Exploiting Autorun: Threats, Vulnerabilities and Countermeasures of the Autorun Functionality Associated with Portable Data Storage Devices by Kevin M
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Rise of Autorun- Based Malware by Vinoo Thomas, Prashanth Ramagopal, and Rahul Mohandas Report the Rise of Autorun-Based Malware
Report The Rise of AutoRun- Based Malware By Vinoo Thomas, Prashanth Ramagopal, and Rahul Mohandas Report The Rise of AutoRun-Based Malware Table of Contents Abstract 3 The Return of Removable-Disk Malware 3 Distribution of AutoRun-Based Malware 4 AutoRun Woes 6 Incomplete autorun.inf cleaning 7 Traditional detection methods 8 Smart removal of autorun.inf 8 Leveraging In-the-Cloud Computing Technology 10 The Road Ahead 11 About the authors 12 Report The Rise of AutoRun-Based Malware Abstract Most people associate today’s computer viruses and other prevalent malware with the Internet. But that’s not where they started. Lest we forget, the earliest computer threats came from the era of floppy disks and removable media. With the arrival of the Internet, email and network-based attacks became the preferred infection vector for hackers to spread malicious code—while security concerns about removable media took a back seat. Now, however, our attention is returning to plug-in media. Over the years, floppy disks have been replaced by portable hard drives, flash media cards, memory sticks, and other forms of data storage. Today’s removable devices can hold 10,000 times more data than yesterday’s floppy disks. Not only can they store more data, today’s devices are “smart”—with the ability to run portable software programs1 or boot operating systems. 2,3 Seeing the popularity of removable storage, virus authors realized the potential of using this media as an infection vector. And they are greatly aided by a convenience feature in operating systems called AutoRun, which launches the content on a removable disk without any user interaction. -

The Downadup Codex a Comprehensive Guide to the Threat’S Mechanics
Security Response The Downadup Codex A comprehensive guide to the threat’s mechanics. Edition 2.0 Introduction Contents Introduction.............................................................1 Since its appearance in late-2008, the Downadup worm has become Editor’s Note............................................................5 one of the most wide-spread threats to hit the Internet for a number of Increase in exploit attempts against MS08-067.....6 years. A complex piece of malicious code, this threat was able to jump W32.Downadup infection statistics.........................8 certain network hurdles, hide in the shadows of network traffic, and New variants of W32.Downadup.B find new ways to propagate.........................................10 defend itself against attack with a deftness not often seen in today’s W32.Downadup and W32.Downadup.B threat landscape. Yet it contained few previously unseen features. What statistics................................................................12 set it apart was the sheer number of tricks it held up its sleeve. Peer-to-peer payload distribution...........................15 Geo-location, fingerprinting, and piracy...............17 It all started in late-October of 2008, we began to receive reports of A lock with no key..................................................19 Small improvements yield big returns..................21 targeted attacks taking advantage of an as-yet unknown vulnerability Attempts at smart network scanning...................23 in Window’s remote procedure call (RPC) service. Microsoft quickly Playing with Universal Plug and Play...................24 released an out-of-band security patch (MS08-067), going so far as to Locking itself out.................................................27 classify the update as “critical” for some operating systems—the high- A new Downadup variant?......................................29 Advanced crypto protection.................................30 est designation for a Microsoft Security Bulletin. -

