Linux Commands Cheat Sheet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MAX3946 1Gbps to 11.3Gbps, SFP+ Laser Driver with Laser Impedance
19-5182; Rev 1; 5/11 EVALUATION KIT AVAILABLE 1Gbps to 11.3Gbps, SFP+ Laser Driver with Laser Impedance Mismatch Tolerance MAX3946 General Description Features The MAX3946 is a +3.3V, multirate, low-power laser S 225mW Power Dissipation Enables < 1W SFP+ diode driver designed for Ethernet and Fibre Channel Modules transmission systems at data rates up to 11.3Gbps. S Up to 100mW Power Consumption Reduction by This device is optimized to drive a differential transmit- Enabling the Use of Unmatched FP/DFB TOSAs ter optical subassembly (TOSA) with a 25I flex circuit. The unique design of the output stage enables use of S Supports SFF-8431 SFP+ MSA and SFF-8472 unmatched TOSAs, greatly reducing headroom limita- Digital Diagnostic tions and lowering power consumption. S 225mW Power Dissipation at 3.3V (IMOD = 40mA, The device receives differential CML-compatible signals IBIAS = 60mA Assuming 25I TOSA) with on-chip line termination. It can deliver laser modula- S Single +3.3V Power Supply tion current of up to 80mA, at an edge speed of 22ps S Up to 11.3Gbps (NRZ) Operation (20% to 80%), into a 5I to 25I external differential load. S Programmable Modulation Current from 10mA to The device is designed to have a symmetrical output 100mA (5I Load) stage with on-chip back terminations integrated into its outputs. A high-bandwidth, fully differential signal S Programmable Bias Current from 5mA to 80mA path is implemented to minimize deterministic jitter. An S Programmable Input Equalization equalization block can be activated to compensate for S Programmable Output Deemphasis the SFP+ connector. -

Linux Pocket Guide.Pdf
3rd Edition Linux Pocket Guide ESSENTIAL COMMANDS Daniel J. Barrett 3RD EDITION Linux Pocket Guide Daniel J. Barrett Linux Pocket Guide by Daniel J. Barrett Copyright © 2016 Daniel Barrett. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebasto‐ pol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promo‐ tional use. Online editions are also available for most titles (http://safaribook‐ sonline.com). For more information, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Editor: Nan Barber Production Editor: Nicholas Adams Copyeditor: Jasmine Kwityn Proofreader: Susan Moritz Indexer: Daniel Barrett Interior Designer: David Futato Cover Designer: Karen Montgomery Illustrator: Rebecca Demarest June 2016: Third Edition Revision History for the Third Edition 2016-05-27: First Release See http://oreilly.com/catalog/errata.csp?isbn=9781491927571 for release details. The O’Reilly logo is a registered trademark of O’Reilly Media, Inc. Linux Pocket Guide, the cover image, and related trade dress are trademarks of O’Reilly Media, Inc. While the publisher and the author have used good faith efforts to ensure that the information and instructions contained in this work are accurate, the publisher and the author disclaim all responsibility for errors or omissions, including without limitation responsibility for damages resulting from the use of or reliance on this work. Use of the information and instructions contained in this work is at your own risk. If any code samples or other technology this work contains or describes is subject to open source licenses or the intellec‐ tual property rights of others, it is your responsibility to ensure that your use thereof complies with such licenses and/or rights. -

