Dataton Watchout Windows 10 Enterprise Tweaking Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The NT Insider May-June 2016
; The commandments of x64 assembly: ; ; 1. Thou Shalt Not Write Inline Assembly ; 2. Thou Shalt Generate Unwind Data ; 3. Thou Shalt Comment Each Line of Assembly ; include macamd64.inc ; ; External C function to read an article ; ; NTSTATUS ; TheNTInsiderReadSingleArticle( ; PCHAR ArticleDescription, ; ULONG_PTR PageNumber, ; ); ; EXTERN TheNTInsiderReadSingleArticle:PROC .DATA PeterPontificates BYTE "COMPUTER SCIENCE EDUCATION? (YUP, STILL SUCKS)", 0 NewWaysToConnect BYTE "INTRODUCTION TO SIMPLE PERIPHERAL BUS DEVICES AND DRIVERS", 0 TipsForUsingIoTargets BYTE "A FEW RULES TO MAKE YOUR USE OF I/O TARGETS SIMPLE", 0 TodayInDriverSigning BYTE "COLOR ME CONFUSED (STILL. AGAIN.)", 0 AnalystsPerspective BYTE "MY DRIVER PASSES DRIVER VERIFIER! (OR DOES IT…)", 0 ByeByeCoInstallers BYTE "SURPRISE? NEW VERSIONS OF WDF NO LONGER SUPPORTED DOWNLEVEL", 0 .CODE NESTED_ENTRY TheNTInsiderReadEntireIssue, _TEXT save_reg rcx, 8h ; Home RCX save_reg rdx, 10h ; Home RDX save_reg r8, 18h ; Home R8 save_reg r9, 20h ; Home R9 alloc_stack 20h ; Make home space for TheNTInsiderReadSingleArticle END_PROLOGUE ; We are done manipulating the stack, so emit the ; appropriate unwind stuff lea rcx, [PeterPontificates] ; We're about to read the first article mov rdx, 4 ; Put page number in RDX. I realize this comment ; isn't useful, but I'm supposed to comment every ; line... call TheNTInsiderReadSingleArticle ; Read the article! test eax, eax ; Returns an NTSTATUS, so check SF js Exit ; If it's set there's an error and we need to leave lea rcx, [NewWaysToConnect] ; Time for the second article! mov rdx, 6 ; Do what I did last time call TheNTInsiderReadSingleArticle ; Read the next article! test eax, eax ; Testin'... js Exit ; And jumpin'... A publication of OSR Open Systems Resources, Inc. Resources, Systems Open OSR of A publication lea rcx, [TipsForUsingIoTargts] ; Let's read another article! mov rdx, 8 ; TODO: Learn to write a MASM loop.. -

Semi-Automated Parallel Programming in Heterogeneous Intelligent Reconfigurable Environments (SAPPHIRE) Sean Stanek Iowa State University
Iowa State University Capstones, Theses and Graduate Theses and Dissertations Dissertations 2012 Semi-automated parallel programming in heterogeneous intelligent reconfigurable environments (SAPPHIRE) Sean Stanek Iowa State University Follow this and additional works at: https://lib.dr.iastate.edu/etd Part of the Computer Sciences Commons Recommended Citation Stanek, Sean, "Semi-automated parallel programming in heterogeneous intelligent reconfigurable environments (SAPPHIRE)" (2012). Graduate Theses and Dissertations. 12560. https://lib.dr.iastate.edu/etd/12560 This Dissertation is brought to you for free and open access by the Iowa State University Capstones, Theses and Dissertations at Iowa State University Digital Repository. It has been accepted for inclusion in Graduate Theses and Dissertations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. Semi-automated parallel programming in heterogeneous intelligent reconfigurable environments (SAPPHIRE) by Sean Stanek A dissertation submitted to the graduate faculty in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Major: Computer Science Program of Study Committee: Carl Chang, Major Professor Johnny Wong Wallapak Tavanapong Les Miller Morris Chang Iowa State University Ames, Iowa 2012 Copyright © Sean Stanek, 2012. All rights reserved. ii TABLE OF CONTENTS LIST OF TABLES ..................................................................................................................... -