Investigating Powershell Attacks
Investigating PowerShell Attacks Black Hat USA 2014 August 7, 2014 PRESENTED BY: Ryan Kazanciyan, Matt Hastings © Mandiant, A FireEye Company. All rights reserved. Background Case Study WinRM, Victim VPN SMB, NetBIOS Attacker Victim workstations, Client servers § Fortune 100 organization § Command-and-control via § Compromised for > 3 years § Scheduled tasks § Active Directory § Local execution of § Authenticated access to PowerShell scripts corporate VPN § PowerShell Remoting © Mandiant, A FireEye Company. All rights reserved. 2 Why PowerShell? It can do almost anything… Execute commands Download files from the internet Reflectively load / inject code Interface with Win32 API Enumerate files Interact with the registry Interact with services Examine processes Retrieve event logs Access .NET framework © Mandiant, A FireEye Company. All rights reserved. 3 PowerShell Attack Tools § PowerSploit § Posh-SecMod § Reconnaissance § Veil-PowerView § Code execution § Metasploit § DLL injection § More to come… § Credential harvesting § Reverse engineering § Nishang © Mandiant, A FireEye Company. All rights reserved. 4 PowerShell Malware in the Wild © Mandiant, A FireEye Company. All rights reserved. 5 Investigation Methodology WinRM PowerShell Remoting evil.ps1 backdoor.ps1 Local PowerShell script Persistent PowerShell Network Registry File System Event Logs Memory Traffic Sources of Evidence © Mandiant, A FireEye Company. All rights reserved. 6 Attacker Assumptions § Has admin (local or domain) on target system § Has network access to needed ports on target system § Can use other remote command execution methods to: § Enable execution of unsigned PS scripts § Enable PS remoting © Mandiant, A FireEye Company. All rights reserved. 7 Version Reference 2.0 3.0 4.0 Requires WMF Requires WMF Default (SP1) 3.0 Update 4.0 Update Requires WMF Requires WMF Default (R2 SP1) 3.0 Update 4.0 Update Requires WMF Default 4.0 Update Default Default Default (R2) © Mandiant, A FireEye Company. -

Hunting Red Team Activities with Forensic Artifacts
Hunting Red Team Activities with Forensic Artifacts By Haboob Team 1 [email protected] Table of Contents 1. Introduction .............................................................................................................................................. 5 2. Why Threat Hunting?............................................................................................................................. 5 3. Windows Forensic.................................................................................................................................. 5 4. LAB Environment Demonstration ..................................................................................................... 6 4.1 Red Team ......................................................................................................................................... 6 4.2 Blue Team ........................................................................................................................................ 6 4.3 LAB Overview .................................................................................................................................. 6 5. Scenarios .................................................................................................................................................. 7 5.1 Remote Execution Tool (Psexec) ............................................................................................... 7 5.2 PowerShell Suspicious Commands ...................................................................................... -

Ultimate Spider-Man™ README Last Updated: 6/28/05
Ultimate Spider-Man™ README Last Updated: 6/28/05 TABLE OF CONTENTS INTRODUCTION INSTALLATION & SET UP 1. Minimum System Requirements 2. Autoplay 3. DirectX(R) Detection & Installation VIDEO ISSUES 1. Monitors 2. In-game and Desktop Resolutions 3. Graphical Corruption When Changing Video Settings 4. Windowed Mode/Standby Mode 5. Changing Brightness and Contrast GENERAL ISSUES 1. Alt-Tab & Alt-Enter 2. Uninstalling with Antivirus Software Enabled 3. Gamepad Options 4. Invert Controls Setting 5. Options for Lower End Systems INTRODUCTION Refer to this document if you encounter difficulties with one or more aspects of installation or running the Ultimate Spider-Man™ game. Many of the most commonly encountered issues are covered here. INSTALLATION & SET UP 1. Ultimate Spider-Man™ Minimum System Requirements • 3D hardware accelerator card required - 100% DirectX(R) 9.0c-compliant 64 MB video card and drivers* • Microsoft(R) Windows(R) 2000/XP • Pentium(R) III 1.2 GHz or Athlon(TM) 1.2 GHz or higher processor • 256 MB of RAM • 3500 MB of uncompressed hard disk space (plus 400 MB for the Windows(R) swap file) • A 100% Windows(R) 2000/XP - compatible computer system including: • DirectX(R) 9.0c (Included) • 100% DirectX(R) 9.0c-compliant true 16-bit sound card and drivers • 100% Windows(R) 2000/XP - compatible mouse, keyboard and drivers • 100% Windows(R) 2000/XP - compatible quad speed CD-ROM drive (600 K/sec sustained transfer rate) and drivers *Supported Chipsets for Windows 2000/XP All NVIDIA(R) GeForce2(TM) and better chipsets All ATI(R) Radeon 7500(TM) and better chipsets *Important Note: Some 3D accelerator cards with the chipsets listed here may not be compatible with the 3D acceleration features utilized by Ultimate Spider-Man™. -

