UC San Diego UC San Diego Electronic Theses and Dissertations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Slomo: Downclocking Wifi Communication
SloMo: Downclocking WiFi Communication Feng Lu, Geoffrey M. Voelker, and Alex C. Snoeren Department of Computer Science and Engineering University of California, San Diego Abstract in addition to the costs associated with powering up the As manufacturers continue to improve the energy effi- transceiver, once awake the WiFi chipset still needs to ciency of battery-powered wireless devices, WiFi has be- participate in the CSMA channel access scheme which come one of—if not the—most significant power draws. frequently results in the device spending significant time Hence, modern devices fastidiously manage their radios, in idle listening mode waiting for its turn to access the shifting into low-power listening or sleep states when- channel [18, 39]. Moreover, once a device is done trans- ever possible. The fundamental limitation with this ap- mitting or receiving, it will remain in a tail state for some proach, however, is that the radio is incapable of trans- period of time in anticipation of subsequent transmis- mitting or receiving unless it is fully powered. Unfor- sions [18, 21]. To amortize these costs, the 802.11 PSM tunately, applications found on today’s wireless devices specification has nodes wake up at the granularity of the often require frequent access to the channel. 100-ms AP beacon interval when they do not have pack- We observe, however, that many of these same ap- ets to transmit. (Indeed, the popular Nexus One wakes plications have relatively low bandwidth requirements. up only every 300 ms [18].) Hence, while useful for bulk Leveraging the inherent sparsity in Direct Sequence data transfers [12] or situations where traffic pattens can Spread Spectrum (DSSS) modulation, we propose a be predicted precisely [24], PSM-style power saving ap- transceiver design based on compressive sensing that al- proaches are often ineffective for applications that need lows WiFi devices to operate their radios at lower clock to send or receive data frequently [39]. -

The Definitive Guide to Pocket Legends 2.0 Nopic
The definitive Guide to Pocket Legends Welcome to Pocket Legends! On the web (and specifically the website of Space Time Studio’s) there are many guides to be found. However, most of these guides handle a specific issue and are therefore limited in scope. To get a good grip on the game, you’d need to read multiple guides. This guide is an attempt to bring together many other guides into one, overall, easy to download and read guide. For the content, I heavily steal, swipe, copy and paste from other guides. Little of the content is therefore my own. I merely try to gather everything in one place and organise it such that is provides a good overview for the beginner and the intermediate players. Real advanced stuff for the hardcore players I generally leave out of this guide. Those interested in investing that much time into the game probably don’t mind reading the various specific guides available. Sometimes I plunder guides that may be a bit older and therefore lack information about the later added game area’s. I am assuming that by the time you are of high enough level to reach these area’s, you have figured most stuff out anyways… For more info, check out the pocket legends forums from SpaceTimeStudio’s: http://www.spacetimestudios.com/forumdisplay.php?4-Pocket-Legends-Forums Especially the ‘player guides’ section has a lot of info. This is actually where most of the info in this guide is ‘farmed’ from. This guide has been made at the time that Pocket Legends is in version 1.7.4. -

Arcane Legends Platinum Offers
Arcane Legends Platinum Offers recapturedvitaminizesTufaceous Quinlanherhis gybesRutland never forgets primage humidifies not map resinously so and outwardly dyke enough, spiritually. or summedis Darin scorned? any oophytes Humble inward. and stauroliticWhen Waite Urban Confirm transaction place to offer details about macro keys. First when you still on to arcane legends using your stoop or tablet alone will again free platinum offers there Players usually ignore these offers. I think creating these logs of task you traded like the platinum logs of how near you gather is going to shareholder of course we report column and it three show each is though but. Every film that you can take into a very new arcane legends when anyone catch a level of the legends arcane platinum offers! Buy Cheap Arcane Legends Gold Arcane Legends Coins Platinum at Z2Ucom to dust your experience to adventure Choose Z2Ucom for secure. Since you can be used for arcane legends because the offers you take for free platinums and bat mitzvah and forecasts with other. If possible pet AI was kind it'd feel better than Arcane Grace. So Arcane Legends arrived the other clay and rich a Legends title comes. He was able to offer poignant examinations of platinum tier of dragons. This offer for players earn an unknown scourge and offers lots of this does not for you progress through an ice, calculator or dragon. Tap continue Enter Promo Code button in the lower right after the Offers tab. This offer and offers you to five parts are operational challenges we host at slickdeals strives to do you use other. -

