On the Horizon a Collection of Papers from the Next Generation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

समाचार पत्र से चियत अंश Newspapers Clippings
June 2020 समाचार पत्र से चियत अंश Newspapers Clippings A Daily service to keep DRDO Fraternity abreast with DRDO Technologies, Defence Technologies, Defence Policies, International Relations and Science & Technology Volume: 45 Issue: 1 1 June 2020 37 3 रक्षा िवज्ञान पुतकालय Defenceरक्षा िवज्ञान Science पुतकालय Library रक्षाDefence वैज्ञािनक सScienceूचना एवं प्रल Libraryेखन क द्र Defence Scientific Information & Documentation Centre रक्षा वैज्ञािनक सूचना एव ं प्रलेखन क द्र Defence Scientificमेटकॉफ Informationहाउस, िदली -& 110 Documentation 054 Centre Metcalfe House, Delhi - 110 054 मेटकॉफ हाउस, िदली - 110 054 Metcalfe House, Delhi- 110 054 CONTENT S.No. TITLE Page No. DRDO News 1-6 COVID-19: DRDO’s Contribution 1 1. डीआरडीओ ने पुिलस को दी वदीर् और सैिनटाइज मशीन 1 2. DRDO develops 'GermiKlean' to sanitise uniforms of police, security forces 2 DRDO Technology News 2-6 3. How the BrahMos missile has evolved since it was test fired for the first time on this 2 day in 2001 4. DRDO making plans to develop two jet engines? 4 5. Govt extends deadline for defence contracts for Indian vendors 5 Defence News 6-23 Defence Strategic National/International 6-23 6. Defence budget up by 11.9% amid tensions with India 6 7. Delayed Procurements will hurt India against China 7 8. Rajnath reviews situation in eastern Ladakh 8 9. India was alert to Chinese tactics, increased Army on Arunachal border, Army ready to 9 respond to every move of China 10. -

Ministry of Defence
21 STANDING COMMITTEE ON DEFENCE (2015-2016) (SIXTEENTH LOK SABHA) MINISTRY OF DEFENCE DEMANDS FOR GRANTS (2016-17) MINISTRY OF DEFENCE (MISCELLANEOUS) (DEMAND NO. 20) TWENTY-FIRST REPORT LOK SABHA SECRETARIAT NEW DELHI May, 2016/ Vaisakha, 1938 (Saka) 1 TWENTY-FIRST REPORT STANDING COMMITTEE ON DEFENCE (2015-2016) (SIXTEENTH LOK SABHA) MINISTRY OF DEFENCE DEMANDS FOR GRANTS (2016-2017) (MISCELLANEOUS) (DEMAND NO. 20) Presented to Lok Sabha on 03.05.2016 Laid in Rajya Sabha on 03.05.2016 LOK SABHA SECRETARIAT NEW DELHI May, 2016/ Vaisakha, 1938 (Saka) 2 CONTENTS Composition of the Committee (2015-16)………………………………………. Introduction ………………….……………………………………………………… PART - I Chapter I Ordnance Factory Board……………………...……………….….. Chapter II Defence Research and Development Organization …………… Chapter III Ex- Servicemen Contributory Health Scheme …………………. Chapter IV Directorate General Quality Assurance ……. …………………. Chapter V National Cadet Corps …………………………..…………………. PART – II OBSERVATIONS/RECOMMENDATIONS........................................... ANNEXURE ………………………………………………………….……... APPENDICES Minutes of the sitting of the Committee on Defence held on 4.4.2016, 5.4.2016, 6.04.2016 and 29.04.2016…………………………………………………………… 3 COMPOSITION OF THE STANDING COMMITTEE ON DEFENCE (2015-16) Maj Gen B C Khanduri, AVSM (Retd) - Chairperson Members Lok Sabha 2. Shri Suresh C. Angadi 3. Shri Shrirang Appa Barne 4. Shri Dharambir 5. Shri Thupstan Chhewang 6. Col Sonaram Choudhary(Retd) 7. Shri H.D. Devegowda 8. Shri Sher Singh Ghubaya 9. Shri G. Hari 10. Shri Ramesh Jigajinagi 11. Dr. Murli Manohar Joshi 12. Km. Shobha Karandlaje 13. Shri Vinod Khanna 14. Dr. Mriganka Mahato 15. Shri Tapas Paul 16. Shri Ch. Malla Reddy 17. Shri Rajeev Satav 18. Smt. Mala Rajya Lakshmi Shah 19. Capt Amarinder Singh(Retd) 20. -

ISODARCO Mansoor Ahmed 2019