The Bioinformatics Lab Linux Proficiency Terminal-Based Text Editors Version Control Systems
The Bioinformatics Lab Linux proficiency terminal-based text editors version control systems Jonas Reeb 30.04.2013 “What makes you proficient on the command line?” - General ideas I Use CLIs in the first place I Use each tool for what it does best I Chain tools for more complex tasks I Use power of shell for small scripting jobs I Automate repeating tasks I Knowledge of regular expression 1 / 22 Standard tools I man I ls/cd/mkdir/rm/touch/cp/mv/chmod/cat... I grep, sort, uniq I find I wget/curl I scp/ssh I top(/htop/iftop/iotop) I bg/fg 2 / 22 Input-Output RedirectionI By default three streams (“files”) open Name Descriptor stdin 0 stdout 1 stderr 2 Any program can check for its file descriptors’ redirection! (isatty) 3 / 22 Input-Output RedirectionII Output I M>f Redirect file descriptor M to file f, e.g. 1>f I Use >> for appending I &>f Redirect stdout and stderr to f I M>&N Redirect fd M to fd N Input I 0<f Read from file f 4 / 22 Pipes I Forward output of one program to input of another I Essential for Unix philosophy of specialized tools I grep -P -v "^>" *.fa | sort -u > seqs I Input and arguments are different things. Use xargs for arguments: ls *.fa | xargs rm 5 / 22 Scripting I Quick way to get basic programs running I Basic layout: #!/bin/bash if test"$1" then count=$1 else count=0 fi for i in {1..10} do echo $((i+count)) let"count +=1" done 6 / 22 Motivation - “What makes a good text editor” I Fast execution, little system load I Little bandwidth needed I Available for all (your) major platforms –> Familiar environment I Fully controllable via keyboard I Extensible and customizable I Auto-indent, Auto-complete, Syntax highlighting, Folding, .. -

CP/M-80 Kaypro
$3.00 June-July 1985 . No. 24 TABLE OF CONTENTS C'ing Into Turbo Pascal ....................................... 4 Soldering: The First Steps. .. 36 Eight Inch Drives On The Kaypro .............................. 38 Kaypro BIOS Patch. .. 40 Alternative Power Supply For The Kaypro . .. 42 48 Lines On A BBI ........ .. 44 Adding An 8" SSSD Drive To A Morrow MD-2 ................... 50 Review: The Ztime-I .......................................... 55 BDOS Vectors (Mucking Around Inside CP1M) ................. 62 The Pascal Runoff 77 Regular Features The S-100 Bus 9 Technical Tips ........... 70 In The Public Domain... .. 13 Culture Corner. .. 76 C'ing Clearly ............ 16 The Xerox 820 Column ... 19 The Slicer Column ........ 24 Future Tense The KayproColumn ..... 33 Tidbits. .. .. 79 Pascal Procedures ........ 57 68000 Vrs. 80X86 .. ... 83 FORTH words 61 MSX In The USA . .. 84 On Your Own ........... 68 The Last Page ............ 88 NEW LOWER PRICES! NOW IN "UNKIT"* FORM TOO! "BIG BOARD II" 4 MHz Z80·A SINGLE BOARD COMPUTER WITH "SASI" HARD·DISK INTERFACE $795 ASSEMBLED & TESTED $545 "UNKIT"* $245 PC BOARD WITH 16 PARTS Jim Ferguson, the designer of the "Big Board" distributed by Digital SIZE: 8.75" X 15.5" Research Computers, has produced a stunning new computer that POWER: +5V @ 3A, +-12V @ 0.1A Cal-Tex Computers has been shipping for a year. Called "Big Board II", it has the following features: • "SASI" Interface for Winchester Disks Our "Big Board II" implements the Host portion of the "Shugart Associates Systems • 4 MHz Z80-A CPU and Peripheral Chips Interface." Adding a Winchester disk drive is no harder than attaching a floppy-disk The new Ferguson computer runs at 4 MHz. -