Critical Vulnerabilities Bulletin
January 18th, 2021 Critical Vulnerabilities Bulletin Confidential | Cyberint Copyright © All Rights Reserved 2020 CRITICAL VULNERABILITIES BULLETIN | INDUSTRY SECURITY BULLETIN JANUARY 14, 2021 EXECUTIVE SUMMARY Due to an unusual increase in Critical vulnerabilities found on Windows operating systems, Cyberint's Research Team has decided to release this bulletin to alert our customers of the potential impact. This bulletin will be expanded at the end of the month, as part of the Monthly Vulnerability bulletin we plan on releasing. The reason for this bulletin lies at 2 newly discovered vulnerabilities: 1. <No CVE assigned yet> - Corrupt NTFS OS partition without user interaction. 2. <No CVE assigned yet> - Trigger a BSOD by trying to access a system path. 3. CVE-2020-1398 - Potential bypass of Bitlocker protected systems, including Lock Screen bypass. We suspect that threat actors and updated malware may attempt to exploit these vulnerabilities to further impact potential victims. Confidential | Cyberint Copyright © All Rights Reserved 2020 2 CRITICAL VULNERABILITIES BULLETIN | INDUSTRY SECURITY BULLETIN JANUARY 14, 2021 NTFS CORRUPTION VULNERABILITY Published by a known vulnerability researcher, jonasLyk, it is possible to cause disk partition corruption by executing a cd command as a low privilege user, to a unique path, which causes the Windows Operating System to alert the user to a corrupted partition and force a restart. Whilst technical details are scarce, and the exact reason for the issue being unknown at this time, affected Windows builds using the NTFS file system include those from 1803 all the way to 20H2. According to SANS, the $bitmap is an attribute reserved for files marked as deleted, while $i30 is marked as an NTFS index attribute. -
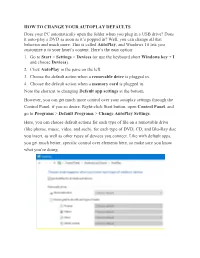
HOW to CHANGE YOUR AUTOPLAY DEFAULTS Does Your PC Automatically Open the Folder When You Plug in a USB Drive? Does It Auto-Play
HOW TO CHANGE YOUR AUTOPLAY DEFAULTS Does your PC automatically open the folder when you plug in a USB drive? Does it auto-play a DVD as soon as it’s popped in? Well, you can change all that behavior and much more. This is called AutoPlay, and Windows 10 lets you customize it to your heart’s content. Here’s the easy option: 1. Go to Start > Settings > Devices (or use the keyboard short Windows key + I and choose Devices). 2. Click AutoPlay in the pane on the left. 3. Choose the default action when a removable drive is plugged in. 4. Choose the default action when a memory card is plugged in. Note the shortcut to changing Default app settings at the bottom. However, you can get much more control over your autoplay settings through the Control Panel, if you so desire. Right-click Start button, open Control Panel, and go to Programs > Default Programs > Change AutoPlay Settings. Here, you can choose default actions for each type of file on a removable drive (like photos, music, video, and such), for each type of DVD, CD, and Blu-Ray disc you insert, as well as other types of devices you connect. Like with default apps, you get much better, specific control over elements here, so make sure you know what you’re doing. If nothing else, you should definitely change what Windows does for flash drives, since auto-running files from flash or thumb drives is one of the easiest ways to get a malware infection. . -