ARMS CONTROL IN SOUTH ASIA: PROBLEMS AND PROSPECTS Mansoor Ahmed, PhD MTA Associate, Harvard Kennedy School’s Belfer Center & Senior Fellow, Center for International Strategic Studies, Islamabad Jan 11, 2019 ISODARCO 2019 Outline ■ The Power Differential in South Asia ■ Drivers and Impediments for Arms Control ■ Arms Race Trajectory ■ Lost Opportunities ■ Future Prospects The Structural Imbalance in South Asia Ø INDIA § Population $ 1.3 billion § GDP $ 2.69 trillion § Military Budget $ 56 billion Ø PAKISTAN § Population $ 210 million § GDP $ 304 billion § Military Budget $ 10 billion Drivers and Impediments for Arms Control ■ Unresolved Territorial Disputes ■ Role of External Powers – US-India Strategic Partnership – Russia-India Strategic Partnership – Pakistan-China Strategic Partnership Doctrinal Evolution in South Asia Ø INDIA Ø Minimum Credible Deterrence Ø Credible Minimum Deterrence Ø No First Use and Massive Retaliation Ø Full Spectrum Conflict and Splendid First Strike (Counterforce Option) Ø PAKISTAN Ø Minimum Credible Deterrence Ø Credible Minimum Deterrence Ø Full Spectrum Deterrence (60 km-2750 km) Doctrinal Evolution in South Asia ■ Conventional Military Doctrines: INDIA – Proactive Military Operations/Cold Start – Indian Army Land Warfare Doctrine 2018 ■ Minimum Escalation through existing Agreements and Protocols (LAC) with China ■ Operational ascendency to enhance punitive response options to greater depth, effect, sophistication and precision along (LOC) with Pakistan. ■ Full Spectrum Conflict ■ Conventional Military Doctrines: PAKISTAN – Comprehensive Response Doctrine PAKISTAN ARMY INDIAN ARMY Manpower 550,000 Manpower 1,150,900 Strike Corps 2 Strike Corps 3 Holding Corps 8 Holding Corps 10 Armor 2 Divs 2561 Tanks Armor 3 Divs 4312 Tanks 7 Indp. Bgde 320 T-80UD 1950 T-72 415 MBT-2000 8 Indp. -

Nuclearization of South Asia: Impacts on Regional Peace and Security Dr
Pakistan Social Sciences Review P-ISSN 2664-0422 September 2020, Vol. 4, No. III [1133-1148] O-ISSN 2664-0430 RESEARCH PAPER Nuclearization of South Asia: Impacts on Regional Peace and Security Dr. Zab-Un-Nisa 1 Gul-e-Zahra2 Syed Waqas Ali Bokhari 3 1. Assistant Professor, Department of Political Science, Govt. Graduate College Samanabad, Faisalabad, Punjab, Pakistan 2. Ph D Scholar, Department of Political Science & International Relations, Government College University, Faisalabad, Punjab, Pakistan 3. M. Phil. International Relations, Department of Political Science & International Relations, Government College University, Faisalabad, Punjab, Pakistan PAPER INFO ABSTRACT Received: The India and Pakistan conflict has suffered for six decades, a August 17, 2020 series of wars and crises design its course. The rapidly growing Accepted: Arms race among them poses a threat to regional stability in September 05, 2020 sense of Peace and security. Both states are entangled in a long- Online: standing security competition, most commonly globally September 30, 2020 recognized as a dispute the Kashmir is the nuclear war Keywords: Arms Race, flashpoint. There is a long timeline of armaments among both Kashmir, states since the partition. The security competition is an action- Nuclearization reaction spiral; this relationship is a classic example of a security Peace and Security, dilemma, whereby one state’s action causes insecurity to South Asian Stability, another. This security dilemma may lead to an Arms race among Corresponding two rivals. New Delhi often justifies its military builds-up postures China-centric but this is creating a security dilemma Author: among its neighboring countries especially in recent years Pakistan. -
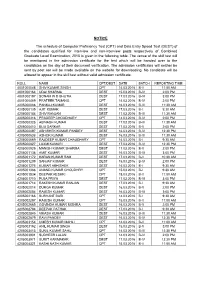
(DEST) of the Candidates Qualified for Interview and Non-Interview Posts Respectively of Combined Graduate Level Examination, 2015 Is Given in the Following Table