Week 49, 2018 – Friday 7Th December Click Here to View the Email As a PDF
Shipping Regulations and Guidance Week 49, 2018 – Friday 7th December Click Here to view the email as a PDF. Forward this email to a friend Flag State Regulations and Guidance Updates UK – has released a new marine guidance notice entitled 'ILO Work in Fishing Convention, 2007 (No. 188) – Fishermen's Work Agreements'. Australia – has released an amendment order to marine order 'Certificates of survey - national law'. Marshall Islands – has published a new marine safety advisory entitled 'Guidance on the Development of a Ship Implementation Plan for the Consistent Implementation of the 0.50% Sulphur Limit under MARPOL Annex VI'. Panama – has updated three circulars: 'Ballast Water Management Convention 2004, Panama Policy' 'Adoption of Amendments to MARPOL 73/78, Annex VI Panama Policy on IMO- DCS scheme'. 'Correction of Deficiencies found in ASI InspectionsCorrection of Deficiencies found in ASI Inspections'. Isle of Man – has issued a new shipping notice entitled 'SOLAS Chapter XI-2 & the ISPS Code'. Singapore – has released a new port marine circular entitled 'Johor Bahru Port Limits'. Recent Class Society Guidance American Bureau of Shipping – has released a new guidance document entitled 'Guide for Enhanced Shaft Alignment', and has updated seven collections of documents: 'Guide for Building and Classing International Naval Ships' 'Rules for Building and Classing Offshore Support Vessels' 'Rules for Building and Classing High-Speed Naval Craft' 'Rules for Building and Classing Mobile Offshore Drilling Units' 'Rules for Building and Classing High-Speed Craft' 'Rules for Building and Classing Steel Vessels' 'Rules for Building and Classing Steel Vessels Under 90 Meters in Length'. Bureau Veritas – has has issued a new guidance document entitled 'Rules for the Classification of Diving Systems'. -

DDOS Detection and Denial Using Third Party Application in SDN
International Conference on Energy, Communication, Data Analytics and Soft Computing (ICECDS-2017) DDOS Detection and Denial using Third Party Application in SDN Roshni Mary Thomas Divya James Dept. of Information Technology Dept. of Information Technology Rajagiri School of Engineering & Technology Rajagiri School of Engineering & Technology Ernakulam, India Ernakulam, India [email protected] [email protected] Abstract— Software Defined Networking(SDN) is a developing introduced i.e, Software Defined Networking (SDN). Software area where network managers can manage the network behavior Defined Networking (SDN) is a developing area where it programmatically such as modify, control etc. Using this feature extract the limitations of traditional network which make we can empower, facilitate or e network related security networking more uncomplicated. In SDN we can develop or applications due to the its capacity to reprogram the data plane change the network functions or behavior program. To make at any time. DoS/DDoS attacks are attempt to make controller the decision where the traffic needs to send with the updated functions such as online services or web applications unavailable to clients by exhausting computing or memory resources of feature SDN decouple the network planes into two. servers using multiple attackers. A DDoS attacker could produce 1. Control Plane enormous flooding traffic in a short time to a server so that the 2. Data Plane services provided by the server get degraded. This will lose of In control plane we can add update or add new features customer support, brand trust etc. to improve the network programmatically also we can change To detect this DDoS attack we use a traffic monitoring method the traffic according to our decision and in updated traffic are iftop in the server as third party application and check the traffic applied in data plane. -

Data Transfer Node (DTN) Tests on the GÉANT Testbeds Service (GTS)
09-12-2020 Data Transfer Node (DTN) Tests on the GÉANT Testbeds Service (GTS) Grant Agreement No.: 856726 Work Package WP6 Task Item: Task 2 Document ID: GN4-3-20-265f683 Authors: Iacovos Ioannou (CYNET), Damir Regvart (CARNET), Joseph Hill (UvA/SURF), Maria Isabel Gandia (CSUC/RedIRIS), Ivana Golub (PSNC), Tim Chown (Jisc), Susanne Naegele Jackson (FAU/DFN) © GÉANT Association on behalf of the GN4-3 project. The research leading to these results has received funding from the European Union’s Horizon 2020 research and innovation programme under Grant Agreement No. 856726 (GN4-3). Abstract Many research projects need to transfer large amounts of data and use specialised Data Transfer Nodes (DTNs) to optimise the efficiency of these transfers. In order to help NRENs to better support user communities who seek to move large volumes of data across their network, a DTN Focus Group was set up in the Network Technologies and Services Development work package (WP6) of the GN4-3 project, which has performed several activities around DTN deployment, the results of which are summarised in this document. Table of Contents Executive Summary 1 1 Introduction 2 2 The DTN Survey and DTN Wiki 5 3 Optimising DTN Configurations 6 3.1 Networking 6 3.1.1 Socket Parameters 7 3.1.2 TCP Socket Parameters 7 3.1.3 NIC Driver Settings 8 3.1.4 MTU Settings 8 3.2 Storage 9 3.2.1 Bus vs Disk Speed 9 3.2.2 Spinning versus Solid State Disks 9 3.2.3 NVMe 9 3.2.4 RAID 10 3.2.5 Remote Storage 10 3.3 Architecture 10 3.3.1 Fast Cores vs Many Cores 10 3.3.2 NUMA 10 3.3.3 -