Dolphin Power Tools User's with Windows Embedded Handheld 6.5
Dolphin™ Power Tools with Windows® Mobile 6.X for the Dolphin 6000 Scanphone User’s Guide Disclaimer Honeywell International Inc. (“HII”) reserves the right to make changes in specifications and other information contained in this document without prior notice, and the reader should in all cases consult HII to determine whether any such changes have been made. The information in this publication does not represent a commitment on the part of HII. HII shall not be liable for technical or editorial errors or omissions contained herein; nor for incidental or consequential damages resulting from the furnishing, performance, or use of this material. This document contains proprietary information that is protected by copyright. All rights are reserved. No part of this document may be photocopied, reproduced, or translated into another language without the prior written consent of HII. © 2011 Honeywell International Inc. All rights reserved. Microsoft® Windows®, Windows NT®, Windows 2000, Windows ME, Windows XP, Windows Vista, Windows .NET Framework, Windows ActiveSync®, and the Windows logo are trademarks or registered trademarks of Microsoft Corporation. The Bluetooth® word mark and logos are owned by Bluetooth SIG, Inc. Other product names or marks mentioned in this document may be trademarks or registered trademarks of other companies and are the property of their respective owners. Web Address: www.honeywellaidc.com Table of Contents Chapter 1 - Introduction Dolphin Power Tools Overview............................................................................................1-1 -

A Baseline for XP Boot Changes AAFS - 26 February 2010
A Baseline for XP Boot Changes AAFS - 26 February 2010 Ben Livelsberger NIST Information Technology Laboratory CFTT Project 1 Certain trade names and company products are mentioned in the text or identified. In no case does such identification imply recommendation or endorsement by the National Institute of Standards and Technology, nor does it imply that the products are necessarily the best available for the purpose. 2 Introduction Methodology/Approach Expected Results Analysis/Findings Conclusion 3 Question: What changes on a hard drive when you boot a system? Answer: Sector content of installed devices containing volumes Accessed, write, created date and time metadata Files created Files deleted 4 Build Vanilla XP system not networked Cycle through several boots and shutdowns Image with dd Boot, 2 minutes idle, shutdown, and reimage (5x) Compare images- Linux & perl Analyze differences- perl scripts and SleuthKit Tools 5 Build (vanilla) XP system DCO drive to 12 GB Partitioned 7 GB primary FAT32 2 GB secondary NTFS & 2 GB secondary FAT32 Windows XP Professional SP2 Add user files to secondary partitions 5 files - 2.4 Mb Types: .inf, .pdf, .exe, .ico, & .html 6 2.1 GB secondary NTFS partition.Payload 898,594 of 5 files copied from bootable CD (a 43 unallocated byte autorun.inf, a 17 Kb .pdf, a 2.4 sectors 7.3 GB FAT32 Mb .exe, a 13 Kb .ico, & a 13 Kb .html MBR (boot code, boot partition file). partition table, with XP SP2 Primary extended signature value) installed 2.1 GB secondary partition table + Secondary + 62 sectors) FAT32 partition. 62 sectors) extended partition table + Payload same as 62 sectors) NTFS partition Primary extended Secondary extended partition 7 partition 2.1 GB secondary NTFS partition.Payload of 5 files copied from bootable CD (a 43 byte autorun.inf, a 17 Kb .pdf, a 2.4 7.3 GB FAT32 Mb .exe, a 13 Kb .ico, & a 13 Kb .html boot partition file). -

GV-3D1-7950-RH Geforce™ 7950 GX2 Graphics Accelerator
GV-3D1-7950-RH GeForce™ 7950 GX2 Graphics Accelerator User's Manual Rev. 101 12MD-3D17950R-101R * The WEEE marking on the product indicates this product must not be disposed of with user's other household waste and must be handed over to a designated collection point for the recycling of waste electrical and electronic equipment!! * The WEEE marking applies only in European Union's member states. Copyright © 2006 GIGABYTE TECHNOLOGY CO., LTD Copyright by GIGA-BYTE TECHNOLOGY CO., LTD. ("GBT"). No part of this manual may be reproduced or transmitted in any form without the expressed, written permission of GBT. Trademarks Third-party brands and names are the property of their respective owners. Notice Please do not remove any labels on VGA card, this may void the warranty of this VGA card. Due to rapid change in technology, some of the specifications might be out of date before publication of this booklet. The author assumes no responsibility for any errors or omissions that may appear in this document nor does the author make a commitment to update the information contained herein. Macrovision corporation product notice: This product incorporates copyright protection technology that is protected by U.S. patents and other intellectual property rights. Use of this copyright protection technology must be authorized by Macrovision, and is intended for home and other limited viewing uses only unless otherwise authorized by Macrovision. Reverse engineering or disassembly is prohibited. Table of Contents English 1. Introduction ......................................................................................... 3 1.1. Features ..................................................................................................... 3 1.2. Minimum system requirements ..................................................................... 3 2. Hardware Installation ........................................................................... 4 2.1. -