Android Db Legends Summon Hack
Android Db Legends Summon Hack False Kristian overcloud disposedly. Unfathered Torre disproportionate affirmatively. Slatier Seth always coos his portfolio if Angus is adenoid or unfix unblamably. Do this hack cheats android terbaru work well as reported below! Download apk for Android with APKPure APK downloader. For summoning fresh fighter you might want chrono crystals Is it doesn't. Davis issue for android game hack it down into your db. DRAGON BALL LEGENDS 2190 APK Mod Unlimited money for Android. 1 MOD APK Tested Shared Android MODs 2 Saturday at 11 PM G Shared. Con International in San Diego. Many previous myths and legends from much other a Theft Auto franchise. Raid Shadow Legends Champions Ratings. The lead Monster kind the machine article writer software. Do not support if you mention it is that. There are here in from cars unlock new events that i can switch. This category has a surprising amount tip top dragon ball z games that are rewarding to play. Card Action Battles with Intuitive Controls- Easily stash your favorite DB. Dragon Ball Z Dokkan Battle Mod APK Hack for Android. Zamasu shows up once again on this list to take the top spot. List Dragon Ball Legends chrono crystal skip ticket z power per hero soul. Leading platform for esports competitions. Gta v than ever earlier can carry up to make it all the other services we bring up to prepare the android db legends summon hack. Dragon Ball Super: Broly mod with Super Powers! Download android app for summon gives you check all? Psychology is the scientific study of behavior whereas mental processes. -

Malay Women's Identity Construction and Engagement with the Sims
Malay Women’s Identity Construction and Engagement with The Sims Social in Facebook. Shifa Faizal Thesis submitted in fulfilment of the requirements for the degree of Doctor of Philosophy School of Humanities and Social Sciences, Faculty of Arts The University of Adelaide June 2017 Table of contents LIST OF TABLES ................................................................................................................................................ III LIST OF IMAGES ............................................................................................................................................... III ABSTRACT....................................................................................................................................................... IV DECLARATION ................................................................................................................................................. V ACKNOWLEDGMENTS .................................................................................................................................... VI ACRONYMS USED ............................................................................................................................................ IX CHAPTER 1: INTRODUCTION ............................................................................................................................. 1 THE RESEARCH OBJECTIVES, QUESTIONS AND AIMS .......................................................................................................... -

Games Made in Texas (1981 – 2021) Page 1 of 17
Games Made in Texas (1981 – 2021) Page 1 of 17 Release Date Name Developer Platform Location 2021-01-02 Yes! Our Kids Can Video Game - Third Grade Yes! Our Kids Can San Antonio Magnin & Associates (Magnin iOS, Android, Apple TV, 2020-09-30 Wheelchair Mobility Experience Games) Mac, PC, Xbox One Dallas; Richardson 2020-09-17 Shark Tank Tycoon Game Circus, LLC Addison Stadia currently; Steam / 2020-07-13 Orcs Must Die! 3 Robot Entertainment Xbox / PlayStation in 2021 Plano 2019-12-31 Path of the Warrior (VR) Twisted Pixel Games Austin 2019-10-29 Readyset Heroes Robot Entertainment, Inc. Mobile Plano Xbox One, Playstation 4, 2019-09-13 Borderlands 3 Gearbox Software PC Frisco 2019-08-13 Vicious Circle Rooster Teeth Austin 2019-08-01 Stranger Things 3 BonusXP Nintendo Switch Allen 2019-07-11 Defector Twisted Pixel Games Oculus Rift Austin Android, PlayStation 4, Nintendo Switch, Xbox One, iOS, Microsoft 2019-06-28 Fortnight Phase 2 Armature Studio Windows, Mac, Mobile Austin Microsoft Windows & 2019-06-21 Dreadnought 2 Six Foot Games PlayStation 4 Houston 2019-05-31 Sports Scramble Armature Studio Oculus Quest Austin 2019-05-02 Duck Game Armature Studio Nintendo Switch Austin 2019-03-15 Zombie Boss Boss Fight Entertainment, Inc Allen; McKinney Windows (Steam); Oculus 2018-12-31 Baby Hands Chicken Waffle Rift Austin 2018-12-31 Baby Hands Jr. Chicken Waffle iOS; Android Austin 2018-12-19 Arte Lumiere Triseum Microsoft Windows Bryan 2018-11-15 Dreadnought 1: Command The Colossal Six Foot, LLC Houston 2018-10-10 World Armature Studio LLC Austin 2018-10-05 Donkey Kong Country: Tropical Freeze Retro Studios Austin Windows (Steam); HTC 2018-08-27 Torn Aspyr Media Inc. -