High Performance Linux Shell Programming Reference 2015 Edition
Extensive, example-based Linux shell programming reference includes an English-to-shell dictionary, a tutorial and handbook, and many tables of information useful to programmers. Besides listing more than 2000 shell one- liners, it explains the principles and techniques of how to increase performance (execution speed, reliability, and efficiency), which apply to many other programming languages beyond shell. High Performance Linux Shell Programming Reference 2015 Edition Order the complete book from Booklocker.com http://www.booklocker.com/p/books/7831.html?s=pdf or from your favorite neighborhood or online bookstore. Your free excerpt appears below. Enjoy! High Performance Linux Shell Programming Reference 2015 Edition High Performance Linux Shell Programming Reference, 2015 Edition Copyright © 2015 by Edward J. Smeltz ISBN 978-1-63263-401-6 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, recording or otherwise, without the prior written permission of the author. Printed on acid-free paper All information herein is believed to be accurate and correct, but the author and Booklocker.com, Inc assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained in this book. Manufacturers and sellers often use specific designations for their products to distinguish them in the marketplace. Where such designations appear in this book, and E. J. Smeltz was aware of a trademark claim, the designations have been printed in all caps or in initial caps. All trademarks are the property of their respective owners. -

Flexible Internet Router for Linux
fli4l – flexible internet router for linux Version 3.10.18 The fli4l-Team email: [email protected] September 15, 2019 Contents 1. Documentation of the base package 10 1.1. Introduction...................................... 10 2. Setup and Configuration 13 2.1. Unpacking the archives................................ 13 2.2. Configuration..................................... 14 2.2.1. Editing the configuration files........................ 14 2.2.2. Configuration via a special configuration file................ 15 2.2.3. Variables................................... 15 2.3. Setup flavours..................................... 15 2.3.1. Router on a USB-Stick............................ 16 2.3.2. Router on a CD, or network boot...................... 16 2.3.3. Type A: Router on hard disk—only one FAT partition.......... 16 2.3.4. Type B: Router on hard disk—one FAT and one ext3 partition..... 16 3. Base configuration 18 3.1. Example file...................................... 19 3.2. General settings.................................... 25 3.3. Console settings.................................... 30 3.4. Hints To Identify Problems And Errors...................... 31 3.5. Usage of a customized /etc/inittab......................... 32 3.6. Localized keyboard layouts............................. 32 3.7. Ethernet network adapter drivers.......................... 33 3.8. Networks....................................... 42 3.9. Additional routes (optional)............................. 44 3.10. The Packet Filter................................... 44 3.10.1. Packet Filter -
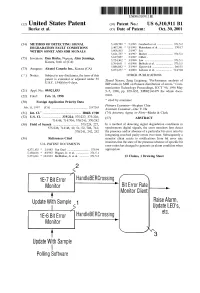
Update W Sample Polling Software U.S
USOO6310911B1 (12) United States Patent (10) Patent No.: US 6,310,911 B1 Burke et al. (45) Date of Patent: Oct. 30, 2001 (54) METHOD OF DETECTING SIGNAL 5,418,789 5/1995 Gersbach et al. ..................... 371/5.2 DEGRADATION FAULT CONDITIONS 5,467,341 11/1995 Matsukane et al. ................... 370/17 WITHIN SONET AND SDH SIGNALS 5,606,563 2/1997 Lee. 5,621,737 * 4/1997 Bucher .................................. 371/5.1 (75) Inventors: panist, Nips Alan Jennings, 5,724,3625,627,837 3/19985/1997 Gillett.Lau ....................................... 371/5.1 s 5,764,651 * 6/1998 Bullock et al. .. ... 371/5.5 rr. A 5,886,842 * 3/1999 Ziperovich ...... ... 360/51 (73) Assignee: Alcatel Canada Inc., Kanata (CA) 6,073,257 * 4/2000 Labonte et al. ...................... 714/704 (*) Notice: Subject to any disclaimer, the term of this OTHER PUBLICATIONS patent is extended or adjusted under 35 Zhand Xiaoru, Zneg Lieguang: "Performance analysis of U.S.C. 154(b) by 0 days. BIP codes in SDH on Poisson distribution of errors.” Com munication Technology Proceedings, ICCT '96, 1996 May (21) Appl. No.: 09/021,833 5–7, 1996, pp. 829–832, XP002146479 the whole docu (22) Filed: Feb. 11, 1998 ment. (30) Foreign Application Priority Data * cited by examiner Primary Examiner Stephen Chin Feb. 11, 1997 (CA) .................................................. 2197263 ASSistant Examiner-Dac V. Ha (51) Int. Cl." ................................................. H04B 17700 (74) Attorney, Agent, or Firm Marks & Clerk (52) U.S. Cl. .......................... 375/224; 375/227; 375/228; (57) ABSTRACT 714/48; 714/704; 370/241; 370/242 (58) Field of Search .................................... -