The Downadup Codex a Comprehensive Guide to the Threat’S Mechanics
Security Response The Downadup Codex A comprehensive guide to the threat’s mechanics. Edition 2.0 Introduction Contents Introduction.............................................................1 Since its appearance in late-2008, the Downadup worm has become Editor’s Note............................................................5 one of the most wide-spread threats to hit the Internet for a number of Increase in exploit attempts against MS08-067.....6 years. A complex piece of malicious code, this threat was able to jump W32.Downadup infection statistics.........................8 certain network hurdles, hide in the shadows of network traffic, and New variants of W32.Downadup.B find new ways to propagate.........................................10 defend itself against attack with a deftness not often seen in today’s W32.Downadup and W32.Downadup.B threat landscape. Yet it contained few previously unseen features. What statistics................................................................12 set it apart was the sheer number of tricks it held up its sleeve. Peer-to-peer payload distribution...........................15 Geo-location, fingerprinting, and piracy...............17 It all started in late-October of 2008, we began to receive reports of A lock with no key..................................................19 Small improvements yield big returns..................21 targeted attacks taking advantage of an as-yet unknown vulnerability Attempts at smart network scanning...................23 in Window’s remote procedure call (RPC) service. Microsoft quickly Playing with Universal Plug and Play...................24 released an out-of-band security patch (MS08-067), going so far as to Locking itself out.................................................27 classify the update as “critical” for some operating systems—the high- A new Downadup variant?......................................29 Advanced crypto protection.................................30 est designation for a Microsoft Security Bulletin. -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Guidelines for Designing Embedded Systems with Windows 10 Iot Enterprise
Guidelines for Designing Embedded Systems with Windows 10 IoT Enterprise Version 2.0 Published July 15, 2016 Guidelines for designing embedded systems 1 CONFIDENTIAL Contents Overview .................................................................................................................................................................................................... 4 Building a task-specific experience ............................................................................................................................................ 4 General Group Policy settings ....................................................................................................................................................... 4 Application control ................................................................................................................................................................................ 5 Application boot options ................................................................................................................................................................. 5 Auto-boot Universal Windows apps ...................................................................................................................................... 5 Auto-boot Classic Windows apps ........................................................................................................................................... 5 Limit application access with AppLocker ............................................................................................................................... -

Inside Windows 10 - an Early Look at Microsoft’S Newest Operating System Volume 1 - by Onuora Amobi
0 www.windows10update.com – Comprehensive Windows 10 News Copyright Notice INSIDE WINDOWS 10 - AN EARLY LOOK AT MICROSOFT’S NEWEST OPERATING SYSTEM VOLUME 1 - BY ONUORA AMOBI ©2015 Nnigma Inc. All rights reserved. Any unauthorized use, sharing, reproduction or distribution of these materials by any means, electronic, mechanical, or otherwise is strictly prohibited. No portion of these materials may be reproduced in any manner whatsoever, without the express written consent of the Publisher or Author. Published under the Copyright Laws of The United States of America by: Nnigma Inc. 3579 East Foothill Blvd, Suite #254 Pasadena, CA 91107 www.Nnigma.com i www.windows10update.com – Comprehensive Windows 10 News Legal Notice While all attempts have been made to verify information provided in this publication, neither the author nor the publisher assumes any responsibility for errors, omissions or contradictory interpretation of the subject matter herein. This publication is not intended to be used as a source of binding technical, technological, legal or accounting advice. Please remember that the information contained may be subject to varying state and/or local laws or regulations that may apply to the user’s particular practice. The purchaser or reader of this publication assumes responsibility for the use of these materials and information. Adherence to all applicable laws and regulations, both federal, state, and local, governing professional licensing, business practices, advertising and any other aspects of doing business in the US or any other jurisdiction is the sole responsibility of the purchaser or reader. Nnigma Inc. assumes no responsibility or liability whatsoever on behalf of any purchaser or reader of these materials. -
![[MS-ERREF]: Windows Error Codes](https://docslib.b-cdn.net/cover/7109/ms-erref-windows-error-codes-437109.webp)
[MS-ERREF]: Windows Error Codes
[MS-ERREF]: Windows Error Codes Intellectual Property Rights Notice for Open Specifications Documentation . Technical Documentation. Microsoft publishes Open Specifications documentation for protocols, file formats, languages, standards as well as overviews of the interaction among each of these technologies. Copyrights. This documentation is covered by Microsoft copyrights. Regardless of any other terms that are contained in the terms of use for the Microsoft website that hosts this documentation, you may make copies of it in order to develop implementations of the technologies described in the Open Specifications and may distribute portions of it in your implementations using these technologies or your documentation as necessary to properly document the implementation. You may also distribute in your implementation, with or without modification, any schema, IDL's, or code samples that are included in the documentation. This permission also applies to any documents that are referenced in the Open Specifications. No Trade Secrets. Microsoft does not claim any trade secret rights in this documentation. Patents. Microsoft has patents that may cover your implementations of the technologies described in the Open Specifications. Neither this notice nor Microsoft's delivery of the documentation grants any licenses under those or any other Microsoft patents. However, a given Open Specification may be covered by Microsoft Open Specification Promise or the Community Promise. If you would prefer a written license, or if the technologies described in the Open Specifications are not covered by the Open Specifications Promise or Community Promise, as applicable, patent licenses are available by contacting [email protected]. Trademarks. The names of companies and products contained in this documentation may be covered by trademarks or similar intellectual property rights. -