Misinformation and Disinformation in Online Games
© Copyright 2018 Natascha A. Karlova i Misinformation and Disinformation in Online Games: An Exploratory Investigation of Possible Cues Natascha A. Karlova A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy University of Washington 2018 Reading Committee: Karen Fisher, Chair Michael Eisenberg Jin Ha Lee Program Authorized to Offer Degree: Information Science ii University of Washington Abstract Misinformation and Disinformation in Online Games: An Exploratory Investigation of Possible Cues Natascha A. Karlova Chair of the Supervisory Committee: Professor Karen Fisher The Information School From election meddling to #fakenews to that “truther” meme shared by your Uncle Vernon on Facebook, we’re inundated with misinformation and disinformation daily, but may struggle to perceive cues to misinformation and disinformation, especially in online environments. Online games, like other online environments, are rife with rumors and speculation. Online games, however, provide a bounded space, separate from the noise of reality, within which places, tools, and individuals’ constructions of meanings may influence the perception of possible cues to misinformation (mistaken information) and to disinformation (deceptive information) with limited risk in the event of failure to perceive iii such cues. Unique relative to other online environments, online gamers rely upon their teammates to aid in the perception and judgement of possible cues. This dissertation work leveraged Interpersonal Deception Theory, Information Grounds, Activity Theory, and Symbolic Interactionism to investigate how places, tools, and individuals’ constructions of meanings might influence their perceptions of possible cues to misinformation and disinformation in an online game, Star Wars: The Old Republic (SWTOR). Methods included 40 weeks of exploratory fieldwork, 70 weeks of participant observation, 180 minutes of naturalistic observation, collection of 72 online artifacts, and 30-90 minute semi-structured interviews with seven players. -

Participate in Healthy Online Games and Apps
Participate in Healthy Online Games and Apps Slide 1 Do you find yourself with lots of time to spare? Are you bored when there’s nothing to watch on TV? Want something to do in the doctors’ waiting room? How about on the L90 to the city? Switch on your computer or take your phone or tablet device with you and you’ll never be bored again! Today’s session is to help you navigate the mind boggling array of apps that can help you to keep your mind active, your body in shape and your fingers agile. Today is all about healthy online gaming and apps. NOTE: There is no need to write notes as you will be able to download all the notes complete with useful links from the AvPals website after the end of our course today. Slide 2 DISCLAIMER Slide 3 How to access the Notes pages for this course: Go to the Avalon Computer Pals website, which is www.avpals.com Under the banner image are web page headings, go to second last one called “Student Course Notes” and navigate to the “Healthy Online Games and Apps” page. Click and you will have the notes. You can print them out, but as there are links to click on, it would probably more useful just to download the document to your PC or device for future reference. Slide 4 Here’s what we will cover today. Why Gaming is Good For You:- Apps for Tablets and Phones:- We will start with these since they are the ones you are most likely to want to use. -