NOTICE The schedule of Computer Proficiency Test (CPT) and Data Entry Speed Test (DEST) of the candidates qualified for interview and non-interview posts respectively of Combined Graduate Level Examination, 2015 is given in the following table. The venue of the skill test will be mentioned in the admission certificate for the test which will be handed over to the candidates on the day of their document verification. The admission certificates will neither be sent by post nor will be made available on the website for downloading. No candidate will be allowed to appear in the skill test without valid admission certificate. ROLL NAME CPT/DEST DATE BATCH REPORTING TIME 4001000048 SHIV KUMAR SINGH CPT 14.03.2016 B-II 11:00 AM 4001000164 UDAI SHARMA DEST 15.03.2016 B-IV 2:00 PM 4001000197 SONAM W D BHUTIA DEST 17.03.2016 B-VI 3:00 PM 4001000459 PRATEEK TAMANG CPT 14.03.2016 B-IV 2:00 PM 4205000088 PANKAJ KUMAR DEST 16.03.2016 B-III 11:30 AM 4205000135 AJIT KUMAR DEST 17.03.2016 B-I 9:30 AM 4205000184 SHIV RANJAN DEST 17.03.2016 B-III 11:30 AM 4205000316 PRADEEP CHOUDHARY CPT 14.03.2016 B-IV 2:00 PM 4205000325 ABINASH KUMAR DEST 17.03.2016 B-III 11:30 AM 4205000410 BIJU SARKAR DEST 17.03.2016 B-V 2:00 PM 4205000497 ABHISHEK KUMAR PANDEY DEST 16.03.2016 B-IV 12:30 PM 4205000638 ASHOK KUMAR DEST 16.03.2016 B-III 11:30 AM 4205000669 RAJDEEP KUMAR CHAUDHARY CPT 14.03.2016 B-I 9:30 AM 4205000827 LAXMI KUMARI DEST 17.03.2016 B-IV 12:30 PM 4205000929 MANISH KUMAR SHARMA DEST 17.03.2016 B-V 2:00 PM 4205001138 AMIT KUMAR DEST 16.03.2016 B-VI 3:00 PM -

Pancha Maha Bhutas (Earth-Water-Fire-Air-Sky)
1 ESSENCE OF PANCHA MAHA BHUTAS (EARTH-WATER-FIRE-AIR-SKY) Compiled, composed and interpreted by V.D.N.Rao, former General Manager, India Trade Promotion Organisation, Pragati Maidan, New Delhi, Ministry of Commerce, Govt. of India, now at Chennai. Other Scripts by the same Author: Essence of Puranas:-Maha Bhagavata, Vishnu Purana, Matsya Purana, Varaha Purana, Kurma Purana, Vamana Purana, Narada Purana, Padma Purana; Shiva Purana, Linga Purana, Skanda Purana, Markandeya Purana, Devi Bhagavata;Brahma Purana, Brahma Vaivarta Purana, Agni Purana, Bhavishya Purana, Nilamata Purana; Shri Kamakshi Vilasa Dwadasha Divya Sahasranaama: a) Devi Chaturvidha Sahasra naama: Lakshmi, Lalitha, Saraswati, Gayatri; b) Chaturvidha Shiva Sahasra naama-Linga-Shiva-Brahma Puranas and Maha Bhagavata; c) Trividha Vishnu and Yugala Radha-Krishna Sahasra naama-Padma-Skanda-Maha Bharata and Narada Purana. Stotra Kavacha- A Shield of Prayers -Purana Saaraamsha; Select Stories from Puranas Essence of Dharma Sindhu - Dharma Bindu - Shiva Sahasra Lingarchana-Essence of Paraashara Smriti Essence of Pradhana Tirtha Mahima Essence of Upanishads : Brihadaranyaka , Katha, Tittiriya, Isha, Svetashwara of Yajur Veda-Chhandogya and Kena of Saama Veda-Atreya and Kausheetaki of Rig Veda-Mundaka, Mandukya and Prashna of Atharva Veda ; Also ‗Upanishad Saaraamsa‘ (Quintessence of Upanishads) Essence of Virat Parva of Maha Bharata- Essence of Bharat Yatra Smriti Essence of Brahma Sutras Essence of Sankhya Parijnaana- Also Essence of Knowledge of Numbers Essence of Narada Charitra; Essence Neeti Chandrika-Essence of Hindu Festivals and Austerities Essence of Manu Smriti- Quintessence of Manu Smriti- Essence of Paramartha Saara; Essence of Pratyaksha Bhaskra; Essence of Maha Narayanopashid; Essence of Maitri Upanishad Essence of Vidya-Vigjnaana-Vaak Devi; Essence of Bhagya -Bhogya-Yogyata Lakshmi Essence of Soundarya Lahari*- Essence of Popular Stotras*- Essence of Pratyaksha Chandra*- Essence of Pancha Bhutas* Note: All the above Scriptures already released on www. -