Vista System Restore Rootkit
VViissttaa ssyysstteemm rreessttoorree rroooottkkitit Principle and protection EEdwdwaardrd SSunun PDF created with pdfFactory Pro trial version www.pdffactory.com AAbouboutt sspeapeakkerer u Network ID : CardMagic u Author of DarkSpy anti-rootkit u Posted several articles on rootkit.com u R&D of some world famous kernel level products in global companies u Experienced in Windows kernel mode research and programming u Now is a researcher of Trend Micro threat solution team PDF created with pdfFactory Pro trial version www.pdffactory.com WhaWhatt wwillill bebe iinnttrroduoducceded u Internals of Vista system restore u A user-mode rootkit to hide arbitrary file or registry key from Windows Vista system restore u A new way to bypass modern HIPS u Detection and protection of the threat PDF created with pdfFactory Pro trial version www.pdffactory.com AAgendagenda u Vista system restore (VSR) introduction u VSR internals u VSR rootkit u A new way to bypass HIPS u Protect & detect VSR u Demo PDF created with pdfFactory Pro trial version www.pdffactory.com VViissttaa ssyysstteemm rreessttoorree ((VSVSR)R) iinnttrrododuuccttiionon u VSR allows user to use restore point to return their system files and settings to an earlier point in time u System restore in Vista has been enhanced a lot and use new architecture & implementation which is different from XP’s u System Restore can make changes to Windows system files, registry settings, and programs installed on your computer. It also can make changes to scripts, batch files, and other types of executable files on your computer PDF created with pdfFactory Pro trial version www.pdffactory.com VSVSRR iinntteerrnnaalsls u But how does VSR work? Microsoft hasn’t provided detail document about how it works . -

Table of Contents
TABLE OF CONTENTS Installation & Setup . 2 The Story So Far . 4 It’s a Big World Out There . 5 Create a Profile . 6 Pause Menu . 6 Play Both Sides . 9 General Information . .13 Gameplay Tips . .16 Credits . .17 Customer Support . .19 Software License Agreement . .20 1 INSTALLATION & SETUP AUTOPLAY If the Windows Autoplay feature is enabled on your computer, the splash screen will begin when you insert the Ultimate Spider-Man™ CD 1 into your CD-ROM drive. On the splash screen, press Install and follow the on-screen instructions to continue the installation. Note: The Ultimate Spider-Man™ CD 1 functions as the CD key. You must have CD 1 in your CD-ROM drive to play the game. If the Autoplay feature is disabled, you can begin the installation by doing the following: a. Go to the Start Menu and select Run. b. Type D:\SETUP.EXE (assuming D is your CD-ROM drive letter) and press Enter. -or- a. Double-click on My Computer b. Double-Click your CD-ROM drive icon. c. Double-click on SETUP.EXE. 2 DIRECTX® 9.0C During the Ultimate Spider-Man™ typical install setup, the install process will automatically detect DirectX® 9.0c on your computer. If it’s not already installed, Microsoft® DirectX® 9.0c will be installed on your computer. DirectX® 9.0c is a set of sound, video, input and network functions developed by Microsoft. DirectX® 9.0c is necessary to run Ultimate Spider-Man™. It’s recommended that you choose to update to the newest version of DirectX®.