Ultimate Spider-Man™ README Last Updated: 6/28/05
Ultimate Spider-Man™ README Last Updated: 6/28/05 TABLE OF CONTENTS INTRODUCTION INSTALLATION & SET UP 1. Minimum System Requirements 2. Autoplay 3. DirectX(R) Detection & Installation VIDEO ISSUES 1. Monitors 2. In-game and Desktop Resolutions 3. Graphical Corruption When Changing Video Settings 4. Windowed Mode/Standby Mode 5. Changing Brightness and Contrast GENERAL ISSUES 1. Alt-Tab & Alt-Enter 2. Uninstalling with Antivirus Software Enabled 3. Gamepad Options 4. Invert Controls Setting 5. Options for Lower End Systems INTRODUCTION Refer to this document if you encounter difficulties with one or more aspects of installation or running the Ultimate Spider-Man™ game. Many of the most commonly encountered issues are covered here. INSTALLATION & SET UP 1. Ultimate Spider-Man™ Minimum System Requirements • 3D hardware accelerator card required - 100% DirectX(R) 9.0c-compliant 64 MB video card and drivers* • Microsoft(R) Windows(R) 2000/XP • Pentium(R) III 1.2 GHz or Athlon(TM) 1.2 GHz or higher processor • 256 MB of RAM • 3500 MB of uncompressed hard disk space (plus 400 MB for the Windows(R) swap file) • A 100% Windows(R) 2000/XP - compatible computer system including: • DirectX(R) 9.0c (Included) • 100% DirectX(R) 9.0c-compliant true 16-bit sound card and drivers • 100% Windows(R) 2000/XP - compatible mouse, keyboard and drivers • 100% Windows(R) 2000/XP - compatible quad speed CD-ROM drive (600 K/sec sustained transfer rate) and drivers *Supported Chipsets for Windows 2000/XP All NVIDIA(R) GeForce2(TM) and better chipsets All ATI(R) Radeon 7500(TM) and better chipsets *Important Note: Some 3D accelerator cards with the chipsets listed here may not be compatible with the 3D acceleration features utilized by Ultimate Spider-Man™. -

Critical Vulnerabilities Bulletin
January 18th, 2021 Critical Vulnerabilities Bulletin Confidential | Cyberint Copyright © All Rights Reserved 2020 CRITICAL VULNERABILITIES BULLETIN | INDUSTRY SECURITY BULLETIN JANUARY 14, 2021 EXECUTIVE SUMMARY Due to an unusual increase in Critical vulnerabilities found on Windows operating systems, Cyberint's Research Team has decided to release this bulletin to alert our customers of the potential impact. This bulletin will be expanded at the end of the month, as part of the Monthly Vulnerability bulletin we plan on releasing. The reason for this bulletin lies at 2 newly discovered vulnerabilities: 1. <No CVE assigned yet> - Corrupt NTFS OS partition without user interaction. 2. <No CVE assigned yet> - Trigger a BSOD by trying to access a system path. 3. CVE-2020-1398 - Potential bypass of Bitlocker protected systems, including Lock Screen bypass. We suspect that threat actors and updated malware may attempt to exploit these vulnerabilities to further impact potential victims. Confidential | Cyberint Copyright © All Rights Reserved 2020 2 CRITICAL VULNERABILITIES BULLETIN | INDUSTRY SECURITY BULLETIN JANUARY 14, 2021 NTFS CORRUPTION VULNERABILITY Published by a known vulnerability researcher, jonasLyk, it is possible to cause disk partition corruption by executing a cd command as a low privilege user, to a unique path, which causes the Windows Operating System to alert the user to a corrupted partition and force a restart. Whilst technical details are scarce, and the exact reason for the issue being unknown at this time, affected Windows builds using the NTFS file system include those from 1803 all the way to 20H2. According to SANS, the $bitmap is an attribute reserved for files marked as deleted, while $i30 is marked as an NTFS index attribute. -