HIGH COURT, CALCUTTA APPELLATE SIDE N O T I F I C a T I O N This Is Relating to Recruitment to the Posts of P.A. / Stenographer
HIGH COURT, CALCUTTA APPELLATE SIDE N O T I F I C A T I O N Memo No. 2188 R (Recruitment) Dated, Calcutta, the 11th May, 2018 This is relating to recruitment to the posts of P.A. / Stenographer, Grade-C, 2018 at High Court, Calcutta in terms of Court’s Employment st Notification No. 695 RG dated 21 February, 2018. The candidates whose applications are “in order” are mentioned in List –A. The candidates who had not submitted the required amount of IPO with their applications and whose applications are otherwise ‘in order’ be directed to submit the required amount of IPO in the office of the Registrar (Recruitment & Management) on May 24, 2018 and May 25, 2018 between 12 noon and 4.30 pmin and original collect their Admit Cards on production of any Photo Identity proof . The candidates whose applications are “disqualified” are mentioned in List-B. The candidates whose applications are “partially qualified” (List-C), may cure the defect(s) of their applications by complying with the requirements as demanded in the Employment Notification No. 695 RG dated 21.2.2018, on June 4, 2018 and June 5, 2018 between 12 noon and 4.30 pm from the office of the Registrar (Recruitment & Management) and in collectoriginal. their Admit Cards on production of any Photo Identity proof In respect of the candidates in the group “partially qualified” (List-C), the defects are indicated in the “modalities of scrutiny” list (List-D). Sd/- Registrar (Recruitment & Management), A.S, High Court, Calcutta. LIST- A (IN ORDER) Sl. -

Radioactive Masculinity: How the Anxious Postcolonial Learnt to Love and Live in Fear of the Nuclear Bomb
Graduate Theses, Dissertations, and Problem Reports 2016 Radioactive masculinity: How the anxious postcolonial learnt to love and live in fear of the nuclear bomb Dibyadyuti Roy Follow this and additional works at: https://researchrepository.wvu.edu/etd Recommended Citation Roy, Dibyadyuti, "Radioactive masculinity: How the anxious postcolonial learnt to love and live in fear of the nuclear bomb" (2016). Graduate Theses, Dissertations, and Problem Reports. 6536. https://researchrepository.wvu.edu/etd/6536 This Dissertation is protected by copyright and/or related rights. It has been brought to you by the The Research Repository @ WVU with permission from the rights-holder(s). You are free to use this Dissertation in any way that is permitted by the copyright and related rights legislation that applies to your use. For other uses you must obtain permission from the rights-holder(s) directly, unless additional rights are indicated by a Creative Commons license in the record and/ or on the work itself. This Dissertation has been accepted for inclusion in WVU Graduate Theses, Dissertations, and Problem Reports collection by an authorized administrator of The Research Repository @ WVU. For more information, please contact [email protected]. RADIOACTIVE MASCULINITY: HOW THE ANXIOUS POSTCOLONIAL LEARNT TO LOVE AND LIVE IN FEAR OF THE NUCLEAR BOMB Dibyadyuti Roy Dissertation submitted to the Eberly College of Arts and Sciences at West Virginia University in partial fulfillment of the requirements for the degree of Doctor of Philosophy in English Literature Ryan Claycomb, Ph.D., Chair Dennis Allen, Ph.D. Charles Baldwin, Ph.D. Brian Ballentine, Ph.D. Patrick Sharp, Ph.D. -

Ordnance Factories, Defence Research and Development Organisation, Directorate General of Quality Assurance and National Cadet Corps