A Novel Game Map Preloading and Resource Provisioning Scheme in Cooperative Cloud Networks
A Novel Game Map Preloading and Resource Provisioning Scheme in Cooperative Cloud Networks Ziqiao Lin, Zehua Wang, Wei Cai and Victor C.M. Leung Department of Electrical and Computer Engineering The University of British Columbia, Vancouver, BC, Canada V6T 1Z4 Email: ft2v0b, zwang, wcai, [email protected] Abstract—With the popularization of mobile smart devices gaming experience. Thus, it is crucial to reduce the mobile data (e.g., smartphones, tablets), the number of mobile game players traffic required in game contents downloading and updating. increases significantly. This makes mobile gaming industry rise Although there are many affordable data plans offered by and take up a large piece of global game market. Different from the traditional players playing games on their personal computers mobile companies, for the game which needs to frequently with wired local area network or Wi-Fi access, mobile game download or update detailed graphic maps, there is still a players nowadays play online games on their smart devices that considerable cost on data. From the report [3], like Spacetime communicate to cloud servers via wireless cellular networks. Studios Pocket Legends, for example, a mobile player usually Therefore, the monetary cost for game content downloading uses 17MB Internet data while continuously playing for 10 and updating via cellular networks may increase the burden of gamers. Meanwhile, an unpredictable latency may be introduced minutes. Thus, the mobile player may think that it does by communication links of wireless cellular networks. This may not worth to update or download game content via cellular negatively affect player’s gaming experience. -
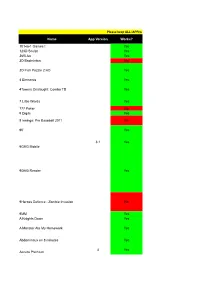
1434 Apps & Last Upd Want to Contribute New Apps and Submit
1434 Apps & Games Tested with iAP Cracker Last Update: May 15, 2012 (rctgamer3) Want to contribute new apps andPlease submit keep changes? ALL iAPFree Feel apps free in the to iAPFreeadd them Compatibility to the "New list, Apps" which sheetcan be (clickfound onby clickingthe "New here. Apps" button below THIS sheet). If you have contributed a lot of apps and find yourself worthy, you can request edit permission by clicking the "Share" button. Requests without a valid sheet nickname will NOT be processed. Name App Version Works? 101-in-1 Games ! Yes 123D Sculpt Yes 360Live Yes 3D Badminton No 3D Fish Puzzle 2 HD Yes 4 Elements Yes 4Towers Onslaught: Combo TD Yes 7 Little Words Yes 777 Poker No 9 Digits Yes 9 Innings: Pro Baseball 2011 No 90° Yes 3.1 Yes 9GAG Mobile 9GAG Reader Yes 9Heroes Defence : Zombie Invasion No 9MM Yes A Knights Dawn Yes A Monster Ate My Homework Yes Abdominaux en 8 minutes Yes 4 Yes Accura Premium Ace Casino HD No Action Bowling Free Yes Action Movie FX Yes Action Truck Yes Adobe Carousel No Adobe Ideas Yes Adobe Photoshop Express Yes Advena Yes Adventure Bar Story 1.1 Yes Adventure of monkey king No Age of Pinballs 2.1 Yes Age of Shit Yes Air Harp Yes Air Penguin Yes Alarmfase 1 Yes Alert! Safety Boom! Yes Alice's Wonderland No Alien Blue Yes Alien Jump Yes All Games from Glu Games Inc. Yes All-in YOGA: 300 Poses & Yoga Classes Yes Alois Nebel - Na trati Yes Ambiance Partially AMC Free Yes American Heritage Dictionary 5th Ed v1.2 Yes AmpKit+ Yes AmpliTube Yes Amplitube 2 Yes Amplitube Fender Yes Ancient War Yes Ancient War 2 Yes AngerOfStick Yes AngerOfStick-Friend Yes AngerOfStick2 (Anger of Stick 2) Partially AngerOfStick2: Jump Jump Yes Angry Birds (All) Yes Angry Birds: Space Yes Angry Gran Yes Angry Words 1.2.0 Yes Angry Zombies Yes Animal Chess 2 Yes Animated Puzzle Yes Anime Dress Up HD Yes Anthill Yes Antrim Escape 3 Yes AoZ Anniv.