA Guest LANs Set Observer Ro Processors y, 9x21 ilit VM/XA Virtual Machine -
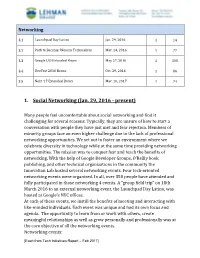
Networking Events
Networking 3.1 Launchpad Day Latino Jan. 29, 2016 1 14 3.2 Path to Success: Women Techmakers Mar. 24, 2016 1 77 3.3 Google I/O Extended Bronx May 27, 2016 1 100 3.4 DevFest 2016 Bronx Oct. 29, 2016 1 86 3.5 Next ‘17 Extended Bronx Mar. 10, 2017 1 74 1. Social Networking (Jan. 29, 2016 - present) Many people feel uncomfortable about social networking and find it challenging for several reasons. Typically, they are unsure of how to start a conversation with people they have just met and fear rejection. Members of minority groups face an even higher challenge due to the lack of professional networking opportunities. We set out to foster an environment where we celebrate diversity in technology while at the same time providing networking opportunities. The mission was to conquer fear and teach the benefits of networking. With the help of Google Developer Groups, O’Reilly book publishing, and other technical organizations in the community the Innovation Lab hosted several networking events. Four tech-oriented networking events were organized. In all, over 350 people have attended and fully participated in those networking 4 events. A “group field trip” on 18th March 2016 to an external networking event, the Launchpad Day Latino, was hosted at Google's NYC offices. At each of these events, we instill the benefits of meeting and interacting with like-minded individuals. Each event was unique and had its own focus and agenda. The opportunity to learn from or work with others, create meaningful relationships as well as grow personally and professionally was at the core objective of all the networking events.