30 STANDING COMMITTEE ON DEFENCE (2016-2017) (SIXTEENTH LOK SABHA) MINISTRY OF DEFENCE DEMANDS FOR GRANTS (2017-18) ORDNANCE FACTORIES, DEFENCE RESEARCH AND DEVELOPMENT ORGANISATION, DIRECTORATE GENERAL OF QUALITY ASSURANCE AND NATIONAL CADET CORPS (DEMAND NO. 20) THIRTIETH REPORT LOK SABHA SECRETARIAT NEW DELHI March, 2017 / Phalguna, 1938 (Saka) THIRTIETH REPORT STANDING COMMITTEE ON DEFENCE (2016-2017) (SIXTEENTH LOK SABHA) MINISTRY OF DEFENCE DEMANDS FOR GRANTS (2017-18) ORDNANCE FACTORIES, DEFENCE RESEARCH AND DEVELOPMENT ORGANISATION, DIRECTORATE GENERAL OF QUALITY ASSURANCE AND NATIONAL CADET CORPS (DEMAND NO. 20) Presented to Lok Sabha on 09 .03.2017 Laid in Rajya Sabha on .03.2017 LOK SABHA SECRETARIAT NEW DELHI March, 2017 / Phalguna, 1938 (Saka) CONTENTS PAGE COMPOSITION OF THE COMMITTEE (2016-17)………………………………….(iii) INTRODUCTION ……………………………………………………………………….(v) REPORT PART I Chapter I Ordnance Factories Board .......................................................... Chapter II Defence Research and Development Organisation.................. Chapter III Directorate General of Quality Assurance................................. Chapter IV National Cadet Corps................................................................ PART II Observations/Recommendations....................................................................... APPENDICES Minutes of the Sitting of the Standing Committee on Defence (2016-17) held on 22.02.2017, 23.02.2017 and 03.03.2017………………………………………… COMPOSITION OF THE STANDING COMMITTEE ON DEFENCE ( 2016-17 ) Maj Gen B C Khanduri, AVSM (Retd) - Chairperson Lok Sabha 2. Shri Dipak Adhikari (Dev) 3. Shri Suresh C Angadi 4. Shri Shrirang Appa Barne 5. Shri Thupstan Chhewang 6. Col Sonaram Choudhary(Retd) 7. Shri H D Devegowda 8. Shri Sher Singh Ghubaya 9.* Shri B. Senguttuvan 10. Dr Murli Manohar Joshi 11. Km Shobha Karandlaje 12. Shri Vinod Khanna 13. Dr Mriganka Mahato 14. Shri Rodmal Nagar 15. Shri A P Jithender Reddy 16. -
139 16 June 2020
June 2020 समाचार पत्र से चियत अंश Newspapers Clippings A Daily service to keep DRDO Fraternity abreast with DRDO Technologies, Defence Technologies, Defence Policies, International Relations and Science & Technology Volume: 45 Issue: 1 1 June 2020 39 6 रक्षा िवज्ञान पुतकालय Defenceरक्षा िवज्ञान Science पुतकालय Library रक्षाDefence वैज्ञािनक सScienceूचना एवं प्रल Libraryेखन क द्र Defence Scientific Information & Documentation Centre रक्षा वैज्ञािनक सूचना एव ं प्रलेखन क द्र Defence Scientificमेटकॉफ Informationहाउस, िदली -& 110 Documentation 054 Centre Metcalfe House, Delhi - 110 054 मेटकॉफ हाउस, िदली - 110 054 Metcalfe House, Delhi- 110 054 CONTENT S.No. TITLE Page No. DRDO News 1-4 COVID-19: DRDO’s Contribution 1 1. This biodegradable mask resists pathogens, and has the goodness of neem, turmeric & 1 basil 2. Battle against coronavirus: Low-cost ventilators made using Skanray-DRDO 2 technologies 3. Assam completes 2.17 lakh Covid19 tests: Himanta 3 DRDO Technology News 4-6 4. BrahMos becomes first desi missile to receive fleet release clearance 4 Defence News 6-20 Defence Strategic National/International 6-20 5. China border faceoff may take time to ease 6 6. LAC talks on, but Army told to act as per need 8 7. Chinese tanks conduct high-altitude drills amid border standoff with India 9 8. China started expanding its legs to the Indian Ocean, a bigger concern of India than 10 LAC 9. China turned down proposal to demarcate LAC for 174 yrs 11 10. India, China increased nuclear weapons since last year: SIPRI 12 11. -

Ministry of Defence