Jim Allchin on Longhorn, Winfs, 64-Bit and Beyond Page 34 Jim
0805red_cover.v5 7/19/05 2:57 PM Page 1 4 Scripting Solutions to Simplify Your Life Page 28 AUGUST 2005 WWW.REDMONDMAG.COM MrMr WindowsWindows Jim Allchin on Longhorn, WinFS, 64-Bit and Beyond Page 34 > $5.95 05 • AUGUST Make Room for Linux Apps Page 43 25274 867 27 Active Directory Design Disasters Page 49 71 Project1 6/16/05 12:36 PM Page 1 Exchange Server stores & PSTs driving you crazy? Only $399 for 50 mailboxes; $1499 for unlimited mailboxes! Archive all mail to SQL and save 80% storage space! Email archiving solution for internal and external email Download your FREE trial from www.gfi.com/rma Project1 6/16/05 12:37 PM Page 2 Get your FREE trial version of GFI MailArchiver for Exchange today! GFI MailArchiver for Exchange is an easy-to-use email archiving solution that enables you to archive all internal and external mail into a single SQL database. Now you can provide users with easy, centralized access to past email via a web-based search interface and easily fulfill regulatory requirements (such as the Sarbanes-Oxley Act). GFI MailArchiver leverages the journaling feature of Exchange Server 2000/2003, providing unparalleled scalability and reliability at a competitive cost. GFI MailArchiver for Exchange features Provide end-users with a single web-based location in which to search all their past email Increase Exchange performance and ease backup and restoration End PST hell by storing email in SQL format Significantly reduce storage requirements for email by up to 80% Comply with Sarbanes-Oxley, SEC and other regulations. -

Microsoft Directshow: a New Media Architecture
TECHNICAL PAPER Microsoft Directshow: A New Media Architecture By Amit Chatterjee and Andrew Maltz The desktop revolution in production and post-production has dramatical- streaming. Other motivating factors are ly changed the way film and television programs are made, simultaneously the new hardware buses such as the reducing equipment costs and increasing operator eficiency. The enabling IEEE 1394 serial bus and Universal digital innovations by individual companies using standard computing serial bus (USB), which are designed with multimedia devices in mind and platforms has come at a price-these custom implementations and closed promise to enable broad new classes of solutions make sharing of media and hardware between applications difi- audio and video application programs. cult if not impossible. Microsoft s DirectShowTMStreaming Media To address these and other require- Architecture and Windows Driver Model provide the infrastructure for ments, Microsoft introduced Direct- today’s post-production applications and hardware to truly become inter- ShowTM, a next-generation media- operable. This paper describes the architecture, supporting technologies, streaming architecture for the and their application in post-production scenarios. Windows and Macintosh platforms. In development for two and a half years, Directshow was released in August he year 1989 marked a turning Additionally, every implementation 1996, primarily as an MPEG-1 play- Tpoint in post-production equip- had to fight with operating system back vehicle for Internet applications, ment design with the introduction of constraints and surprises, particularly although the infrastructure was desktop digital nonlinear editing sys- in the areas of internal stream synchro- designed with a wide range of applica- tems. -
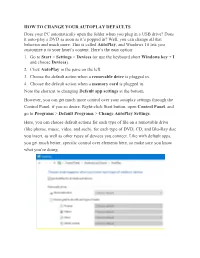
HOW to CHANGE YOUR AUTOPLAY DEFAULTS Does Your PC Automatically Open the Folder When You Plug in a USB Drive? Does It Auto-Play
HOW TO CHANGE YOUR AUTOPLAY DEFAULTS Does your PC automatically open the folder when you plug in a USB drive? Does it auto-play a DVD as soon as it’s popped in? Well, you can change all that behavior and much more. This is called AutoPlay, and Windows 10 lets you customize it to your heart’s content. Here’s the easy option: 1. Go to Start > Settings > Devices (or use the keyboard short Windows key + I and choose Devices). 2. Click AutoPlay in the pane on the left. 3. Choose the default action when a removable drive is plugged in. 4. Choose the default action when a memory card is plugged in. Note the shortcut to changing Default app settings at the bottom. However, you can get much more control over your autoplay settings through the Control Panel, if you so desire. Right-click Start button, open Control Panel, and go to Programs > Default Programs > Change AutoPlay Settings. Here, you can choose default actions for each type of file on a removable drive (like photos, music, video, and such), for each type of DVD, CD, and Blu-Ray disc you insert, as well as other types of devices you connect. Like with default apps, you get much better, specific control over elements here, so make sure you know what you’re doing. If nothing else, you should definitely change what Windows does for flash drives, since auto-running files from flash or thumb drives is one of the easiest ways to get a malware infection. .