SECUMOBI SERVER Technical Description
SECUMOBI SERVER Technical Description Contents SIP Server 3 Media Relay 10 Dimensioning of the Hardware 18 SIP server 18 Media Proxy 18 Page 2 of 18 SIP Server Operatingsystem: Debian https://www.debian.org/ Application: openSIPS http://www.opensips.org/ OpenSIPS is built and installed from source code. The operating system is installed with the following packages: Package Description acpi displays information on ACPI devices acpi-support-base scripts for handling base ACPI events such as the power button acpid Advanced Configuration and Power Interface event daemon adduser add and remove users and groups anthy-common input method for Japanese - common files and dictionary apt Advanced front-end for dpkg apt -utils APT utility programs aptitude terminal-based package manager (terminal interface only) autopoint The autopoint program from GNU gettext backup -manager command -line backup tool base-files Debian base system miscellaneous files base-passwd Debian base system master password and group files bash The GNU Bourne Again SHell bc The GNU bc arbitrary precision calculator language binutils The GNU assembler, linker and binary utilities bison A parser generator that is compatible with YACC bsdmainutils collection of more utilities from FreeBSD bsdutils Basic utilities from 4.4BSD-Lite build -essential Informational list of build -essential packages busybox Tiny utilities for small and embedded systems bzip2 high-quality block-sorting file compressor - utilities ca-certificates Common CA certificates console-setup console font and keymap -

Section 4 Network Programming and Administration Exercises
Lab Manual SECTION 4 NETWORK PROGRAMMING AND ADMINISTRATION EXERCISES Structure Page Nos. 4.0 Introduction 48 4.1 Objectives 48 4.2 Lab Sessions 49 4.3 List of Unix Commands 52 4.4 List of TCP/IP Ports 54 3.5 Summary 58 3.6 Further Readings 58 4.0 INTRODUCTION In the earlier sections, you studied the Unix, Linux and C language basics. This section contains more practical information to help you know best about Socket programming, it contains different lab exercises based on Unix and C language. We hope these exercises will provide you practice for socket programming. Towards the end of this section, we have given the list of Unix commands frequently required by the Unix users, further we have given a list of port numbers to indicate the TCP/IP services which will be helpful to you during socket programming. To successfully complete this section, the learner should have the following knowledge and skills prior to starting the section. S/he must have: • Studied the corresponding course material of BCS-052 and completed the assignments. • Proficiency to work with Unix and Linux and C interface. • Knowledge of networking concepts, including network operating system, client- server relationship, and local area network (LAN). Also, to successfully complete this section, the learner should adhere to the following: • Before attending the lab session, the learner must already have written steps/algorithms in his/her lab record. This activity should be treated as home- work that is to be done before attending the lab session. • The learner must have already thoroughly studied the corresponding units of the course material (BCS-052) before attempting to write steps/algorithms for the problems given in a particular lab session.