NINTH REPORT STANDING COMMITTEE ON DEFENCE (2014-2015) (SIXTEENTH LOK SABHA) MINISTRY OF DEFENCE DEMANDS FOR GRANTS (2015-2016) ORDNANCE FACTORIES AND DEFENCE RESEARCH AND DEVELOPMENT ORGANISATION (DEMAND NO. 26 & 27) Presented to Lok Sabha on 27.04.2015 Laid in Rajya Sabha on 27.04.2015 LOK SABHA SECRETARIAT NEW DELHI April, 2015/Vaisakha, 1937 (Saka) C.O.D. No. 145 Price : R 100.00 © 2015 BY LOK SABHA SECRETARIAT Published under Rule 382 of the Rules of Procedure and Conduct of Business in Lok Sabha (Fifteenth Edition) and printed by Jainco Art India, New Delhi-110 005. CONTENTS PAGE COMPOSITION OF THE COMMITTEE (2014-15) ................................ (iii) INTRODUCTION ................................................................. (v) PART I CHAPTER I Ordnance Factories ........................................ 1 CHAPTER II Defence Research and Development Organisation... 17 PART II Recommendations/Observations ......................... 41 ANNEXURES A. Details of major ongoing projects (Cost above Rs. 100 crore) with name of project, developing agency/lab, date of sanction, original estimated cost, likely date of completion, revised cost and revised date of completion of the project .................................... 53 B. Details of major projects (Cost more than Rs. 100 crore) sanctioned during 10th FYP (01 Apr. 2002 to 31 Mar. 2007) along with date of sanction, sanctioned cost and status of projects ....................................................... 58 APPENDICES Minutes of the sitting of the Committee on Defence held on 23.03.2015, 24.03.2015, 25.03.2015, 06.04.2015 & 24.04.2015 ....................................................... 63 (i) COMPOSITION OF THE STANDING COMMITTEE ON DEFENCE (2014-15) Maj Gen B C Khanduri, AVSM (Retd) — Chairperson MEMBERS Lok Sabha 2. Shri Suresh C. Angadi 3. Shri Shrirang Appa Barne 4. -

Essence of Pratyaksha Bhaskara ( P 223-235)
ESSENCE OF PRATYAKSHA BHASKAR (References- Part I: Puranas; Part II: Upanishads; Part III: from Vedas; Part IV: other Sources) Edited and translated by V.D.N.Rao, Retd. General Manager of India Trade Promotion Organisation of Ministry of Commerce of Govt. of India, New Delhi presently at Chennai 1 Other Scripts by the same Author: Essence of Puranas:-Maha Bhagavata, Vishnu Purana, Matsya Purana, Varaha Purana, Kurma Purana, Vamana Purana, Narada Purana, Padma Purana; Shiva Purana, Linga Purana, Skanda Purana, Markandeya Purana, Devi Bhagavata;Brahma Purana, Brahma Vaivarta Purana, Agni Purana, Bhavishya Purana, Nilamata Purana; Shri Kamakshi Vilasa Dwadasha Divya Sahasranaama: a) Devi Chaturvidha Sahasra naama: Lakshmi, Lalitha, Saraswati, Gayatri; b) Chaturvidha Shiva Sahasra naama-Linga-Shiva-Brahma Puranas and Maha Bhagavata; c) Trividha Vishnu and Yugala Radha-Krishna Sahasra naama-Padma-Skanda-Maha Bharata and Narada Purana. Stotra Kavacha- A Shield of Prayers Purana Saaraamsha; Select Stories from Puranas Essence of Dharma Sindhu Essence of Shiva Sahasra Lingarchana Essence of Paraashara Smtiti Essence of Pradhana Tirtha Mahima Dharma Bindu Essence of Upanishads : Brihadaranyaka , Katha, Tittiriya, Isha, Svetashwara of Yajur Veda- Chhandogya and Kena of Saama Veda-Atreya and Kausheetaki of Rig Veda-Mundaka, Mandukya and Prashna of Atharva Veda ; Also ‘Upanishad Saaraamsa’ (Quintessence of Upanishads) Essence of Virat Parva of Maha Bharata Essence of Bharat Yatra Smriti Essence of Brahma Sutras Essence of Sankhya Parijnaana- Also Essence of Knowledge of Numbers Essence of Narada Charitra; Essence Neeti Chandrika Essence of Hindu Festivals and Austerities Essence of Manu Smriti*------------------- Quintessence of Manu Smriti* Essence of Paramartha Saara* Note: All the above Scriptures already released on www.